Help with physical interfaces and VLANs
-
Hi, I am planning a new home pfsense install on an HP T730 that will have 5 physical ethernet ports. Obviously one is WAN. However I am not sure how to set up the others. If I will have an outbuilding that will contain a managed switch and a wifi AP with three VLANs that will connect to one physical port on the pfsense box, how do I set up that port? Can I assign mutliple VLANs to the port? Each VLAN should have its own subnet. For example, those VLANs would be for Wifi, Guest Wifi and iOT devices, all different subnets with pfsense doing the dhcp for each. Would I create the VLANs and assign them each to their physical port? And then under interfaces, assign them each with the OPT# and the VLAN? Would the outbuilding switch be configured with an IP in the same subnet as the pfsense box ?
-
You probably have this post in the incorrect topic for what you're asking, maybe a mod can move it later...
Anyway, you can either run your VLANs on 1 interface, or you can break them out on their own interfaces. If you don't actually need them to talk to each other, separate interfaces is really easy. But, if for say, you want a common wireless network, both for mixed "trusted" LAN traffic and "untrusted" GUEST traffic, you should run them both over the same interface, and in turn, the same wire. I don't want to confuse you, but you can also allow talking between all networks and all interfaces, on either setup, simply by using appropriate firewall rules.
So, if I were you, just to keep things simple, use just the LAN interface, and setup your VLANs in pfsense to use the LAN interface as their parent interfaces. It's the first box when you config a new or existing VLAN.
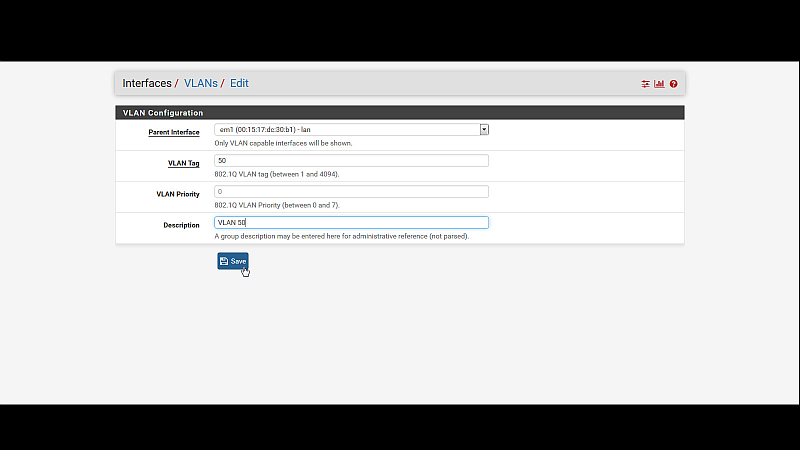
Then, on your switch, you have to setup your VLANs correctly. When it's all setup correctly, everything should work just fine. You might have to consult your switch user manual, or online resources, to figure out the switch settings.
The answer to your question, yes you can run multiple VLANs off of a common interface. Be warned, if they are all high-traffic networks, you're splitting up the speed of the single port between that many VLAN networks. In most home settings, this is ok to do.
Hope that helps!
Jeff
-
Thanks, yes this should probably be moved, when I saw "virtualization" I immediately thought it was for VLANs lol.
As far as putting everything on one physical LAN interface, would that impact the performance either hardware/cpu wise or bandwidth wise on the pfsense box?
-
All tagged VLANs on one physical interface will share the same bandwidth (probably gigabit).
Whether that is or is not an issue depends on the traffic levels in play.
It is often more convenient to use VLANs but you will have to decide for yourself whether you need more than one gigabit pipe for your traffic.
If you are not moving, say, 600Mbits/sec consistently I wouldn't worry about it. Especially if your NIC drivers can use multiple cores for multiple queues.
-
If you have the physical nics, and you have the ports on your switch - its better use 1 gig for each vlan since as mentioned vlans on the same physical port share the bandwidth. And if your doing intervlan routing and traffic is routing over the vlans on the same physical interface your hairpinning your traffic.
So if you have the physical media why not use it.. If you don't have enough for all - spread your vlans out over different physical interfaces that makes the most sense for traffic flow, put some lower use vlans on the same physical for example - that don't really talk to each other if you can.
For example my wireless vlans share the same physical interface on my router.. Since these are not even capable of gig anyway, So sharing a physical gig interface is less likely to cause a bottle neck. And wireless clients are never talking to each other with anything that would require any real bandwidth at all..
-
Thanks, yes that is why I put the quad port NIC in it, I would like to use all ports. So lets say on igb0 (LAN), I can put vlan 100 for lan mgmnt. On igb1, I can put vlan 200 for my in-law suite outbuilding. Everything on that interface/vlan will be coming from one wire and can all be vlan 200 with no access to anything else but internet. On igb2 I can put vlan 300 for guest wifi, vlan 400 for main wifi, vlan 500 for iOT and vlan 600 for a/v. The last interfance, igb3, can be future use. Does that sound ok? or am I over engineering things? Would/should each vlan have their own subnet?
-
Yes - each VLAN will be a different broadcast domain (the whole point) so they all need their own subnets.
Again, it depends on traffic levels, not the number of VLANs.
I have pretty much all of my VLANs here on one 2 x 1G LACP to my switching gear.
Some things, like the hypervisor to NAS shared storage are direct-attach for obvious reasons.
Never give it a second thought.
-
Ok I think I understand that enough to be dangerous. Now I need assistance with configuring my LAN and VLAN100 to get internet access. For testing purposes, lets pretend my Linksys router is the cable modem. I have my pfsense WAN plugged into my Linksys router. Pfsense has a WAN DHCP of 192.168.100.100 and WAN gateway of 192.168.100.1 (that is the Linksys router). The LAN interface IP is 192.168.200.1, with DHCP on the same subnet. I have a PC on that VLAN that obtained address 192.168.200.10, but the PC cannot access the internet. What gateway should be on the LAN interface or what am I missing? Do I need a firewall rule to allow VLAN100 internet access across the WAN?
-
@BlankSpace said in Help with physical interfaces and VLANs:
Do I need a firewall rule to allow VLAN100 internet access across the WAN?
You would need to create rule(s) yes - only lan gets default any rules, if you fire up another interface or vlan there will be no rules.. To get things working for testing you can just duplicate your lan rule any any with the new vlan net as source vs lan net. Once your sure things are working you can lock stuff down how you want.
-
I am not even sure the WAN side of things has internet. Should I be able to ping WAN hosts (google.com) from the CLI shell? because I cannot.
-
Well yeah pfsense needs internet to be able to give it to clients behind ;)
Does your pfsense show its wan up, it will tell you if it can reach its gateway, even if just your other router.
You sure when you setup your lan 192.168.200 you didn't use a /16 mask did you? if your wan mask is /24 which should be common your lan should be /24 as well - if 16 it would overlap your wan and then yeah things would have issues.
-
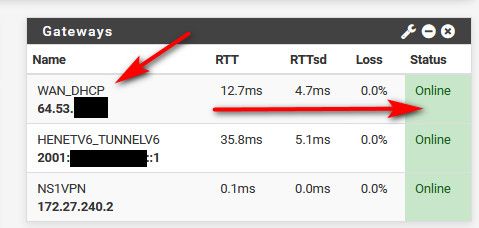
The WAN_DHCP gateway (192.168.100.1) is listed as online, then there is another GW_LAN (default) (192.168.0.1) that is offline.
-
@BlankSpace said in Help with physical interfaces and VLANs:
GW_LAN (default) (192.168.0.1) that is offline.
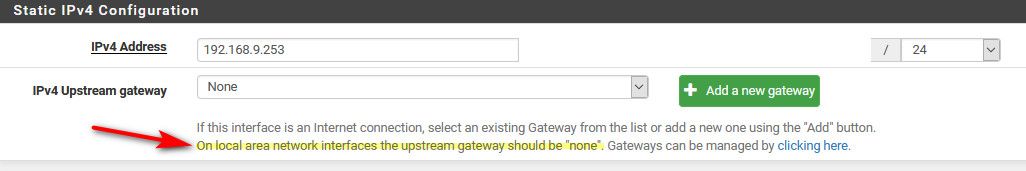
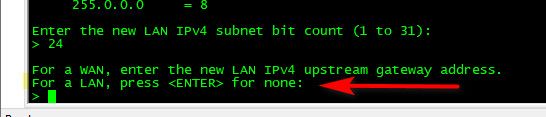
Well that is WRONG!!! you wouldn't set a gateway on your lan! I never understand how users do this - it doesn't ask you to do that... And even if you set one up, it tells you shouldn't
-
In the LAN interface config, the IPv4 Upstream gateway is listed as "none", but I think I have more problems then that lol. If I can't ping internet hosts from the WAN. Also my LAN is 192.168.200.0/24 not 192.168.0.1.
-
Post up your gateways... You shouldn't have any gateways other than your wan, which I assume you got from dhcp... Your sure pfsense wan is actually 192.168.100
-
Ok I deleted the 192.168.0.1 gateway. The only one now is the WAN which was from DHCP as you stated. It is listed as WAN_DHCP, WAN, 192.168.100.1 192.168.100.1 Interface WAN_DHCP Gateway.
-
Something going on with the WAN tho, can't ping Internet, destination unreachable.
-
@BlankSpace said in Help with physical interfaces and VLANs:
WAN_DHCP, WAN, 192.168.100.1 192.168.100.1
can you you ping that? From pfsense
You can not ping say 8.8.8.8 from pfsense or you can not resolve www.google.com
-
Yes I can ping that from pfsense shell and no, I cannot ping 8.8.8.8 or resolve google.com.
-
what about 8.8.8.8
That 192.168.100.1 is your current router?