pfSense Unbound DoT - additional setting needed?
-
So... I came across this blog post on another site from 2018 regarding Unbound forwarding and how many articles about setting up DoT and Unbound are missing one thing: Certificate validity checks. What does this mean? It means that anyone could still intercept your DoT request and replace it with a response of their own, even with just a self-signed certificate, and Unbound would be none the wiser.
Here's the article: https://www.ctrl.blog/entry/unbound-tls-forwarding.html
Apparently, there are two pieces needed to completely secure Unbound DoT:
- Root CA Bundle (located in /etc/ssl/cert.pem)
- An additional piece for each forwarder line indicating the TLS domain that the server will be presenting
pfSense is already configured with #1. But #2 is the piece that is missing. Since pfSense just takes the DNS server IP addresses from System > General, it doesn't have any info regarding the domain that should be getting returned in the TLS certificate, thus not being able to fully validate that the request is coming from the server it thinks it is.
From the Unbound Config man page (forward-addr):
If you leave out the '#' and auth name from the forward-addr,
any name is accepted. The cert must also match a CA from the
tls-cert-bundle.I'll be happy to open a feature request for this (if something similar isn't already open), adding the ability to specify DNS forwarders on the DNS Resolver settings page, including the domain name. Maybe the System > General servers could be automatically imported, but don't allow saving until the domain names are added if the "Use SSL/TLS for outgoing queries..." option is checked? But this seems like a pretty big piece missing to ensure that DoT is fully secured here.
-
System > General also includes a box to define the hostname for checking the cert validity. If you don't see that, you must be on an outdated version of pfSense.
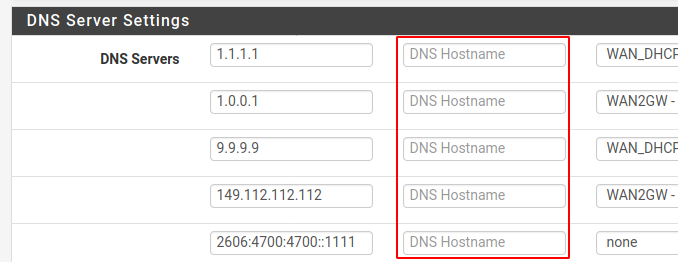
-
Thanks for that... I had seen the DNS hostname boxes, but must've missed the text below indicating that they're related to DoT. Something might want to be mentioned on the DNS Resolver page at the SSL/TLS checkbox too, that for best security the hostnames for the servers should be entered on System > General.