Ping and Traceroute basics
-
Hi all,
My ping and traceroute functionality is not performing as I would expect so I'm coming here as I'm sure there as some basic things I am missing. All below is me trying to ping/traceroute public hosts/IPs.
Two images that give an idea of my setup and interfaces:
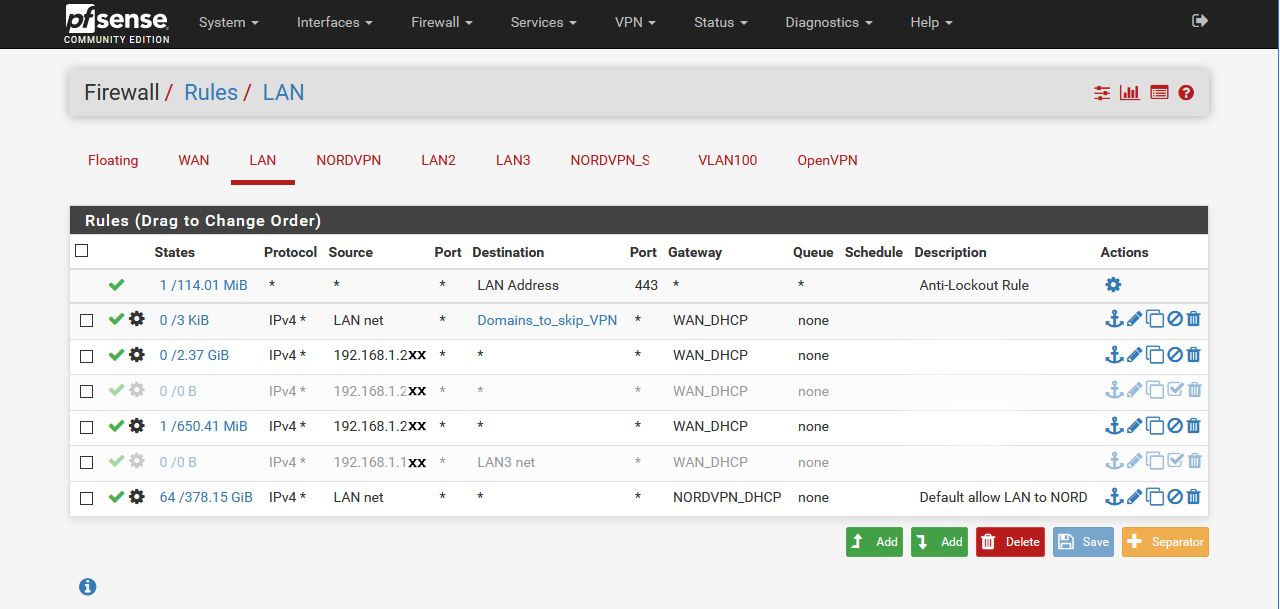
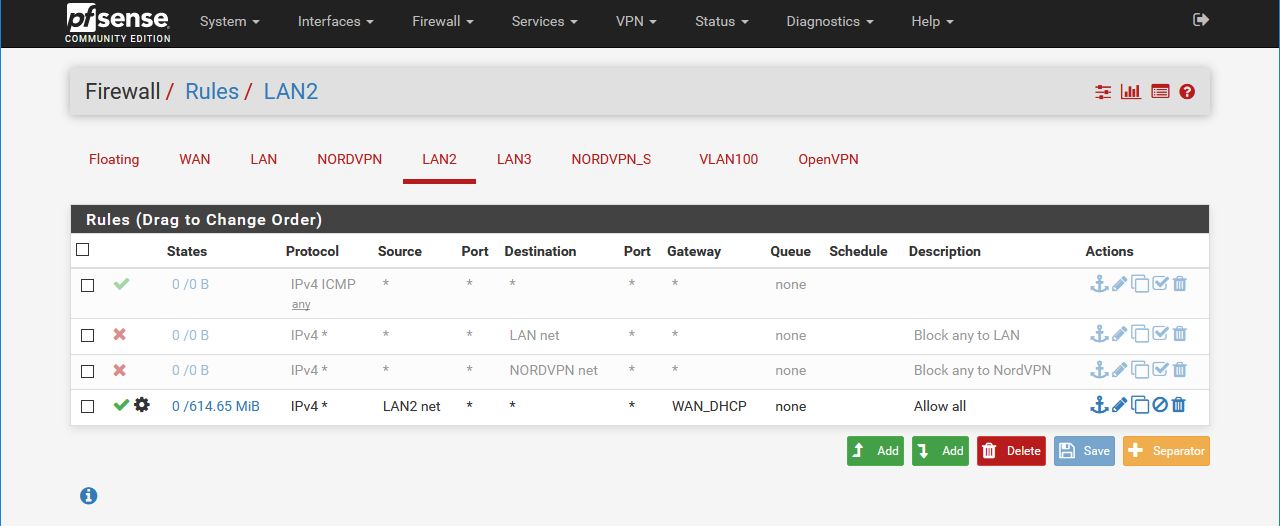
Some indicative facts or issues:
- I can ping/traceroute from LAN and NORDVPN interfaces. The LAN, with a couple of exceptions, routes to the NordVPN gateway.
- I cannot ping/traceroute from LAN2 interface. LAN2 traffic is routing straight to the WAN gateway.
- When I set some domains to skip the VPN for devices on LAN, a traceroute from the device will confirm traffic to that domain is not going through the VPN.
- A traceroute on pfsense LAN interface will still go through the VPN (first hop being the VPN gateway).
- The default gateway for pfsense is still the WAN gateway.
I have tried a few more things but don't want to clutter this initial post and list them all. I am trying to ping/traceroute from various networks to the external addresses/URLs to make sure filters or routes I set up are working. But evidently, pings and traceroutes are not performing as I would expect at all.
What am I not understanding???
-
So on your lan2, your saying a client can not ping anything? So can it ping the lan2 pfsense IP, can it ping pfsense wan IP?
Do you have any rules in floating?
-
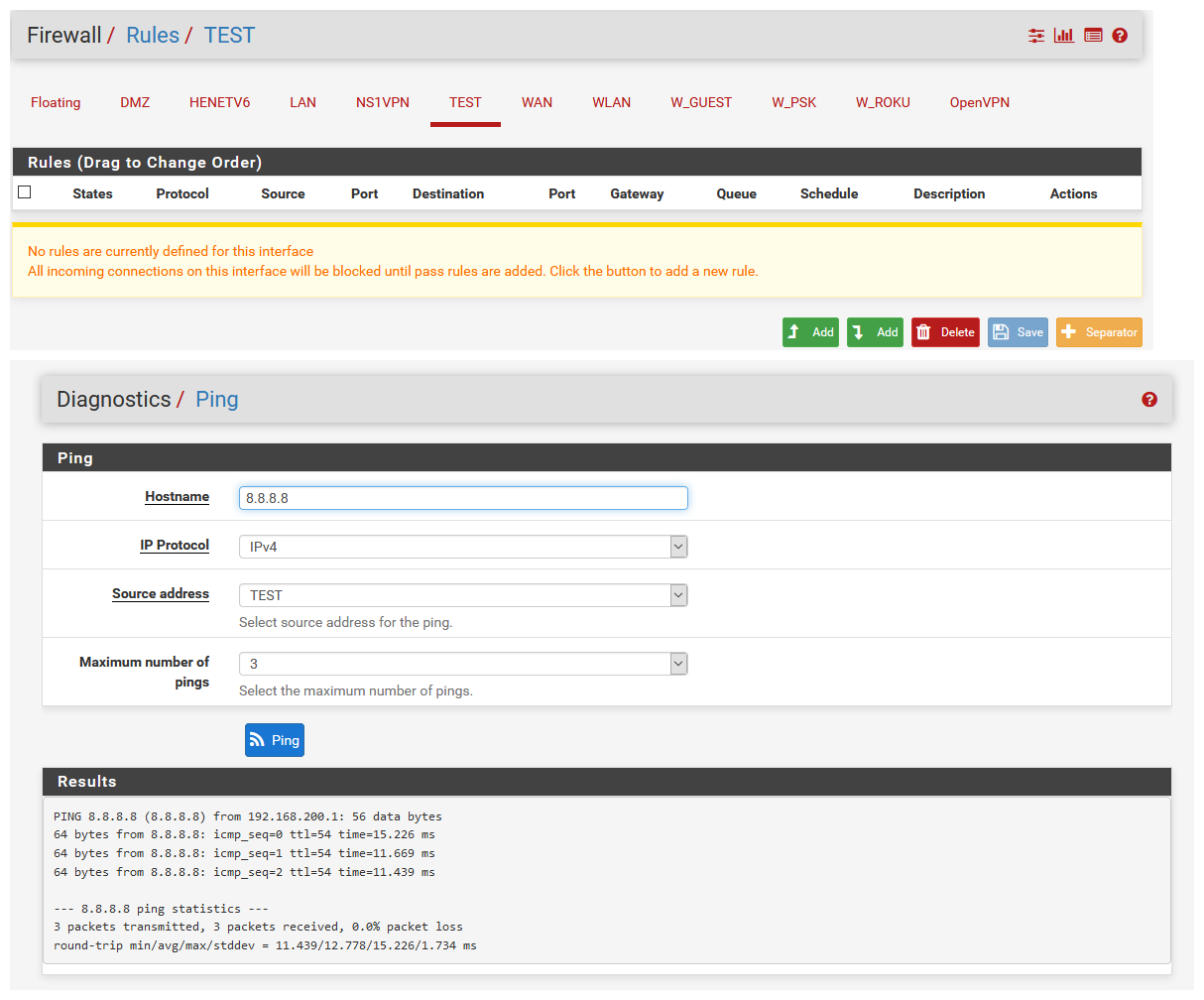
@johnpoz Thanks for the reply. This is all regarding performing the ping/traceroute from the pfsense GUI. However I have tried what you asked (I had to connect a client as I use LAN2 for IoT type devices) and I can ping the LAN2 pfsense IP. I can also ping public IPs from that client connected on LAN2.
To perhaps help (I hope) with your question, I had to do some further tests from LAN3 as there is only 1 device and no switch currently on LAN2.
- From the pfsense UI, with the source set to LAN3, I can ping a device on LAN3.
- From the pfsense UI, with the source set to LAN3, I cannot ping a public IP.
And for completeness, this is the result of me trying to ping the same 8.8.8.8 IP from the pfsense GUI, changing the source to different interfaces:
- WAN - yes
- LAN (routed through NORDVPN) - yes
- NORDVPN - yes
- LAN2 - no
- LAN3 (routed through NORDVPN_S) - no
- NORDVPN_S - yes
Lastly, there are no rules in Floating.
Hopefully this is useful info.
-
What are you outbound nats set as? My guess is you pulled routes from your vpn service, and that is what pfsense is using as its default - and your not natting these other interfaces to your vpn ip..
I don't believe pfsense itself would use a gateway rule you set on the interface..
Post up your outbound nats, and routes from pfsense. You can view them in the gui under diag, routes
-
@johnpoz I thought the answer my be NATing but I haven't found it myself. I probably overlooked/didn't understand something. Here you go:
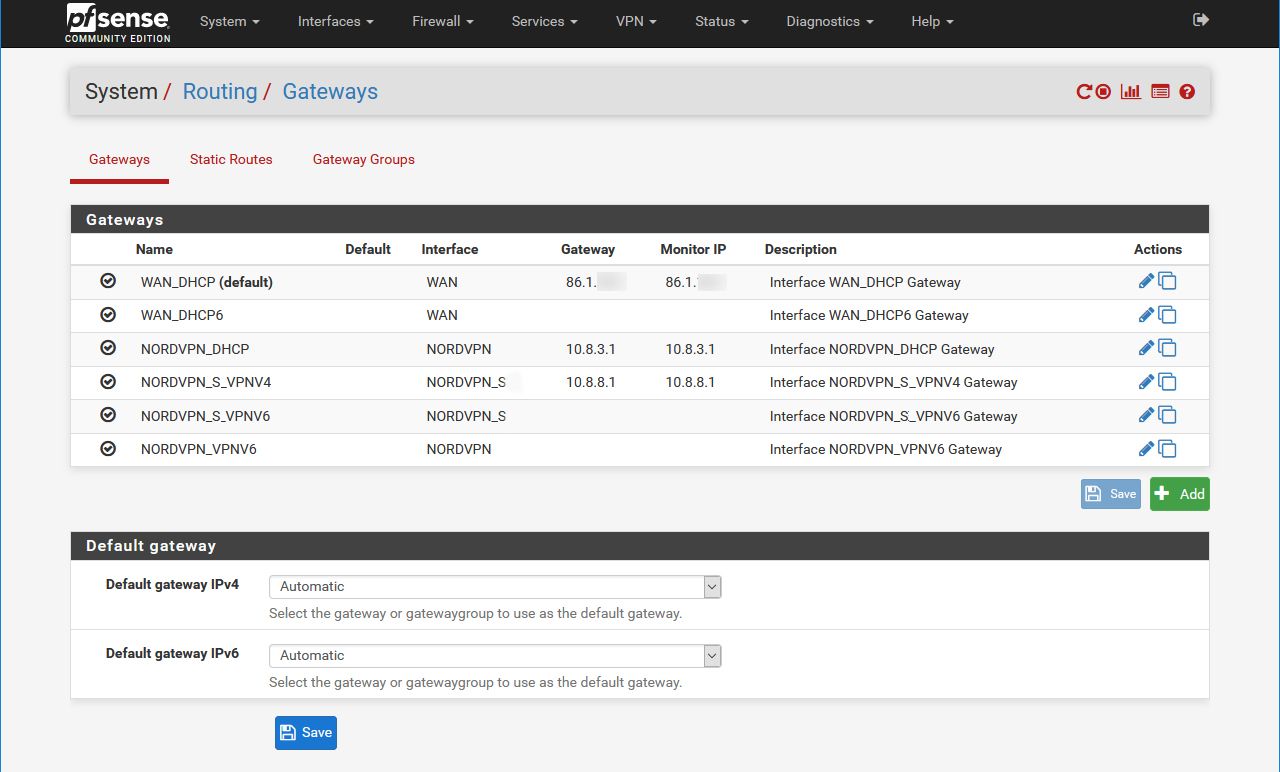
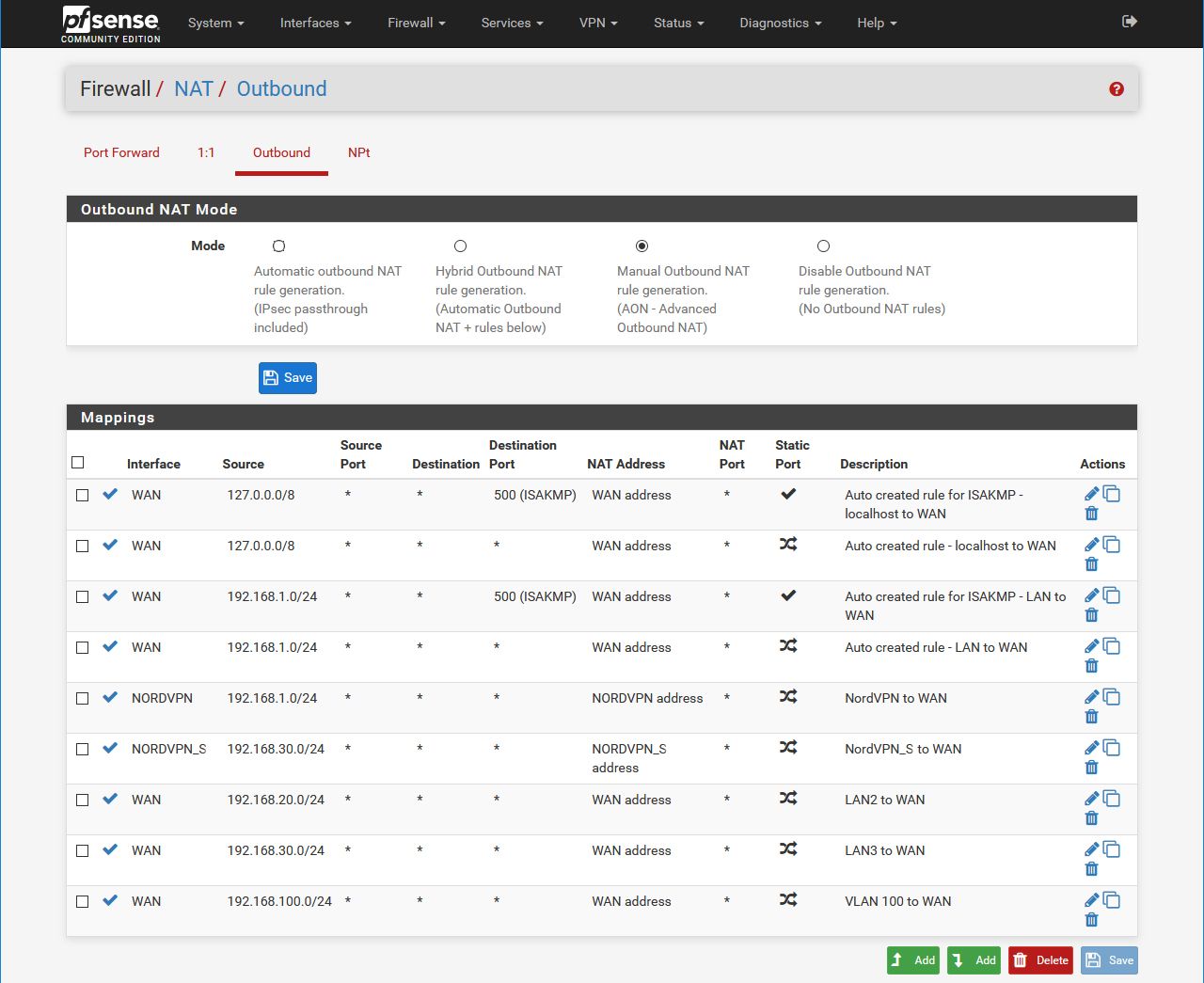
-
where are you routes - can almost bet you pulled routes from you vpn service. And setting manual is not required, all that is required to use vpn service is set hybrid and set the local networks you would like to nat to the vpn interface in the hybrid rule.
-
Running tests from the pfSense GUI is not valid in a situation like this. Those tests do not hit the policy routing rules as they never pass the interface they ate only sourced from that IP.
Without using the policy rules they will be routed according to the system routing table. That will be using the default gateway which is currently set to 'automatic'. I strongly suggest setting that to a known fixed gateway so you know where traffic will be routed.Steve
-
@johnpoz Sorry. I think I made an error in my response showing you gateways and not routes. And you are right, I'm pretty sure I copied configs initially from the VPN service I had set up, and adapted where needed. There is nothing yet set in the static routes config (if that's what you originally wanted).
I have changed the NAT rule to hybrid.
-
@stephenw10 Ok good. That was a fear of mine that any traffic originating at the interface IP will not be subject to rules of the interface subnet.
Also, I'm assuming setting a single default gateway would not achieve the result I want as, as you've figured out, I'm trying to have a way to troubleshoot routing from all subnets through all gateways I have set up? Should I not be creating a rule for each interface to pass through a suitable gateway? Though I tried setting a rule on LAN2 for ICMP from "LAN2 address" to any destination through WAN gateway, which still failed.
-
Your default route should always be out your wan... You then can policy route traffic you want to go out your vpn connection.
Most of the guides out there are just BS... they have you switch to manual outbound nat and pull routes from the vpn service.. Zero reason to do any of that.
-
@johnpoz said in Ping and Traceroute basics:
Most of the guides out there are just BS... they have you switch to manual outbound nat and pull routes from the vpn service.. Zero reason to do any of that.
<Sarcasm On>
Yes, there is a great reason for them to do that if the VPN provider wants to collect all of your traffic for possible use in some other revenue stream of theirs ...
</Sarcasm Off> -
@johnpoz I suppose it may depend on the context of the instructions. In a commercial context you may not want any other rules to exist than what was manually created for security and compliance reasons. But I digress. :-)
So.... I've changed the outbound NAT mode to hybrid. I've set the default gateway to the WAN gateway. This all makes sense.
Now what?
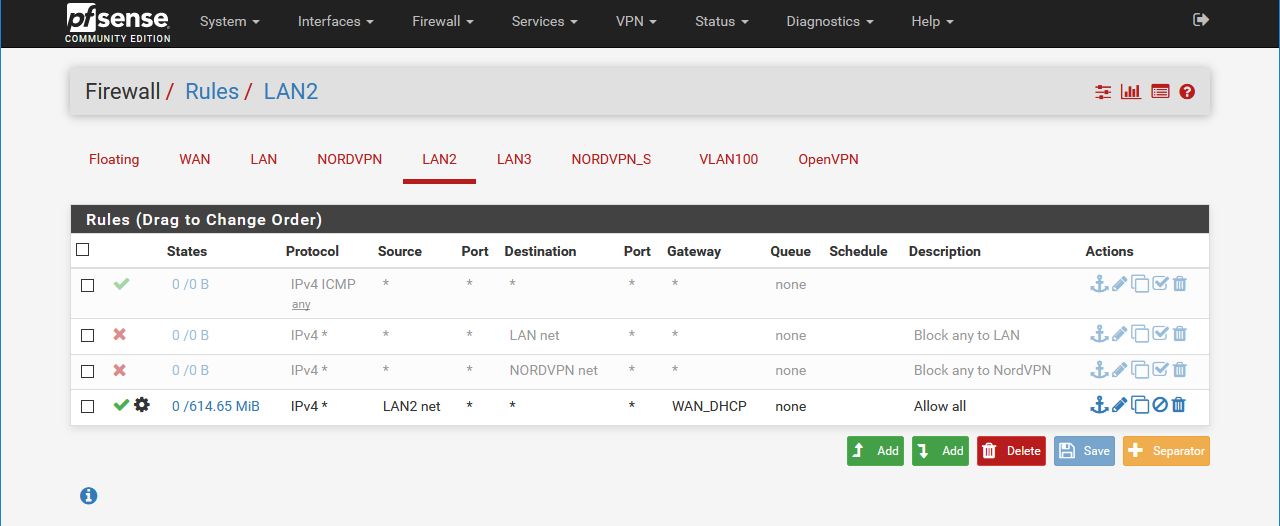
Is it as in my message to @stephenw10 where I need to create an ICMP rule for each interface to route through a specific gateway? I tried setting up such a passrule as follows:
Protocol: IPv4 ICMP any
Source: I tried both "LAN2 address" and "any"
Gateway: Now left at default.
The rest of the options were left.This didn't work. Hopefully someone can help with the next step(s).
-
You have yet to show your routes dude. If your default route is your wan, and your outbound nat is correct then you would be able to ping from that as source.
You don't need any rules on the interface to ping with pfsense using that as source.
Pfsense itself does not use the rules that are on the interface.
You need rules on the interface to allow or block traffic entering pfsense from that network.
Gateway: Now left at default.
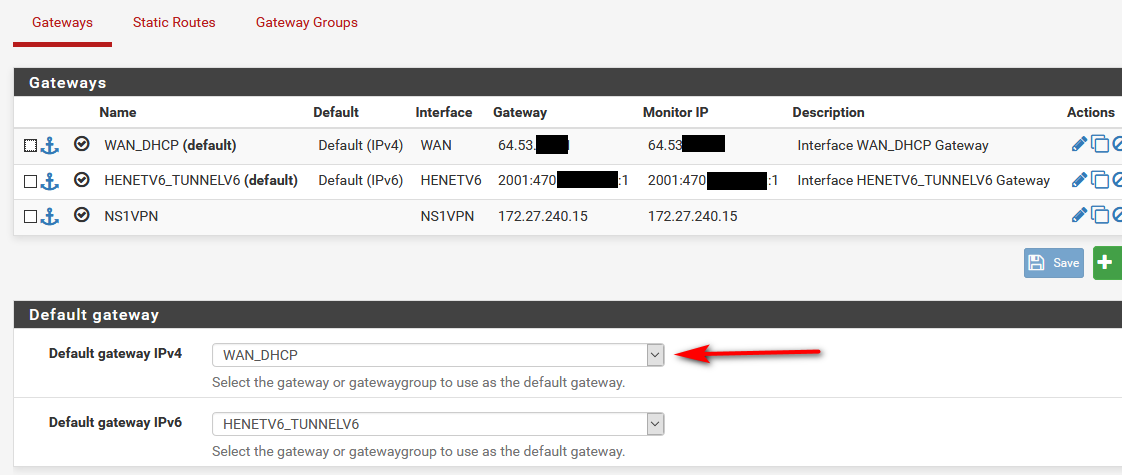
Set your gateway - don't leave it at auto.
-
@johnpoz Thanks for the time you are putting in.
What I meant was under System > Routing > Gateways, I have now set the default gateway as WAN, as in your image above. I then went to Firewall > Rules > LAN2 and set up a rule with the gateway left to default. Though I also tested specifically with WAN set as the gateway. Show below (disabled).
Just to make sure I understand correctly and don't post stuff you don't need, when you say you want the routes, do you mean the rules for each interface (which has rules) under Firewall > Rules?
-
dude pfsense will NOT use rules you set on the interface.. Only clients hitting pfsense from that network will use them.
set your gateway as I showed in mine above vs using automatic.
And post up your routes
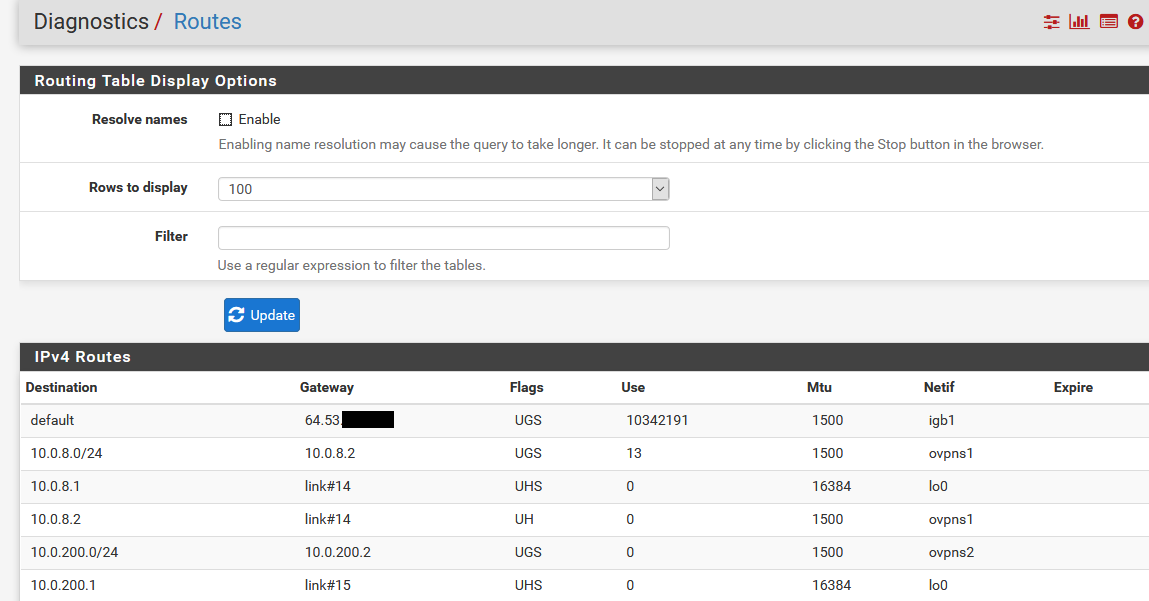
Do you see the default route there... That is what pfsense will use to talk outbound from itself.
If you wan to test if policy routes are working, etc. then you have to do the ping / trace from a client on that network - not from pfsense.
-
@johnpoz Understood. Also, ping/traceroute is now working from all interfaces. Though I'm not sure why it wasn't working at the time of my last post.
My routes anyway:
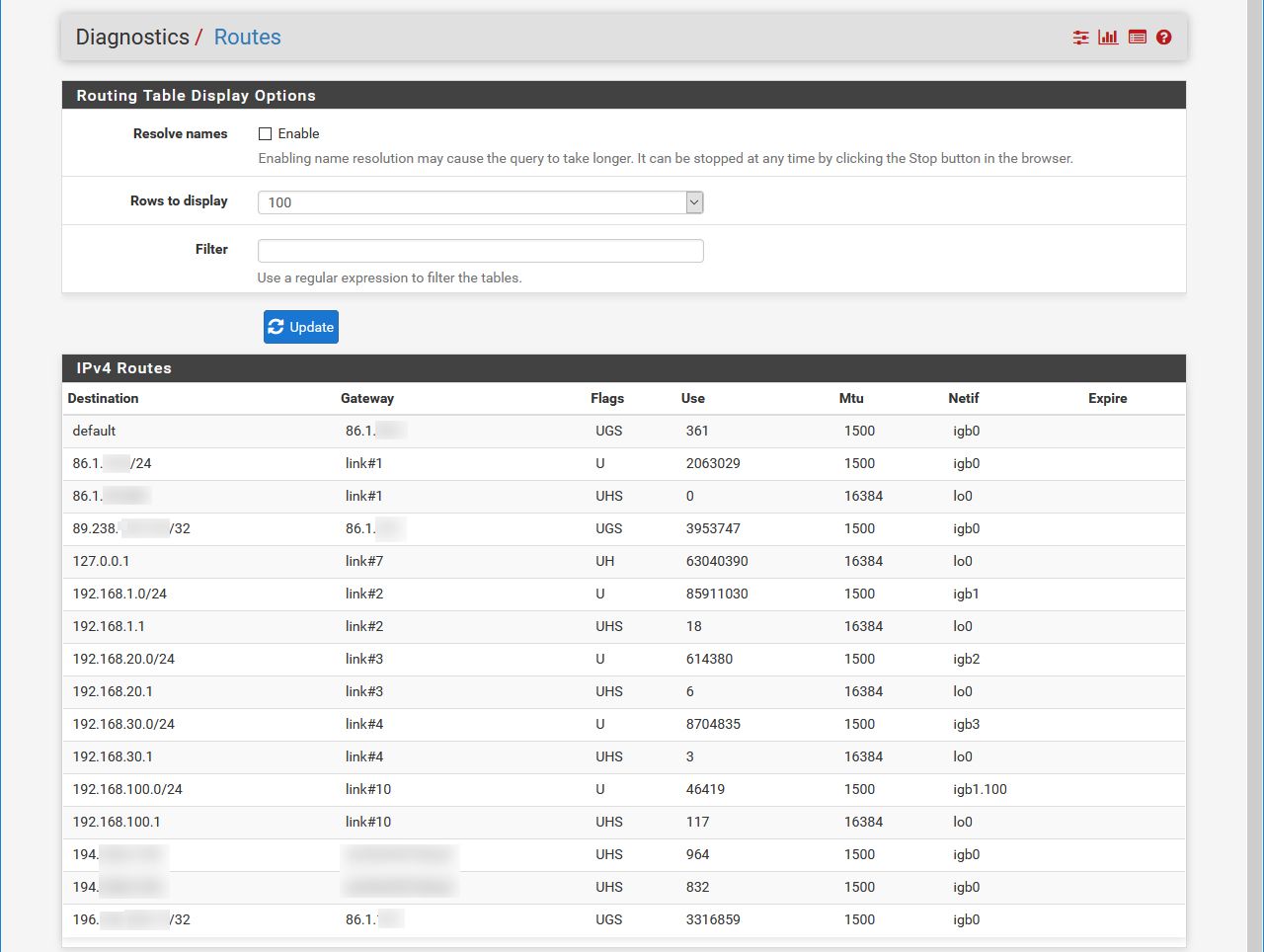
I suppose now I have both answers of getting ping working on the router and figuring out how to test
routingfirewall rules for each network by using a client in that network. And also a clearer understanding of pinging via interfaces.@johnpoz a hundred thank yous.
-
The only way to validate rules on an interface is to check from client on that network, you can not test them from pfsense directly.