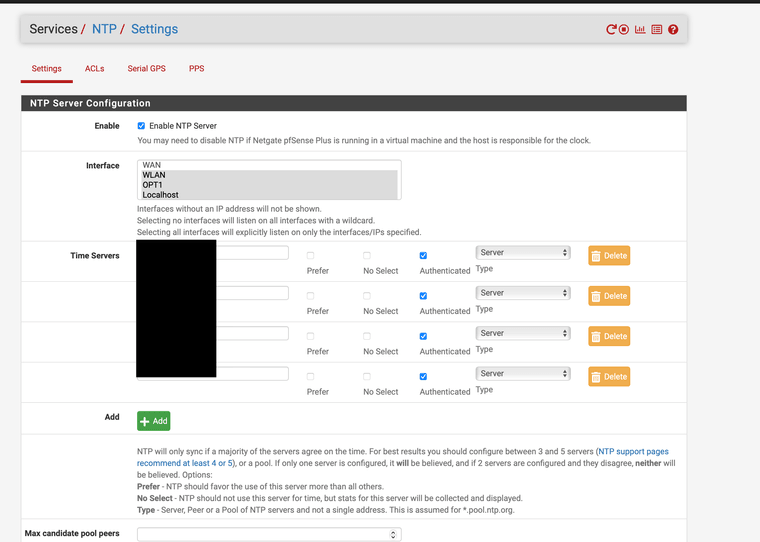
Authenicated NTP
-
Did this github ever get merged?
847e417b5612f28bc1e84ca028a980df9c5c57a7
I can pull it in patches now
-
 J JonathanLee referenced this topic on
J JonathanLee referenced this topic on
-
@JonathanLee It has not, and I have not seen any further feedback.
I agree these aren't all the changes that it would be nice if were implemented, but it at least takes it from an almost useless feature (because you are never going to get the key ID 1 from a shared system) to something with some problems.
I'm willing to add some of the missing pieces (e.g., per server authentication) but I'm not inclined to do so if it isn't going to be reviewed. As I mentioned in the Redmine issue, if someone can tell me what the most important changes needed for this to be accepted are, I'd take care of them.
@marcosm Sure, I think NTS would be great, but for now, at least as far as I can tell, none of the major time providers support NTS, and I doubt many GPS based time systems will support it for some time (at least the lower-end systems) -
@MatthewA1 Netgate I have been told has a very small staff and strict budget, they will get to it eventually. Don't be discouraged.
-
I made an update where authentication can be enabled or disabled per server/peer (and it actually validates that you didn't enable authentication for a pool).
The latest version can be applied using the package patch using this URL if anyone wants to test:
https://github.com/pfsense/pfsense/pull/4658.diffSide note: I would like to further improve this by allowing multiple keys to be configured and then have a dropdown for each server to select the key (or no authentication), but I don't see any way to do that without making some significant changes to the config.xml format. I don't think I should go down that road without input from Netgate first though.
I think this needs to be done anyways to resolve some other issues such as:- Like @marcosm pointed out on Redmine, there are two places to configure NTP servers, but they edit the same config option while implying they are separate settings
- Disabling the NTP server from Services > NTP results in ignoring time servers set in System > General Setup, but there is no indication of that on the General Setup page
I'll add a couple more notes on this to the Redmine. I'm not sure if this should be a separate ticket or not either, but I think I don't want them in the same branch/PR for now.
-
-
@MatthewA1 Open a redline and put the patch and the GitHub into it, Netgate will see it in 2 seconds after that, I bet it will be added to the development version if you do that route.
-
-
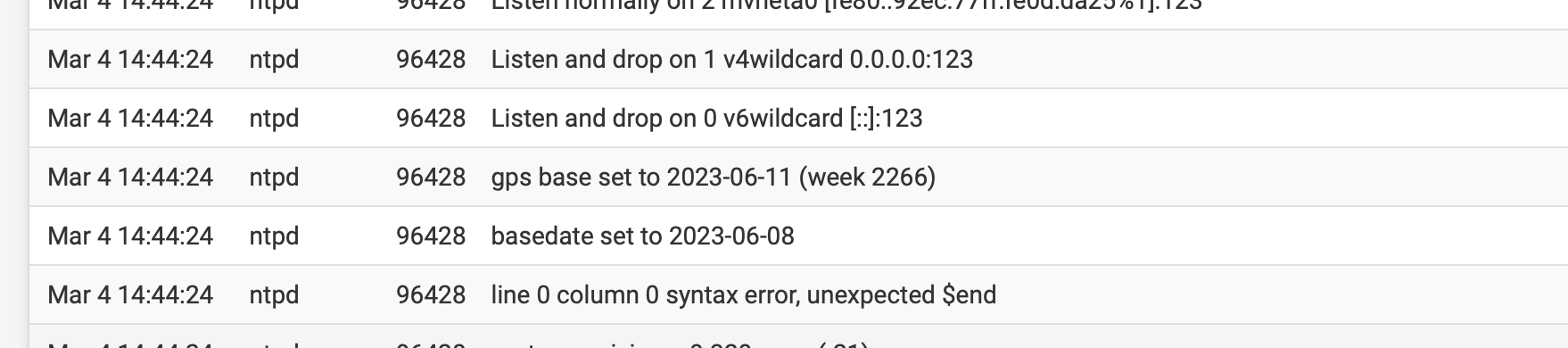
@JonathanLee Hmm, I'm not sure what is causing that. However, I checked an unmodified pfSense CE 2.7.2 and pfSense Plus 23.09.1 and this shows up in the logs on both of those appliances after a reboot. Also interesting is that it does not occur on a service restart, only on a system reboot.
-
@MatthewA1 when I removed the patch it goes away, I think it has to do with the status page adjustments.
-
 J JonathanLee referenced this topic on
J JonathanLee referenced this topic on
-
Anybody else using authenticated NTP?
We got our config info from that very nice gentleman Judah at NIST over a year ago, and I just now--as in, an hour ago- finally found the time to get ours working right with pfSense. :) I try to be a security nut, and, from what I understand, NIST's authenticated NTP service feels like the most secure inexpensive option for time sync.
As far as how I got it configured, I really appreciate your work above, @LamaZ, as it helped me quickly find where I needed to make changes in pfSense to get it all working. Ultimately, I just ended up commenting out the code in that system_ntp_configure() function you mentioned that overwrites the NTPD .keys and .conf files, and just populated the files myself, by hand. That seemed like a pretty quick and easy way to get it working.
It definitely would be nice if the pfSense UI supported this, but in the meantime, I guess we can just keep hacking the system_ntp_configure() function whenever it's modified, to keep it from overwriting the config files.
 I definitely encourage everyone who is using pfSense as their corporate firewall to get their firewall(s) set up as secure/authenticated NTP servers, though. It's just one more way to reduce would-be hackers' attack vectors, right?
I definitely encourage everyone who is using pfSense as their corporate firewall to get their firewall(s) set up as secure/authenticated NTP servers, though. It's just one more way to reduce would-be hackers' attack vectors, right? -
@LamaZ Folks, just upgraded to pfSense+ 24.03-RELEASE and this still works.
I fumbled and didn't quite get @MatthewA1's sweet patch method working yet. That would of carried over across the upgrade right?
-
@MaximillianC Warms my heart! Make me glad knowing that my efforts helped someone out there.
I just updated and revisited this page to remind myself how to get this working again. :) I had high hopes the changes would have made it in by now.
-
I am missing my photos here too :( Can you help with a couple of these posts the photos are vanishing ..
-
Probably not those from the begining of March unfortunately. For some period attachments were being uploaded to an invalid storage location and when that was corrected those were effectively lost. But all other attachments (since the move to NodeBB) were restored.
-
-
If anyone wants to test (@JonathanLee ?), I've rebased the work onto the current state of master and updated the config accesses to use the new required functions. Below is the current patch, and the latest version is always available from the GitHub PR diff.
ntp-authentication-feature_20240620.patch
pfsense/pfsense#4658 diff
I don't have my development environment up and running at the moment (getting a new NTP key) so I haven't tested this yet. I think it will work, but the patch may not apply to the current 2.7.0 release. There's also no dev snapshots available at the moment it seems, so if it doesn't apply to 2.7.0 release, and advice on how to test in the absence of dev snapshots would be appreciated. -
@MatthewA1 I have to test when I get home it is merged I just saw the GitHub. I need to creat a new boot environment for it and load 24.08 on it. I am still utilizing 23.05.01 because of the crypto chip and offboarding acceleration with vpn on the 2100, the new 2100 does not ship with a acceleration chip, so they do not include software for it any longer, I need it purchased one with it so I am stuck on that version or what I call the everything bagel 🥯 version. I can get a BE up and running later this week.
-
All 2100s ship with the SafeXcel crypto hardware. It's in the SoC. It's supported in all versions, including the upcoming 24.08:
[24.08-DEVELOPMENT][admin@2100-2.stevew.lan]/root: dmesg | grep crypto armv8crypto0: <AES-CBC,AES-XTS,AES-GCM> safexcel0: <SafeXcel EIP-97 crypto accelerator> mem 0x90000-0xaffff irq 18,19,20,21,22,23 on simplebus1What is no longer used is the crypto ID chip. That doesn't (and never did) accelerate anything.
-
@stephenw10 my OpenVPN can not do off boarding in the new versions. I think it’s OpenVPN related. I know it is off topic, plus I love that proxy you know that. I have way to much time and effort put in that proxy, I am convinced that that is the future solution for invasive containers, because it gives cybersecurity the ability to start caching them and after start fingerprinting the containers. You can run all of Kali on a docker container right now, that is scary. Future cybersecurity solutions I am willing to bet involve updating older accelerator technology and proxys and reworking code to detect and block before it hits the secure side of lans. That’s why I can’t give up on proxy software. I just need a 30 floor building of software developers, and it should work right, plus a database of container fingerprints, and a couple good lawyers on container, hr staff, some good managers, a good break room, 401k plan, some other stuff too, bank loans etc.
-
You cannot select an off-loading engine in OpenVPN because OpenSSL does not support it. We removed the setting there because it was no longer doing anything (and had not been for some time)
However kernel mode crypto should use SafeXcel so OpenVPN with DCO enabled should.
We should move this to a different thread though. This is nothing to do with NTP Auth.