Squid + https
-
@DaddyGo said in Squid + https:
disable port 80, though that would still be crazy
That's too much haha. I want to do what "https everywhere" does but on the pfsense or other end equipment and without breaking internal pc/os stuff. On a DNS level basically but on the other hand how do you determine what comes from browsing and what not...
@DaddyGo said in Squid + https:
I think the pi-hole is forgettable, here is the great Unbound + pfBlockerNG pair
DNS is probably one of the only services I wouldn't mind to "outsource" from the firewall. Especially when Pi-hole is much more organized, visual and has a bunch of people who all they do everyday 24/7 is trying improve it.
An entire project dedicated solely to DNS.
pfBlockerNG is at the end of the day a package. I'd still use it as an IP blocker though :)@DaddyGo said in Squid + https:
their names are not public, because you would faint if you knew
Crazy! With all the money these companies have they still try to save as much as possible and be cheap, even when it's in their best interest to invest it hahaha unbelievable.
-
Hmmm HTTP...
with http you you can't start anything this is a webserver question, for example on a web server in the .htaccess file all http must be redirected to https
plus Let'sE certificate and that's aboutonly web masters are lazy, cca. 10 minutes job it
you don't think so,.. the Pi-hole is just popular and beautiful nothing more
(I apologize to all the Pi-hole fans) - perfect for raspberry piUnbound + DoT + DNSSEC + CF DNS servers and pfBlockerNG -devel, it is a professional solution
+++edit:
people tend to overcomplicate everything even though it is simple and everything is included in pfSense (more or less)
-
@DaddyGo said in Squid + https:
Unbound + DoT + DNSSEC + CF DNS servers and pfBlockerNG
That's exactly what I use! But...except for the fact that it's AIO solution + IP blocking what would be another advantage of pfBlocker over Pi-Hole (DNS wise)? Also, I've seen more lists and just info in general about Pi-Hole and as I said it seems much more organized, visual etc.
One last question if you may.
What happens when/if a MITM has its PK signed by a trusted CA? Would it still break because the browser will check from which domain/address the data came from resulting in a mismatch between what the client requested and the source? -
pfBlockerNG does exactly the same thing as Pi-hole, only better
mainly because it does with a professional DNS resolver, which is Unbound
don't be fooled by the look...(GUI, etc) - Pi-holeprofessional stuff usually doesn't even have a GUI, just a CLI
just look at Brocade, Juniper, etc. switches or Cisco enterprise devices
pfBlockerNG has a clean design and what is good can be set even by those who don't understand it so muchthe browser only sees the Squid internal certificate behind the proxy
he does not even know the existence of the original certificate -
@DaddyGo said in Squid + https:
professional stuff usually doesn't even have a GUI, just a CLI
I know, but it's not only the GUI part here. It's an entire dedicated solution for one single task - "DNSing", but I'll search for some good lists for pfBlockerNG and see.
@DaddyGo said in Squid + https:
mainly because it does with a professional DNS resolver
I forward the requests anyway, because the 13 DNS root servers don't support DoT (yet).
With Pi-Hole it would be DoH because they don't support DoT yet for some reason. -
@DaddyGo @Gertjan Do any of you know how does a certificate validation works exactly, in technical details?
I just posted it on security.stackexchange but decided to try and ask you guys as well :)I've read this post - https://security.stackexchange.com/questions/135401/certificate-validation,
where it says this : "...an attacker can still take the whole signed content and present it to you but won't be able to change any details or the signature won't match."My questions are these:
(1) How does the browser validates the details of a certificate and see its content like: domain name etc.? Knowing that the cert is encrypted.
(2) If a MITM wanna change anything he would need to decrypt the cert, which is impossible, or simply change what he wants but then fail at the browser because, as mentioned above, the signature won't match?Thank you,
-
@techtester-m said in Squid + https:
but I'll search for some good lists for pfBlockerNG and see.
in the "devel" version have a lot of built-in lists, but I also have a lot of collected lists
don't be fooled by the word = DEVEL - this current / actual version
-
@techtester-m said in Squid + https:
Do any of you know how does a certificate validation works exactly, in technical details?
Yep.
Have a look at least 10 videos from this list https://www.youtube.com/results?search_query=https+certificate+how+it+worksAdded to that :
In a perfect world, DNS is non spoofable (because you use the Resolver and DNSSEC ;) ), your app will know for sure what the real IP of a site is.The important things :
In a certificate, you find the dates of validity,
The CA, used to certify that the certicate is valid. An OS, web browser, app, whatever, sues a build in list with known trusted CA's - and take note : you can add your own CA .... you can become a CA for your own network.
In a certificate is embedded the domain name or even a root domain name :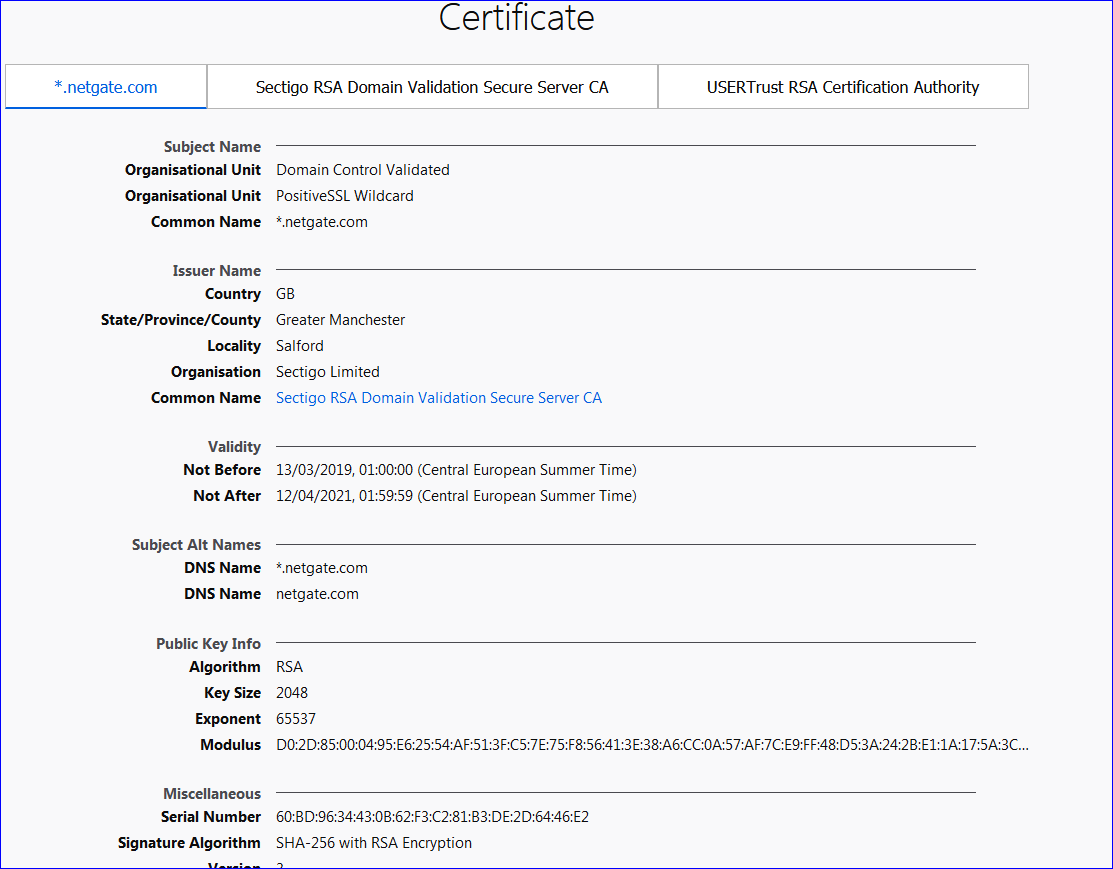
-
@Gertjan @DaddyGo I already knew about the certificate itself and I myself have signed or got signed by a trusted one etc. All I wanted to know is the security mechanism(s) that prevent MITM. Yesterday I did more reading on the subject and on digital signatures as well and understood everything I wanted to understand and know. It took a few hours over 1-2 days but Hopefully it'll be stored in my head forever haha
As I understand it - Unless a MITM got the end user to trust his CA, the attack will fail.
It would fail because:
(A) MITM would try and send his own PK and the browser will give warning.
(B) MITM must send his own PubK in order to encrypt/decrypt the content with his Private Key which is the key to everything here basically.
(C) If MITM changes anything in the message that comes with the certificate, like the domain name etc. the signature verifying algorithm would fail and the browser will give warning.
(D) No CA would sign fraudulent certificate unless they wanna go bankrupt and get sued.
(E) Even if a MITM sends the end user the exact same certificate he himself got from let's say Google then the browser might think for the first time that it's talking to Google but the next communication would fail because it would be encrypted with Google's PubK and could be decrypted only with Google's Private-Key so the MITM won't be able to read anything, there will be a connection time out and the attack would fail.
(F) I'm sure there are few more reasons...Thank you guys for all your help, input and knowledge. A pleasure as always :)
-
Hello,
Can you help me find solution?
I've added CA of our domain controller in System > Cert Manager
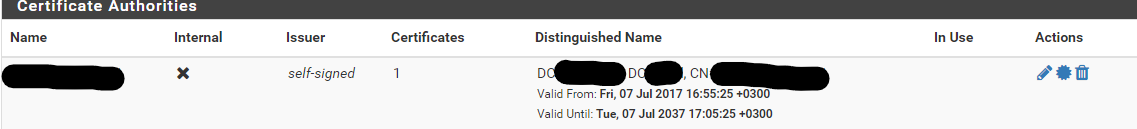
But in squid SSL MITM i can't select this CA and enable SSL filtering. Only "None" can select.
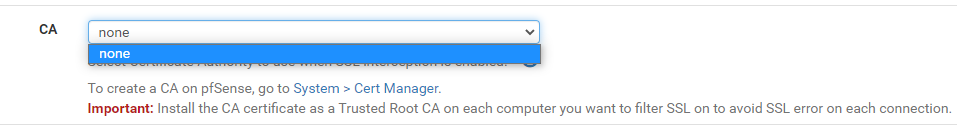
How i can set up domain CA for enabling SSL filtering ?
Or pfsense can only accept self made cert from internal CA?
Thanks in advance. -
@viberua I'm no expert at all on the matter but it tells you to create your own on pfSense, because it needs to be able to create certs on demand and locally...I think, but again..no expert.

-
Never used squid before, but I guess a CA should be created first.
Here :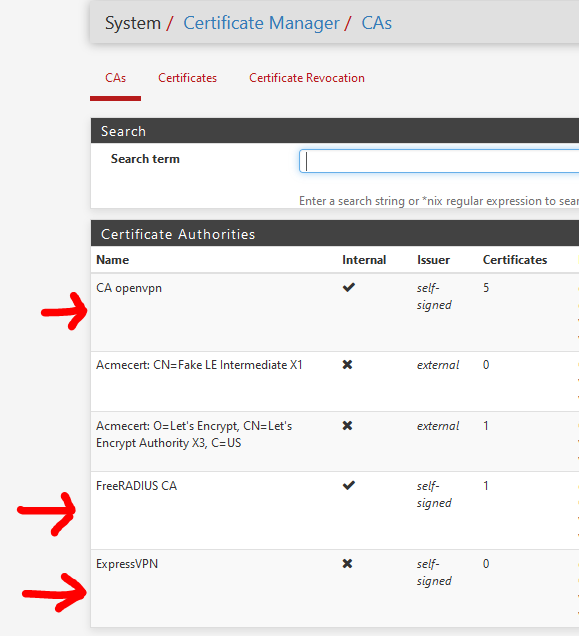
Then, based on the CA, you create your certs :
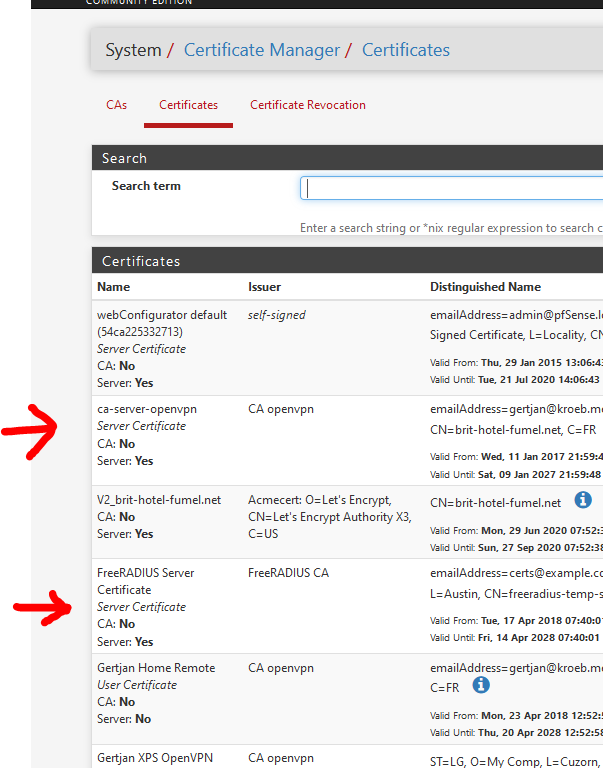
These certs can be used in OpenVPN, FreeRadius, the pfSense GUI, etc.
CA's can't be use directly, except for signing (your own) certs. -
@Gertjan said in Squid + https:
Never used squid before, but I guess a CA should be created first.
Here :exactly,
use the pfSense certificate builder and then it will appear in Squid settingsthen you can also export it for installation on external devices
like:

-
@DaddyGo so if i don't want create new CA because i already have one, then i can't use this external CA cert in MITM?
-
Squid works with an internal intermediate certificate
you can't use example Lets' E or otherbecause of what is described above in this thread......
like:
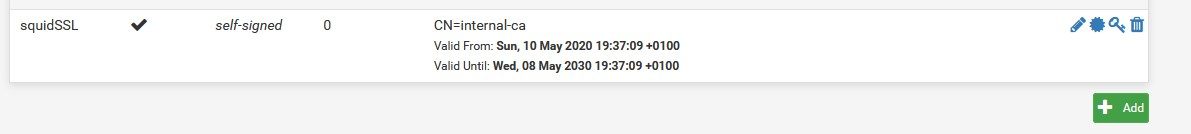
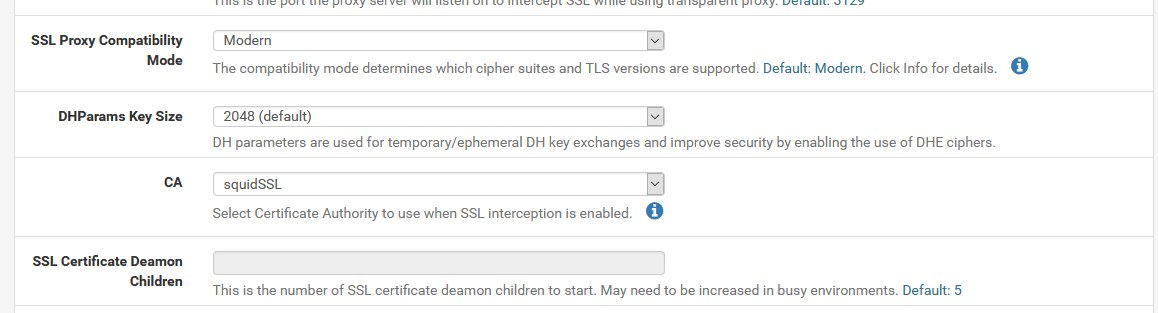
-
@viberua You need to "become" a CA (a local one of course) and have your own Public Key & Private Key in order for Squid to encrypt-decrypt.
-
@DaddyGo when i try to create an intermediate CA, the list of signing CA is empty
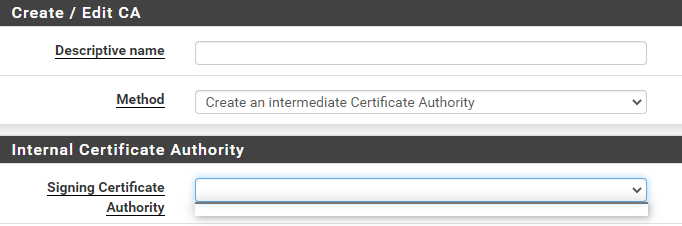 but as i said i have our domain CA server and added his CA cert to CA settings
but as i said i have our domain CA server and added his CA cert to CA settings
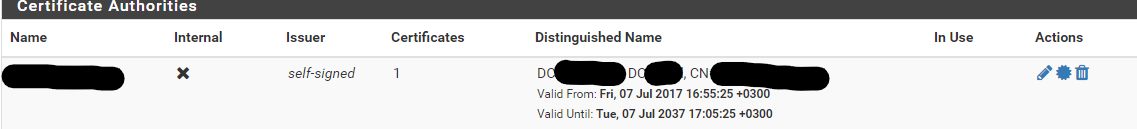
-
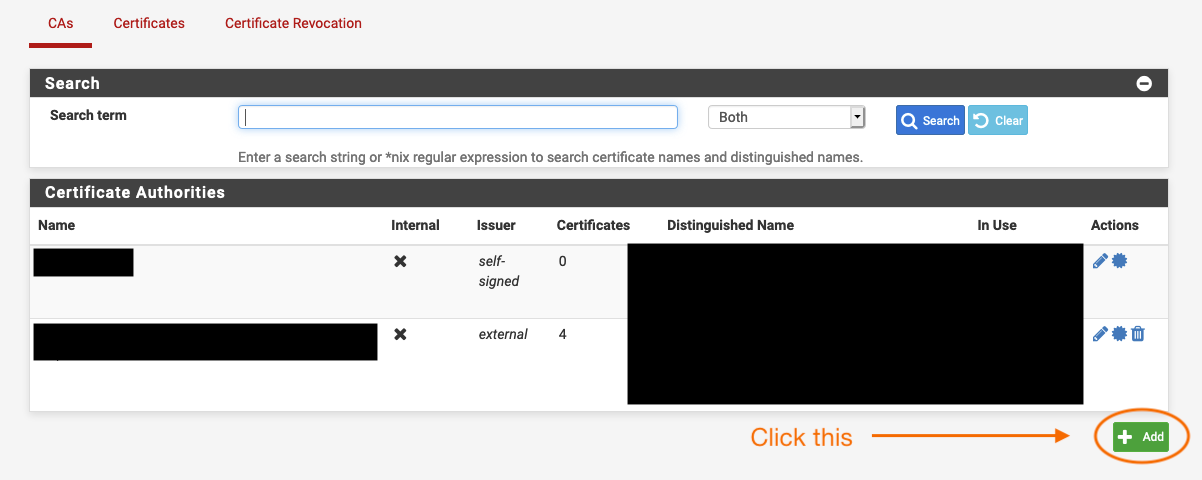
@viberua said in Squid + https:
but as i said i have our domain CA server and added his CA
Won't work.
Do this from scratch:
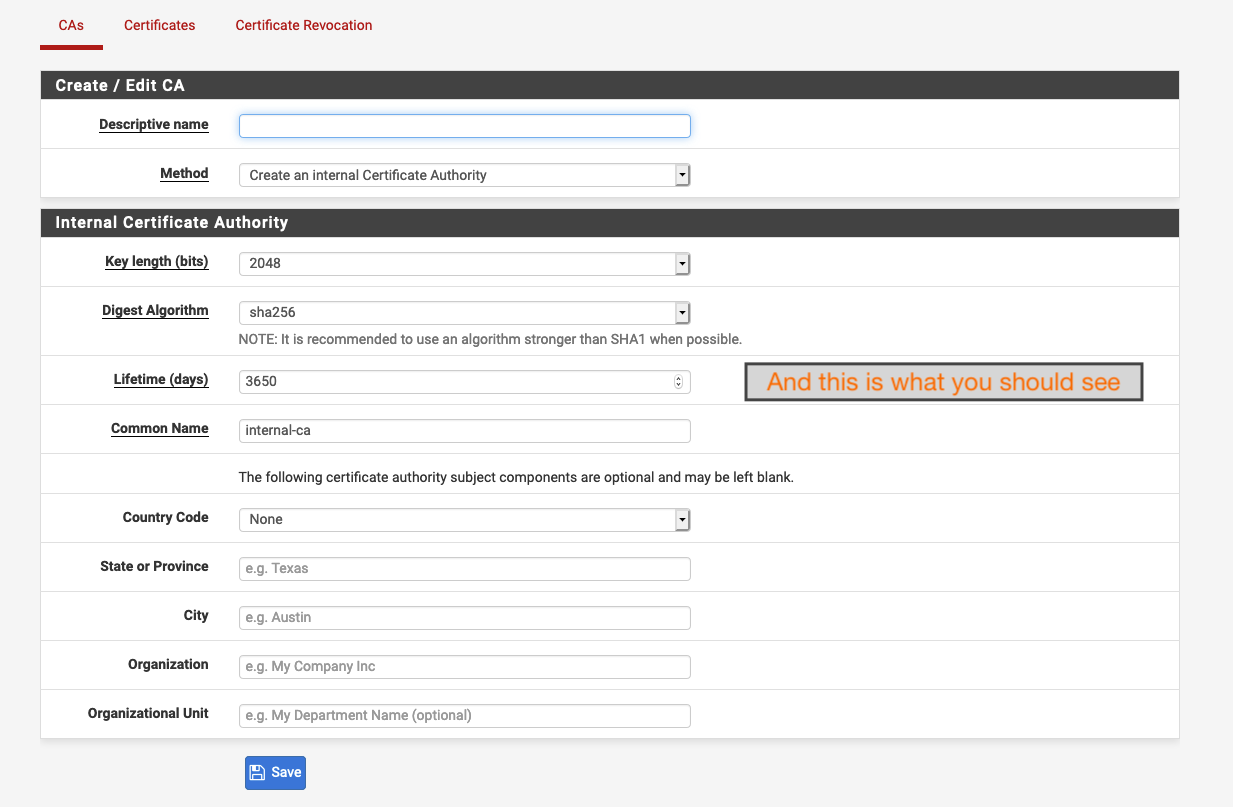
And this is what you should see:
-
you are doing something wrong...

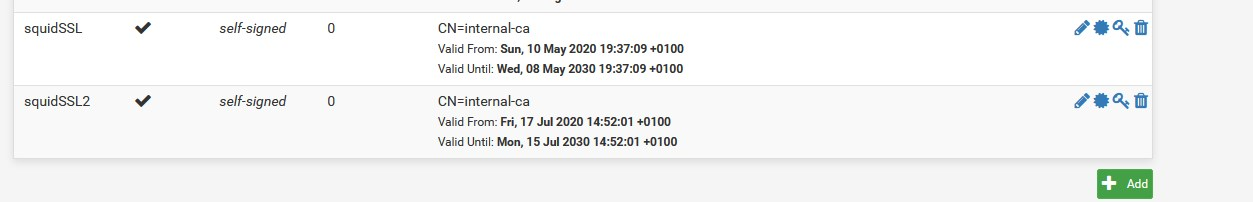
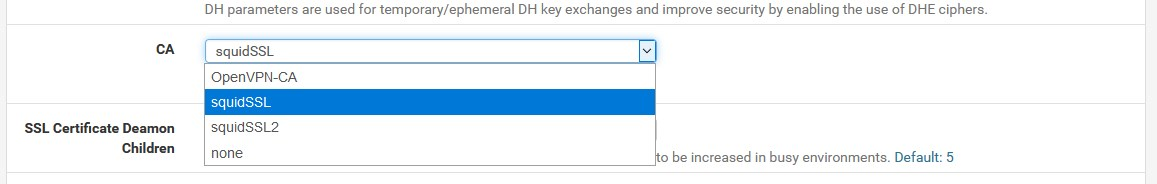
because it works very well in pfSensejust watch squidSSL2 I just created for the sake of the test...
-

I like you bro, but it is not appropriate to speak into an ongoing conversation...forum etiquette