OpenVPN - Site to Site VPN behind existing Firewall
-
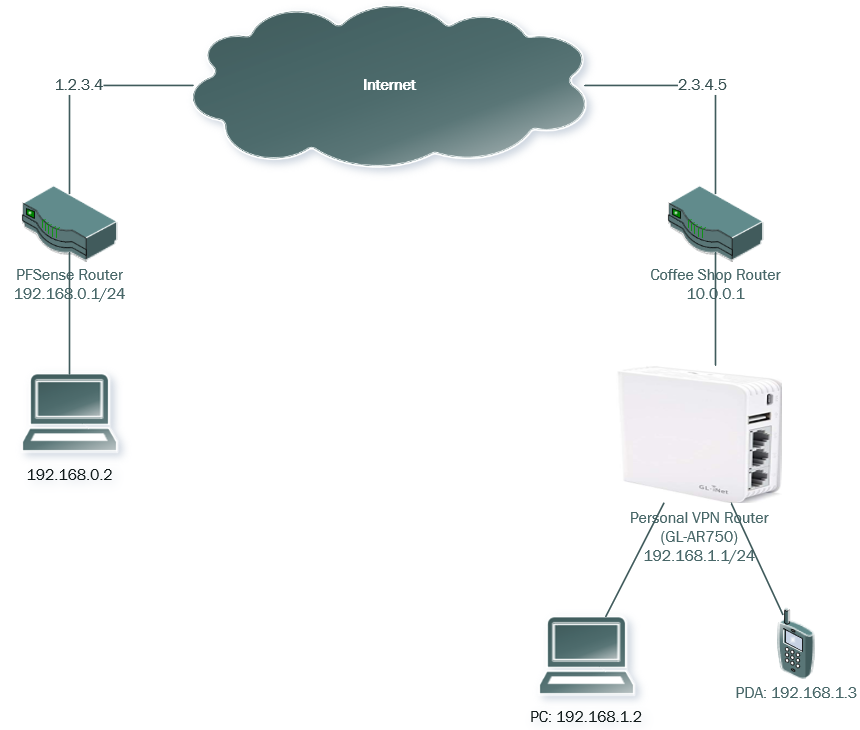
I have a corporate site with a PFSense router and a static IP.
I have quite a few users who are always on the go, but need direct access to the internal network.Here are the needs that I have for an OpenVPN configuration:
- Each of these users will have a dynamic IP address
- Sometimes these clients will be behind another firewall, such as hotels, coffee shops, a personal hotspot on their cell phone, etc...
- I need each of these clients to also have their own subnet (i.e., /24).
- Each of these clients must have access to the network at the corporate site
- The corporate site must have access to route to each of the devices (as they would allow) on the clients subnet
- I also want them to be able to have all traffic route to this OpenVPN connection
- I can't control in most cases the NAT of the Firewall that the client is on, as it is usually a hotel, coffee shop or something else.
- The client must automatically use DNS from the Corporate site.
I did this using SonicWall in the past (https://www.sonicwall.com/support/knowledge-base/how-to-set-up-a-vpn-behind-an-existing-firewall/170505253857071), and I assume this is also possible on OpenVPN. The problem with SonicWall was the devices were all too big for travel, and I had a need to switch over to PFSense. I have purchased a few devices that are small and capable to perform this, but willing to purchase other devices as needed.
If it is recommended to use IPSec instead I can.
To summarize my question, what type of configuration do I use to PFSense to achieve what I am looking to do here for site to site behind an existing firewall?
-
An OpenVPN "road access" connection would work for this. You will have to play with the port a little to make sure the coffee shop ect. allows it but I use 1198 and have never failed to connect back to my office here.
You can do a road warrior setup and literally install an OpenVPN client right on a laptop if you wish.
Your corporate site will need the OpenVPN server setup and a port open on its WAN firewall rules.
Easy Peasy!
The "tunnel" address will be your remote devices subnet so make it something outside your own subnet like 172.20.10.0/28 That will give you 14 addresses in the field.
OpenVPN is a Client Server relationship so works like any other client behind a router.
-
I tried that but the tutorials that I have all followed didn’t allow this. Also I want to make sure that the client device has its own subnet and that I can use it to access any of the devices from Corp to the client and vice versa. Do you have a suggested tutorial?
-
I did use a tutorial at the time but I forget which one.. Its pretty standard nowadays because Ive done it before.
Let me look around a bit. :)
-
@chpalmer thanks a million.
-
This guy is pretty easy to follow and listen to..
https://www.youtube.com/watch?v=7rQ-Tgt3L18
I know Netgate did do a how to but I havent found it yet.
-
Thanks. I’ll try it again.
-
@chpalmer I tried that and it does work however I would like for the little traveling router to have and registered the whole subnet that we would give for that device. For example a /24
-
Can the little router be set up with the files from the export program?
Otherwise Id set the little routers up each with their own "site to site" config.
https://www.youtube.com/watch?v=-8xt7LUtYH4
Ive got a couple dozen of these around my region.
-
@chpalmer yes I can download the profile to that router but with site to site remember one is behind a firewall such as at the coffee shop. Will this work? Thanks a lot for your help!!
-
Yes it will work because of the client server relationship. The client goes out on the internet to look for the server. So only one side has to be visible to those seeking it.
I know of at least two of my customer sites that are behind another router full time. And my vehicle router is on Verizon. Im behind carrier grade NAT when ever I switch it on.
The only reason it will not work is if the wifi you try to use blocks the specific port you are trying to use. Many will use something like port 80 to get by this. Like I said though.. Ive never been blocked using port 1198 on my road warrior setup.
-
Some links.
https://forum.netgate.com/category/34/openvpn
https://docs.netgate.com/pfsense/en/latest/vpn/openvpn/index.html
-
I was having problems with the last video because it was requiring me to upload a config file, however now, I installed OpenWRT on it, and I think there has to be a way now to configure the device manually. I am really looking into this now.
-
This post is deleted!