Verizon Fios and IPV6, Which Settings Work?
-
Yeah, tracking the rollout is a bit out of scope for here (since this is the pfSense support forum)... post in the DSLR thread and I'll get your CO added to the list.

-
C Cyth referenced this topic on
-
B betapc referenced this topic on
-
Hi everybody, this is an update, today I did a clean installation of pFSense, out of the box I had IPV6 without any issues, I didn't have to change any settings, I have full access. Then I upgraded to pFSense plus, same thing I didn't have any issues, full IPV6 working out of the box.
The size of the IPV6 is 56 automatically Verizon provided the size to pFSense, again I didn't change any settings.
The only strange thing is the size of the IPV6 change when I upgraded to pFSense plus. I didn't have the time to figure out what happened.
So far is working.
I think Mike is right, looks like some areas just started rolling out dual stack and there is some technical issues in the implementation, couple more weeks of patience for some areas, I was waiting for Verizon implementation of dual stack for almost 10 year.
Thanks everyone for your posts, they were really helpful.
-
@betapc Are you able to share full screenshots of the Router Advertisements page? What, if anything, do you have checked? I have everything set up the same as your screenshots, but for whatever reason IPv6 traffic is not passing. I even found that spreadsheet that says that my CO should be live (since the end of July). Everything was working with Hurricane Electric before, so not sure if I'm missing something here.
-
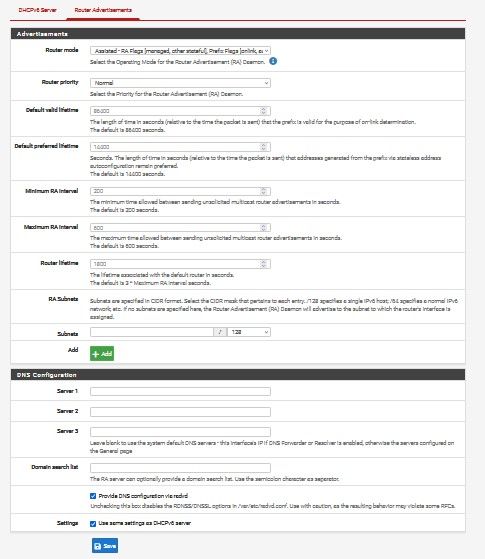
@jdefuria Is frustrating to make it work, I still have the same setting, still working. The only thing I change was the router advertisement mode to assisted because they can do both DHCPv6 server and/or stateless auto-configuration.
So far is working same settings, the only issue if you release the IP address to get a new one take time, you have to reboot pFSense.
The problem with Verizon support they don't tell you if there is a issue on their side, they do all this rebooting multiples times and that's it. They sent me a new Verizon router that was their solution, and even with the new router didn't work because they were having issues with IPv6, couple days later just work, after I spend hours trying to make work. I tested my ONT if I was getting an IPv6 was with the Verizon router before connecting my pFSense.
If you have a Verizon router connected directly to you ONT and then you login into router setting and you can see if you are getting the IPv6 address and if you connect a laptop and then you test it with IPv6 test web page, if that doesn't works is because Verizon still have issues. If the laptop works and past the IPv6 test, so something is not right with the pFSense configuration.
-
@betapc thanks for posting- I will have to find a time to plug in directly to to ONT and see. I just found the thread on DSLreports where the spreadsheet comes from, and it looks like someone else posted that they are having issues at the Marlton, NJ CO. I wonder if it’s not really “on” here yet!
-
@jdefuria I spend hours with FiOS customer support, I did clean installation of pFSense. Spend days trying to configure everything on pFSense and nothing, until I figure out that was FIOS problem. The worst part customer service don't confirm or denied if they are providing IPv6 in the area or if is working without issues.
The settings I post still working with out issues.
The only problem is traffic shaping, I still unable to configure it right, my bufferbloat is really high. I tired all the settings and nothing.
I have IPv6 connection speed and connection are good. All my devices are working properly so far.
-
@jdefuria I forget mentioning, for all the testing and configuration I used a different DNS, because Verizon DNS for IPv6 is not really good, there is some issues too, is not giving good responses, I used Google and 1.1.1.1 for both IPv6 and 4.
Google
2001:4860:4860::8888
2001:4860:4860::88441.1.1.1
2606:4700:4700::1111
2606:4700:4700::1001 -
@betapc said in Verizon Fios and IPV6, Which Settings Work?:
The only problem is traffic shaping, I still unable to configure it right, my bufferbloat is really high. I tired all the settings and nothing.
I am still trying to tweak my configuration, but I have managed to raise my grade on the Waveform Bufferbloat Test from
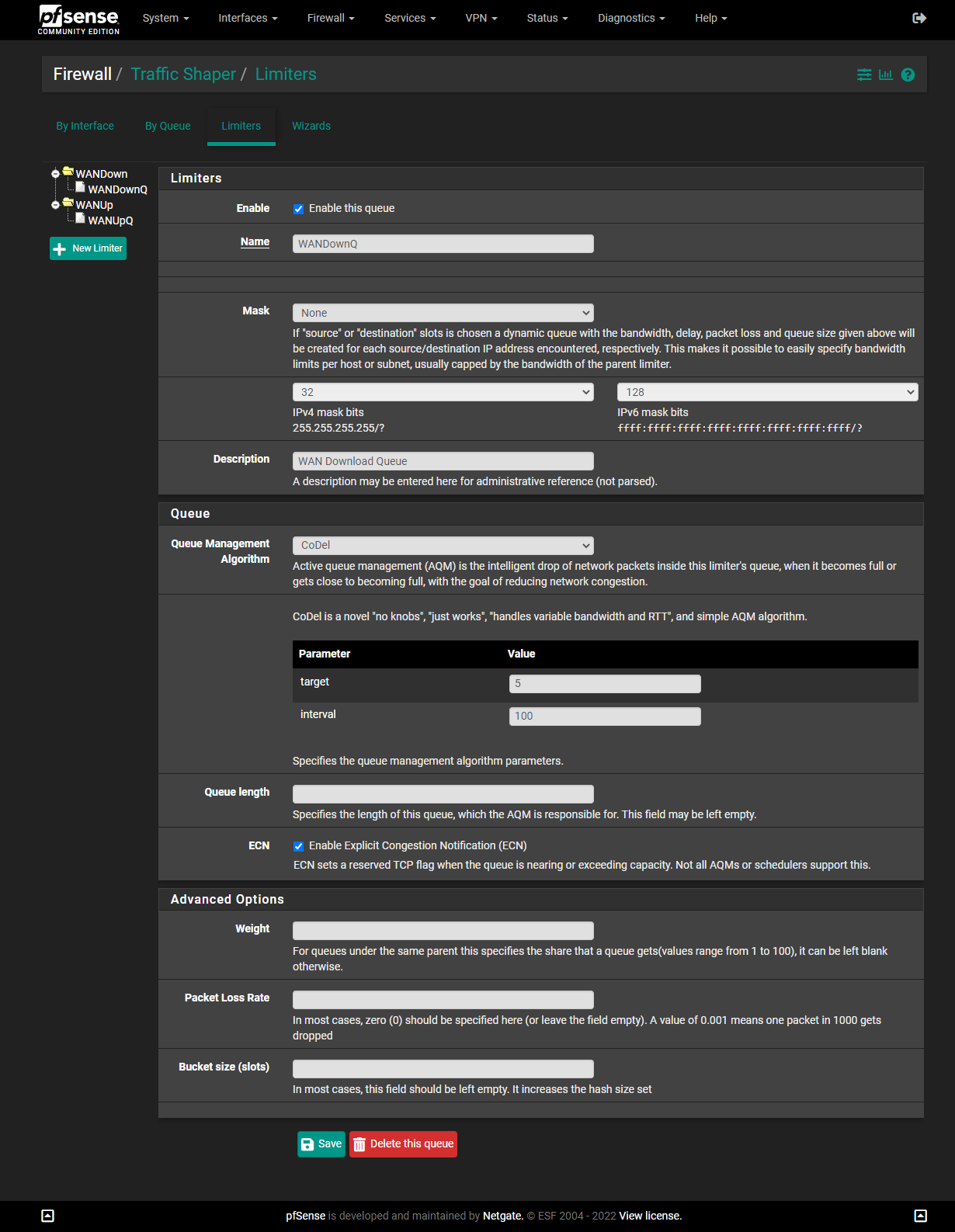
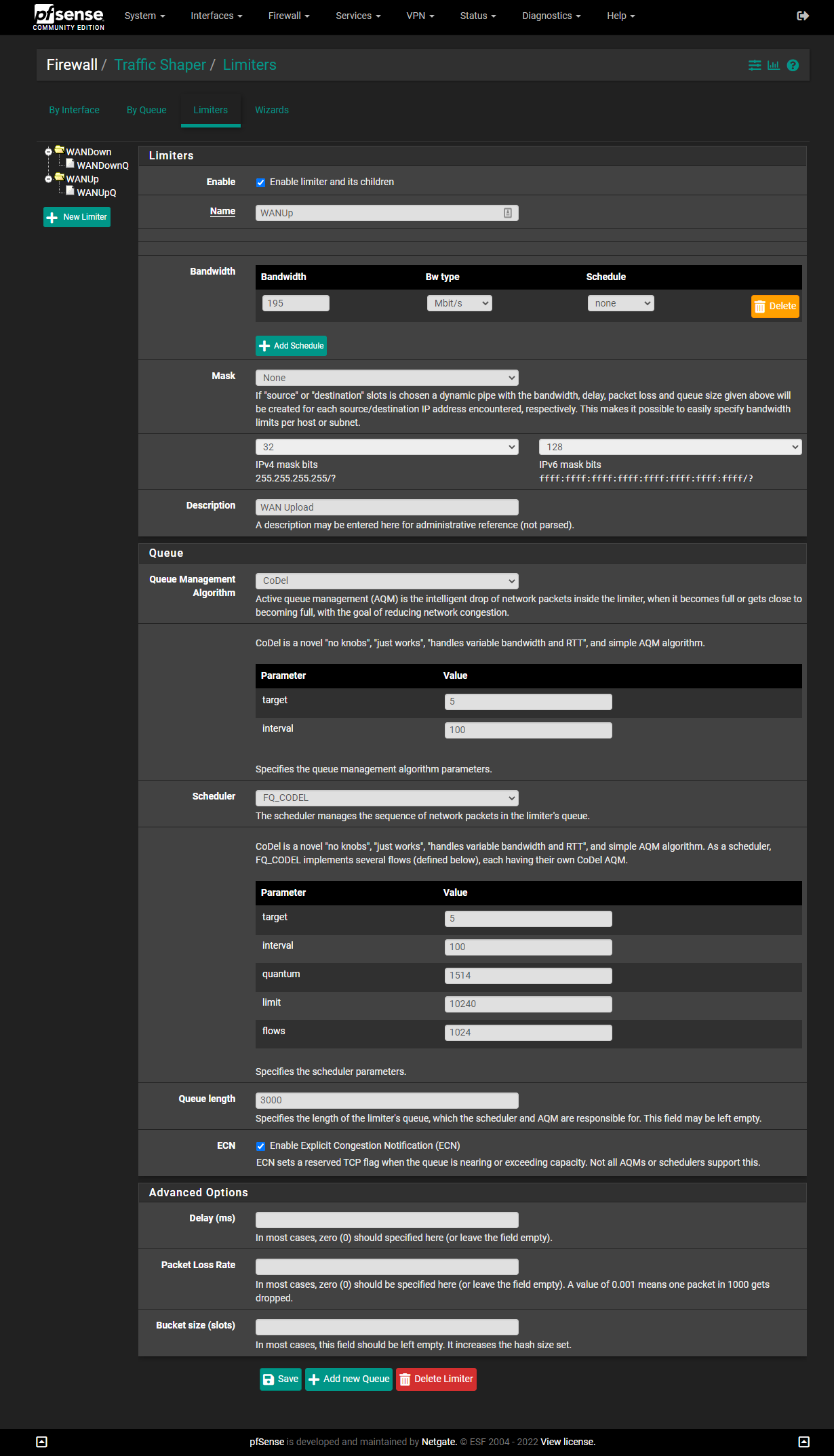
DtoBlike this:(Note: I have 200/200 service. You will need to change the numbers if you have different speeds. While Verizon often overprovisions the speed settings (I've occasionally gotten 250Mbps in some speed tests), many forums suggest subtracting 5 from your official speed, as I've done here.)
IMPORTANT: The screenshots below are older and show a "Queue Length" of
3000. I found that4000works even better for me, but5000is too high. You may need to experiment to find the best number for you.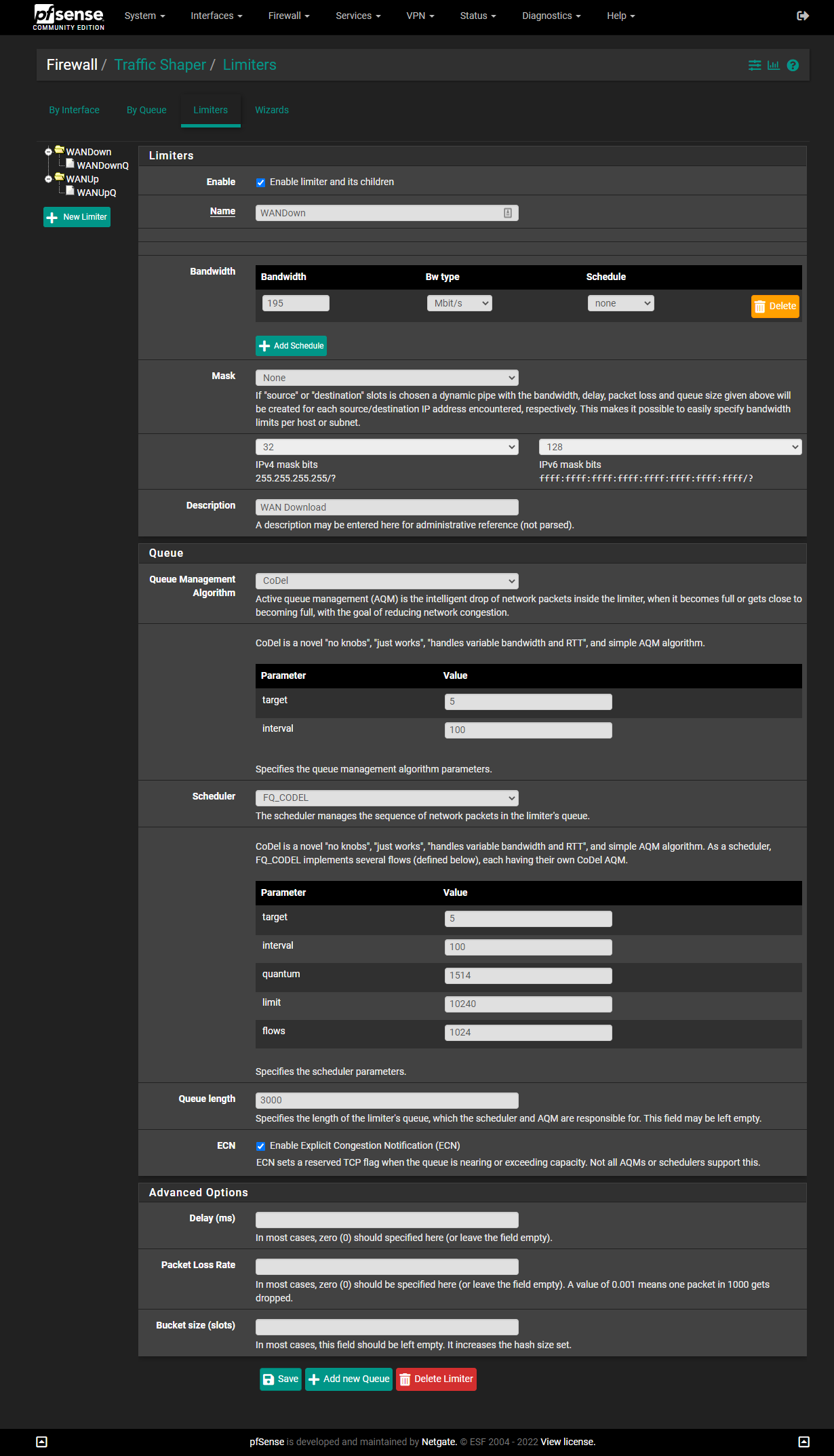
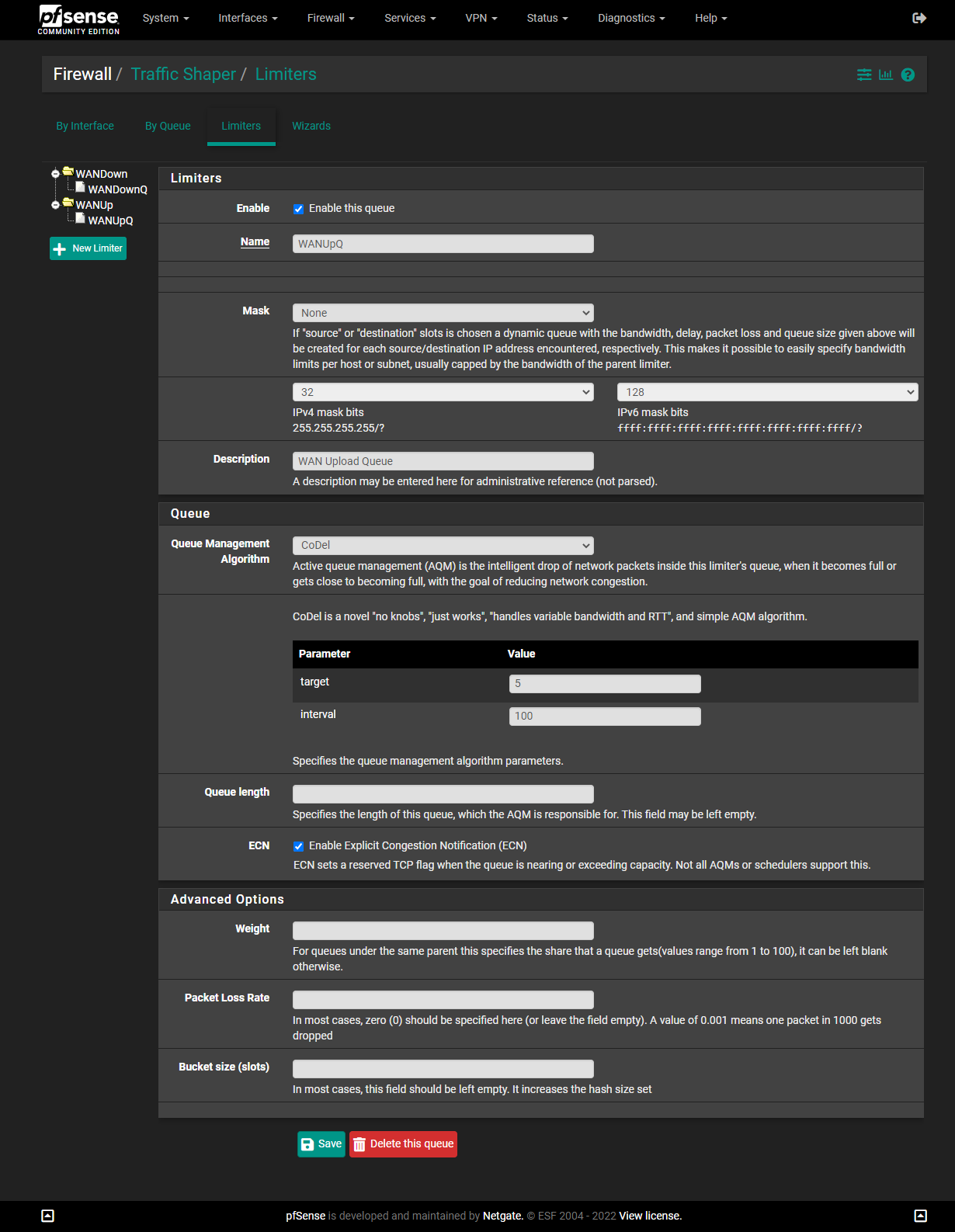
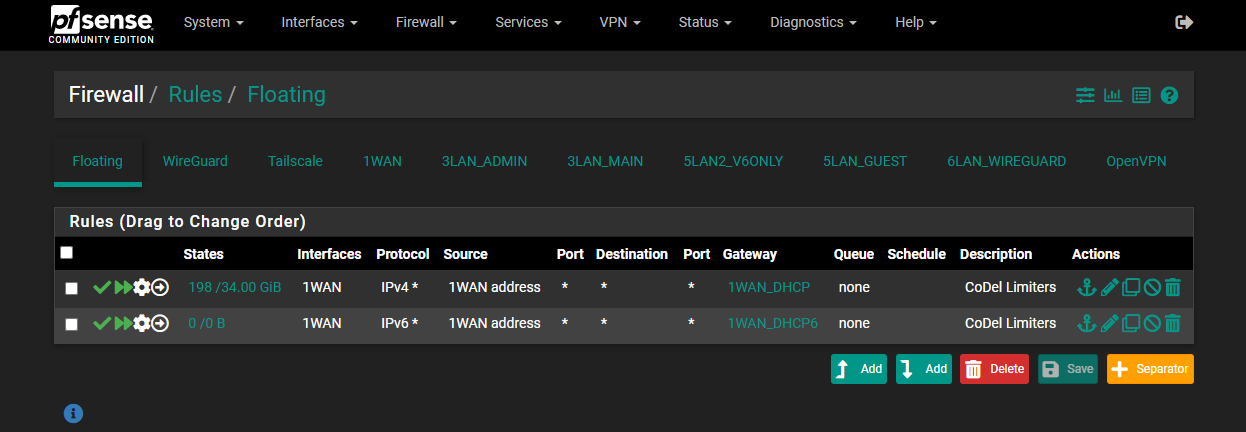
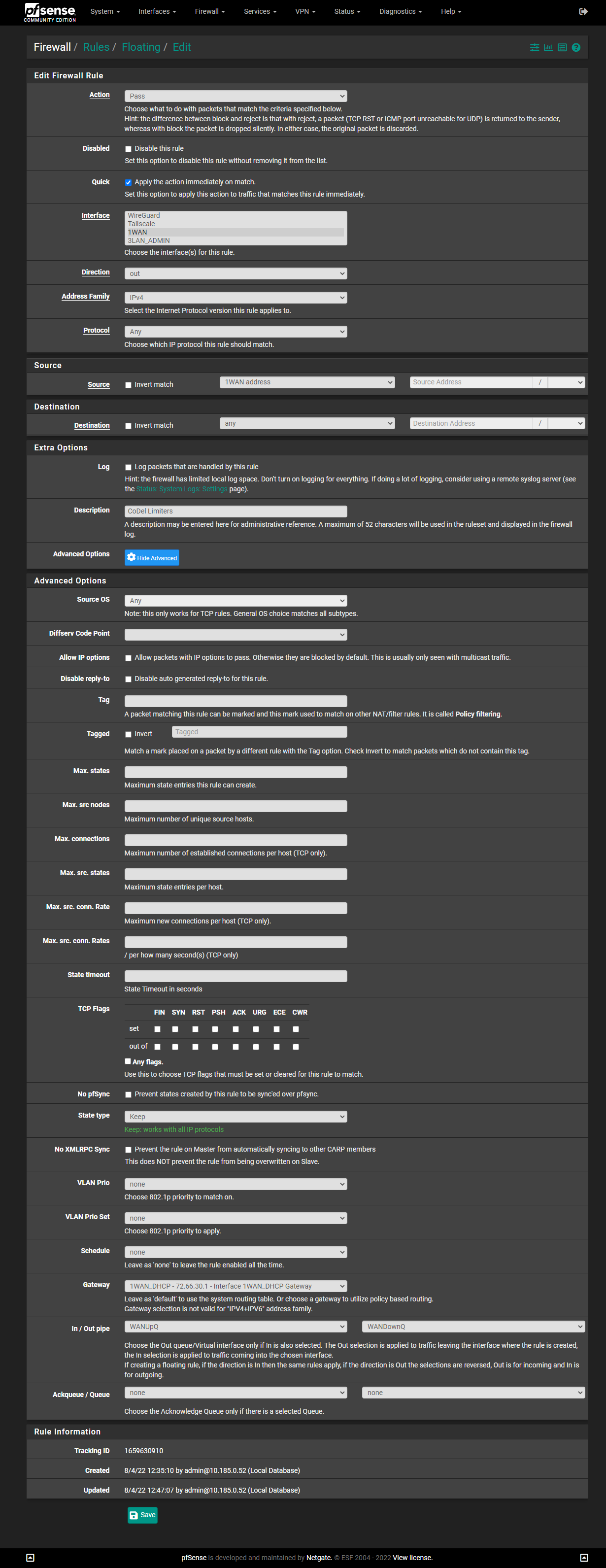
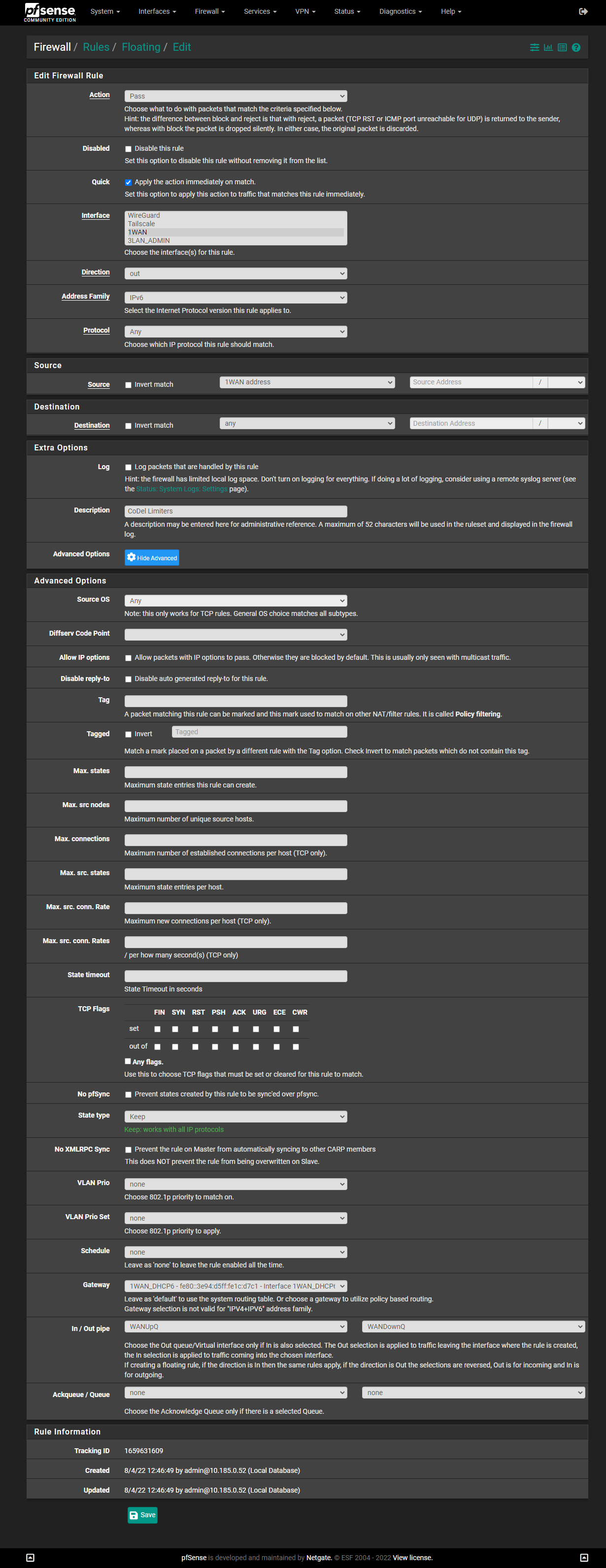
-
@betapc Your troubleshooting tip of asking to plug right into the ONT does indeed show that IPv6 is not on at my CO, and I tried at my friends house in a different subdevelopment (she thought I was crazy) and I do not believe MARLNJMA is online with IPv6. @MikeV7896 are you the one that updates this spreadsheet?
-
@jdefuria I am on the list. My didn't work for the first week. Can be coincidence, I also left my ONT unplug all the cables and from electricity over night, that is another way to release all the IP address, usually 3 hour unplug FIOS release the IP and provided new one. I leave over night just to tried. You can give it a tried, you never know.
The roll over had been slow and no perfect. Don't tried to hard maybe is not you, is FIOS.
-
@kohenkatz Thanks for the info, I am on pFSense Plus 22.05, I did use your setting and the whole system stop, because Queue Management Algorithm can not be CoDEL, need to be Tail Drop and the Scheduler FQ_CODEL on pFSense Plus 22.05. When I test those setting on pFSense CE work good as soon upgrade I have the issues. I applied this documentation https://docs.netgate.com/pfsense/en/latest/recipes/codel-limiters.html thanks to @luckman212, still no luck. I will just wait if more people have the same issue or if the problem is with Verizon. That will be another post.
-
Recently upgraded to a pfsense router (v2.6.0). I have Verizon FIOS. The previous router (EdgeRouterX) never obtained an IPv6 even though DHCPv6 was enabled on the WAN interface. However, after enabling DHCPv6 on my WAN interface with pfsense, I noticed it obtained an IPv6 address. Afterwards, I enabled "Track Interface" on the LAN interface, the "DHCPv6 Server" service, and "Router Advertisements" (and setting Router mode to "assisted". everything worked.
pfsense is plugged directly into the external ONT and it a older model (4+ year old).
-
For those of you on consumer FiOS plans, how large of a block are you getting on IPV6? /64 or /56? Or maybe even larger?
Can you use DHCPv6 or are you stuck with SLAAC?
Are they static or do they change? With the new address space available in IPV6, there should be no reason anyone gets a dynamic IP address anymore, unless they are just being jerks and randomizing the IP on purpose to make people pay for business plans.
I'm still wrapping my head around how addressing works on a LAN when everything has to be a globally unique IP, especially if the ISP changes block addresses on me.
With NATed IPV4 it is great. I can set my own local static IP's in a private address range, and never have a problem, but now in a globally unique 1:1 world, my IP address has to match my ISP's block allotment.
Does this mean that static LAN IP's are pretty much dead, unless your ISP grants you a static block?
Sigh.
It's really frustrating to have to mess around with this stuff when IPV4 was working perfectly.
We certainly needed the larger address space, but the IPV6 implementation is a bloody nightmare. If it were up to me, I'd send the whole shebang back tot he IETF and have them start over with a focus on usability, human readability, and independence between LAN IP addresses and globally unique IP addresses.
-
@mattlach Verizon is giving me a /56. IPv6 has a feature called "Prefix Delegation". Pfsense supports that under DHCPv6. Prefix delegation allows the specification of the end of the IPv6 address. You specify the end address for under DHCPv6 and therefore still have a quasi static addresses. By default Pfsense assigns a range like ::1000 to ::2000. But you can still have static assignments for the DHCPv6, too
Additionally, you can use the fd00 and NAT the IPv6 connection. But, then again that really does go against the purpose of IPv6.
-
@mattlach said in Verizon Fios and IPV6, Which Settings Work?:
Can you use DHCPv6 or are you stuck with SLAAC?
ISPs generally use DHCPv6-PD. SLAAC is normally used on the LAN.
Are they static or do they change? With the new address space available in IPV6, there should be no reason anyone gets a dynamic IP address anymor
With IPv6, the prefix is usually stable, provided you select Do not allow PD/Address release. I've had my prefix for years and it has even survived replacing my modem and the computer I run pfSense on. On the other hand, some ISPs are stupid.
I'm still wrapping my head around how addressing works on a LAN when everything has to be a globally unique IP, especially if the ISP changes block addresses on me.
Even if they change the prefix, the addresses will still be globally unique. However, it will mess up DNS. You can use Unique Local Addresses to avoid this issue on your LAN.
Does this mean that static LAN IP's are pretty much dead, unless your ISP grants you a static block?
My addresses, both IPv4 and IPv6 are virtually static. Also, on IPv4, the host name is based on modem and router MAC addresses and so change only with hardware change. My IPv6 prefix doesn't even change then.
It's really frustrating to have to mess around with this stuff when IPV4 was working perfectly.
If you had to use NAT, it wasn't working perfectly. You are using a hack that causes it's own problems.
If you want to really learn about IPv6, I can recommend "IPv6 Essentials" from O'Reilly.
-
@jdefuria said in Verizon Fios and IPV6, Which Settings Work?:
@betapc Your troubleshooting tip of asking to plug right into the ONT does indeed show that IPv6 is not on at my CO, and I tried at my friends house in a different subdevelopment (she thought I was crazy) and I do not believe MARLNJMA is online with IPv6. @MikeV7896 are you the one that updates this spreadsheet?
I am... I'd prefer any discussion of the sheet and active (or non-active) CO's take place on DSLR though... that's a bit off-topic for this site since it's not directly related to pfSense. Plus, that's where the original report was made (page 70 of the topic; East Cherry Hill was reported, phone numbers in that area appeared to point back to Marlton). No registration needed if you don't want (you can post as an anonymous user there). Here's a link to the last page of the topic as of the time I'm posting this.
-
@jknott said in Verizon Fios and IPV6, Which Settings Work?:
If you had to use NAT, it wasn't working perfectly. You are using a hack that causes it's own problems.
I fundamentally disagree with this assertion.
NAT works, works well, and is even desirable in many circumstances. It is not just a hack, it is a valuable tool.
I feel like people overplay the issues with NAT, derisively calling it a hack, and completely dismiss its benefits.
No, I am not talking about security. Anyone who thinks NAT provides them with any level of security is in for a surprise. That's what the firewall is for. But NAT is an immensely valuable tool for flexibility.
I take exception with the concept that my local network is just a way to get to the greater internet, and because of this everything on my local network needs to be 1:1 addressable with everything else in the world. In fact, I fundamentally reject this concept.
My network is not part of the internet. It is a completely separate thing. The majority of my traffic never even leaves my LAN. It is separate from the internet, does not exist because of the internet, and really has very little to do with the internet at all, except for the occasional packet I direct to traverse my router to the outside world.
My network should be completely separate and completely independent of the internet. There being a firewall is not enough.
If I have to manage my internal network with coordinated globally unique addressing and DNS, there is something very very wrong.
This is what NAT buys me. Complete independence. I am not dependent on my ISP to provide me a block of some completely unintelligible hexadecimal nonsense address range. As long as I use the predefined private address blocks, I can set anything I want, and use it however I want, which is the way it should be, because it is my private network. I shouldn't be tied to the internet in any way.
In fact, I PREFER my local network being NAT:ed for this reason, and I don't want NAT to ever go away. Without NAT my network isn't truly mine.
As long as I control it, NAT doesn't cause me any problems at all. If I need to open and forward a port I can easily do so, no problem at all. And in return it offers me true flexibility with what I want to do with my local network. (This - however - only holds true if I am the one controlling the NAT. If my ISP uses CG-NAT to provide me a non-public IP address from upstream, I'll be pretty upset.)
Anyway, having done some reading, that if I switch to IPV6, I have determined that SLAAC is not going to work for me, so I am going to need DHCPv6, but I have also discovered that Google refuses to support DHCPv6 on their devices, leaving them with a broken IPV6 implementation. Because of this I am going to have to stay on IPV4 until Google pulls their heads out of their asses and properly implements IPV6. I'm not even going to try to transition until that happens....
...unless:
1.) My ISP eventually starts CG-NAT:ing me, and I can no longer use a dynamic DNS to access my network remotely; or
2.) I stop being able to access the remote sites I want to useIf either of these happen, I'll have to selectively enable IPV6 on a limited number of systems, but keep blocking it on everything else. I'd probably lean towards using the link local addresses and NAT66 though, because that's the way I like it.
I have zero tolerance for this "everything should be 1:1" mindset. There is absolutely no reason why my local media file server needs to be 1:1 with some guy halfway around the world's "smart" toaster.
When creating IPV6, the IETF made erroneous assumptions about how people want to use their networks that might work well for some, but certainly is not the solution for all.
-
The first issue with NAT I was aware of was active mode FTP didn't work. At that time most FTP clients didn't support passive mode. Browsers were still fairly new then, so FTP clients were generally used. These days, you need STUN servers for VoIP and some games, to get through NAT. It breaks IPSec authentication headers. It also adds extra overhead for routers to process NAT. You can get the same function as RFC1918 addresses with Unique Local Addresses on IPv6.
-
@mattlach IPv6 specifically has ULA addresses available to meet your desire for local addresses.
Meanwhile, NAT is problematic for security applications like IPSec, DNSSEC, and Geolocation. CGNAT just makes this problem even worse.
Also, private RFC1918 addressing makes combining internal networks with overlapping 10.x.x.x space unnecessarily complicated (very common in the case of business acquisitions and mergers). Never mind that the entire RFC1918 space is insufficient for large individual organizations.
-
@mattlach IPv6 has been working fine for Google, Facebook, and Verizon wireless for many years now. If you want to use site-specific addresses, those are called ULAs in IPv6.