Default GW not being used
-
Hi,
We are using pfsense version 2.4.4-RELEASE-p3 installed on Dell R620.
We use dual WAN. I added the configuration for our current setup and some traceroute screenshot.Wan2 is set as default so all trafic should pass through it but whenever we do a traceroute,
it goes through the WAN1 ip. Also, when WAN1 becomes down or has packet loss, the connections are affected, vpn disconnect, servers loose connections etc...I'm wondering if there is an error in our configuration or if I'm missing something.
Thanks for your help!
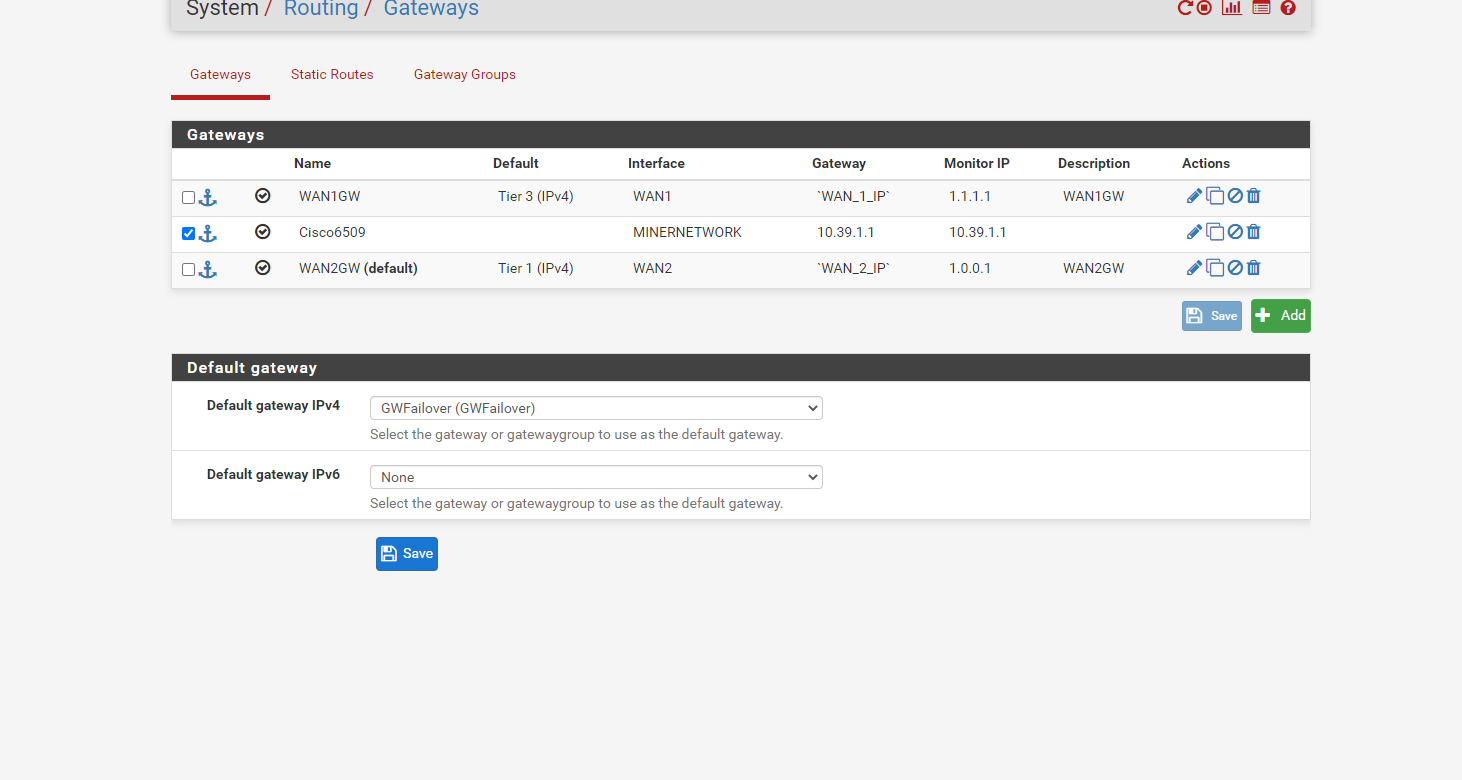
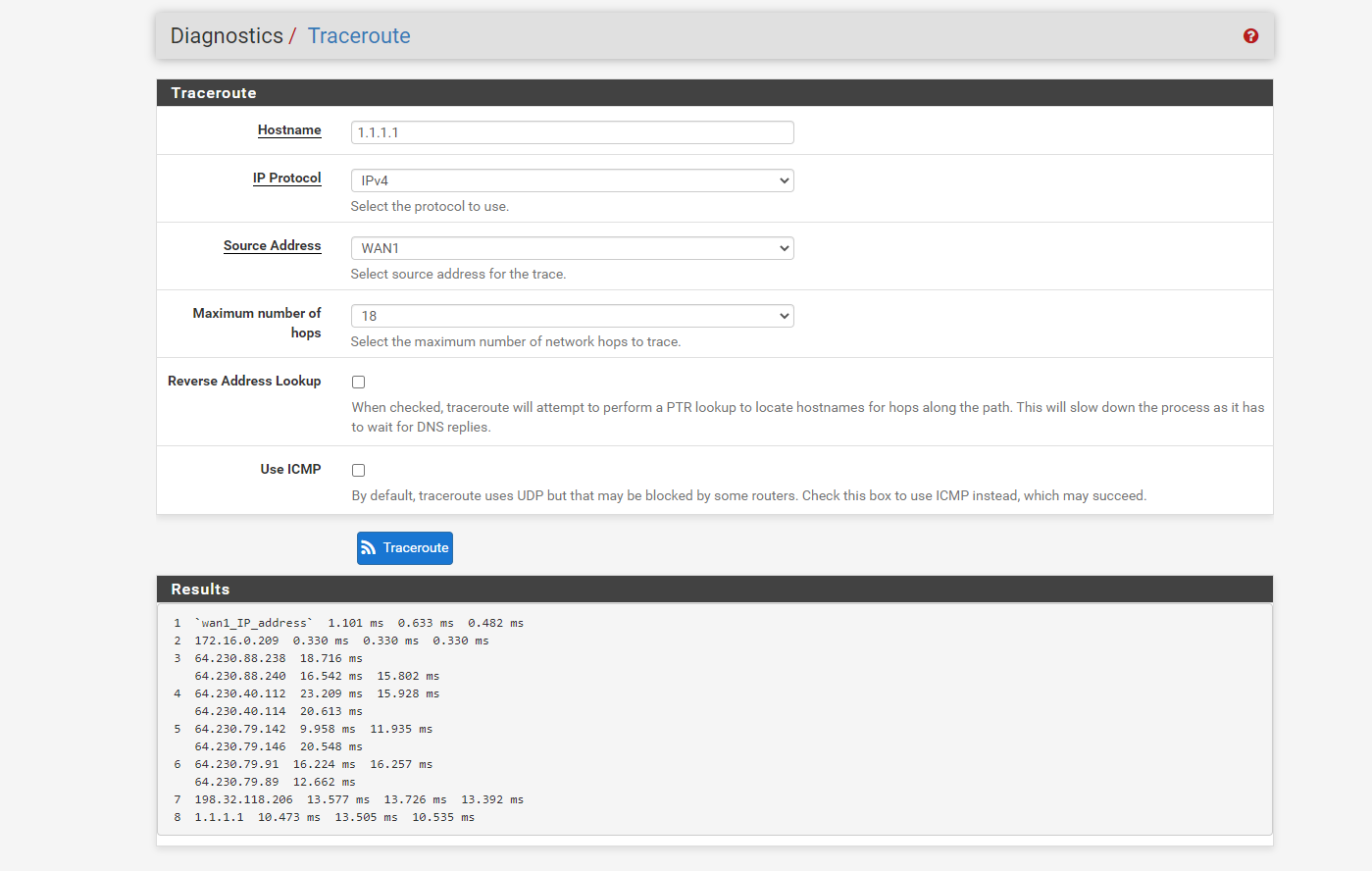
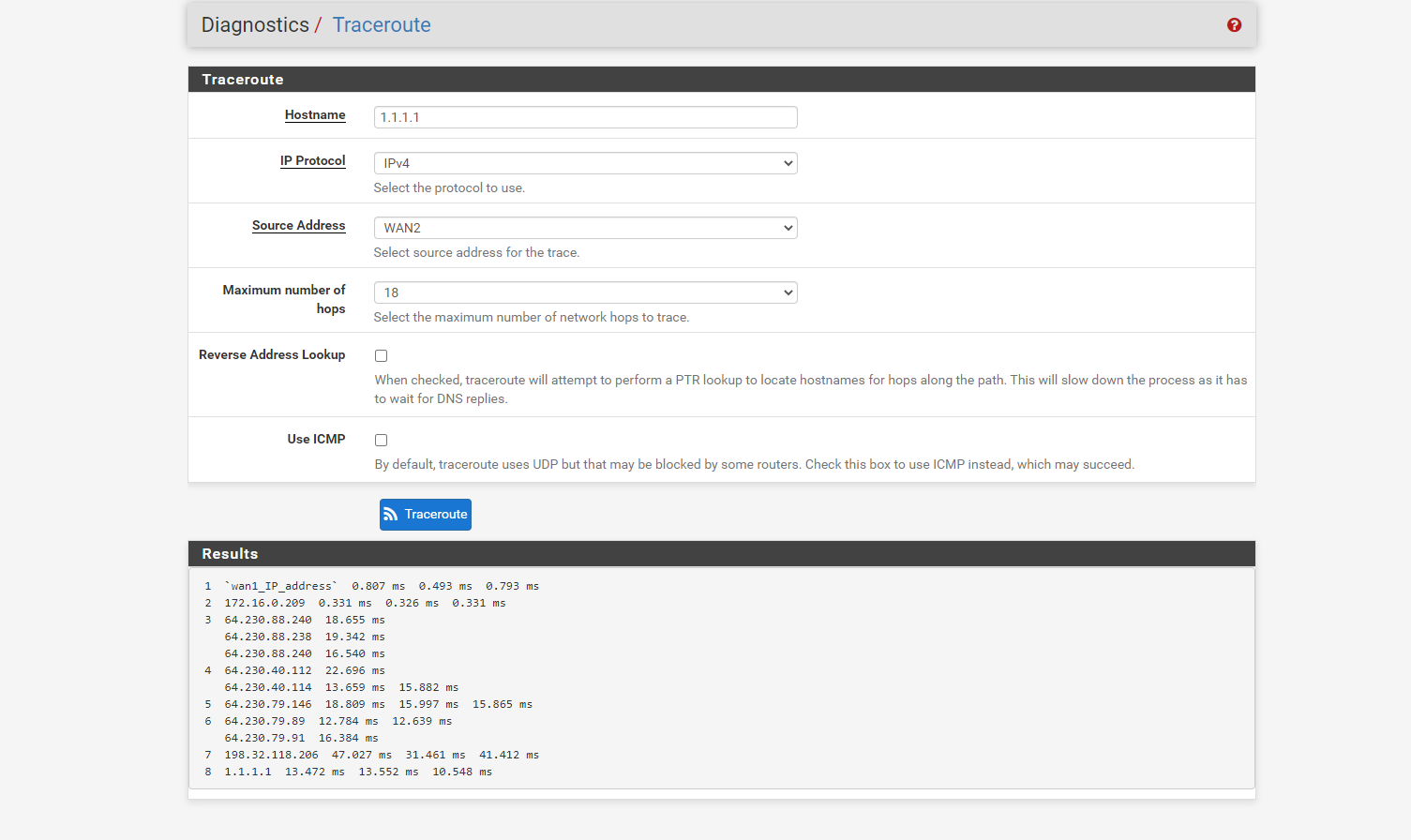
-
The source of the traceroute should be LAN, or try from a device connected to the LAN network.
-
@mcury Thanks for the input,
Although, which ever source Address is selected, it's always going through WAN1 -
What is showing in Status > Gateway?
I wouldn't use 1.1.1.1 as a monitor IP, I would use your WAN1 ISP default gateway, or the ISP DNS server.
In the past, Google 8.8.8.8 was dropping ping packets due to the high load, maybe 1.1.1.1 is doing the same.
Maybe 1.1.1.1 is dropping packets and the failover happens, check the logs in Status/System Logs/System/Gateways
-
Hello!
Diagnostics -> Routes...?
John
-
Here is the Status > Gateway page.
I tested from a server on the Lan Network and The Server Network and traceroute goes through the right GW (WAN2).I can't test right now, but when WAN1 goes down, the whole network is affected. Is that a normal behavior event if it's not the default GW?
Thank you
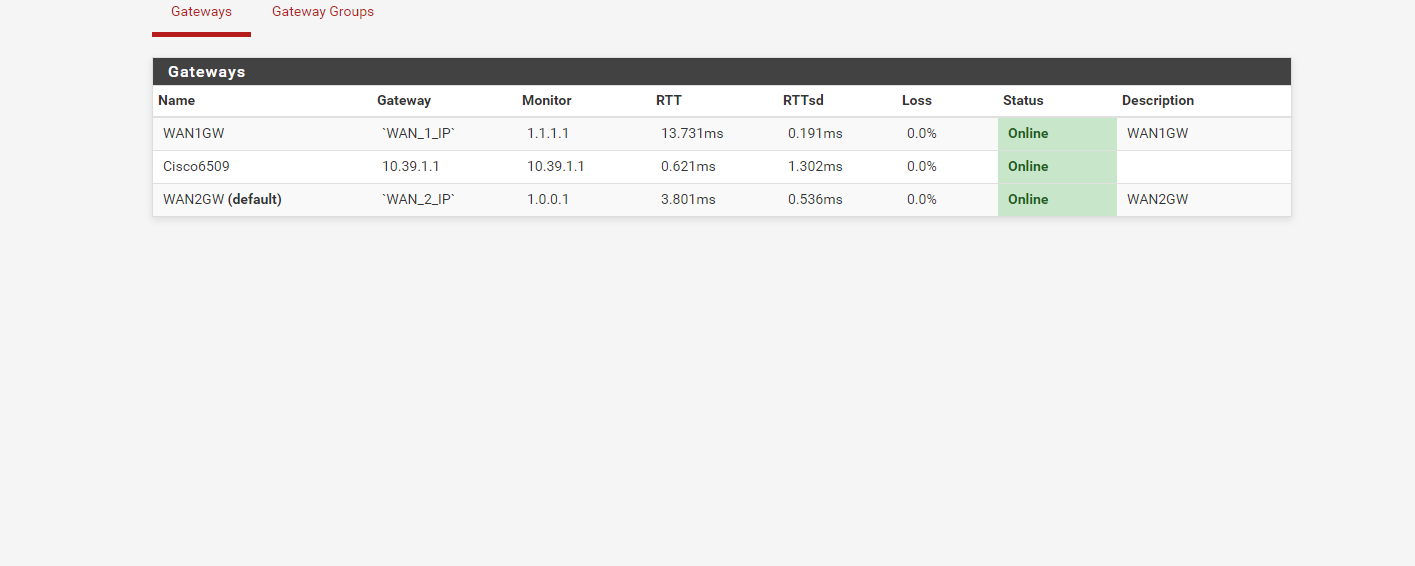
-
@serbus Hi!
The default route at the top is WAN2 GW. -
Hello!
Can you elaborate on, " the whole network is affected".?
Are you doing any policy routing?
Is upgrading to 2.4.5-p1 an option? There may have been changes to multi-wan since your release.
John
-
Your Status > Gateway Page is showing no drops, it should be fine, but still I would change the monitor IP, but that is up to you.
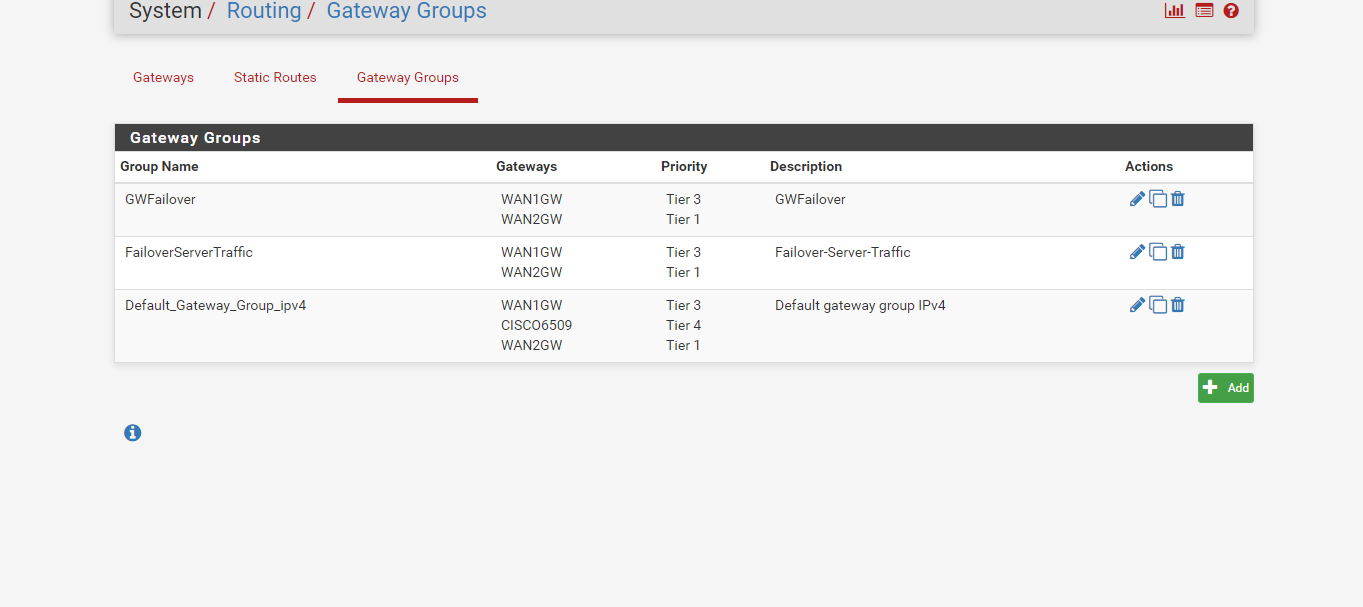
Check the logs as mentioned earlier to confirm if drops happened during the period you noticed the failover.The gateway group of the LAN is set in the LAN firewall internet rule, in advanced options.
In case you set the gateway group GWFailover in the advanced options of the Firewall rule, it will use Tier1 (WAN2GW), and in case WAN2GW goes down, it will use WAN1GW (Tier3).
-
@serbus Sorry that wasn't really clear.
Last time we lost GW1, VPN user got disconnected. We checked the logs and OpenVPN server got restarted.
The servers also lost connection.I got a maintenance scheduled for early next week, I'll test unplugging WAN1 to see what happens and view the log in real time.
Thanks
-
Hello!
I am on 2.4.5-p1 with multi-wan (failover/loadbalance). WAN0 -tier1, WAN1 - tier2.
When WAN1 goes down/up, I dont see any of the tunnels on WAN0 being affected.
John