I made a WireGuard package for pfSense
-
Hey everyone.
I wanted to try out WireGuard on my new pfSense router, and in the process I decided to make a package for it. I've been running it on my router for about a week without any issues, so I figured I'd share. Please note that both WireGuard and this package are still very experimental. Use at your own risk.
Source and release is here: https://github.com/Ascrod/pfSense-pkg-wireguard Bug reports and PRs welcome.
This package depends on the
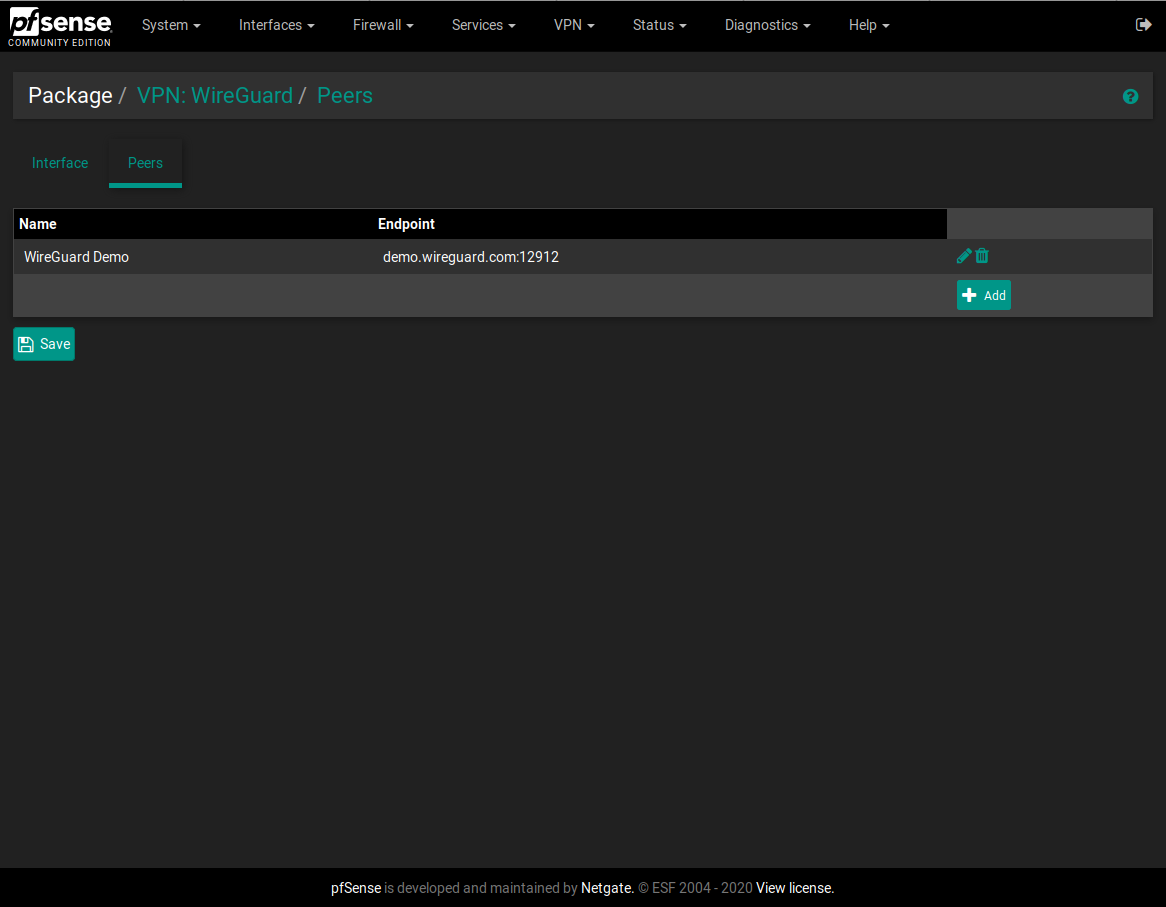
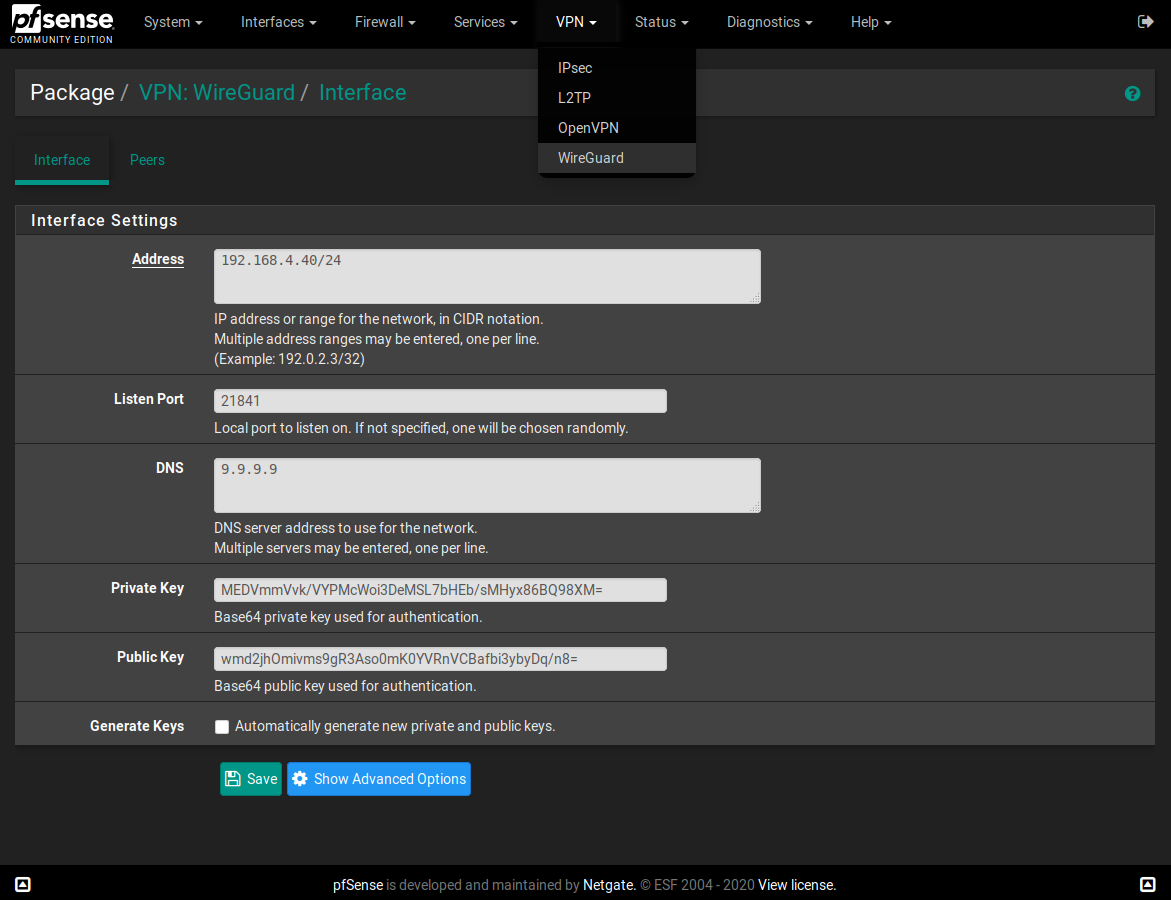
wireguardandwireguard-goports for FreeBSD. You will need to download the appropriate builds for your version of pfSense, or build them, and then manually install them before installing this package. I am using wireguard-0.0.20190227_3 and wireguard-go-0.0.20181222 in my current setup.The package supports configuring one interface and any number of peers. Once you have them set up, go to the Assign Interfaces screen and create a new interface for tunwg0. Name it, enable it, and don't touch any other settings. Once the interface is up you can configure firewall rules for it and generally treat it the same as a physical interface. It should persist across reboots.
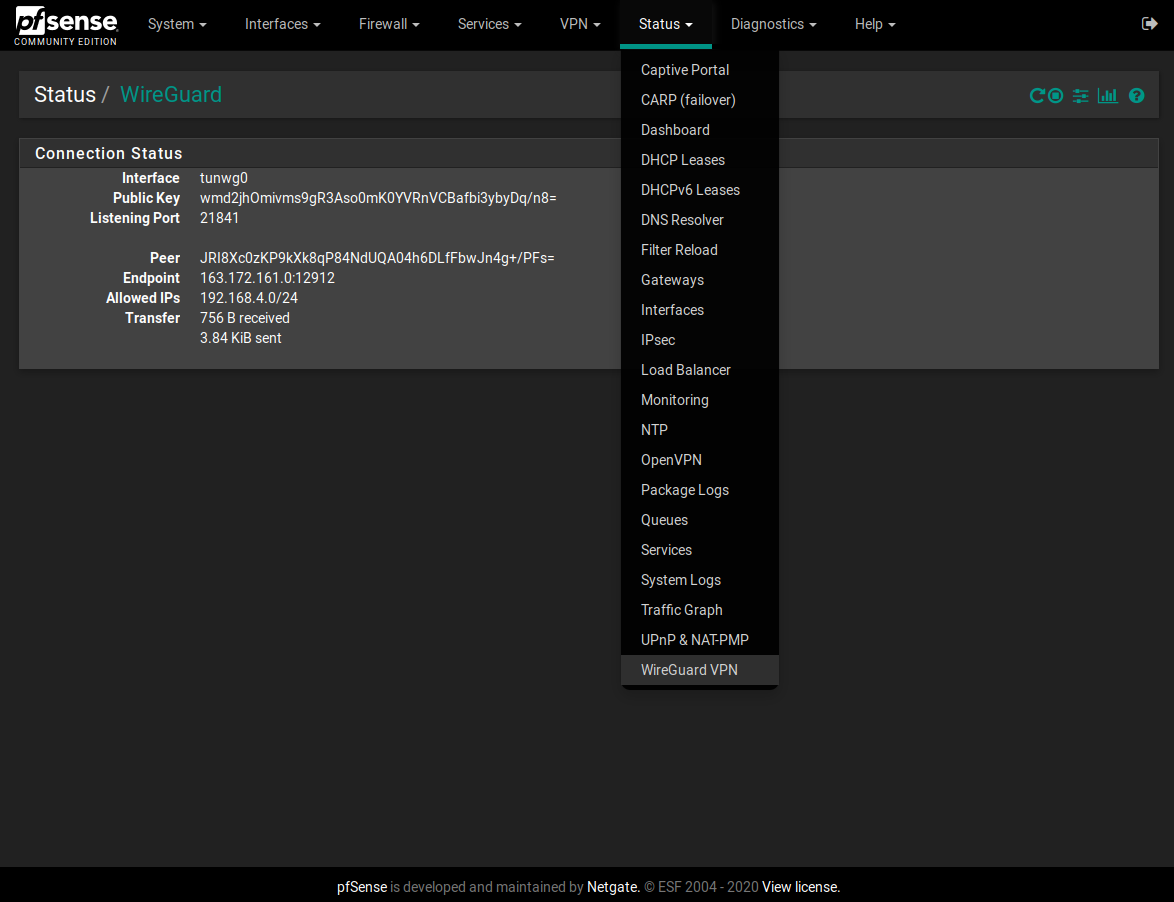
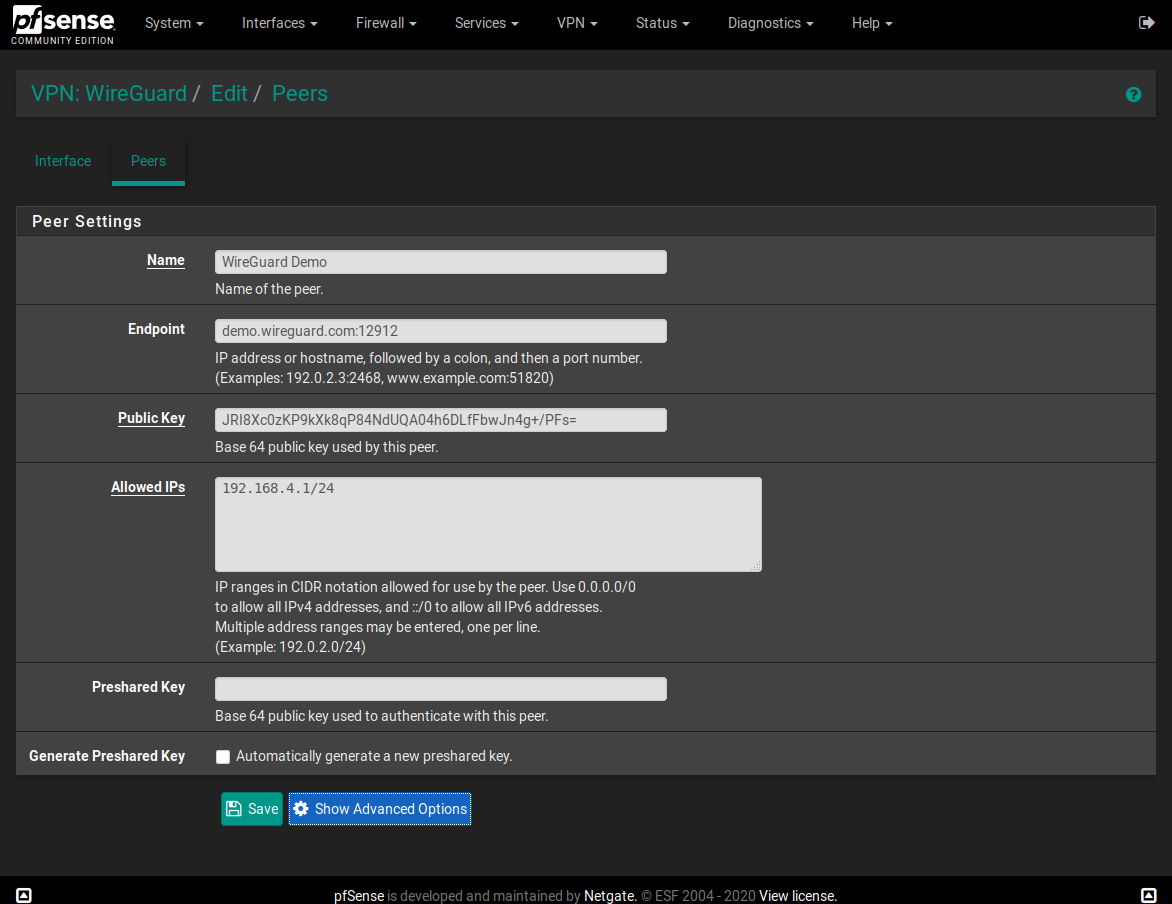
Screenshots:
Interface Editor
Peers
Peer Editor
Service Page
Status Page -
Excellent contribution, I would like to try it, but I am not able to compile it in pfsense.
Could you share the package already compiled for pfsense v2.4.4-p3?
-
@pepe00 The release on the GitHub page should already be targeting 2.4.4-p3, the current release.
-
Sorry, I only found the source code and not the pfSense-pkg-wireguard-1.0.0.txz
I already have it installed, I will perform tests
-
For my first test, I would like to connect my android mobile to my internal network.
I create the "WireGuard" interface group, but I don't know what rules I have to add to the pfsense, could you help me?
This is my configuration:
My internal LAN: 192.168.1.0/24In pfsense:
[Interface]
Address = 10.23.5.1/24
ListenPort = 51000
PrivateKey = server_private_key
PostUp = ifconfig tunwg0 group WireGuard[Peer]
PublicKey = movil_public_key
AllowedIPs = 10.23.5.2/32In android:
[Interface]
PrivateKey = movil_private_key
Address = 10.23.5.3/24
DNS = 1.1.1.1[Peer]
PublicKey = server_public_key
Endpoint = public_IP:51000
AllowedIPs = 192.168.1.0/24 -
@pepe00 My bad, I should have explained this more - I have updated my initial post to include some instructions. When I get time I will also add a README to the repository.
For a simple setup, you shouldn't need to create an interface group or configure a
PostUpcommand. On the Interface Assignments page, create a new interface fortunwg0and enable it. Don't touch any other interface settings. Once you have the interface set up, you can then forward the VPN's port (51000in your case) to your interface's IP and assign firewall rules to it like any other interface. That should get you started.Looking at the config you posted, I think the interface address on your Android client needs to be a single address, not a range (e.g.
10.23.5.3/32). Typically for mobile clients you also want to set AllowedIPs to0.0.0.0/0,::/0so that the interface can route all traffic over the tunnel. If you need more help configuring WireGuard itself, I can recommend this unofficial documentation, especially the examples.Hope that helps!
-
Thanks for your help!!!
I created the "WireGuard" group, because I thought that the assignment of tungw0 would not be persistent to reboots, but I just verified that it is wrong.
I have deleted the group and the PostUp rule.
I have added a peer for another site (LAN: 192.168.10.0/24) with pfsense:
[Peer]
Endpoint = Public_IP_Site_B: 51000
PublicKey = public_Site_B_key
AllowedIPs = 10.23.5.254/24,192.168.10.0/24Route tables were created automatically, and it worked without problems.
The VPN road warrior from the mobile, still not working, I will have to check my settings. I have already applied the changes you suggested.
-
A very interesting functions would be:
- The possibility of automatically creating the private and public key of the peers.
- The possibility of exporting the peers configuration file.
The WireGuard program for android, you can export and import a "wireguard-export.zip" with the wg0.conf inside.
Do you see it viable or very complicated to program?
-
@pepe00 There are options for automatically generating a public/private key pair for the interface, and a PSK for a peer. Just click the respective checkboxes for those options and then click save. (I would like to make those into buttons that can work dynamically without saving, but I don't know if packages can make AJAX calls like that.) Note this will overwrite any keys or PSK already present.
I'm not sure about importing and exporting the config file yet. Currently to export you could use
scpto copy the config file under/etc/wireguard/to your system; I'm not sure if you can import this way, as the package config might overwrite it. You can also copy-paste text from the configuration UI or from the status page (which shows the same info as if you had runwg show tunwg0from the command line). -
My idea is to add the possibility to export the client configuration file for a peer, to import it on the mobile device and configure it quickly, something similar to the "OpenVPN client export" plugin.
I have already seen that there are options to automatically generate a public / private key pair for the interface and a PSK for the peer.
What is missing is the option to automatically create a public / private key pair for the peer, with the intention of using that private key to generate the exportable configuration file.
In the case of a road warrior connection, it is as simple as generating a [peer_name].txt with:
[Interface]
Address = IP_peer
DNS = 1.1.1.1
PrivateKey = private_key_for_peer (self-generated in peer configure)[Peer]
AllowedIPs = 0.0.0.0/0, :: / 0
Endpoint = Public_IP: UDP_port (request public_IP)
PublicKey = public_key_serverI don't know if I have explained myself better now, sorry for my English.
-
The VPN from my mobile already works!
In addition to opening the UDP port in WAN and allowing the necessary traffic in WIRE (tungw0), so that the mobile can go to the internet, it is necessary to create a manual outbound NAT witch source 10.23.5.0/24 rule in my case.
-
Is this plugin compatible with the new 2.4.5 release?
Has anyone done a performance comparison with ipsec and openvpn so far?Anyway, thank you and keep up with the good work!

-
I would also love to know if anyone has tried this out on 2.5, I imagine there could potentially be an issue because of the kernel update? But I have no clue myself.
I just updated to 2.5 and was wondering if there was any update on wireguard working and of course only saw that someone had figured out a way to get it working after I updated.
I'm so glad that someone decided to try to make it work! Been waiting on wireguard integration for too long. Keep up the great work!
-
@oneiro I intend to upgrade my router to 2.4.5 soon, along with
wireguardandwireguard-go, and will post results; since it's a security/maintenance release, I don't expect too many issues.@BRH212 Unfortunately I don't have a spare physical machine to use for testing 2.5, but I did install all three packages on a VM and did some preliminary testing. Haven't see see any issues with the UI package so far.
Keep in mind that this package is only an interface for the
wireguardandwireguard-gopackages (which I am not involved in the development of). You could theoretically use WG on pfSense without my package and it should still work, you'd just have to configure it from the console instead of the web UI.Also, be sure that the versions of
wireguardandwireguard-gothat you install match the version of FreeBSD for your pfSense install, otherwise you could potentially run into some issues. pkg should warn you if there's a version or architecture mismatch when attempting to add a package. -
I would like to give this a try but I’m not a CLI person so don't know how to install the package or where to even start. Do I unpack the compressed file(s) and use something like WinSCP to place them into the directory? Thanks in advance
-
This post is deleted! -
All right, I upgraded to 2.4.5 and so far I'm not seeing any issues. During the upgrade process
pfSense-pkg-wireguardwas removed, and after reboot I had to remove the oldwireguardandwireguard-gopackages before adding the new ones. I'm now using wireguard-1.0.20200319_2 and wireguard-go-20200320.@S762 Perhaps this page would be helpful to you? Assuming you haven't downloaded anything yet, you can use the command
pkg add http://<url_to_pkg>to download and install a package from a URL - no need to unpack anything.If you're using pfSense 2.4.5 like I am, you can use these commands on the command line interface, or the Command Prompt page on the web interface:
pkg add http://pkg.freebsd.org/FreeBSD:11:amd64/latest/All/wireguard-1.0.20200319_2.txz pkg add http://pkg.freebsd.org/FreeBSD:11:amd64/latest/All/wireguard-go-0.0.20200320.txz pkg add https://github.com/Ascrod/pfSense-pkg-wireguard/releases/download/v1.0.0/pfSense-pkg-wireguard-1.0.0.txz(I cannot stress enough that you should heed all the warnings about how using the command line or installing outside packages can possibly break your system. This is all very experimental and not officially supported in any way, and not for the faint of heart. If you don't mind taking a risk and/or are comfortable with the possibility of having to fix or reinstall your firewall, and you still want to try it out, make a configuration backup first!)
-
@Ascrod So I found this yesterday and I tired it for the first time just now. I'm on 2.4.5 and I used the links from your post just a few hours ago. I got no errors, but if I can into Assign Interfaces I don't see it. I see the Wireguard package status in my dash and it is stopped, but when I try to start it then it tries for a bit and then fails. The system log shows these entries every time I go through that process;
Apr 12 12:29:22 kernel tunwg0: link state changed to DOWN
Apr 12 12:29:22 kernel tun0: changing name to 'tunwg0'
Apr 12 12:29:22 kernel tun0: link state changed to UP
Apr 12 12:28:26 kernel tunwg0: link state changed to DOWN
Apr 12 12:28:26 kernel tun0: changing name to 'tunwg0'
Apr 12 12:28:26 kernel tun0: link state changed to UP
Apr 12 12:27:41 kernel tunwg0: link state changed to DOWN
Apr 12 12:27:41 kernel tun0: changing name to 'tunwg0'
Apr 12 12:27:41 kernel tun0: link state changed to UP
Apr 12 12:27:34 kernel igb3: promiscuous mode enabledAny ideas what it could be tripping up on?
-
As a follow up, it does show in VPN and I can configure things like the IP range and have it gen private and public keys. It seems the key will be being able to get that interface up and running and I'll be in business. Thanks for any suggestions you can provide.
UPDATE - Once I'd input the items above, I could get the service to start. Once the service was started, i was able to assign the interface. Looks like I am in pretty good shape now. This is great work - I really hope they can get something like this into pfSense ASAP so we'll have support for upgrades and backups and such.
-
@burntoc You have to configure the VPN before you can use it... was that your issue?
If you need to troubleshoot further, running WireGuard from the command line might help. I haven't figured out how to pipe all of WG's output to the log yet, so some errors may not be easy to troubleshoot from the web interface alone.