Windows Server DNS Server can't forward to pfSense
-
Hi,
I have a lab which contain a pfSense behind a VMware NAT and 4 LANs. In one of my LAN I have a Windows Server 2016 (DC and DNS Server) and all my machines have this WS2016 as primary DNS (172.16.1.5).
On the WS2016 I have set the primary DNS to the loopback address (127.0.0.1). In its DNS server parameters I have set the forward address to my pfSense IP (LAN or WAN interface does it matter ?) which has set my NAT gateway (192.168.101.2) as DNS Server.
- pfSense LAN Interface : 172.16.1.2
- pfSense WAN Interface : 192.168.101.40
My pfSense can resolve hostname but my Windows Server cannot, nslookup fails everytime whereas the traffic is allowed and seen in the logs.
I truly don't know when I misconfigured something here.
-
@Hekmil Always lan interface of pf should be used
-
Alright then the issue doesn't come from this, it was already the case.
-
@Hekmil Lan rules allowing port 53 tcp and udp?
-
@netblues At first only udp but to find the issue and test I allow all traffic from my Windows Server to ANY
-
@Hekmil You need tcp for nslookup.
try nslookup from windows.
server ip.of.pfsense.lan
cnn.com -
@netblues Yeah everything is allowed at the moment so it's fine

-
@Hekmil Is dns resolver service running on pf? is it listening on lan interface?
-
@netblues yes it's running, I can resolve any domain from the pfSense.
The configuration is the default one, listening on all interfaces.
It's like the Windows machine can't forward the DNS request to the pfSense.
-
@Hekmil No. You run nslookup
What is the lan ip of pf sense?
Try running nslookup from pf cli
pf sense it self can resolve without a local resolver if configured to use wan connection dns for example. -
@netblues Yes I was talking about running a nslookup from the pfSense CLI, sorry if it wasn't clear. From the CLI it manage to resolve.
My LAN ip of my pfSense is 172.16.1.2
Yes the pfSense does use the WAN connection when resolving
-
@Hekmil not much left to do.
can you ping pfsense lan from windows server? -
@netblues Yeah that's why i'm asking here, because I'm out of option
Yes all my machines can ping together. But only pfSense can ping outside the NAT (for example 8.8.8.8).
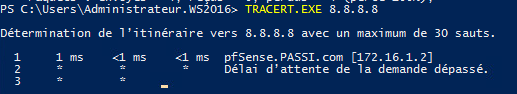
Here is a tracert command to 8.8.8.8 which timeout after reaching pfSense LAN interface. The firewall log :
-
And you cant nslookup from everywhere else with pfsense lan ip but you can from pfsense cli using lan ip.
Anything on floating rules? -
@netblues Wait I was only trying to do
nslookup cnn.comon the cli not using lan IP. If I do that it doesn't work of course sorry. It's like the resolving DNS service was not enabled for all interfaces except it is.Floating rules are empty.
-
@Hekmil please post services resolver settings.
Have you tried restarting resolver service? -
@netblues Here are my setting of my resolver :
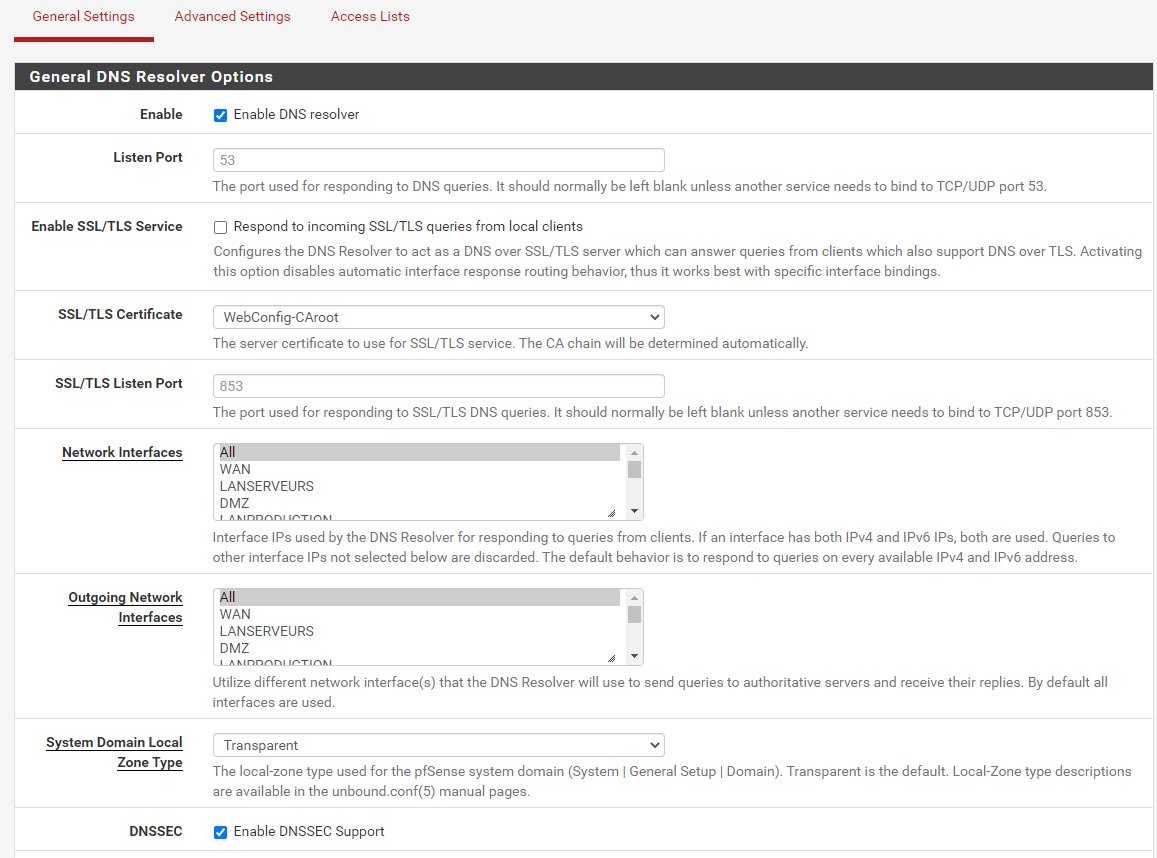
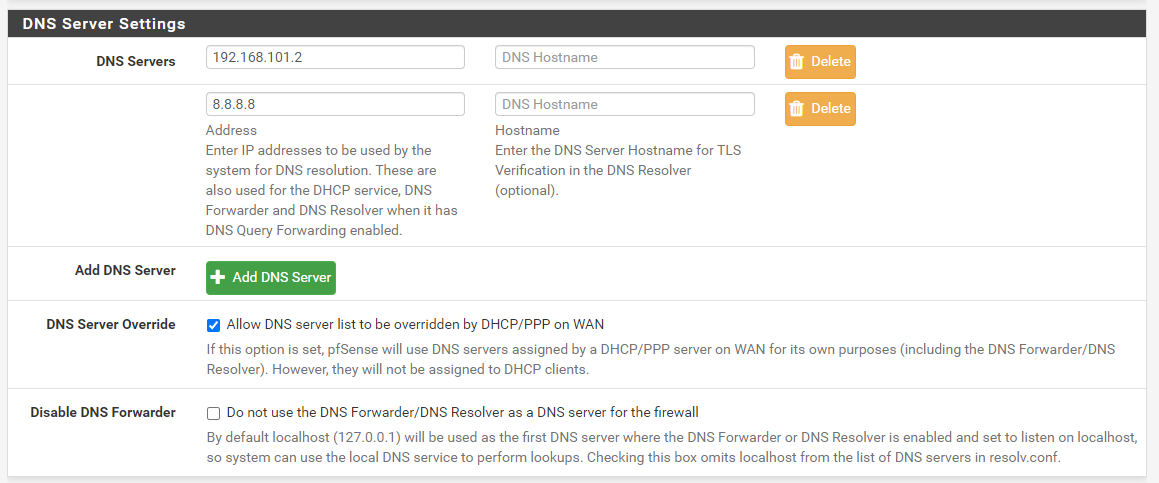
192.168.101.2 = NAT GatewayYes the service and even the machine has been restarted trying fixing the issue
-
@Hekmil you dont really need any dns servers if pf can reach the internet..
However this is irrelevant.
Dns resolver should be listening on lan anyway.
Do restart the srrvice and look at status system logs resolver logs for anything strange. -
@netblues True that
Nothing really usefull from the logs :
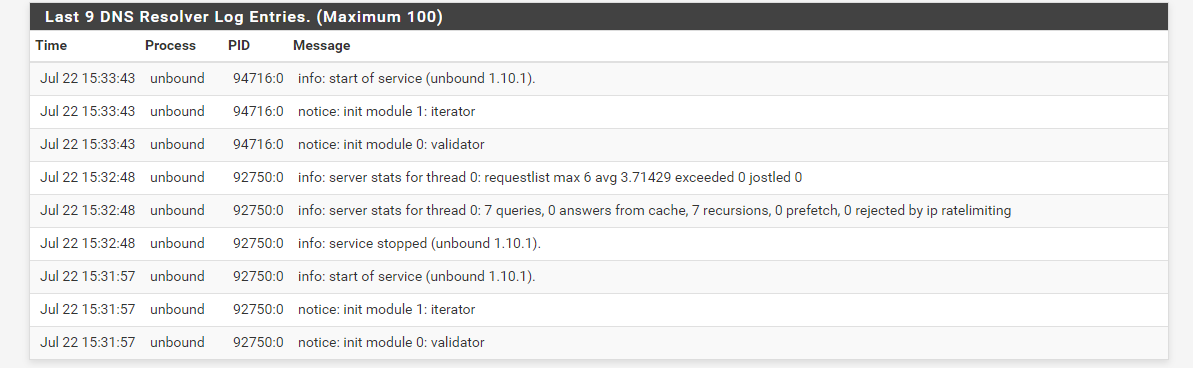
-
@Hekmil output of sockstat -l please