pfSense NAT not working, nor showing related incoming packet in Packet Capture (even yet it is on wire) or in logs
-
@icansoft said in pfSense NAT not working, nor showing related incoming packet in Packet Capture (even yet it is on wire) or in logs:
Which makes me wonder, how comes that, the Mikrotik router does the NAT fine, and the pfSense not ?
Now we're talking. Exactly!
Factory defaulted Mikrotik with a single rule added works. No other specific config due to whatever the ISP might be doing. So if that router handles it well, I do expect the pfSense to do the same - but it seems it needs to be configured somehow more. Any ideas ?
Somehow I smell "darkmagic(tm)". Almost sounds like some kind of upnp/natpnp at work that automagically requests the port upstream from the UBNT device, which in turn maps the port, which in turn leads to the package being delivered. As I don't play around with Mikrotik that much, I don't know if that's what they do per default, but that would be one guess (some kinda NAT punch technique).
-
@icansoft said in pfSense NAT not working, nor showing related incoming packet in Packet Capture (even yet it is on wire) or in logs:
Factory defaulted Mikrotik with a single rule added works.
None of us would be able to understand why this would be unless your ISP had done port forwarding to it's IP address.. which your pfsense box is obviously not obtaining. I.E. if your Microtik box got 192.168.1.60 and they set up a port forward to that box then your pfsense would also have to get .60 in order to receive that traffic. Since it does not we can only guess.
-
@JeGr said in pfSense NAT not working, nor showing related incoming packet in Packet Capture (even yet it is on wire) or in logs:
Almost sounds like some kind of upnp/natpnp at work that automagically requests the port upstream
^^ or that..
-
@chpalmer said in pfSense NAT not working, nor showing related incoming packet in Packet Capture (even yet it is on wire) or in logs:
@icansoft said in pfSense NAT not working, nor showing related incoming packet in Packet Capture (even yet it is on wire) or in logs:
Factory defaulted Mikrotik with a single rule added works.
None of us would be able to understand why this would be unless your ISP had done port forwarding to it's IP address.. which your pfsense box is obviously not obtaining. I.E. if your Microtik box got 192.168.1.60 and they set up a port forward to that box then your pfsense would also have to get .60 in order to receive that traffic. Since it does not we can only guess.
@chpalmer also has a good point. Does your mikrotik router get the same IP every time you plug it in behind the UBNT device? Does it also work every time? What if you shut it down and statically configure pfSense' WAN to the IP that the mikrotik had before?
@chpalmer said in pfSense NAT not working, nor showing related incoming packet in Packet Capture (even yet it is on wire) or in logs:
^^ or that..
that's what happens if we write at the same time, hehe

-
Somehow I smell "darkmagic(tm)". Almost sounds like some kind of upnp/natpnp at work that automagically requests the port upstream from the UBNT device, which in turn maps the port, which in turn leads to the package being delivered.
Right, right, I'm going to investigate. Not that I know Mikrotik any better to be able to answer this.
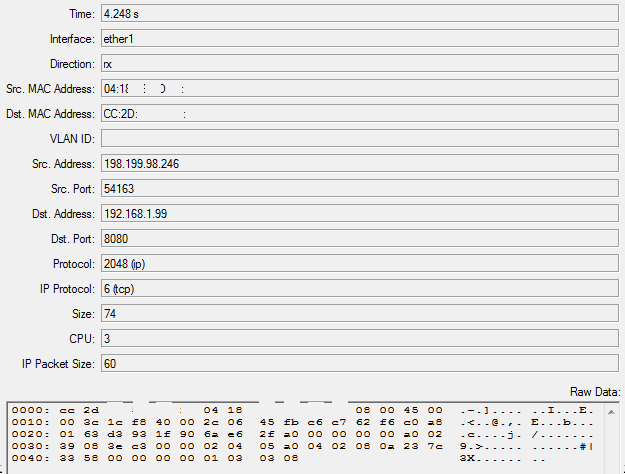
Anyway - have a look at the captured packet on top, it comes with the Source IP as original and unmodified, and target is the IP of the only device on the UBNT (ISP) subnet. If that is that Mikrotik (or my NB for that matter), the packet is captured... if it is pfSense, no luck.
The ISP has no idea what is on my network, and I've just verified it by changing MAC on the Mikrotik, it gets assignment from UBNT (different .ip) and yet it DST-NATs OK.
-
OK by thinking this through (and thank you all for helping me out to do so),
there definitelly must be some sort of detection mechanism on the ISP side.I think @chpalmer has the best answer, which makes the best of the sense, ... yet there must be something which I'm missing (and therefore it would be hard for others to figure it out as well).
I'll write an email with a query to the ISP, on how the configuration is done.
Perharps they somehow detect the device connected to a client of theirs, and it just happen that the pfSense is not handled properly on the ISP's side.
No idea if I ever get a response though.Anyway, I would consider the case closed. There is no more that could be done on the pfSense side.
Many thanks to all, you guys helped.
Please eventually move this thread to a more proper topic, if required. -
@icansoft said in pfSense NAT not working, nor showing related incoming packet in Packet Capture (even yet it is on wire) or in logs:
If that is that Mikrotik (or my NB for that matter), the packet is captured... if it is pfSense, no luck.
Yeah we get that. But even UBNT has no automagic guessing crystal ball as to automagically guess/read, what it will hand out your router as DHCP address and again automagically forward every packet to that address. Also: if you would attach that line from your UBNT to a switch and then to both the pfSense and mikrotik router, it would hand out two addresses as that's what DHCP does. So where should it route your packets to? That's why I'm guessing strange things happening like some UPnP/NATPnP magic.
Various home/SOHO routers like those AVM boxes have an option like "allow devices on the LAN to ask for port forwardings via UPnP". If something like this is working on the Mikrotik (as in you create a forwarding and it sends the request upstream), no wonder it "just works". But as my example above: what would happen if you'd attach multiple routers behind it? The box could never just assume "send anything to xy" with more then one DHCP client.
So either the Mikrotik is doing some UPnP (or other magic) that the UBNT box is allowing or it gets the same IP everytime and your ISP configured the box to always route it to e.g. IP .99 or anything the like.
I'd recommend using a static IP on the WAN side of your pfSense box anyway. I'd talk to the ISP if they could disable / rearrange the DHCP to exclude e.g. 192.168.1.2 or .1.254 from the DHCP segment and if they could please full-forward all traffic to said IP .2 or .254
So you don't have to guess what does what and simply know it will be sent there to which device whatsoever has it :)
-
Must be somewhere within these lines. There is simply no other answer.
Quite possible that the Mikrotik has set it up somehow, and it persisted for some time, but it got (who knows) cleared when switched to pfSense. Without additional info, it is now all just guessing.
I'll query the ISP on what are they doing there. Doubt they'll talk... but that is a different story.
I feel bad the pfSense was the one who got the blame, I have to apologize to it for that :) but the best apology is that I yet want to keep it and use it, it is a great thing, with a great support BTW.
But hey, without going this way, I would have not got this far. This whole discussion helped, a lot ! -
Oh, and I forgot to write down a "solution" that is right now working within my place, at the moment.
In case anyone else would face a similar issue (with a small rural european ISP... and a unknown uppath setup):Originally, I had the pfSense connected right to the ISP's POP; this did not go well for the NAT (even though it was finally not the issue of the pfSense's NAT itself, but an issue of the system setup including the pfSense);
now I have simply inserted a vanilla Mikrotik router in between (ISP and pfSense).
The router does src-nat and dst-nat, and the pfSense nicely humms right behind that, doing the firewall job as well as the NAT.
Of course this is not a clear way to do, nor a solution I'd ever like to keep, but it is a band-aid I have just needed.Thanks to all of you within this thread, your comments allowed me to figure this quick dirty fix up !
-
I'll query the ISP on what are they doing there. Doubt they'll talk... but that is a different story.
Just as a quick follow up: If you pay for your own public IP to get forwarded to you, they should have no trouble setting their UBNT POP the way you want. Otherwise what's the gain in paying for something you can't successfully use all the way you want? ;)