Pfsense with AP dhcp server settings
-
Ping from lan interface:
To lan switch ip:
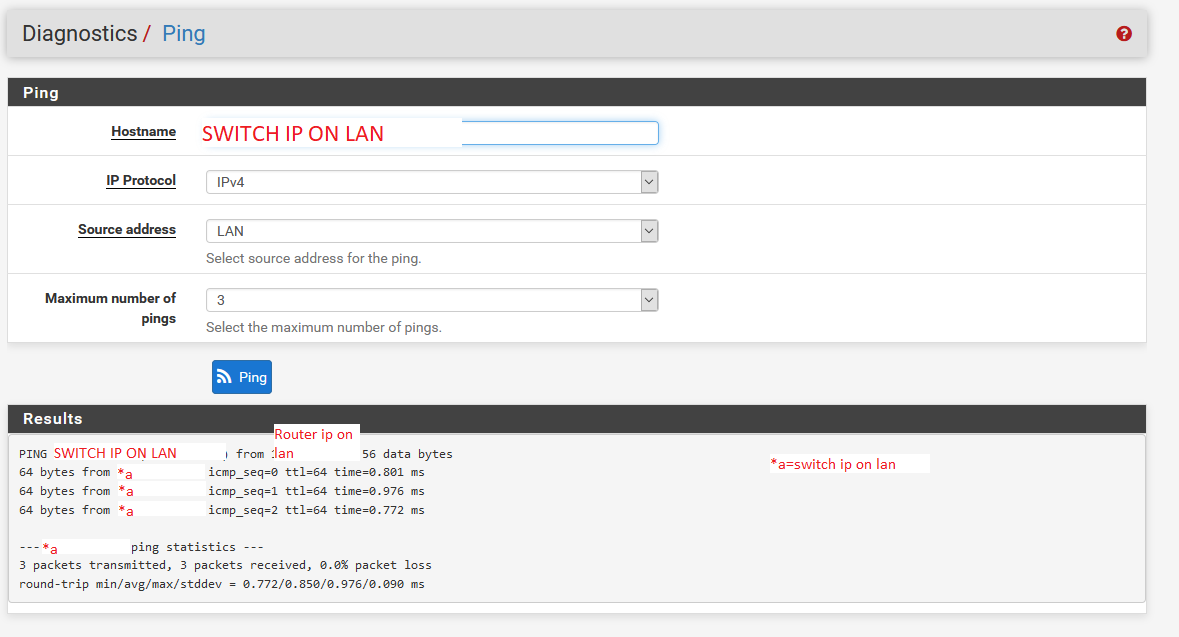
To vlan switch ip:
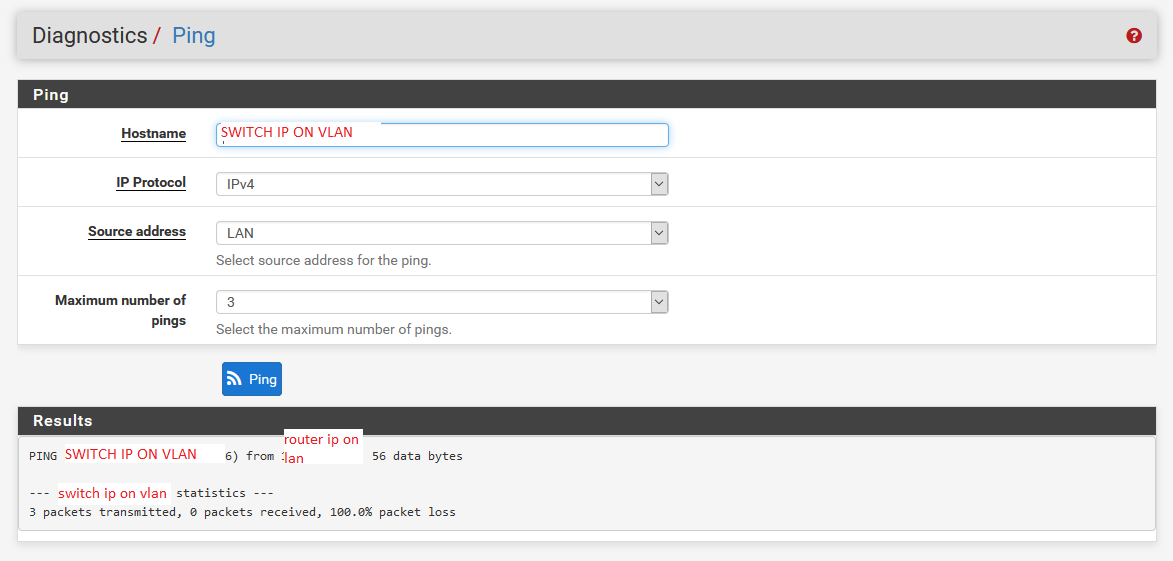
-
Ping from vlan interface:
To lan switch ip:
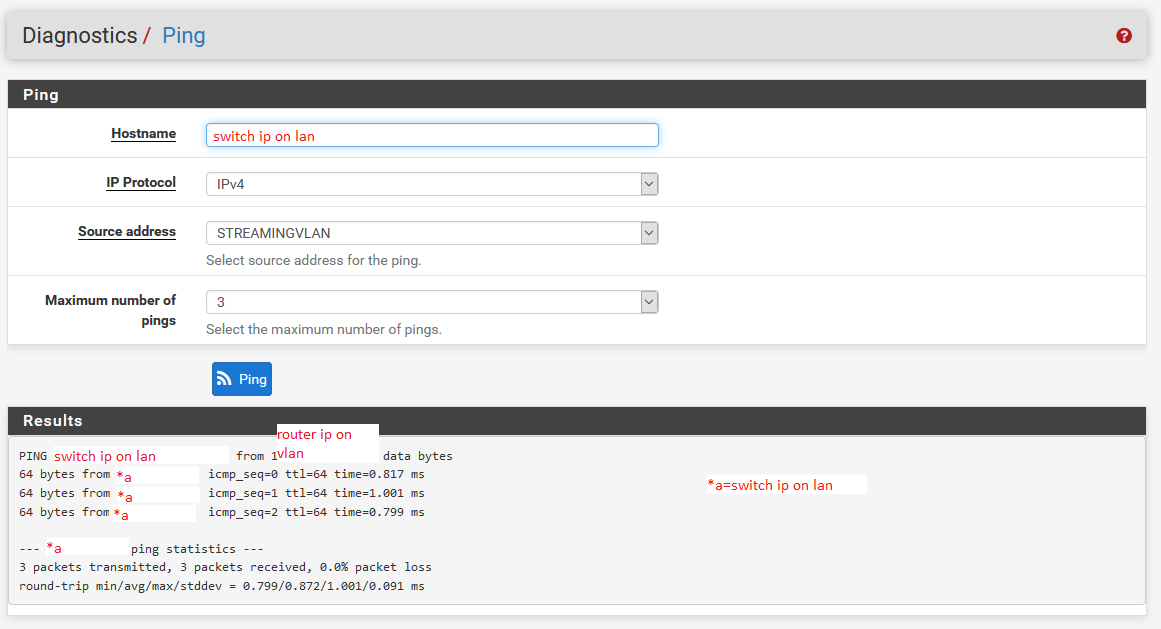
To vlan switch ip:
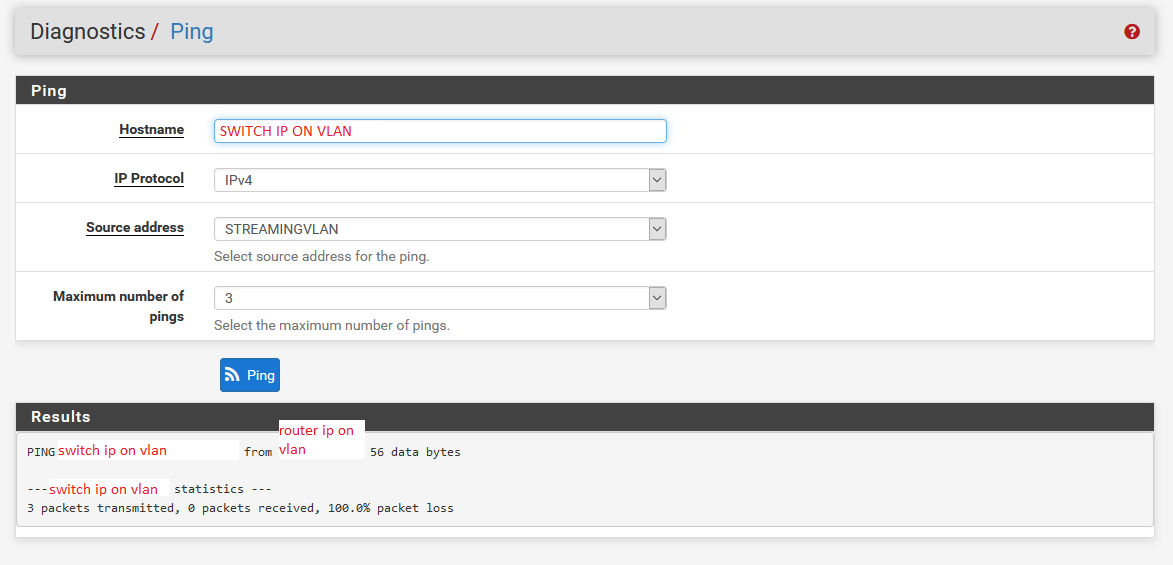
-
@SlayrNeo I'm pretty sure your ping from LAN to VLAN switch IP fails, since your LAN interface has no rules to get to the VLAN network. The 3 allow rules on the LAN tab are: anti-lockout, all LAN to the WAN-DHCP gateway, and all LAN to the NordVPN gateway. There is nothing there to keep traffic from LAN inside your internal networks. You are forcing all of it out the 2x gateways you've got there. You need to get that disabled "Default allow LAN to any rule" back online. Do you really want to force all of your LAN traffic out the NordVPN gateway like that?
And, I think the VLAN router to the switch IP on the same VLAN might be the same problem. You are forcing all VLAN traffic out thru the WAN_DHCP gateway. You also have an alias "Streaming", but you don't explain what those machines/hosts actually are. So, it's a mystery what's in there.
What you could do, to put some devices in these networks put thru the VPN and gateways you want, are to make aliases for just those machines, and use those aliases in an allow rule. Then below this allow rule, set the default allow any rule at the bottom. So, the "approved" machines in the alias will use the VPN gateway stuff first, and the "not approved' devices will use your default gateway next. Make sense?
Also, since these are internal private networks, you don't need to mask the IP addresses like you have.
Jeff
-
@akuma1x said in Pfsense with AP dhcp server settings:
@SlayrNeo I'm pretty sure your ping from LAN to VLAN switch IP fails, since your LAN interface has no rules to get to the VLAN network. The 3 allow rules on the LAN tab are: anti-lockout, all LAN to the WAN-DHCP gateway, and all LAN to the NordVPN gateway. There is nothing there to keep traffic from LAN inside your internal networks. You are forcing all of it out the 2x gateways you've got there. You need to get that disabled "Default allow LAN to any rule" back online. Do you really want to force all of your LAN traffic out the NordVPN gateway like that?
Yeah those rules are:
Specific websites just go to wan
Everything else is forced to vpn, don't want lan to connect to internet directly.And, I think the VLAN router to the switch IP on the same VLAN might be the same problem. You are forcing all VLAN traffic out thru the WAN_DHCP gateway. You also have an alias "Streaming", but you don't explain what those machines/hosts actually are. So, it's a mystery what's in there.
Alias streaming is all ip from 150-200. But now I think about it, maybe this is blocking the ip's from switch and router on vlan(under 100).
What you could do, to put some devices in these networks put thru the VPN and gateways you want, are to make aliases for just those machines, and use those aliases in an allow rule. Then below this allow rule, set the default allow any rule at the bottom. So, the "approved" machines in the alias will use the VPN gateway stuff first, and the "not approved' devices will use your default gateway next. Make sense?
Also, since these are internal private networks, you don't need to mask the IP addresses like you have.
Jeff
Beter safe thans sorry

Thanks, I will look into the vlan rule.
-
ok i tried to change rules:
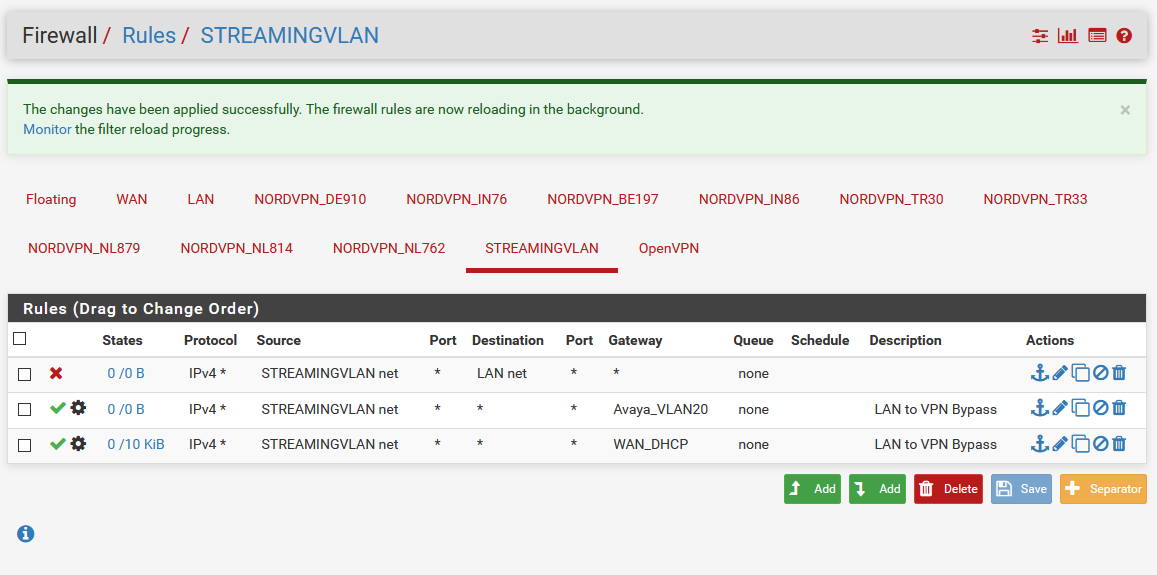
What I also discovered: when I am on lan network I can connect to router with it's lan ip and it's vlan ip, but I can only connect to switch with it's lan ip.
still no automatic ip-address on the vlan 20 ports on switch...
What I also discovered was that the pfsense router sees 2 additional gateways. Those are the standard lan(vlan1 on switch), but it also sees the vlan20. Do I need to do something with this? As you can see in screenshot I tried to add it in rules, but still nothing(even with that rule disabled).
What I want:
Ports 1-24 and the ap on port 46 on switch on vlan1(standard lan) with dhcp connected on port 48. ALL traffic from devices connected to these need to go through vpn.Ports 25-36 and the ap on port 46 on switch vlan20 with dhcp connected on port 47. ALL traffic from devices connected to these need to go to wan(internet) directly.
First part works, second part nothing... ;)
-
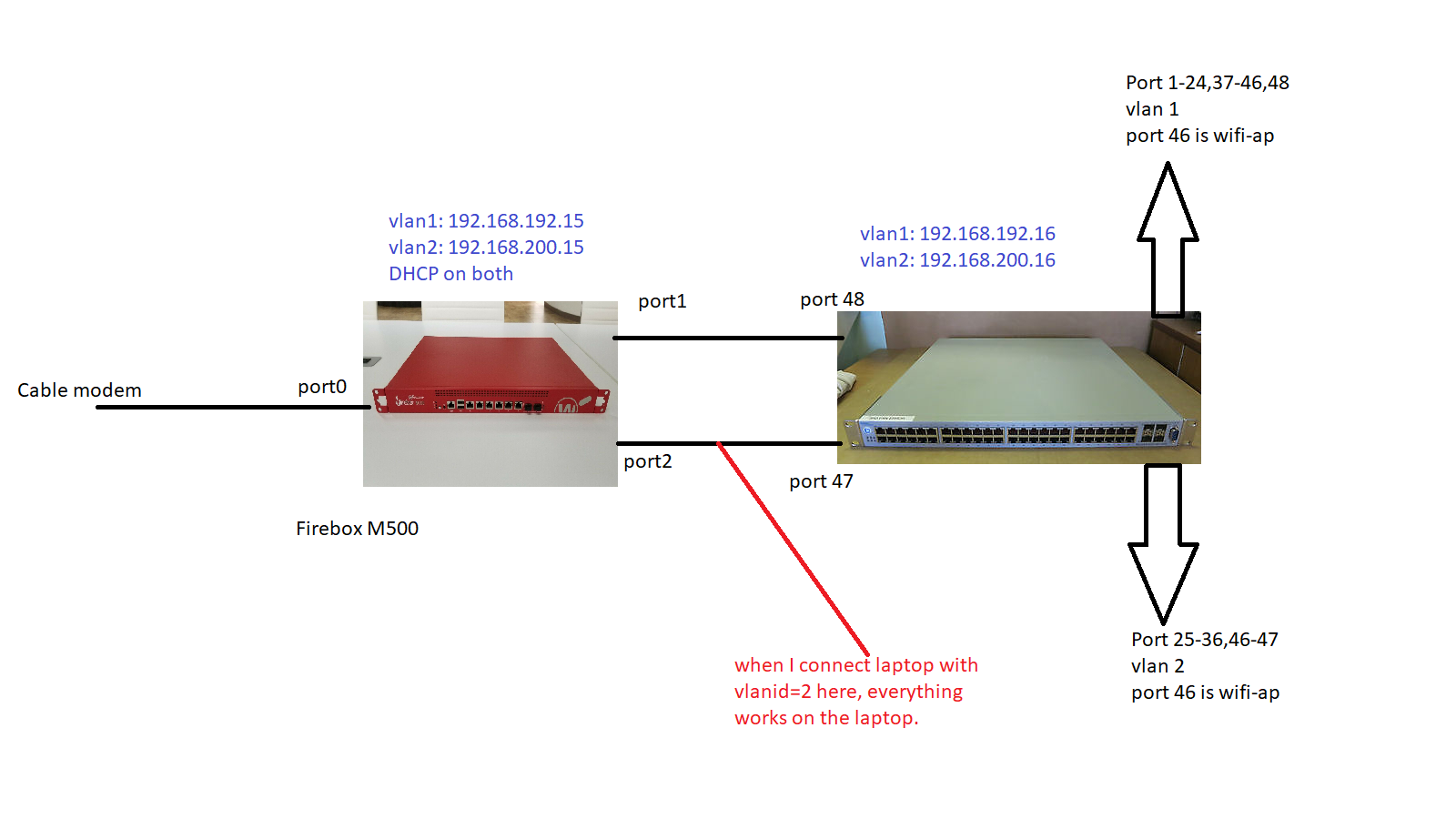
this is my setup
-
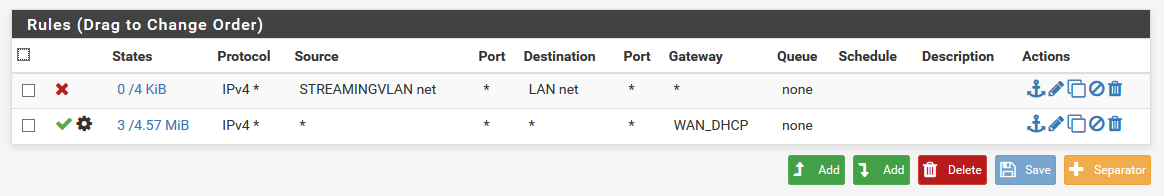
Ok, new switch (linksys) and now I am getting somewhere.
When connecting to vlan2 port on switch I get vlan2 ip from pfsense router and can access router.
When connecting to vlan2 wifi, I get vlan2 ip from pfsense router and can access router.
When connecting to port 3 on router(port1=wan, port2=lan, port3=vlan2) with laptop with configured vlan2 id, I get vlan2 ip from pfsense router and can access router.In all cases I have access to vlan2 devices and can't access lan devices. I have to use vlan2 ip from router to access it and can't access it with lan ip from router. So far so good.
Now the problem: in all cases I don't have internet on vlan2. I do have internet connection on lan net, but unfortunately not on vlan2. This looks like a pfsense problem(as plugging directly laptop on router gives same result). Uploaded above is the rule I have. First I had source: Streamingvlan-net in both rules, but that didn't work either.
Where do you think the problem is?
-
found it, I had to make a rule in Firewall-Nat-Outbound