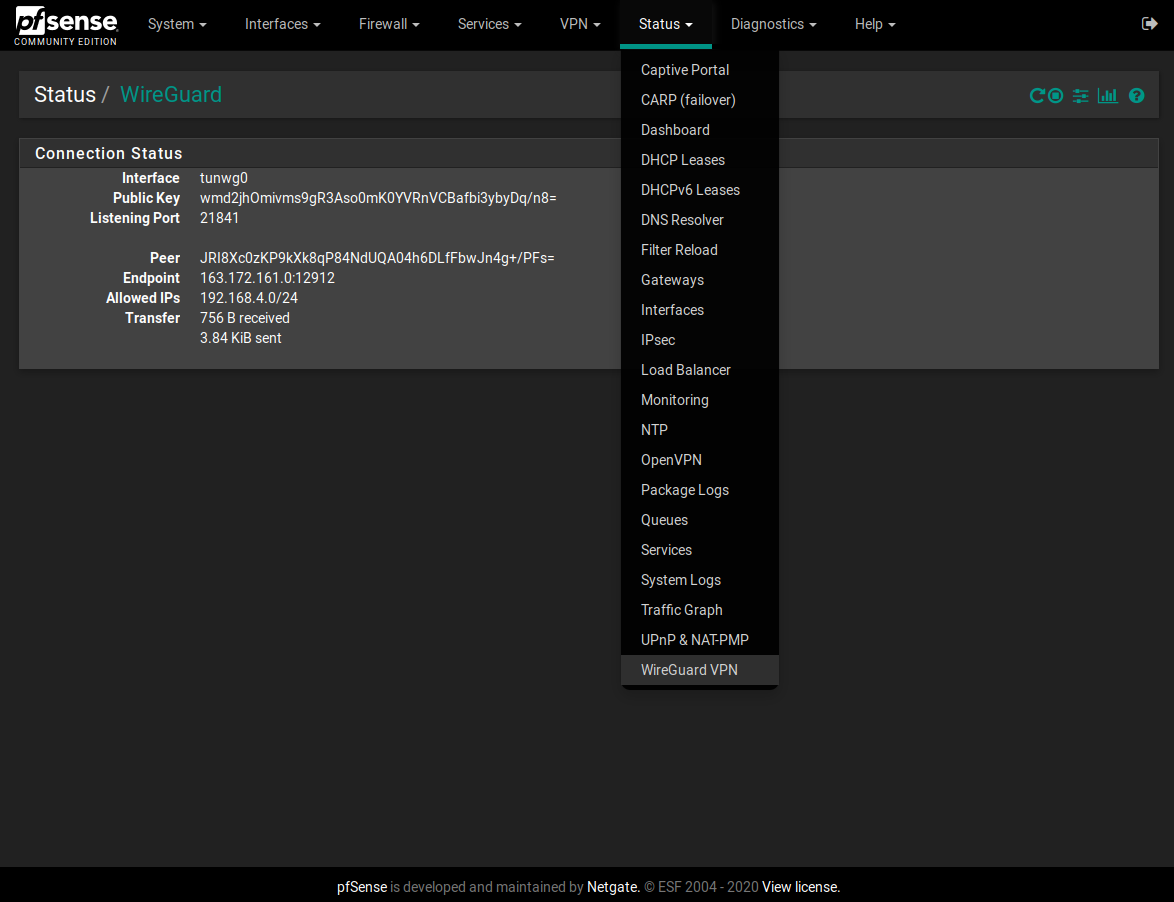
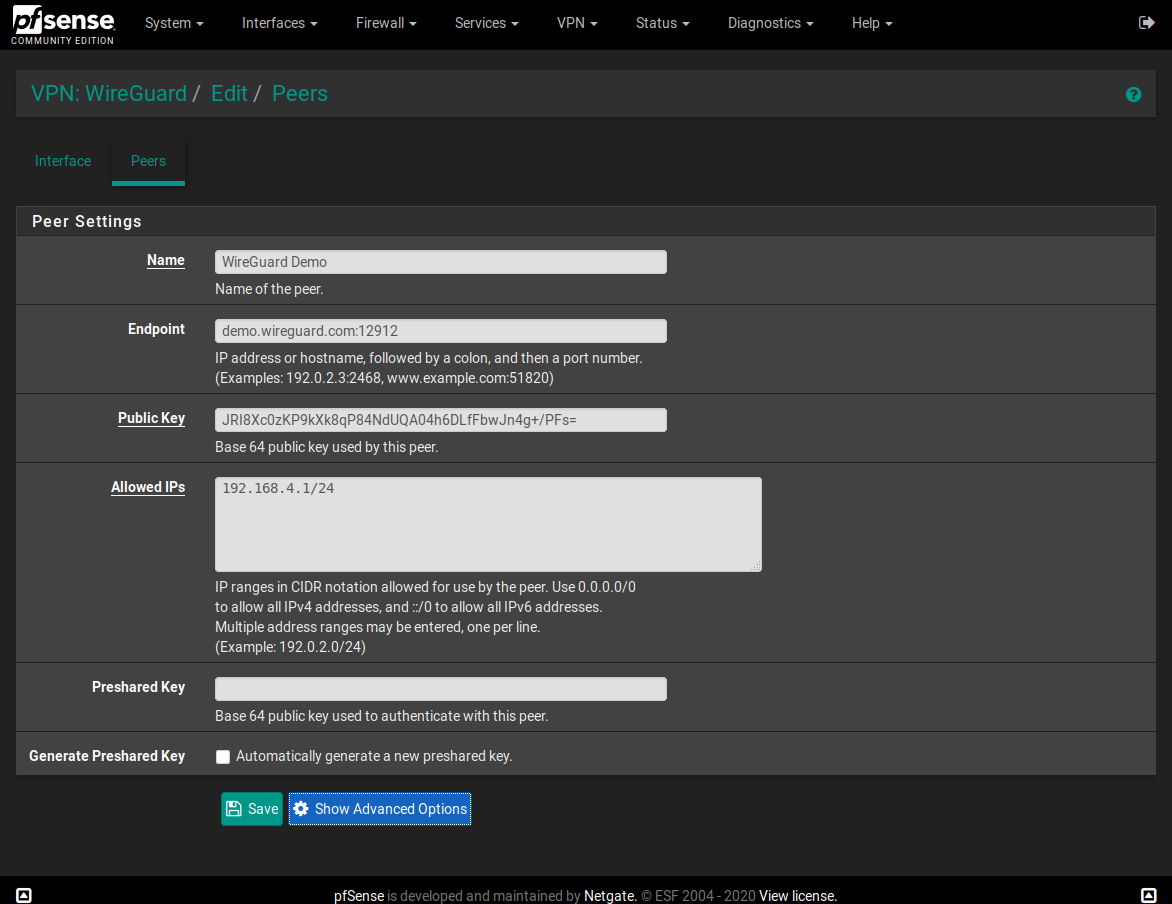
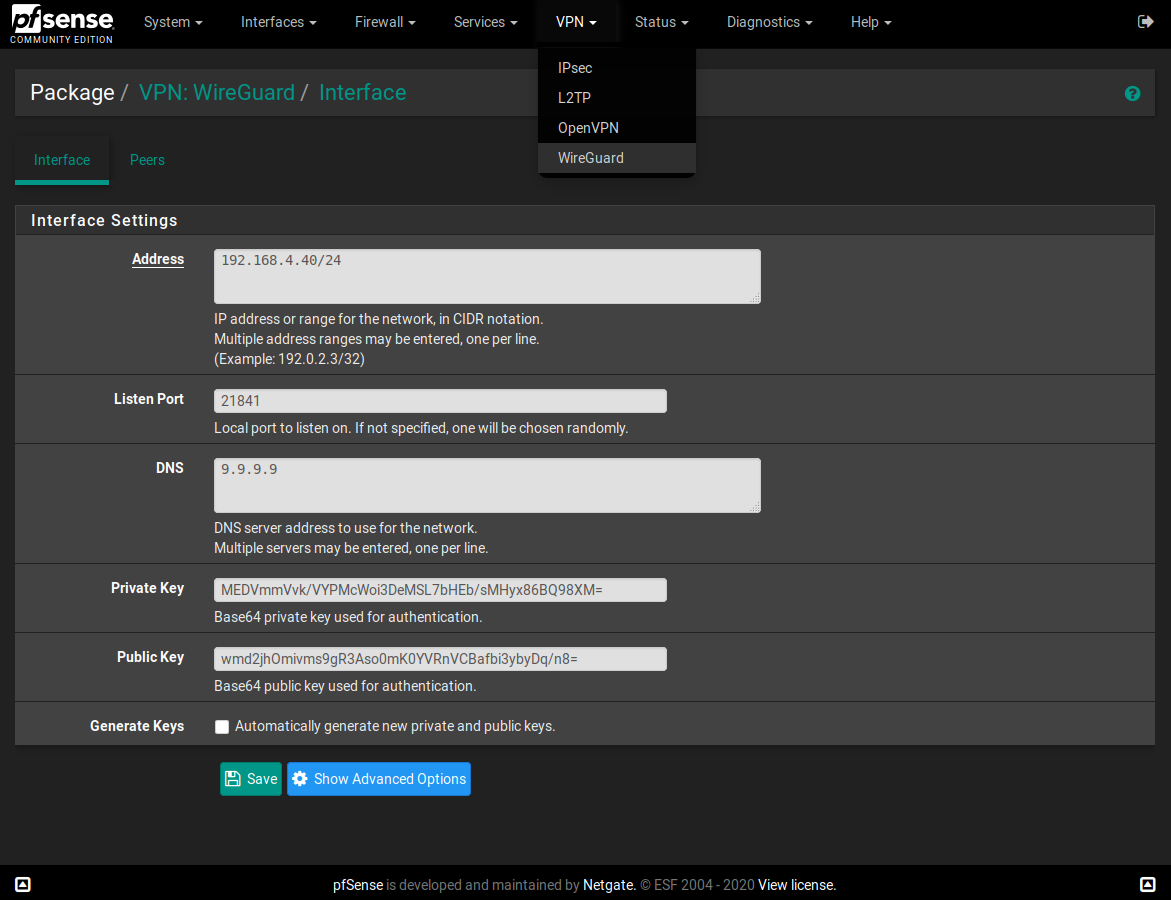
I made a WireGuard package for pfSense
-
How can I add a new interface and configure it seperately from this package?
-
@baran WireGuard only supports one interface per configuration file. You will need to create and use a new config file entirely from the command line. Unfortunately you won't be able to use it with this package at this time.
-
Any input would be appreciated. I have the same issue as @cappiz where, when my wireguard service is running, my pfsense loses all internet connectivity on the WAN interface. Is there a need of some additional rules to be added or something?
-
@alirz I haven't been able to reproduce this, so I'm not sure what exactly would be causing it. A cursory Google search shows that others have had this problem, and doesn't appear to be specific to a particular OS. What happens if you restart the WG service? Are you only seeing traffic in one direction to/from the WAN port? Do you see anything unusual in your system logs?
-
@Ascrod if i restart the wireguard interface, i lose internet again at home. its like there is some conflict of routing between WAN/LAN/TUNWG0 or something.
Do i need to some ip forwarding/NAT rules between WAN/TUNWG0/LOCALHOST etc ?I have wireguard server successfully running on an ubuntu machine on my LAN.However i would prefer to run that on my pfsense box also. on ubuntu I had to enable ip4 forwarding and add some NAT iptable rules etc to get the traffic flowing as per all the intrucions out there in almost all tutorials.... Does the same need to be done on pfsense? I cant find any info on this. Thank you.
-
@alirz I didn't have to set up anything special on my actual setup or my test VM, other than port forwarding inbound traffic to the VPN interface and actually enabling the interface, so I would ensure that you have done both of those. You shouldn't have to set up any other special forwarding on pfSense like you would on Ubuntu, because pfSense is designed to be a router (this post goes into some detail about that). Also, iptables rules definitely won't work on pfSense because it uses pf rather than iptables.
I'm not entirely sure what's going on here, but I would double-check your WG config against some working examples (again, ignoring the PostUp/PostDown commands that most people use for routing in Ubuntu) as well as your logs. Make sure your interface address is a range if necessary (I use /24 on mine) and that your client is routing properly. (One time I ran into an issue where I had set the allowed IPs on one of my "client" peers to 0.0.0.0 rather than 0.0.0.0 /0. That caused a few hours of headache.)
-
@Ascrod ok so I didn't add any inbound route to the VPN interface(tunwg0) yet.
So am I to a FW RULE for udp traffic from any port, Where source is ANY or WAN? and destination is the particular VPN interface? -
@Ascrod It looks like I'm almost there. But missing some routing.
Here is my setup.Pfsense WG config: I've hidden real keys. But still showing which keys are used where
[Interface] # Generated by pfSense Address = 10.100.100.1/24 ListenPort = 51830 DNS = 10.0.0.1 <----- Pfsense local LAN IP PrivateKey = xxxxxxxxxxxxxxxx [Peer] # phone PublicKey = cccccccccccccccccc AllowedIPs = 10.100.100.2/32 [Peer] # IPAD PublicKey = vvvvvvvvvvvvvvvvv AllowedIPs = 10.100.100.3/32Client config of Android Phone
[Interface] Address = 10.100.100.2/32 DNS = 10.100.100.1 PrivateKey = dddddddddddddd [Peer] AllowedIPs = 0.0.0.0/0 Endpoint = my_ddns.com:51830 PersistentKeepalive = 21 PublicKey = ccccccccccccccccccNow im not sure which and where i need to add the rule for the vpn interface. Is it under NAT and port forward from WAN to OPT4 Address? OR is it under NAT> Outbound?
Note my above config works fine if i move that to my ubuntu wireguard server and simply forward UDP port 51830 from pfsense to my ubuntu machine IP.. NOTE: For testing purpose im using the same private and public keys on my ubuntu wireguard server and this one im trying to setup on the PF box. I believe that should not be an issue? Thanks for your helpI tried the following rule but i dont think thats correct
If i tcpdump on my pfsense internet side(WAN) interface, i see constant incoming connection attempts from phone and then the pfsense reponding back to the phone from the WAN interface.
But if I trace on the TUNWG0 interface i only 1 request from 10.100.100.2(Phones vpn ip) to the pf sense WAN inteface.
This is the furthest ive been able to get now. From the pfsense and from my LAN devices, i can ping the phone's vpn ip(10.100.100.2) but thats it. I cannot ping LAN IPs, lan DNS, 8.8.8.8 etc from the phone. -
Please help me to install on 2.5...
-
@murzik 2.5 or you mean 2.4.5?
-
2.5.0
file in repository built for FreeBSD 11, so I am getting an error trying to install on Pfsense 2.5.0 -
@alirz Your configs look all right. I can't see your NAT rule, but if you already have one set up for your server then the only modification you would need to make to it (or a copy of it) is to have it redirect to the VPN interface address instead of the server address and making sure the associated firewall rule updates accordingly.
-
@murzik As stated above, you need wireguard packages for the version of FreeBSD that corresponds to your pfSense version. 2.5.0 is based on FreeBSD 12.
-
@Ascrod I did attach the links to google photos for a screenshot of my interface page and one showing the port forward tule in my post above.
By the way, I’m using the packages listed above on my 2.4.5 pfsense. That should be ok right? I didn’t rebuild them or anything.i simply installed the ones listed above. Even though they are for 2.4.4. But seems as one poster mentioned, they work on 2.4.5 also? -
ok. i got it to work. Had to add two rules.
One on the WAN rule to allow inbound on the WG portStates Protocol Source Port Destination Port Gateway Queue Schedule Description Actions 0 /2.67 MiB IPv4 UDP * * WAN address 51830 * noneSecond FW rule for my WG interface(OPT4) in my case
Firewall >Rules >OPT4 States Protocol Source Port Destination Port Gateway Queue Schedule Description Actions 15 /9.99 MiB IPv4 * * * * * * none Wireguard vpnBased on DNS leak checks, looks like all traffic from my phone is now going through the home internet as it should. I can also access my Lan network devices etc.
-
@alirz Well After my brief success, something is not right again. DNS is not working. I can ping everything over the vpn via IPs but not my hostname.
perhaps at some point something was working and active sessions probably led me believe that everything was working. But eventually when either those states/sessions expired or when i rebooted the FW just to be sure, at some point DNS stopped working.
I really wish routing for this was simple. -
@alirz I've had some issues with DNS occasionally not working after a reboot. Try restarting the DNS service; I believe that's what I've had to do the last few times.
-
@Ascrod OK that fixed it..thats strange though. Ive done several reboots and it didnt do anything. So is there some sort of race condition going on here that the DNS service on pfsense needs to restarted once more after a reboot? Sucks as this kind of makes it a bit unreliable!!
i am also running openvpn server on the pfsense...Does that show affect this?
Any fix for this DNS issue? perhaps add a startup script to restart DNS shortly after a reboot is done? -
ok so i used the "shellcmd" package that can launch commands during/after boot.
I added the following command in there to run after reboot.sleep 30 && pfSsh.php playback svc restart unboundHad to put a sleep because restarting dns right after reboot doesnt fix the issue.
Wish this get resolved eventually when this whole thing makes it into PFsense officially. I dont like these patchy fixes that i lived with for years when i was suing dd-wrt/openwrt years ago. -
Do we know of the dns issue is related to the unbind DNS server or to the wireguard models? If later, is there a newer build of wireguard available?