Netgear/Vlans/Pfsense
-
@johnpoz said in Netgear/Vlans/Pfsense:
This is switch setup
pfsense - 1U,5T --- switch --- 5U --- vlan 5 clientIf you could look at the following pictures they show the netgear switch setup as it is at the moment.
https://ibb.co/0ft99fJ
https://ibb.co/D9W0ZXV
https://ibb.co/wy401MF
https://ibb.co/z7Rv26ZPfsense is plugged in to port 2
VLAN5 PC Client is plugged in to port 1
Everything else is plugged into port 3
-
that looks correct yes..
But its not working if your seeing mac of devices in 192.168.1..
Clear your arp table... Do they come back? trying pinging one of those 192.168.1 address from your client after you clear your arp.
BTW your rules on vlan 5 are WRONG!!! source would NEVER be pfsense on vlan 5 address.. Source would be vlan 5 net..
What did you set netgears IP too? You said you changed it.
What is the hardware of your pfsense box?
6DB311That doesn't resolve as maker of networking gear..
-
@johnpoz said in Netgear/Vlans/Pfsense:
Clear your arp table
cleared and not returned
cannot ping any 192.168.1 or 192.168.5
i have the following arp entries now
192.168.5.1
192.168.5.255
224.0.0.22
224.0.0.251
224.0.0.252
239.255.255.250
255.255.255.255 -
Ok that is better!
So simple test is sniff on pfsense vlan interface while you ping it from the client.. Do you see the ping?
BTW what hardware is the nic on pfsense? that mac doesn't resolve to anyone..
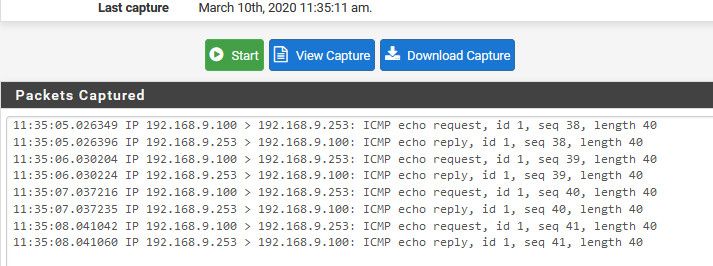
-
@johnpoz said in Netgear/Vlans/Pfsense:
Do you see the ping?
16:37:10.374829 IP 192.168.5.50 > 192.168.5.1: ICMP echo request, id 1, seq 36, length 40 16:37:15.321366 IP 192.168.5.50 > 192.168.5.1: ICMP echo request, id 1, seq 37, length 40 16:37:20.337599 IP 192.168.5.50 > 192.168.5.1: ICMP echo request, id 1, seq 38, length 40 16:37:25.318515 IP 192.168.5.50 > 192.168.5.1: ICMP echo request, id 1, seq 39, length 40 16:37:26.442815 IP 192.168.5.50.53865 > 239.255.255.250.1900: UDP, length 174 16:37:27.009842 IP 192.168.5.50.60396 > 192.168.5.1.53: UDP, length 46 16:37:27.463007 IP 192.168.5.50.53865 > 239.255.255.250.1900: UDP, length 174 16:37:28.011221 IP 192.168.5.50.60396 > 192.168.5.1.53: UDP, length 46 16:37:28.465757 IP 192.168.5.50.53865 > 239.255.255.250.1900: UDP, length 174 16:37:29.013961 IP 192.168.5.50.60396 > 192.168.5.1.53: UDP, length 46 16:37:29.468473 IP 192.168.5.50.53865 > 239.255.255.250.1900: UDP, length 174 16:37:31.022413 IP 192.168.5.50.60396 > 192.168.5.1.53: UDP, length 46 16:37:32.811702 ARP, Request who-has 192.168.5.1 (6c:b3:11:1c:6c:77) tell 192.168.5.50, length 46 16:37:32.811707 ARP, Reply 192.168.5.1 is-at 6c:b3:11:1c:6c:77, length 28 16:37:35.033636 IP 192.168.5.50.60396 > 192.168.5.1.53: UDP, length 46 -
@r79c said in Netgear/Vlans/Pfsense:
16:37:10.374829 IP 192.168.5.50 > 192.168.5.1: ICMP echo request, id 1, seq 36, length 40
16:37:15.321366 IP 192.168.5.50 > 192.168.5.1: ICMP echo request, id 1, seq 37, length 40Yup... So lets see your rules on on vlan 5 again... And do you have any rules in floating?
-
https://ibb.co/rs4tG8r
https://ibb.co/zVDwqW4
-
So your blocking it with pfblocker... Disable those rules on floating as test!
That firehol list contains rfc1918 address space!!
-
Ok I disabled those rules and disabled pfblocker for the time being.
I set those rules up when I set up pfblocker but I was never 100% competent on how it is setup, I only set it up about two weeks ago....
-
And - are you pinging?
-
-
Well your firewall rule that allows all of IPv4 show hits... And your seeing the traffic actually hit pfsense vlan interface... You were sniffing on the vlan interface right!! not lan..
So lets see your routing table..
Unless you where not sniffing on vlan 5 interface it makes no sense to be honest..
Is pfsense a VM? Or this is a physical box... What is the nic of this box? Why does the mac of the 5.1 not show as known company?
-
@johnpoz said in Netgear/Vlans/Pfsense:
You were sniffing on the vlan interface right!!
yes
routing table
Destination Gateway Flags Use Mtu Netif Expire 0.0.0.0/1 10.8.2.1 UGS 2057 1500 ovpnc3 default 192.168.10.1 UGS 112 1500 igb0 10.8.2.0/24 10.8.2.1 UGS 0 1500 ovpnc3 10.8.2.1 link#10 UH 7060 1500 ovpnc3 10.8.2.19 link#10 UHS 0 16384 lo0 10.8.3.1 link#8 UH 7074 1500 ovpnc1 10.8.3.10 link#8 UHS 0 16384 lo0 10.8.8.0/24 10.8.8.1 UGS 0 1500 ovpnc2 10.8.8.1 link#9 UH 7078 1500 ovpnc2 10.8.8.4 link#9 UHS 0 16384 lo0 127.0.0.1 link#4 UH 1350047 16384 lo0 128.0.0.0/1 10.8.2.1 UGS 57242 1500 ovpnc3 192.168.1.0/24 link#2 U 815693 1500 igb1 192.168.1.1 link#2 UHS 0 16384 lo0 192.168.5.0/24 link#7 U 1927 1500 igb1.5 192.168.5.1 link#7 UHS 0 16384 lo0 192.168.10.0/24 link#1 U 0 1500 igb0 192.168.10.1 6c:b3:11:1c:6c:76 UHS 53316 1500 igb0 192.168.10.3 link#1 UHS 0 16384 lo0 217.146.82.191/32 192.168.10.1 UGS 24899 1500 igb0 -
Well that looks correct.. you have 192.168.5 and using the interface..
And it was seeing traffic - your not running any sort of IPS are you?
Can you post output of
cat /tmp/rules.debug
-
-
Dude!!!! you need to give this info.... Disable it!!! What do its logs say..
-
@johnpoz said in Netgear/Vlans/Pfsense:
So maybe its just an issue with this nic and vlans
perhaps the card that I bought off Amazon does not support VLAN's, although I presumed it did. Also I saw that pfsense only shows interfaces that VLAN's can be created on so if the card didn't support VLAN's it should not show in the pfsense drop down.
igb0: flags=8843<UP,BROADCAST,RUNNING,SIMPLEX,MULTICAST> metric 0 mtu 1500 options=6400bb<RXCSUM,TXCSUM,VLAN_MTU,VLAN_HWTAGGING,JUMBO_MTU,VLAN_HWCSUM,VLAN_HWTSO,RXCSUM_IPV6,TXCSUM_IPV6> ether 6c:b3:11:1c:6c:76 hwaddr 6c:b3:11:1c:6c:76 inet6 fe80::6eb3:11ff:fe1c:6c76%igb0 prefixlen 64 scopeid 0x1 inet6 fdc0:13c1:78f1:0:6eb3:11ff:fe1c:6c76 prefixlen 64 autoconf inet 192.168.10.3 netmask 0xffffff00 broadcast 192.168.10.255 nd6 options=23<PERFORMNUD,ACCEPT_RTADV,AUTO_LINKLOCAL> media: Ethernet autoselect (1000baseT <full-duplex>) status: active igb1: flags=8843<UP,BROADCAST,RUNNING,SIMPLEX,MULTICAST> metric 0 mtu 1500 options=6500bb<RXCSUM,TXCSUM,VLAN_MTU,VLAN_HWTAGGING,JUMBO_MTU,VLAN_HWCSUM,VLAN_HWFILTER,VLAN_HWTSO,RXCSUM_IPV6,TXCSUM_IPV6> ether 6c:b3:11:1c:6c:77 hwaddr 6c:b3:11:1c:6c:77 inet 192.168.1.1 netmask 0xffffff00 broadcast 192.168.1.255 inet6 fe80::1:1%igb1 prefixlen 64 scopeid 0x2 nd6 options=21<PERFORMNUD,AUTO_LINKLOCAL> media: Ethernet autoselect (1000baseT <full-duplex>) status: active enc0: flags=0<> metric 0 mtu 1536 nd6 options=21<PERFORMNUD,AUTO_LINKLOCAL> groups: enc lo0: flags=8049<UP,LOOPBACK,RUNNING,MULTICAST> metric 0 mtu 16384 options=600003<RXCSUM,TXCSUM,RXCSUM_IPV6,TXCSUM_IPV6> inet6 ::1 prefixlen 128 inet6 fe80::1%lo0 prefixlen 64 scopeid 0x4 inet 127.0.0.1 netmask 0xff000000 nd6 options=21<PERFORMNUD,AUTO_LINKLOCAL> groups: lo pflog0: flags=100<PROMISC> metric 0 mtu 33160 groups: pflog pfsync0: flags=0<> metric 0 mtu 1500 groups: pfsync syncpeer: 224.0.0.240 maxupd: 128 defer: on syncok: 1 igb1.5: flags=88843<UP,BROADCAST,RUNNING,SIMPLEX,MULTICAST,STATICARP> metric 0 mtu 1500 options=600003<RXCSUM,TXCSUM,RXCSUM_IPV6,TXCSUM_IPV6> ether 6c:b3:11:1c:6c:77 inet6 fe80::6eb3:11ff:fe1c:6c77%igb1.5 prefixlen 64 scopeid 0x7 inet 192.168.5.1 netmask 0xffffff00 broadcast 192.168.5.255 nd6 options=23<PERFORMNUD,ACCEPT_RTADV,AUTO_LINKLOCAL> media: Ethernet autoselect (1000baseT <full-duplex>) status: active vlan: 5 vlanpcp: 0 parent interface: igb1 groups: vlan ovpnc1: flags=8051<UP,POINTOPOINT,RUNNING,MULTICAST> metric 0 mtu 1500 options=80000<LINKSTATE> inet6 fe80::6eb3:11ff:fe1c:6c76%ovpnc1 prefixlen 64 scopeid 0x8 inet 10.8.3.10 --> 10.8.3.1 netmask 0xffffff00 nd6 options=21<PERFORMNUD,AUTO_LINKLOCAL> groups: tun openvpn Opened by PID 7054 ovpnc2: flags=8051<UP,POINTOPOINT,RUNNING,MULTICAST> metric 0 mtu 1500 options=80000<LINKSTATE> inet6 fe80::6eb3:11ff:fe1c:6c76%ovpnc2 prefixlen 64 scopeid 0x9 inet 10.8.8.4 --> 10.8.8.1 netmask 0xffffff00 nd6 options=21<PERFORMNUD,AUTO_LINKLOCAL> groups: tun openvpn Opened by PID 82209 ovpnc3: flags=8051<UP,POINTOPOINT,RUNNING,MULTICAST> metric 0 mtu 1500 options=80000<LINKSTATE> inet6 fe80::6eb3:11ff:fe1c:6c76%ovpnc3 prefixlen 64 scopeid 0xa inet 10.8.2.19 --> 10.8.2.1 netmask 0xffffff00 nd6 options=21<PERFORMNUD,AUTO_LINKLOCAL> groups: tun openvpn Opened by PID 33738 -
You've made a lot of changes, I suggest you reboot the firewall to make sure the pfb/snort is off.
-
Well I am out of ideas to be honest... You say your sniffing on your vlan, and seeing the ping request.. Your rule you posted shows your allowing it... And your showing hits..
So makes no sense..
But your running IPS, and you had pfblocker with rules that would block rfc1918 space, etc..
Your nic is some no name???, never heard off - and its mac address does not even lookup... So maybe its just an issue with this nic and vlans... Lets see a ifconfig output from pfsense. I want to see what is showing for options on your igb1...
example - here is an interface I am running vlans on.
igb2: flags=8843<UP,BROADCAST,RUNNING,SIMPLEX,MULTICAST> metric 0 mtu 1500 options=6500bb<RXCSUM,TXCSUM,VLAN_MTU,VLAN_HWTAGGING,JUMBO_MTU,VLAN_HWCSUM,VLAN_HWFILTER,VLAN_HWTSO,RXCSUM_IPV6,TXCSUM_IPV6> ether 00:08:a2:0c:e6:20 hwaddr 00:08:a2:0c:e6:20 inet6 fe80::208:a2ff:fe0c:e620%igb2 prefixlen 64 scopeid 0x3 inet 192.168.2.253 netmask 0xffffff00 broadcast 192.168.2.255 nd6 options=21<PERFORMNUD,AUTO_LINKLOCAL> media: Ethernet autoselect (1000baseT <full-duplex>) status: active igb2.4: flags=8843<UP,BROADCAST,RUNNING,SIMPLEX,MULTICAST> metric 0 mtu 1500 options=600003<RXCSUM,TXCSUM,RXCSUM_IPV6,TXCSUM_IPV6> ether 00:08:a2:0c:e6:20 inet6 fe80::208:a2ff:fe0c:e620%igb2.4 prefixlen 64 scopeid 0xb inet 192.168.4.253 netmask 0xffffff00 broadcast 192.168.4.255 nd6 options=21<PERFORMNUD,AUTO_LINKLOCAL> media: Ethernet autoselect (1000baseT <full-duplex>) status: active vlan: 4 vlanpcp: 0 parent interface: igb2 groups: vlan igb2.6: flags=8843<UP,BROADCAST,RUNNING,SIMPLEX,MULTICAST> metric 0 mtu 1500 options=600003<RXCSUM,TXCSUM,RXCSUM_IPV6,TXCSUM_IPV6> ether 00:08:a2:0c:e6:20 inet6 fe80::208:a2ff:fe0c:e620%igb2.6 prefixlen 64 scopeid 0xc inet 192.168.6.253 netmask 0xffffff00 broadcast 192.168.6.255 nd6 options=21<PERFORMNUD,AUTO_LINKLOCAL> media: Ethernet autoselect (1000baseT <full-duplex>) status: active vlan: 6 vlanpcp: 0 parent interface: igb2 groups: vlanOnly other thing would be to run tcpdump on pfsense with -e flag so you can see the tagging is happening or not happening... Maybe its answering without the tag???? So your sniff on vlan wouldn't show it - that is guess..
But sure a reload of your rules, or reboot couldn't hurt.
From pfsense - sniff on your vlan 5, and try to ping your client 192.168.5.50..
-
@johnpoz said in Netgear/Vlans/Pfsense:
So maybe its just an issue with this nic and vlans
Perhaps it is, I presumed the card that I purchased off amazon supported vlan's and the pfsense drop down showed the card as an interface that could create vlans on...
igb0: flags=8843<UP,BROADCAST,RUNNING,SIMPLEX,MULTICAST> metric 0 mtu 1500 options=6400bb<RXCSUM,TXCSUM,VLAN_MTU,VLAN_HWTAGGING,JUMBO_MTU,VLAN_HWCSUM,VLAN_HWTSO,RXCSUM_IPV6,TXCSUM_IPV6> ether 6c:b3:11:1c:6c:76 hwaddr 6c:b3:11:1c:6c:76 inet6 fe80::6eb3:11ff:fe1c:6c76%igb0 prefixlen 64 scopeid 0x1 inet6 fdc0:13c1:78f1:0:6eb3:11ff:fe1c:6c76 prefixlen 64 autoconf inet 192.168.10.3 netmask 0xffffff00 broadcast 192.168.10.255 nd6 options=23<PERFORMNUD,ACCEPT_RTADV,AUTO_LINKLOCAL> media: Ethernet autoselect (1000baseT <full-duplex>) status: active igb1: flags=8843<UP,BROADCAST,RUNNING,SIMPLEX,MULTICAST> metric 0 mtu 1500 options=6500bb<RXCSUM,TXCSUM,VLAN_MTU,VLAN_HWTAGGING,JUMBO_MTU,VLAN_HWCSUM,VLAN_HWFILTER,VLAN_HWTSO,RXCSUM_IPV6,TXCSUM_IPV6> ether 6c:b3:11:1c:6c:77 hwaddr 6c:b3:11:1c:6c:77 inet 192.168.1.1 netmask 0xffffff00 broadcast 192.168.1.255 inet6 fe80::1:1%igb1 prefixlen 64 scopeid 0x2 nd6 options=21<PERFORMNUD,AUTO_LINKLOCAL> media: Ethernet autoselect (1000baseT <full-duplex>) status: active enc0: flags=0<> metric 0 mtu 1536 nd6 options=21<PERFORMNUD,AUTO_LINKLOCAL> groups: enc lo0: flags=8049<UP,LOOPBACK,RUNNING,MULTICAST> metric 0 mtu 16384 options=600003<RXCSUM,TXCSUM,RXCSUM_IPV6,TXCSUM_IPV6> inet6 ::1 prefixlen 128 inet6 fe80::1%lo0 prefixlen 64 scopeid 0x4 inet 127.0.0.1 netmask 0xff000000 nd6 options=21<PERFORMNUD,AUTO_LINKLOCAL> groups: lo pflog0: flags=100<PROMISC> metric 0 mtu 33160 groups: pflog pfsync0: flags=0<> metric 0 mtu 1500 groups: pfsync syncpeer: 224.0.0.240 maxupd: 128 defer: on syncok: 1 igb1.5: flags=88843<UP,BROADCAST,RUNNING,SIMPLEX,MULTICAST,STATICARP> metric 0 mtu 1500 options=600003<RXCSUM,TXCSUM,RXCSUM_IPV6,TXCSUM_IPV6> ether 6c:b3:11:1c:6c:77 inet6 fe80::6eb3:11ff:fe1c:6c77%igb1.5 prefixlen 64 scopeid 0x7 inet 192.168.5.1 netmask 0xffffff00 broadcast 192.168.5.255 nd6 options=23<PERFORMNUD,ACCEPT_RTADV,AUTO_LINKLOCAL> media: Ethernet autoselect (1000baseT <full-duplex>) status: active vlan: 5 vlanpcp: 0 parent interface: igb1 groups: vlan ovpnc1: flags=8051<UP,POINTOPOINT,RUNNING,MULTICAST> metric 0 mtu 1500 options=80000<LINKSTATE> inet6 fe80::6eb3:11ff:fe1c:6c76%ovpnc1 prefixlen 64 scopeid 0x8 inet 10.8.3.10 --> 10.8.3.1 netmask 0xffffff00 nd6 options=21<PERFORMNUD,AUTO_LINKLOCAL> groups: tun openvpn Opened by PID 7054 ovpnc2: flags=8051<UP,POINTOPOINT,RUNNING,MULTICAST> metric 0 mtu 1500 options=80000<LINKSTATE> inet6 fe80::6eb3:11ff:fe1c:6c76%ovpnc2 prefixlen 64 scopeid 0x9 inet 10.8.8.4 --> 10.8.8.1 netmask 0xffffff00 nd6 options=21<PERFORMNUD,AUTO_LINKLOCAL> groups: tun openvpn Opened by PID 82209 ovpnc3: flags=8051<UP,POINTOPOINT,RUNNING,MULTICAST> metric 0 mtu 1500 options=80000<LINKSTATE> inet6 fe80::6eb3:11ff:fe1c:6c76%ovpnc3 prefixlen 64 scopeid 0xa inet 10.8.2.19 --> 10.8.2.1 netmask 0xffffff00 nd6 options=21<PERFORMNUD,AUTO_LINKLOCAL> groups: tun openvpn Opened by PID 33738just to recap the NAT automatic rules have added 192.168.1.0/24 and 192.168.5.0/24
can I just be sure that I'm not missing a specific mapping that needs to be added???? like you have said before would the automatic rule be enough???