DNS Leaks using DNS Resolver
-
Hello all,
I am having a problem with DNS leaks from my ISP
On pfsense, I have the DNS Resolver configured to forward queries to the Upstream DNS servers in the General Setup.
I have one DNS server for an OpenVPN client which is set to be the server for that specific gateway
Then I have three other DNS servers which I have set as none for now because if i set them for the WAN interface they get bypassed everytime. When they are set as the servers for my WAN connection, they show up but so do the servers from my ISP.
My network is set up like this:
My netgear modem acts as the DHCP server for WAN, its address is 192.168.1.1 and its giving my Pfsense an ip address of 192.168.1.2
Pfsense box LAN is set to 192.168.2.0/24 and runs DHCP for that network
Then i have another interface that has a static IP of 192.168.200.1 and that runs DHCP. I call that houselan
Then there are two VLANs set up: 192.168.3.1/24 and 192.168.4.1/24On the Netgear modem internet settings, i can specify the DNS servers to use. I am trying to avoid using these servers because I would prefer all DNS queries to be handled by pfsense and the DNS resolver. After multiple configuration changes to the DNS servers and the DNS resolver I am still seeing the Netgears DNS servers (which are provided by my ISP unless I set them) show up when I got to ipleak.net
I have set up Port Forwarding rules to try and prevent DNS queries going outside pfsense but that does not work, I will still see the DNS servers specified in the Netgear modem.
I have kept the "Allow DNS server list override" checked off, still was getting a leak with my modems DNS servers
Ive tested the "Disable DNS Forwarder" option both on and off, didnt make a difference either way.
These settings changes were coupled with a restart of both the DNS resolver service and the DHCP service for the LAN that I was working with.
Ive followed the directions here to try and block out or redirect the DNS queries
https://docs.netgate.com/pfsense/en/latest/multiwan/interfaces-and-dns.html
https://docs.netgate.com/pfsense/en/latest/recipes/dns-redirect.htmlFor the time being, I have set the DNS servers that I want in the Netgears Modem settings and this is fine, except for the fact that I want to redirect DNS queries based on the WAN interface.
Any assistance or advice is greatly appreciated. Thank you.
-
hi,
Weekend is coming up, so most of use are focussed elsewhere.
I advise you to use the word "leaking' and the search function of the forum.You will find very quickly some (many, actually) posts about what leaking is. The definition.
Very rapidly you find out that it's mostly a buzz word, used by VPN service sellers.Just a hint :
@ahiggs117 said in DNS Leaks using DNS Resolver:
On pfsense, I have the DNS Resolver configured to forward queries to the Upstream DNS servers in the General Setup.
When you install pfSense, there is no and can't be a DNS issue, as the default mode is what one could call the perfect mode. That's why it is default.
'Forwarding' should be done on your LANs (to pfSense), which is the default since the creation of IP, DHCP, DNS etc. The default DHCP-client mode for every LAN devices takes care of this.If you have to 'give' or 'sell' (or leak, as it is identical) your DNS traffic to some "fortune 500" company, or you want to give it to your ISP (who is gona sell it to these companies ;) ) then ok .... your choice.
But why creating a hole first, and then speaking about leaks ??True, in the past, your ISP gives you an (WAN) IP, mask and a gateway. Often they also handed you over one or two IPs, pointing to their 'internal' DNS servers. This could speed up things a little bitffor you, as fast Internet connections were expensive, and you were using some 33,6 kbits /sec POTS line.
That situation doesn't exist any more. Your main DNS should be the Internet itself, the way it was designed : https://en.wikipedia.org/wiki/Root_name_server (these are used by default). -
Instead of the word leaking, would the word override be better? I did use the search function of this site as well as a few hours just esearching for a solution. I wouldnt be posting a question if I had been able to find the answer myself. Yes, its the weekend, but you also werent required to answer, but thanks anyway, I guess? This isnt a production server nor is it that dire so I can wait for advice or an answer.
My Netgear modem has DNS servers set inside it, pfsense has DNS servers specified in the General Setup section.
When I use a service like ipleak.net or dnsleaktest.com, the IPs that are set in the DNS settings of my Netgear modem show up along with the ones that I've set in pfsense. If pfsense was perfect, I think it would just use the DNS server IPs that i have set in pfsense itself. This is not the case. If I have two WAN connections and I want to make it so each WAN connection uses a specific DNS server, which I should be able to do according to pfsense settings and also the documentation around it, but it still shows my modems DNS servers, is it realyl doing what its supposed to. I obviously have a hole somewhere or have misconfigured something, so what could it be with all of the information that ive given so far? Or where should I be checking? -
Which DNS-servers are shown on the dashboard of pfSense? If you really have turned off DNS Server Override, they shouldn't be listed there.
-
@ahiggs117 said in DNS Leaks using DNS Resolver:
This is not the case. If I have two WAN connections and I want to make it so each WAN connection uses a specific DNS server
This is where I am a bit confused.. While yes you can setup multiple dns, and have specific ones use a specific connection by setting a gateway for that dns server.
And while you can policy route a client to use a specific gateway - what is that client using for dns? If it just asks pfsense. How do you suppose you are controlling which path pfsense uses to query dns.. If your forwarding to multiple dns, its not really possible to know which one will be queried at any given time..
Showing us your actual config and which dns setup in pfsense, and what your dns leak test is showing would help us figure out what is going on.
edit: Keep in mind in this day an age of CDN, global dns providers - there is little reason to list more than 1.. They are all hosted on global networks via anycast.. And highly unlikely to go down, if they did it would be a major global outage.. So it is better to just use 1 dns provider if you insist on forwarding to someone.. So you are sure which provider you are using - the other problem with using multiple providers is they provide different info - if you are using a filtering dns - cloudflare filtering is going to be different than say quad9.. Setting both to maybe be used, you have no idea which filtering you will get. And once something is cached, that is what would be used. You should pick 1 dns provider that filters how you want, and only use them. So you are sure what filtering is taking place, if any..
This is no longer the days of users using ISP dns that was almost always under powered, and lack of maint.. And they provided you multiple IPs normally to just load share their users across nameservers. This is no longer the case with global DNS providers.. And the reliability and performance of current systems. There is little reason to ever list more than 1 forwarder anycast address.
-
@ahiggs117 said in DNS Leaks using DNS Resolver:
or dnsleaktest.com
Here you got my test result :
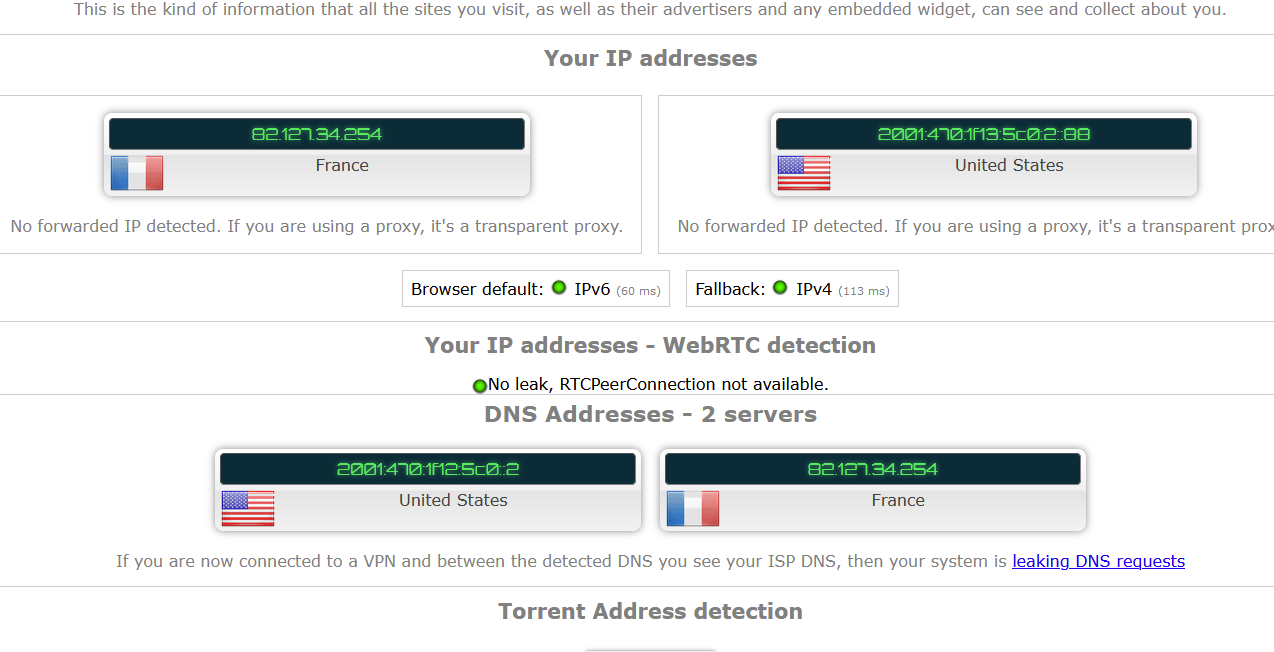
Note that my WAN IPv4 is correct. The IPv6 also, although that "WAN IP" is actually the IP v6 of my PC, somewhere on my LAN. But that another story.
The 2 DNS shown ..... is my IPv6 tunnel IP - the one that ends with a "::2" => ???? and the other IPv4 is my .... WAN IP => ??^2 My WAN == my DNS ?
Yeah. As said, it's Friday.My main conclusion is : nice looking page full with no useful information. At least, I qualify it, using my connection, as close to BS ...
@ahiggs117 said in DNS Leaks using DNS Resolver:
My Netgear modem has DNS servers set inside it
So, even if it has a modem thing integrated, converting, for example, cable or ADSL signals to an pure IP flux, it is NOT a modem but a known router.
So, like my ISP router, which uses ADSL to connect to my ISP, it probably has it's own ISP-DNS. But pfSense isn't forwarding to my ISP router, I'm not forwarding at all.
I use the default Resolver mode.To complete the question of @Bob-Dig : you should be seeing this :
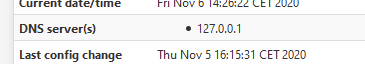
127..0.0.1 works great ;)
And it is the default setting. Netgate was right !@ahiggs117 said in DNS Leaks using DNS Resolver:
werent required to answer
True. Just see it as a way to start up the thread ;)
You use 2 WANs.
Good question : which WAN is used for requests from unbound ?
Both ? Using round robin ? Using the "lowest latency known" ? Random ? Other criteria ?
In a best case - or worst case ^^, the answer can be found in the manual == the open source code. -
Here is my Dashboard and also the config for the DNS Resolver
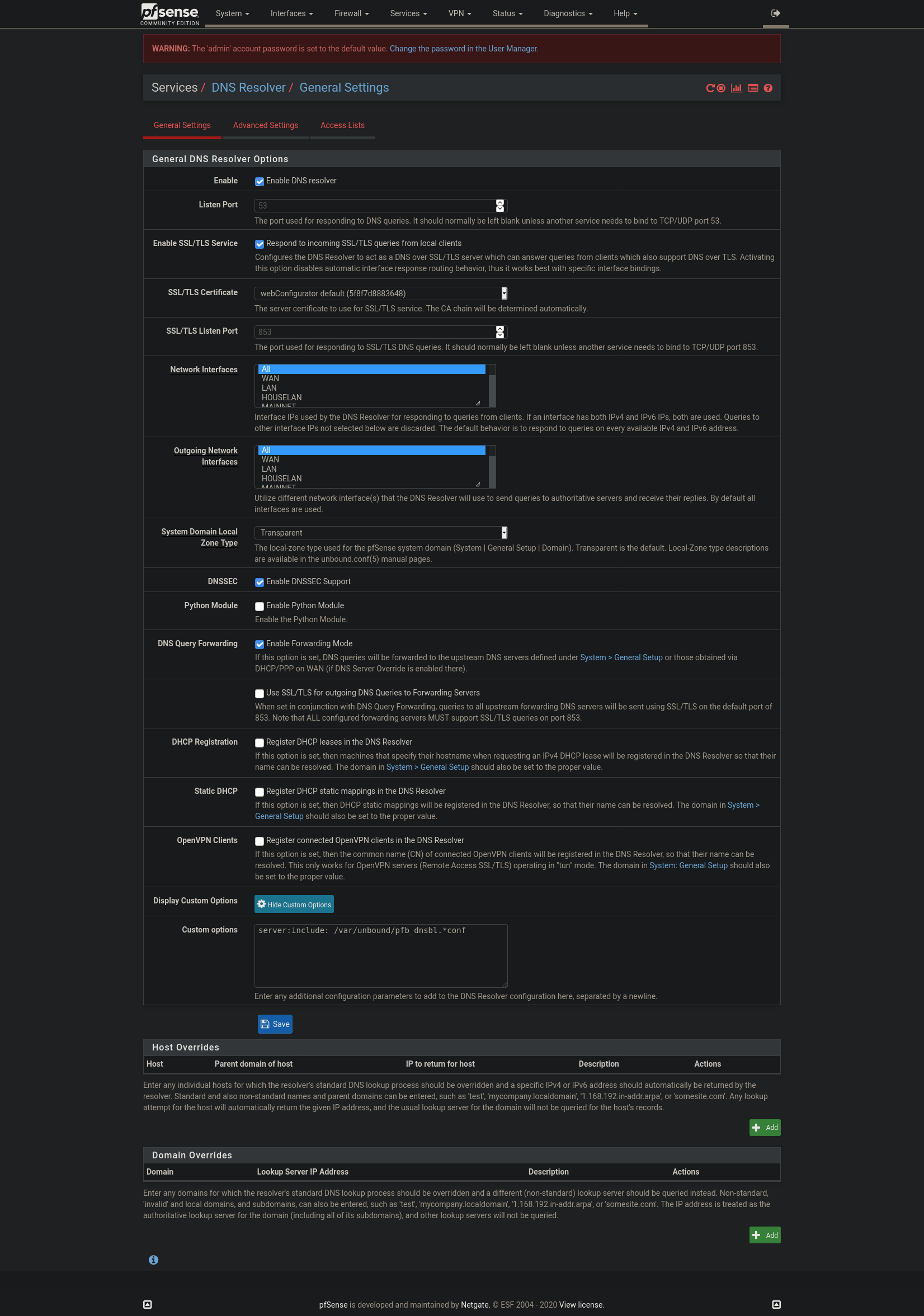
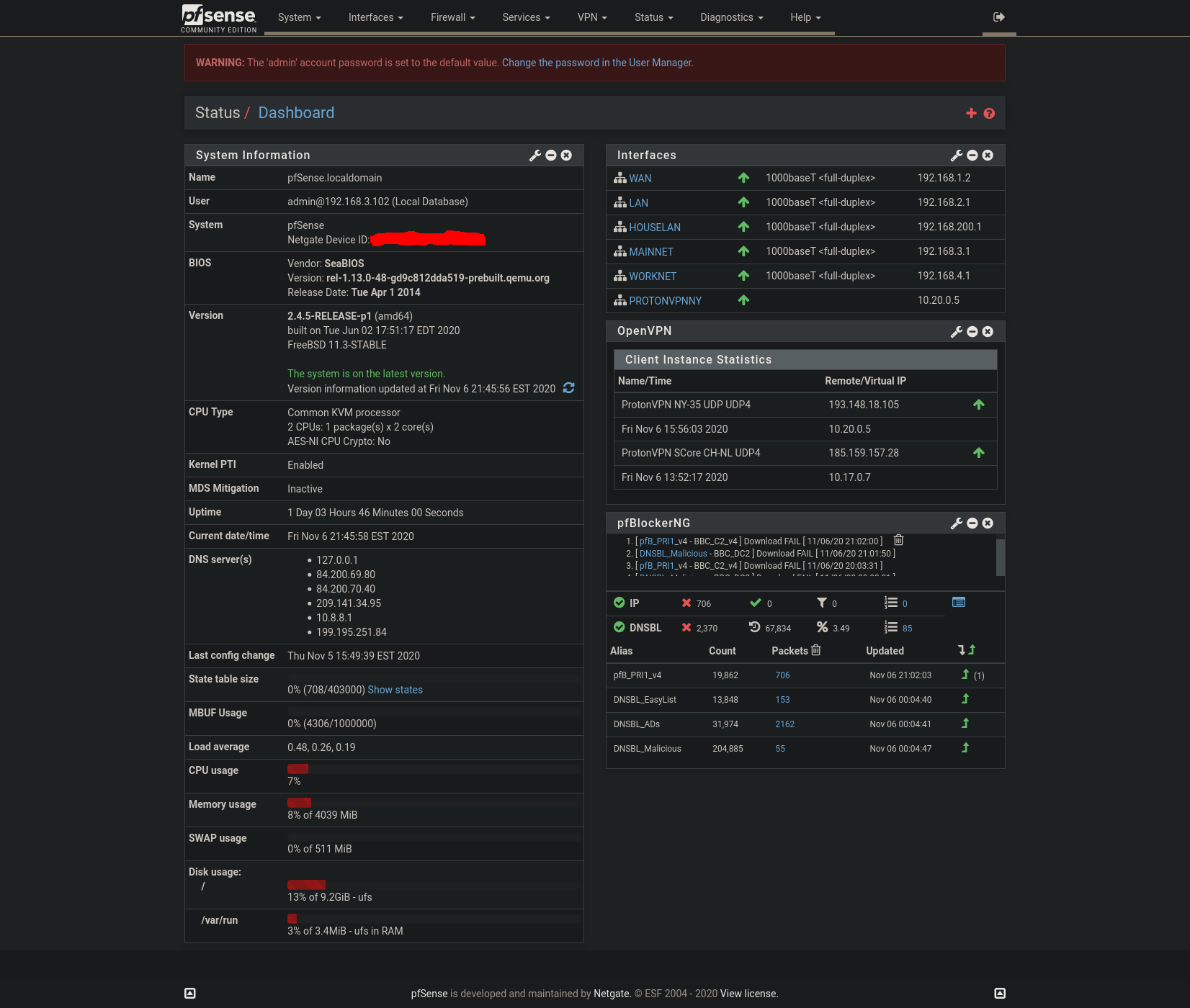
-
And who is 10.8.8.1 for dns?
Why do you have dnssec enabled if your forwarding - pointless.. Also why are you listening via tls? locally?
Where are you settings for dns..
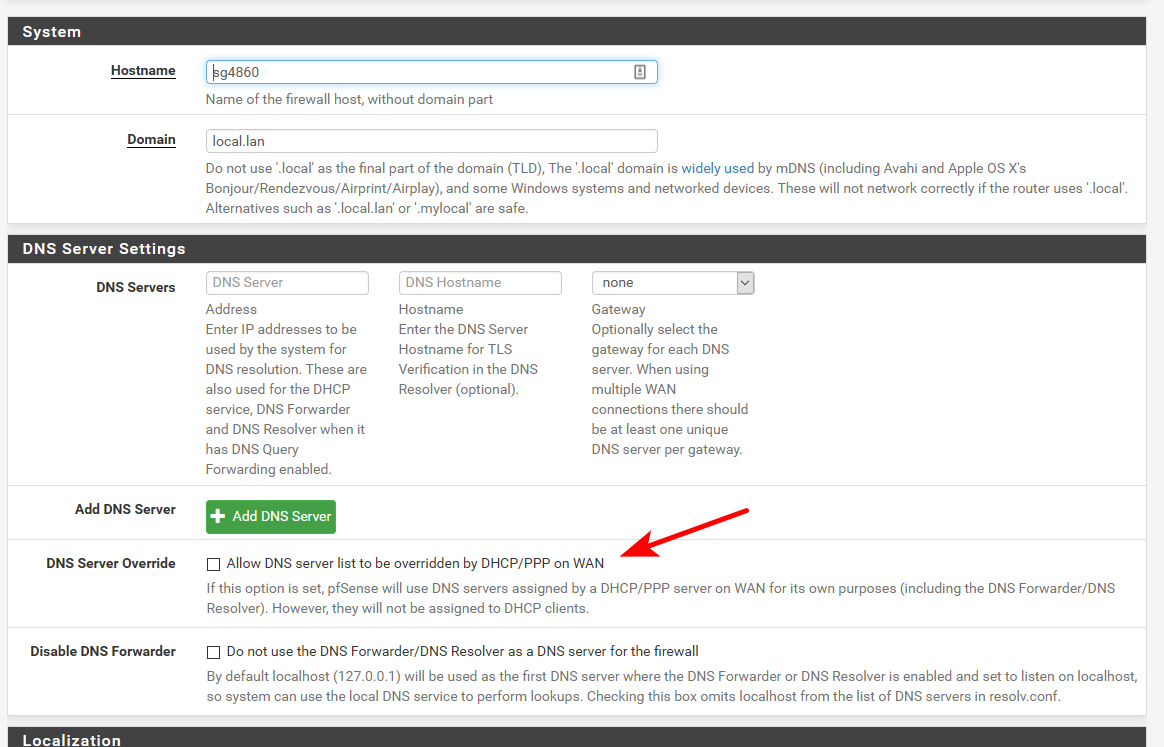
-
10.8.8.1 is for the ProtonVPN gateway. I have set up NAT forwarding rules for it.
Here are the DNS server settings, sorry, will double check when I post now to make sure everything is in the message.
These are the NAT settings that I have, for context about the Proton gateway
edit:
Here are the settings in my Netgear modem.
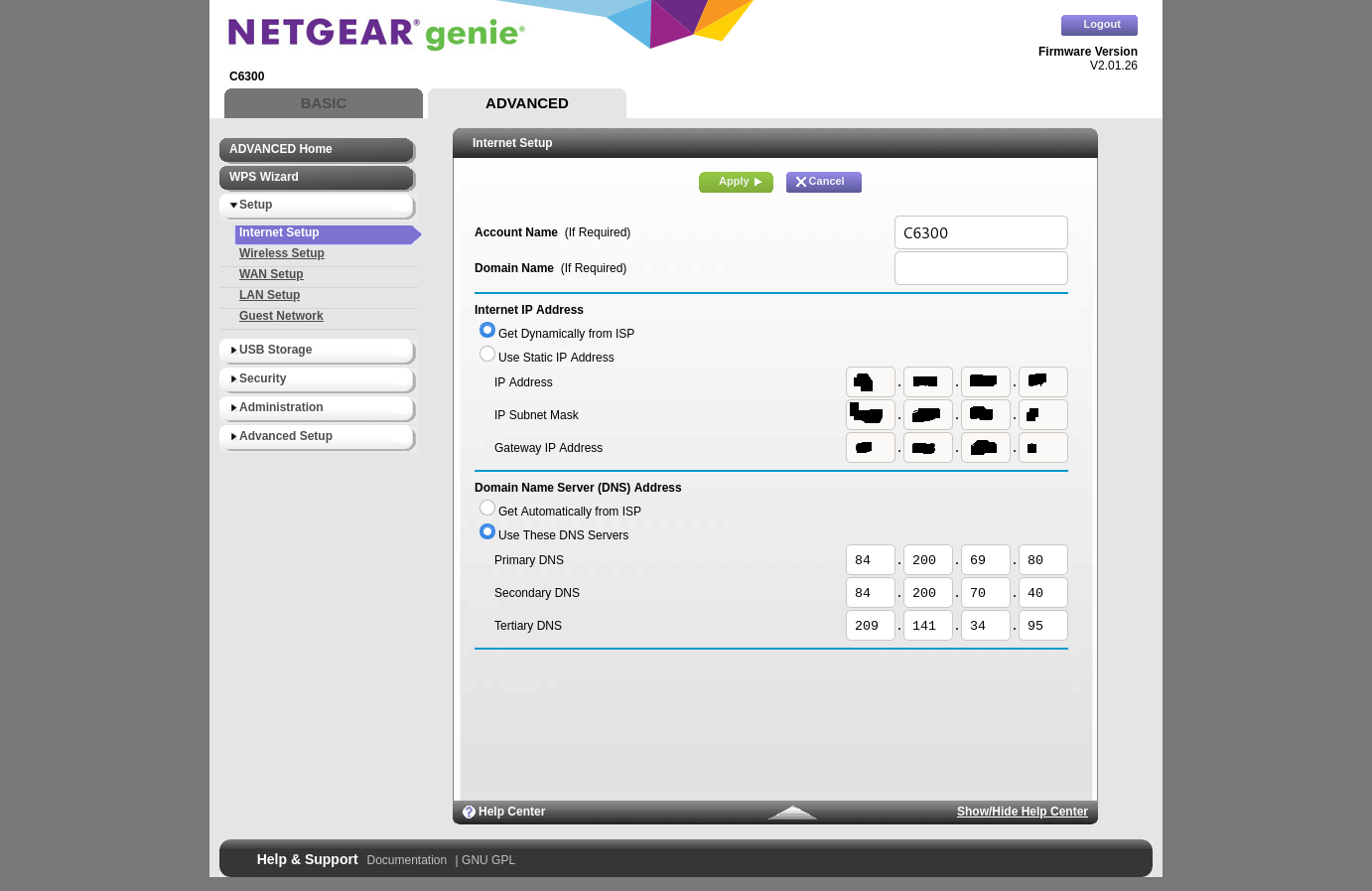
I have set the desired DNS servers so when I run a leak test, it only shows one or more of these three. But when I have it set to get automatically from ISP, ill see their DNS servers show up in a leak test. This is what I am trying to avoid. There is no way for me to leave these blank, dont even know if that would serve for this but either way, my DNS requests will be sent to one or two of the servers I have set in pfsense but I will also see my ISPs DNS servers in the leak test. I will change this back to my get automatically from ISP and run a leak test at dnsleaktest.com and ipleak.net so i can show the results
-
Pfsense is not set to ask that router for dns - is I don't see it listed.. so pfsense would never ask it.. Unless pfsense was set to get dns from isp... Which you turned off - so unless something asks that router for dns - your isp dns would not be used.
-
This is exactly my frustration. I'm a complete noob to pfsense so I wasn't sure if i missed something or that I misread directions on how to set this up.
I'm going to set the modem router to use my ISPs DNS and then run a couple tests so I can get screenshots of the repro.
@johnpoz Thanks for confirming that I haven't done this to myself and just set it up wrong. -
What client are you testing from - if its on that routers wifi, and using that routers dhcp the client would ask your router, which would then ask whatever you have in that router for dns.
-
I was using wifi, which was connected to a wifi AP that Ive setup. That is set to forward all requests to pfsense. I also am testing on a client that is connected to a switch that has two VLANs running through it. The clients I was testing with were not connected to the Netgear routers wifi.
Here are the DNS tests that I ran to see what happens when I set the modem router DNS to googles resolvers 8.8.8.8 and 8.8.4.4 pfsense still has the same DNS servers as before.
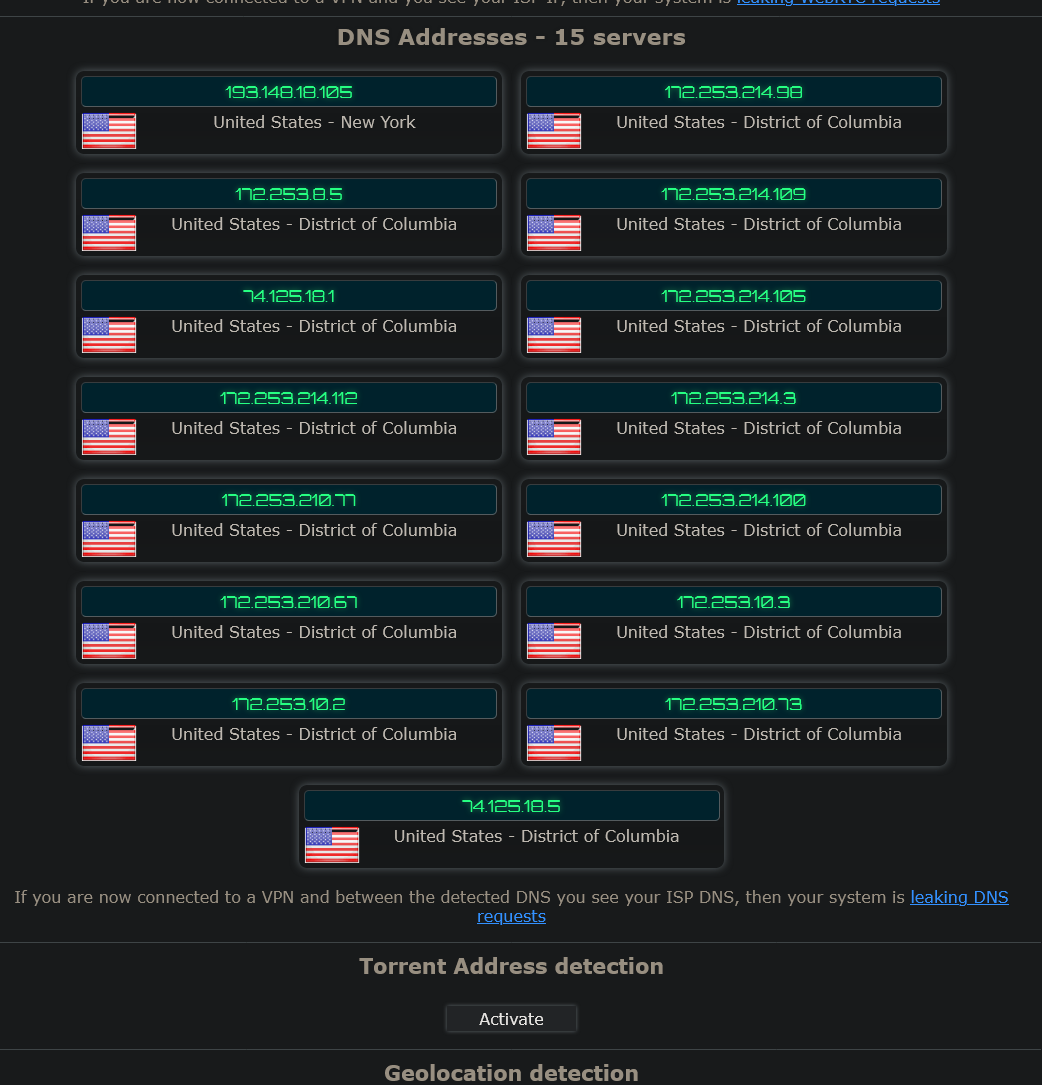
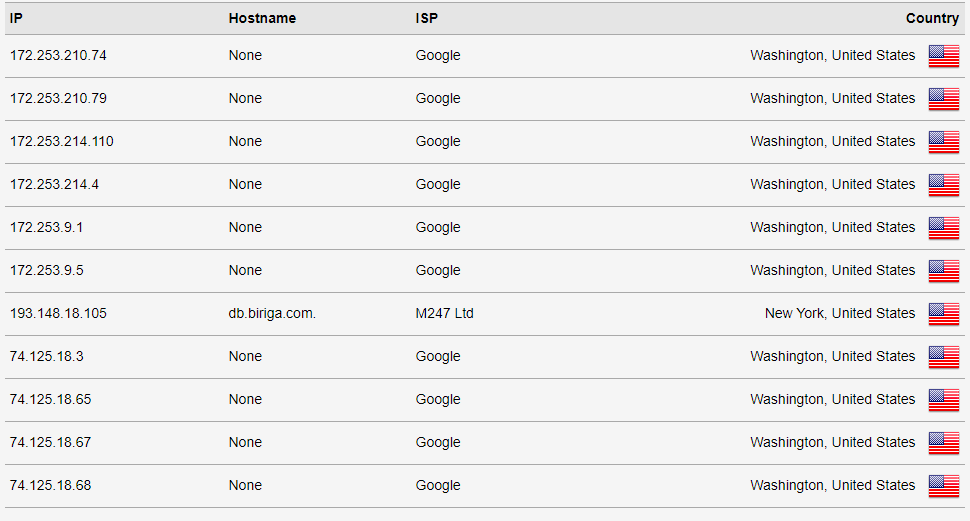
-
You understand that is what suppose to show up right if your using google.. did you think it would be 8.8.8.8
You have no freaking clue to what your 10.8.8.1 could be doing - prob forwarding to google ;)
I would suggest as I stated before - pick 1!!! Don't try and use multiple.. For those nixnet ones - why would you not just use the anycast address?
Maybe your router is intercepting dns? Sniff on pfsense wan and validate it sending the dns query to where you think its going..
Just like how pfsense can intercept dns - your router could be doing the same sort of thing.
-
Haha yes, that is exactly what should happen because those are googles servers. Im not that dense, buddy. The reason I set those in the Netgear modem router is to prove the fact that DNS requests are getting handled there when they should just be handled by Unbound DNS resolver in pfsense.
The 10.8.8.1 is so the DNS requests are sent to the protonvpn interface so that the DNS requests made through the protonvpn interface go through protonvpn.You can clearly see that the 10.8.8.1 should only be used by the protonvpn interface thats set in the general setup in one of my earlier posts.
Shouldnt ubound be stopping my ISP from intercepting requests? Isnt that part of the point of it lol? -
Well I would think you router is intercepting your dns then...
Its a common setting in many a soho router.. Prove it to yourself.. do a sniff on pfsense wan - if you only see it sending queries to what you set, then your router is intercepting the traffic.. Just like pfsense can do if you set that up.
You can clearly see that the 10.8.8.1 should only be used by the protonvpn interface thats set in the general setup in one of my earlier posts.
But you don't know when pfsense(unbound) would use those.. You have multiple dns listed - which interface used to talk to something doesn't mean its not used.
If you have dns 1,2 and 3 listed as forwarders - any of those can be used.. You don't have control over when which is used..
I would for your testing, turn everything off but 1 dns in unbound.. And then sniff on your wan - do you see it sending to that IP.. But your dns leak shows what your router is using - then its intercepting the traffic!
Just like you can setup pfsense to intercept traffic... Here I set my client to use 4.2.2.2 as dns
Connection-specific DNS Suffix . : Description . . . . . . . . . . . : Realtek PCIe GbE Family Controller Physical Address. . . . . . . . . : 00-13-3B-2F-67-63 DHCP Enabled. . . . . . . . . . . : No Autoconfiguration Enabled . . . . : Yes IPv4 Address. . . . . . . . . . . : 192.168.9.100(Preferred) Subnet Mask . . . . . . . . . . . : 255.255.255.0 Default Gateway . . . . . . . . . : 192.168.9.253 DNS Servers . . . . . . . . . . . : 4.2.2.2 NetBIOS over Tcpip. . . . . . . . : EnabledAnd before I tell pfsense to intercept that via your dnsleak test site - I see exactly that, 4.2.2.2 is a level3 public dns... So if I set that level3 is what shows as dns doing the lookups.
I then set pfsense to intercept the traffic - and even though my client is still sending to 4.2.2.2, you can not see that pfsense intercepted the traffic and my public IP (resolver) is what is seen as the dns on the leak test.
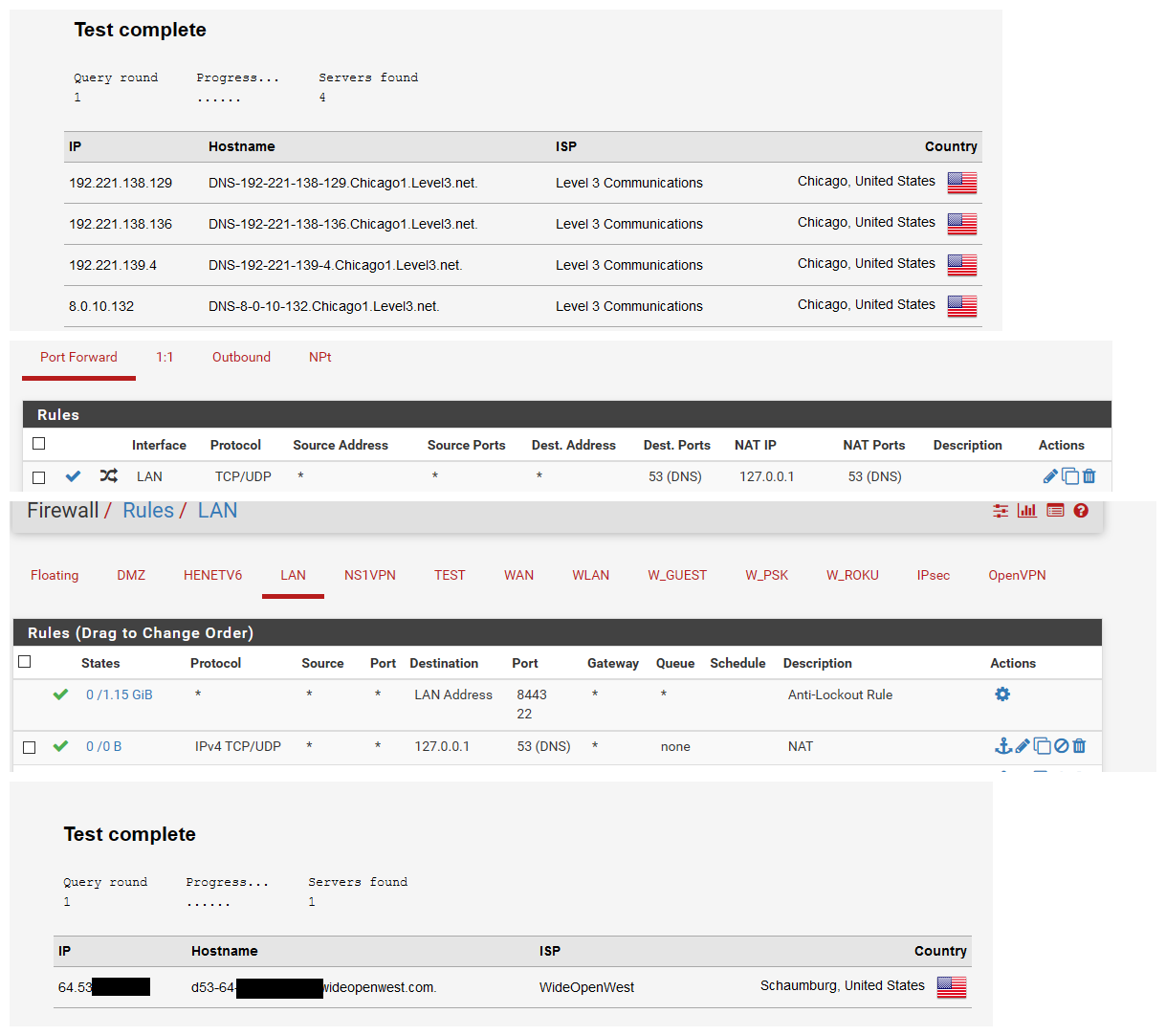
If your router is doing dns intercept - that is exactly what would happen no matter where pfsense is trying to query for dns.
-
A Netgear doing DNS intercepting ?
Google up the firmware, that would be known on the net.The ISP doing intercepting, that would be the next question.
-
This post is deleted!