Port forward to an address behind another router
-
Hello ,
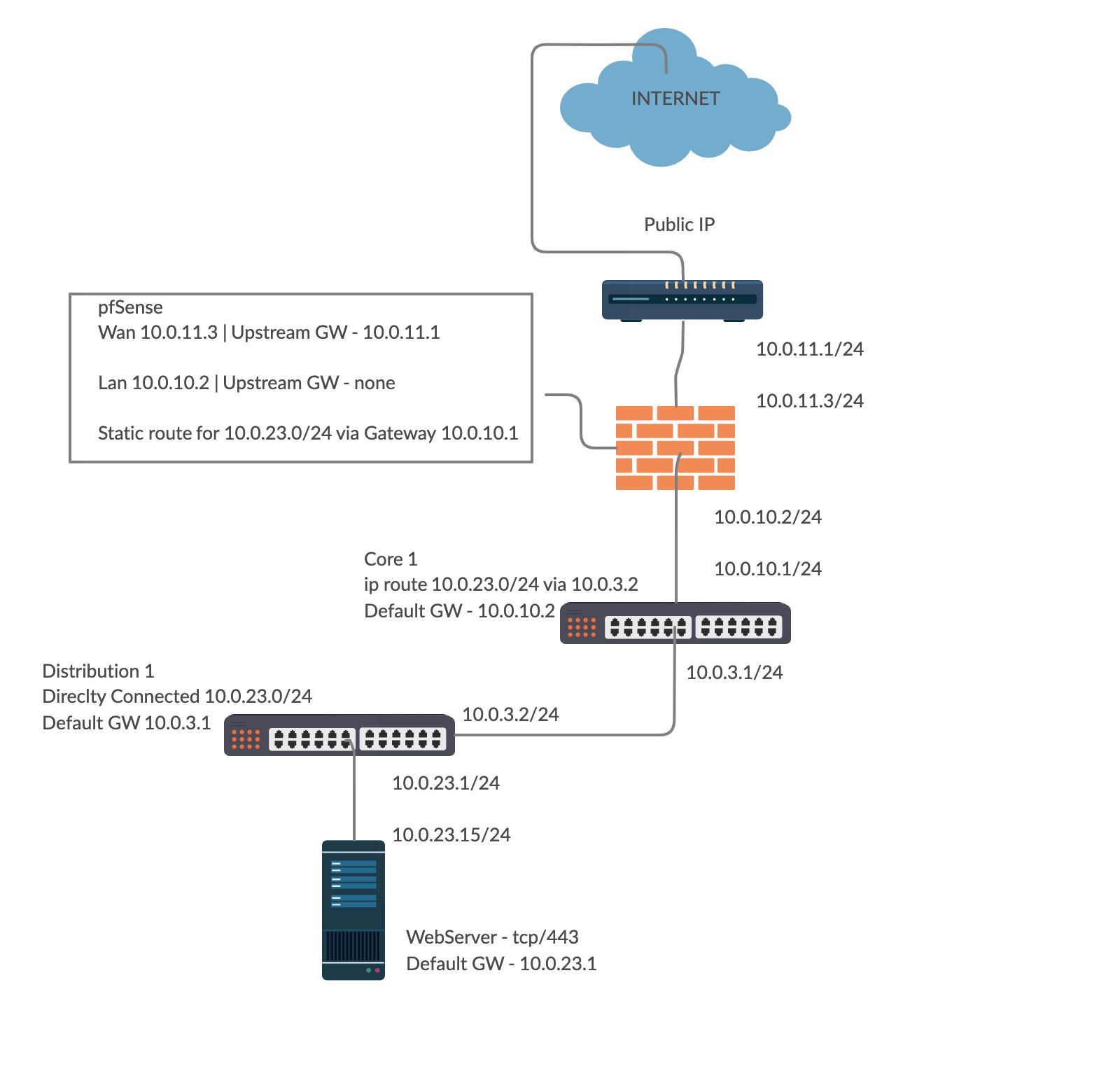
My network is like this :
{Internet Router - 10.0.11.1} => {10.0.11.3 -PfSense- 10.0.10.2} => {10.0.10.1 - L3 SW - 10.0.23.1 } => 10.0.23.15 - Web Server}Internet Router is owned by ISP ( leased line ) and i dont have any access so i forward everything to PfSense. In Pfsense i need to port forward port 443 to server 10.0.23.15 .
All static Routes are OK, NAT is ok , everyone has internet and and every host or intermediary device is reachable by anyone in Intranet.
If i move my server in Pfsense LAN network (i.e 10.0.10.254) , everything is ok but if i move it in 10.0.23.0/24 Network the NAT Port Forward does not work. I am sure that i miss something.
Any suggestions ? -
Your L3 switch has all necessary routes? Does it filter?
Has 10.0.23.15 the right default route?
Port forwarding in pfSense correct? Did you create a filter rule yourself or let it create one for you? Can you ping 10.0.23.15 from pfSense (Diagnostics)? Test Port for tcp/443 working, too? -
@geokef said in Port forward to an address behind another router:
and every host or intermediary device is reachable by anyone in Intranet
are you saying you have devices on 10.0.10 I assume /24.. So your downstream is not via a transit?
-
@JeGr
L3 switch has all routes . It doesnt filter anything , only routing . Port Forwarding in pfSense is correct. Firewall Rule is auto created after Nat Port Forward rule created by me. I can ping 10.0.23.15 from pfSense and backyards. Server is listening tcp/443 and checked from pfsense also.
Also no blocked logs on FW neither packet sniff from LAN side of pfsense to rest intranet.Webserver Default GW - 10.0.23.1
L3 SW Default GW - 10.0.10.2
pfSense Default GW - 10.0.11.1@johnpoz
In 10.0.10.0/24 i have pfsense ( lan side ) and L3 SW ( "wan side" ) . As i said before L3 SW has default GW pfsense etc.
I have tested also with VDSL line and home base modem router . Same results.The problem is specific and as i said before it appears when the NATed packet need to routed from pfSense instead of just ARP forward on his lan network.
I used to work with CISCO intermediary | FW and this is my first psSense so i thought that i missed something in Advanced Config of pfsense . If you believe that with the standar routing and NAT conf it should work . I ll reset it and start over , especially NAT and rules probably i forgot something.
-
A port forward would not require and arp to be returned for the ip your forwarding too, unless pfsense thought the downstream network was its own local L2.
So if you have overlapping lan on pfsense with some downstream that could be a problem yes.
-
Ill try to visualize a part of my network.
I just want to port forward tcp/443 from pfSense to my webserver.
NAT/Port Forward in my pfSense is :
Source Any
Destination Wan Address
port 443
redirect address 10.0.23.15
Automated rule exists.
Route to 10.0.23.0/24 exists via GW 10.0.10.1Thanks in advanced for your replies
-
Wow two downstrea routing hops.. There is no problem with doing that... As long as you routing is correct, pfsense will send the packets on.. Sniff on it... When you hit your port forward.. Does pfsense send the packets out the 10.0.10 network to 10.0.10.1 mac...
I can fire this up to show it working... But take me a bit to add the 2nd downstream hop.. I wouldn't be able to do that remotely. But once it leaves pfsense.. Its job is done... So validate that pfsense is putting the traffic on the wire to 10.0.23.15..
So I can fire up a svi on my downstream L3 switch, and then have pfsense forward to a network behind that..
-
@johnpoz
Thats all i need to hear . That there is no limitation in pfSense about that. I ll make same monitoring again and packet sniff and check again rules and ill come back .
Thx a lot -
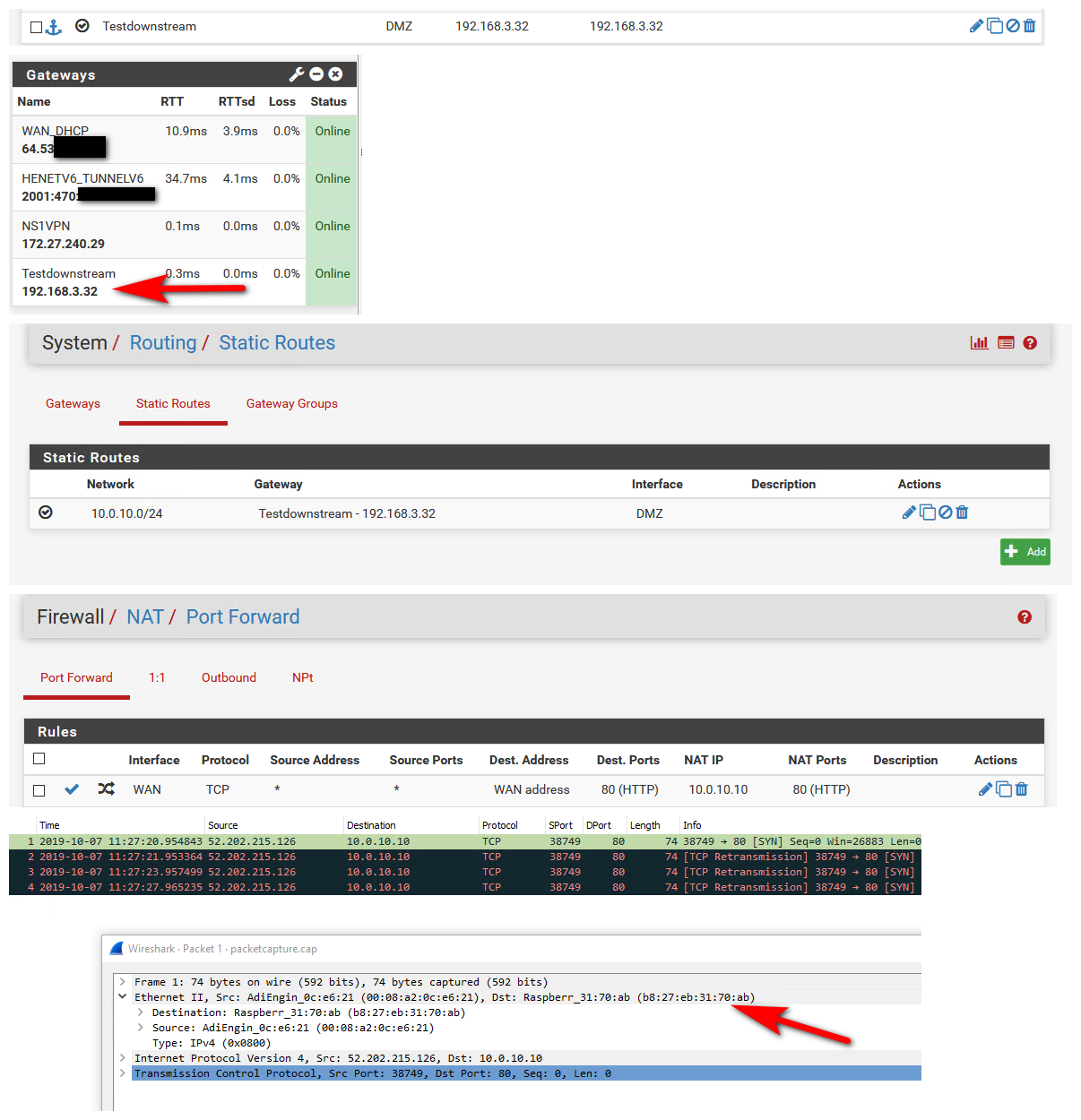
Here you go did a simple test for you... Created a downstream gateway, created a route to a downstream network 10.0.10/24
Then created a forward to an IP on this downstream network (which doesn't really exist).. But pfsense doesn't know that..
Then sniffing on the interface were this downstream gateway exist with pfsense diag, packet capture then loading it in wireshark to see all the meaty bits easy.. I from the outside sent some traffic to port 80.. As you can see pfsense put it on the wire to 10.0.10.10 with the mac of my downstream router interface.
After that pfsense is out of the equation until there is return traffic.
-
@johnpoz
You are 100% correct.
pfSense can port forward at any subnet behind other routers as NAT and Routing tables are correct. The problem was on my ISP and the new Public IP he gave me which was blocked in inbound traffic. SOLVED. Thanks a lot for your time.