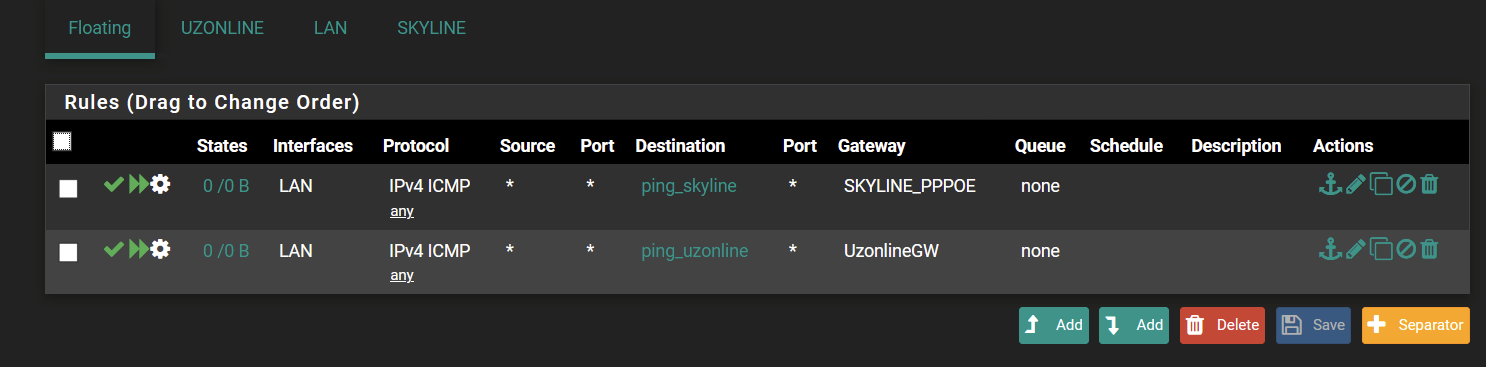
Firewall rules does not apply to pfsense hosted machine
-
I am using pfsense as my home firewall and configured multi-wan setup.
In addition, I have installed package 'Telegraf ' package for exporting my pfsense stats into InfluxDB, also in 'Telegraf' configuration I have enabled 'Ping Monitor' for 4 different hosts.
Since, all ping packets go through the default gateway and I wanted to create separate rule for each ping hosts to forward them manually.
My goal is to track latency of each gateway/wan so I can complain to my ISP with solid facts lol. Also, I need to track that pings before I play online competitive games, to make sure it does not ruin my game.
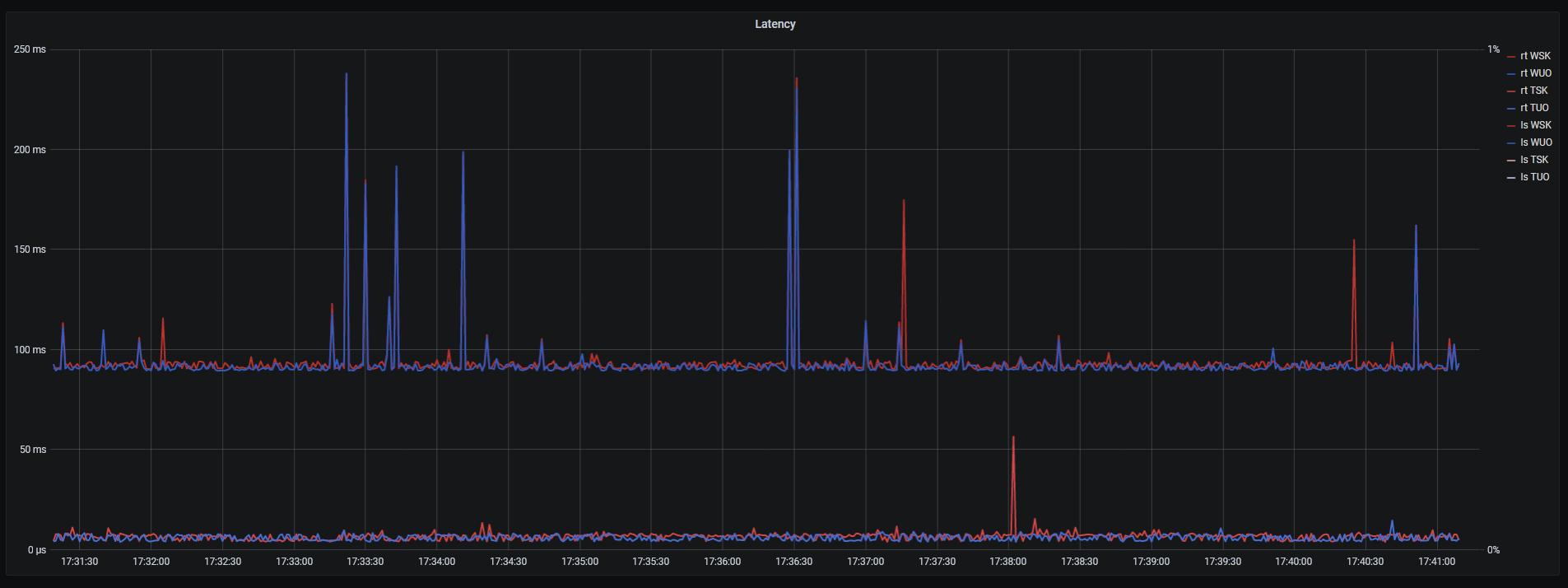
But these firewall rules does not work. When I start download from my default (UzonlineGW) gateway, in my Grafana stats I can see that ping to all hosts increase equally.
Also when I traceroute to all 4 hosts from pfsense shell, pfsense uses my default gateway (UzonlineGW).
My first thought was, it might be because pfsense is not in LAN, but I am not sure about that.
What am I doing wrong?
p.s. I am newbie here, sorry if I posted under wrong section of this forum.
-
Gateways are monitored out of the box, if you go to status, then gateways you can see each gateway and it's RTT/RTTsd.
If you want something more comprehensive, go to status, monitoring and configure a WAN monitor for each.
you can edit the default page or configure new ones using the wrench icon at the top.
Set left axis to quality and the right box as your WAN you want to monitor, set your desired interval time, 1h 8 hours etc. and choose show advanced, here you can save that configuration and give it a name - ISP1-WAN-8h for example, rinse and repeat for each WAN and configuration you want, then you can simply click them to see the status, this is also logged under, status, system logs, gateways
-
If a quick overview of current RTT will do, on the main dashboard page, click the plus sign top right and add the gateways panel, save and all your WANs will show up here right in front of you.
-
@rod-it That was useful thanks, but I am already using ping monitoring on gateways. Other pings should check other network segments. Let me explain.
What I want to achieve is to check 3 lines/routes/hosts/idk you name it :)
- Ping to my ISP's gateway.
- Ping to host that is located in my country (we call it TAS-IX/Center for data networks interaction).
- Ping to host that is located outside of my country.
In that way I can see where the problem is.
-
But you still need a machine to run those pings, unless your using some type of cron from the PF box itself, meaning your results may be skewed or an issue with the client, not the external side of things.
Maybe you want to consider traffic shaping to keep specific games as high priority instead?
-
@rod-it I was using Telegraf package to run pings from PF box itself.
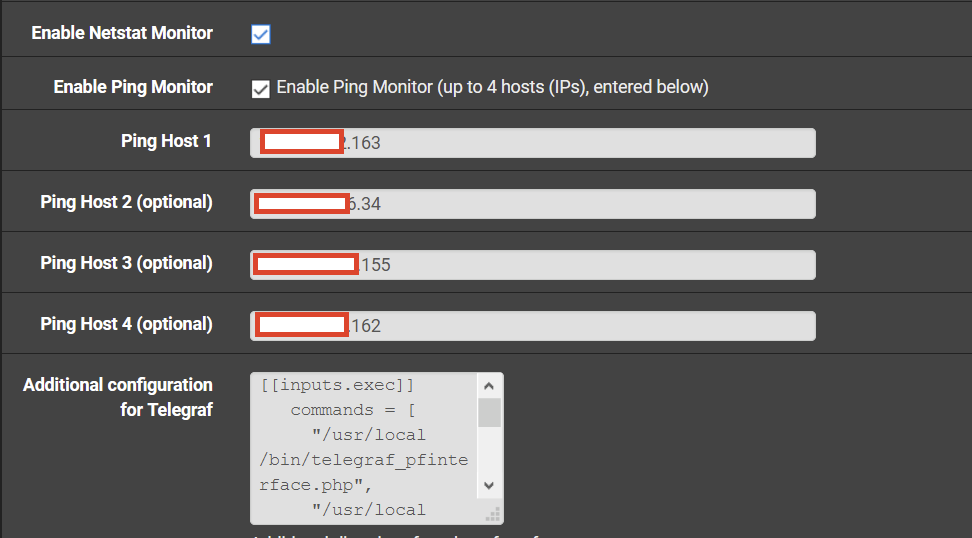
-
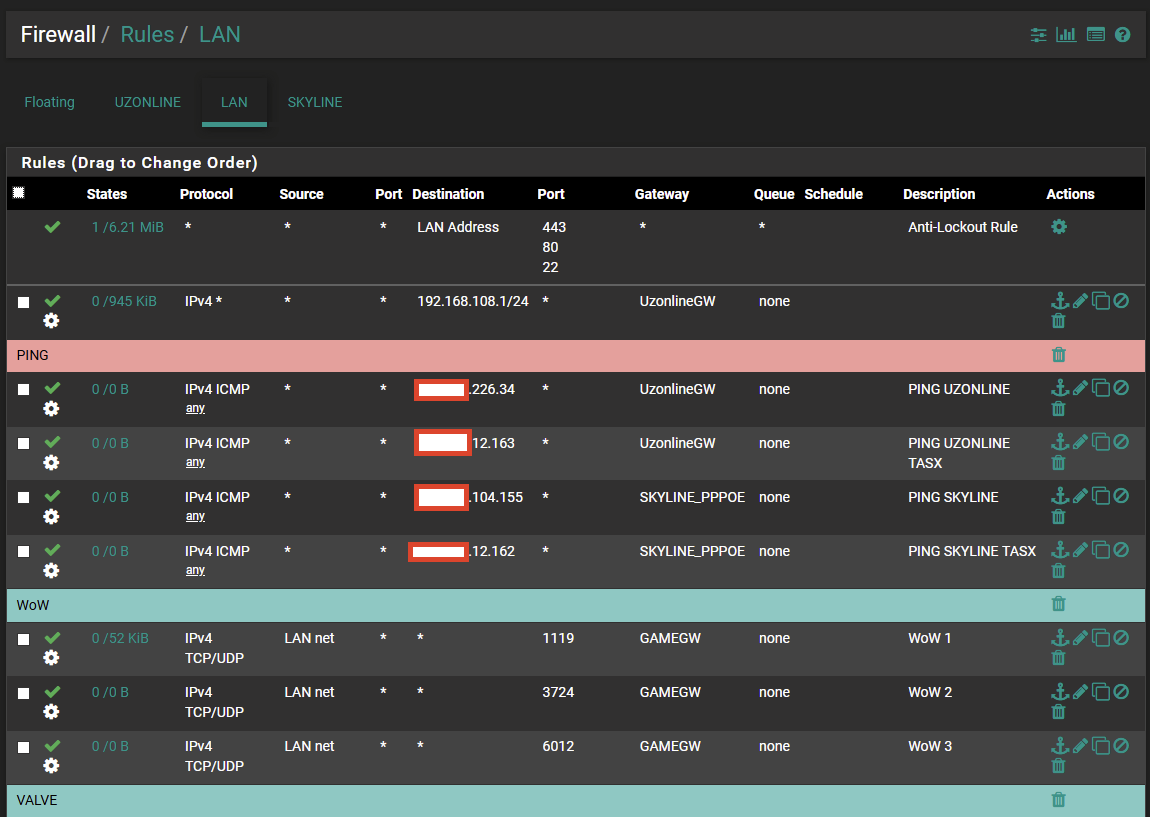
Looking at your screenshot above, those rules are not being hit as there are no states on them
If you set a ping going to one of those IPs, then run a packet trace within Pfsense, you should find some clues
You may want to change your source to LAN net though for those rules, or consider moving those rules to floating if you expect the source to be any network sending the pings.
To simplify things, I'd probably create an alias for your 2 IPs for each GW and use those so you only need 1 rule for each and likewise an alias for WOW with each of the 3 ports in, unless you're specifically looking for stats per FW rule
Your last rule shows a 3rd GW but you're not interested in pings for this one?
-
@rod-it I have created floating rules as you suggested.
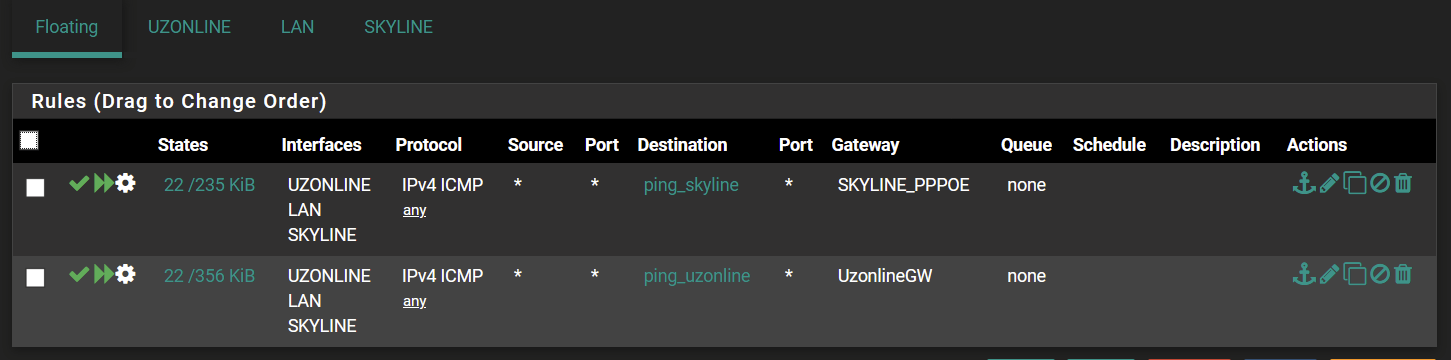
Traceroute shows that it is still using my default (UzonlineGW) gateway for all ping hosts.
3rd GW is Gateway Group, Where I set priority SKYLINE_PPPOE (Tier 1) over UzonlineGW (Tier 2)
-
Those are showing traffic now, but i would remove your WAN networks from the selected interfaces since oyu only want traffic going out to trigger those rules.
If you only have LAN as your internal network, that's all you want in the interface selection for that rule.
Having your WAN interfaces selected could be causing your current issue
I'd also run a packet capture to see what the traffic is doing, i dont have dual WAN to set it up and test it for you
-
@rod-it Oh, I am now deploying vm that will use telegraf (only input.ping). Those packets are coming from that VM :) sorry.
-
Forget pings for a moment.
If you specify 2 different source IPs and set their GWs, clearing any open states in the FW, do they route correctly over their respective WAN?
Are there any opens states for the old pings, if so clear the state table and try again
-
@rod-it I will try that later, thanks.
But I have found another thing, I have edited telegraf config file and specified source IP where pings should come from. smth like: ping -S 192.168.1.1 xxx.xxx.xxx.155
Now pings appear on Diagnostics > States
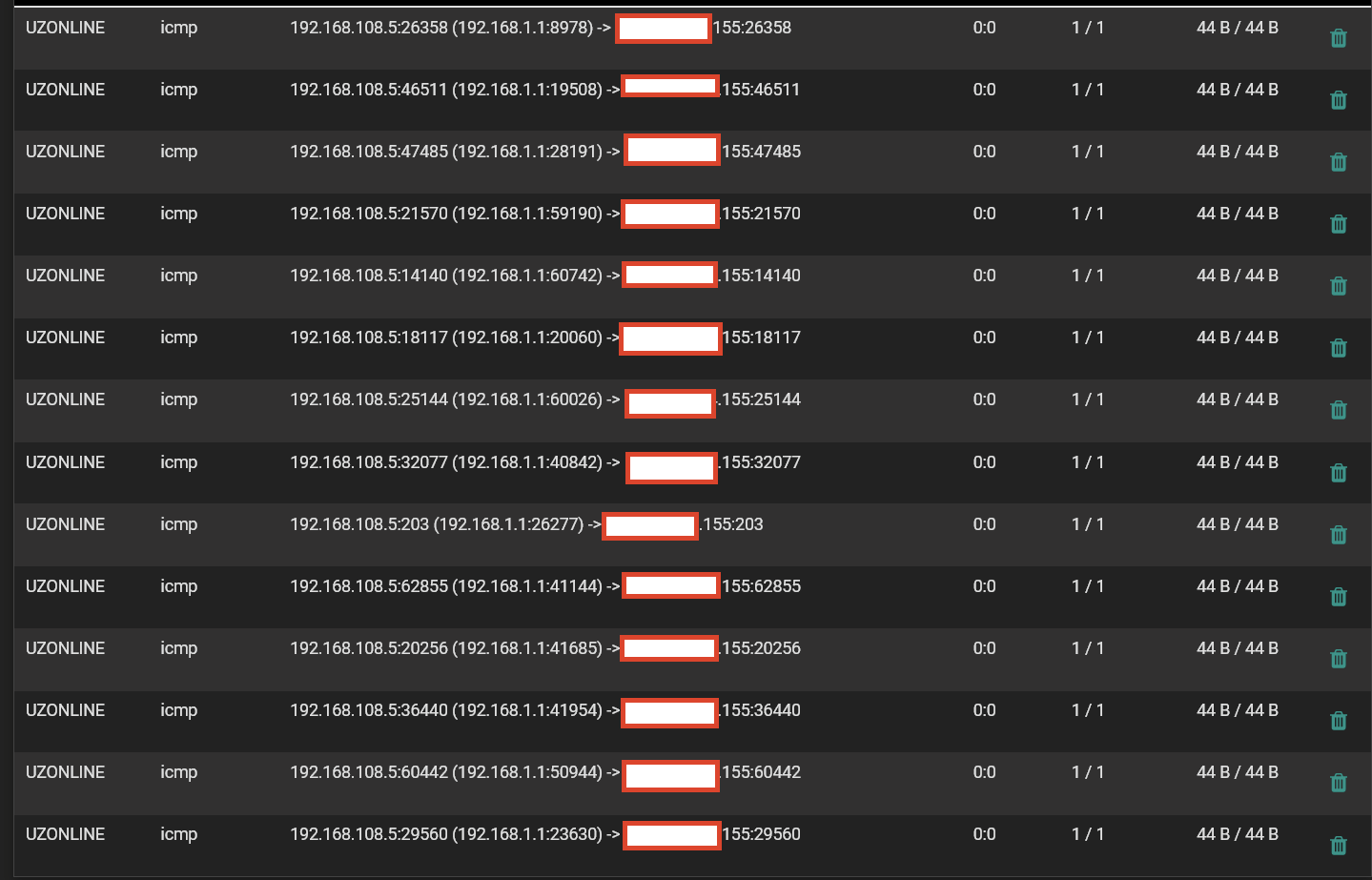
But somehow they do not want to obey the firewall rules (0 states/0 B)
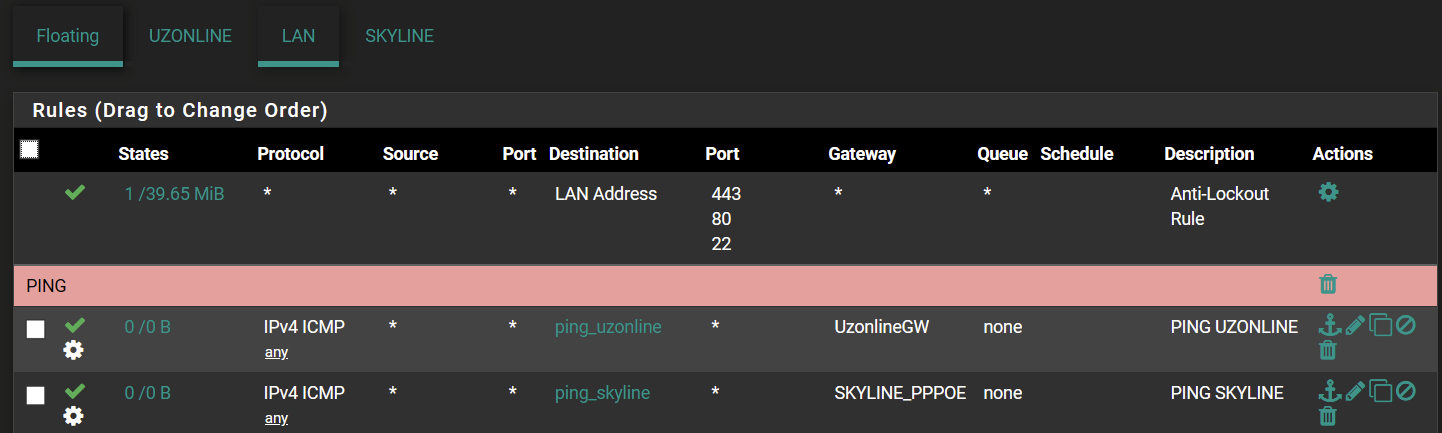
-
Your first screenshot shows your states from the OZONLINE WAN, you need to remove these from the interfaces on your floating rule. Then your rule can only come from the LAN network, you dont need the WAN networks selected for your use case.
You only want traffic going out of your LAN, not the WAN networks, so they do not need to be selected under the floating rule for your case.
Your second screenshot, if you're talking about LAN, ignore it, those rules can be disabled/deleted, floating rules are triggered first, so these will never be hit and were not being hit anyway.
FYI, I am not a network of firewall guy by any means.
-
-
I'd start by nailing a single client to each gateway and re-run the pings.
Hover over your destination alias too and check the IPs listed are the one you are pinging.
I'd still get that packet capture running so you can see what is happening, but do make sure you clear the states table otherwise you've already got open connections that will be re-used.
-
@rod-it okay, got it, thanks.