Help with physical interfaces and VLANs
-
Thank you for all of the assistance, first time with pfsense here. So "technically" I can drop this in off my cable modem and should at least have one interface and vlan up and running.
-
It should yes - keep in mind that almost always when you change something connected to a cable modem, ie swap out your router for pfsense you would have to reboot your router. I would disconnect your router... Power cycle your cable modem... Wait for it to show online, then connect pfsense and it should grab a public wan IP.. And then yeah all your networks behind should be up and running.. that have rules to allow :)
Auto should work - but I have seen it be finicky myself sometimes.. Especially if you have something else setup as a gateway - where I saw it have a problem was when I had a downstream router setup (ie another gateway)... But if your not multiwan or whatever doesn't hurt to hard code it.
-
@johnpoz said in Help with physical interfaces and VLANs:
...keep in mind that almost always when you change something connected to a cable modem, ie swap out your router for pfsense you would have to reboot your router. I would disconnect your router... Power cycle your cable modem... Wait for it to show online, then connect pfsense and it should grab a public wan IP..
Found that out last night, actually had the cable company come and replace my modem cuz it took a shit when I put it in bridge mode. It was a Pace D5001. I plan on upgrading to gig internet (500/50 now) so they gave me a docsis3.1 Arris CM8200a which is no frills bridge, easy to work with.
Now gotta get my Netgear managed switches figured out with the VLANs and I'll be set.
-
Nice... How much a bump in cost for the move to gig, and is it 1k/1k - or is it asymmetrical? I'm also on 500/50 plan - but really want the more up, down 500 is more than enough... But could use more up.. Not worth the cost bump for 1k/100 currently - if it was 1k/1k - would be all over it ;)
Not so much the monthly cost - but my current modem won't do gig.. It handles 500 without issue, but not really looking to drop money on a new modem, and monthly bump for 50 more up... I don't need the down.. And sure wouldn't be happy paying the extra monthly if couldn't actually get the gig down, even if don't really need it ;) hehehe
I wish they had a 500/500 plan or 500/200 would be freaking sweet! That would be a sweet spot for me...
Enjoy your new speed and pfsense - your going to love it!
-
It'd still be 50 up which sucks. I think they also increase the total up/down max data from 4000gb to 6000gb, which I'll probably never hit anyway. I believe its around 20 more a month. I do, however, almost always get 50 up when testing.
-
I'm on no cap.. So not something I would have to worry about.. I do about 2TB a month..
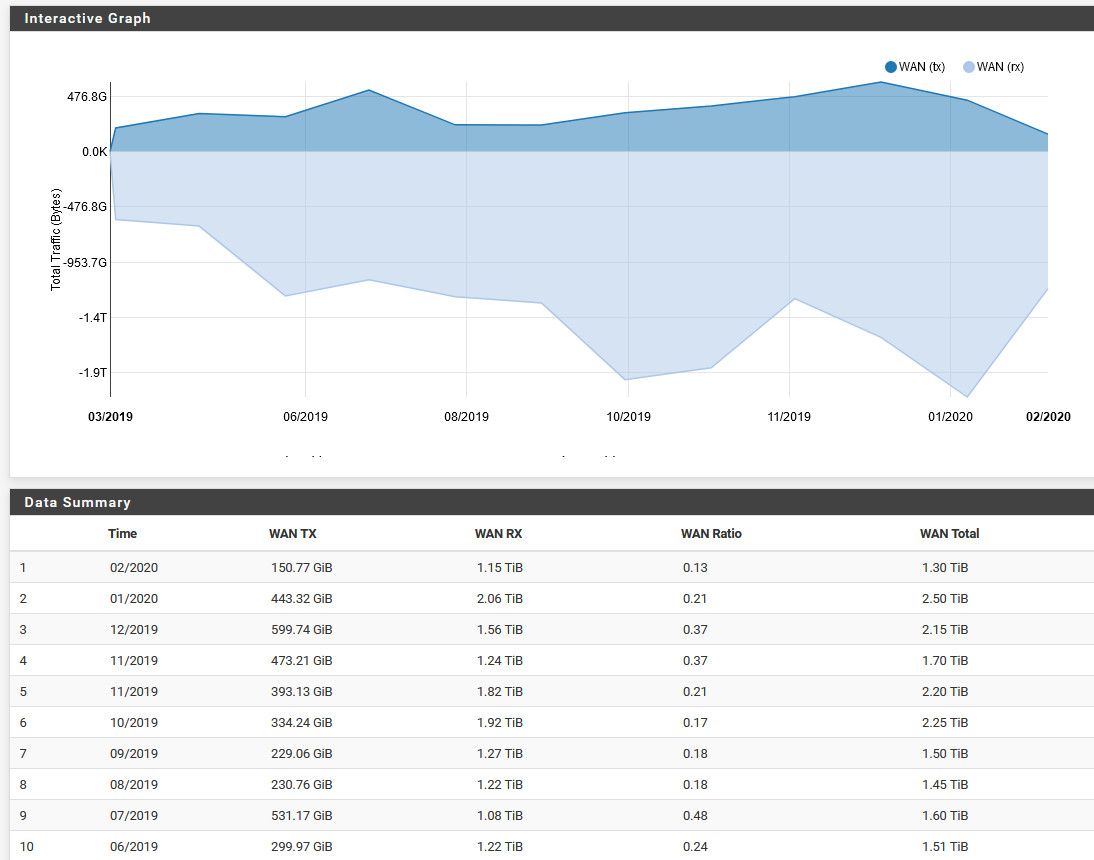
But curious what the next couple of months will be like - work just put us on work from home for next few weeks. Not sure how long that will last with all this virus stuff, sure hope it gets back to normal sooner vs later..
And all friends and family all going to be home more, etc. So sure my plex server will be seeing more traffic ;)
-
holy #)(U% that's alot! I'm in PA and the gov just shut down all schools for two weeks so I got a 6yo and 8yo who'll be home. My wife is also on work from home, she works for a hospital and they do not want anyone in the office who doesn't need to be.
-
Next question as I try to draw my future topology for the 1000th time. Management switches - the IP's of those switches only matter to be able to manage them, correct? So if my main LAN and management vlan is vl100 192.168.200.0/24 - ALL my managed switches should have an IP in that subnet, correct? It doesn't matter what VLANs are assigned to ports on those switches as long as one is the trunk with vl100?
-
Generally the only layer 3 interface on a managed layer 2 switch is for management, yes.
-
@Derelict said in Help with physical interfaces and VLANs:
Generally the only layer 3 interface on a managed layer 2 switch is for management, yes.
So am I correct in thinking that as I go from my Pfsense box with 4 LAN interfaces, I can put each interface to separate ports on my main, lets call it my "BDM" 16 port managed switch. Then from that BDM switch, I'll go out one wire each to what I'll call my "IDE" managed switches.
-
Just put the management interfaces for your switches on a VLAN you can access from your management workstation.
Just like any other host you want to connect to.
You will find different capabilities in switching gear depending on what you get. Some have to be managed on the untagged VLAN, some allow you to set the VLAN of the management interface. it depends.
It all boils down to just setting an IP address, subnet mask, and default gateway of the management interface though. DHCP can be used if that fits with your network design.
-
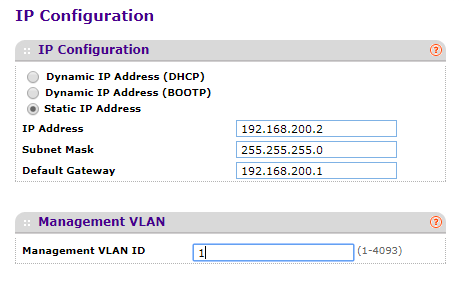
Ok, in my Netgear I can set it to any vlan. So if my main lan is vl100, which will only have my main pc's on it, I should set that to 100 and give it the required IP info from vl100. And every other switch will be the same way with different IP's, most likely sequentially numbered... 192.168.200.3, 192.168.200.4, etc.
-
Depends. I do not work for Netgear. I would expect that to need to be set to VLAN 100 though if you are accessing that interface from VLAN 100.
-
Now that I have my VLANs designated, I understand pfsense is default deny for everything. So for any VLAN that I only want to be able to access the internet, all I need is a pass rule from that VLAN net to WAN net ? Everything else to anything else is default blocked, correct?
-
No.
WAN net is not the internet. any is the internet.
You need to block the destinations you do not want them to have access to then pass everything else (the internet).
-
@Derelict said in Help with physical interfaces and VLANs:
No.
WAN net is not the internet. any is the internet.
You need to block the destinations you do not want them to have access to then pass everything else (the internet).
I would want everything blocked but the Internet so would I need to create a block rule to every other VLAN and then change WAN net to "any"?
-
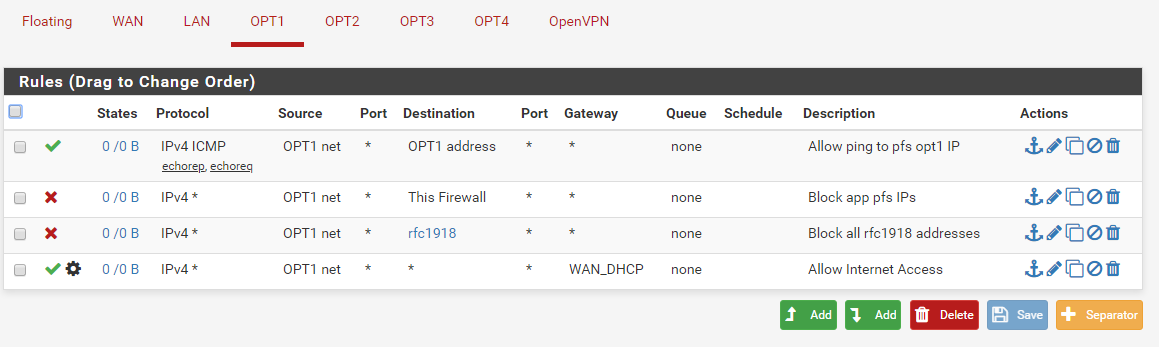
Found some pointers from johnpoz in another thread.
How's this look:
-
fine if This Firewall and rfc1918 cover everything you don't want them to be able to access.
-
So I take it they are going to use external dns?
-
@Derelict said in Help with physical interfaces and VLANs:
fine if This Firewall and rfc1918 cover everything you don't want them to be able to access.
Well, I don't want them accessing anything on pfs other then ping their gw. And my alias of rfc1918 includes all private networks. I think that should work?