segment wifi traffic (guest, IoT, trusted)
-
You could reuse your old "dumb" switches , if you have the need for many ports of the same type (vlan)
Good to know - I'll probably go with 3 of the 5-port flex mini's and if I need to add more devices (same vlan), I'll attach one of my 8-port dumb switches.
But, found this in the unifi datasheet:
USW-Flex-Mini uses port-based VLANs only and does
not support SSH, STP (forwarding only), 802.1X, DNS
suffix, or experience in the controller.SSH is not an issue for me, but not sure about the other limitations.
-
Re : Ubi switches ...
While cheap .. I'd drop them , looks like an el-cheapo model.D-Link just released a new 1100-08V2 (V2 is new)
https://us.dlink.com/en/products/dgs-1100-08v2-8-port-gigabit-smart-managed-switchDS
https://us.dlink.com/-/media/obu-content/us/datasheets/dgs/dgs-1100-v2-series_datasheet_v_100_dus.pdfGuide
https://support.dlink.com/resource/PRODUCTS/DGS-1100-08V2/REVA/DGS-1100-08V2_REVA_MANUAL_v1.00_WW.pdfBuy
https://www.amazon.com/dp/B08P2C2GXFI have used the old 1100-08 and 1100-08P (Non V2) , and that is my goto switch when needing something small & effective.
Seems like the PoE V2 has a bit of issues , but $35 for an 8-port & $30 for a 5-port, not that bad.
But they mention some GUI issues
But I'd get one , and try it out , if it were me.Datasheet actually shows a lot of value for the $$
My choice would be D-Link or Netgear
/Bingo
-
@bingo600
thanks for the recommendations - I will check them out. One appeal of the ubiquity, was that if I went with the wireless AP and switches, it would be easier to manage them all under their unifi controller software. I was hoping the reduced features of the flex mini would not be an issue for my use case. -
If you read what you wrote above about the UBI switches
USW-Flex-Mini uses port-based VLANs only and does
not support SSH, STP (forwarding only), 802.1X, DNS
suffix, or experience in the controller.I read that as it's too cheap to play w. the controller.
So no advantage in going for those cheapo's -
So while the $29 mini look interesting and I could seem them in specific use case..
But for my switch I was going to put on my network as just a general purpose switch. No - wouldn't look at those even with the nice price point.
Switching is quite often over looked at the importance in your network - just connect this one there, that one there.. you find daisy chained, etc. etc..
A proper laid out and configured L2 is a huge portion of overall network health and performance for sure.. Always overlooked.. Don't just buy xyz because its cheap.. think about what your wanting to do and what you may "want" to do in the future..
For example - being able to filter multicast doesn't always come to mind.. Tell you what with the broadcast monsters you put on your network.. Its a major thing I do and filter at my L2.. Just noise machines!! Filter them at the port vs that noise going everywhere..
-
My choice would be D-Link or Netgear
ok, given the small price difference (8-port vs. 5), I'll go with 8-port, either:
- Ubiquiti UniFi Switch 8 60W, $99
- Netgear ProSafe Plus GS108E, $48
- Dlink DGS-1100-08V2, $35
It doesn't make sense to go with ubiquity (if buy 3 switches) just for their unifi controller software. So appears Dlink is the way to go. Makes we rethink the ubiquity wireless AP now since no advantage of using their unifi controller software for just one device.
-
@farmerjohn said in segment wifi traffic (guest, IoT, trusted):
Netgear ProSafe Plus
I bought a used 16 ports one on eBay $30 freed shipping last year ... FYI. Still using it also, no problem; however, on my LAN, I have a Mikrotik RB450x2 5ports ($149 shipped) so I can separate guest, cameras, etc, plus the managed switch attached to it... many ways to feed a Cat ... I don't skin or kill Cat.
-
@farmerjohn said in segment wifi traffic (guest, IoT, trusted):
@bingo600
Makes we rethink the ubiquity wireless AP now since no advantage of using their unifi controller software for just one device.I'd still consider AP-AC-Pro , in fact i would still get it (them).
I would just see the unifi controller sw as an "AP Config tool" , and you don't even have to have it running, once the AP is set up.My controller at work , is permanently running in a Debian10 VM (because i have a VMware environment already).
But if i has just one AP and no "Always on server" , i'd prob just install & configure the AP , and stop the controller until next configure/update.
At home i'm using Cisco AP's (autonomous) , but that's because i got some for free. Else my budget (or power use / & Noise-level) isn't for "Enterprise" ....
If/when the Cisco's goto "Silicon heaven" i will be getting Unifi AP's.I might have gone a bit overboard w. SSID's on the Cisco's , i have 6 active and are using 4.
I have no idea what else there is besides Unifi , in the upper "home" price range.
/Bingo
Edit:
@JP .... Yes i know , many SSID's , management frames etc .yada..yada
But it's nice to have the "Phones" & "Mmedia" boxes in their own Vlans.
I can give the wife "Read-Only" to the pictures on the server , based on the phone ip range. And make sure the ATV's & other boxes arent used as jumphosts for poking around (if/when DHS wants that).And i like to be able to have a VPN "SSID" , that points to whatever my Deb10 ExpVPN GW is pointing at.
I can be "Cloaked" at will ..... -
have no idea what else there is besides Unifi , in the upper "home" price range.
ok, I'll stay with the unifi AP
My controller at work , is permanently running in a Debian10 VM
i have a raspberry pi 4b running ubuntu server that is always on, so I'll probably install the unifi controller on that, but a bit concerned about the write frequency on the 32GB sdhc. As you say, I can just stop the 'unifi service' and start when needed if write activity is too much.
-
@farmerjohn
I have Raspi's running on year 4..5 , using Sandisk Extreme & Sandisk Ultra.
Life is to short for cheap SD-CardsMy "backup" DNS/DHCP server is a Raspi3 - running on 4'th year , on a 32GB Sandisk Extreme.
/Bingo
-
My controller is running on my main Linux desktop system. This computer is up 24/7.
-
My controller is running on my main Linux desktop system. This computer is up 24/7.
I'm on Arch and would have to install via AUR, so prefer the debian pkg on a debian based distro.
-
D-Link just released a new 1100-08V2
I just purchased two of these to connect to a netgear smart switch (5 years running), but unable to get the d-link switches to be recognized by pfsense (I enabled DHCP for both d-link switches via default 10.90.90.90 web UI). I suspect it is a configuration / trunk port issue in connecting the d-links to the netgear.
On netgear, I set Ports 1,7,8 as 'T' (1 is pfsense, 7.8 are dlink connection ports). I also set the switchport connections on the d-links to 'T'. Mgmt. vlan is enabled and set to '1' for all devices. I'm sure i'm missing something simple but flying blind (I've never connected two switches together before) and d-link manual is only for one switch-to-router use case.modem | pfsense | netgear_GS108Tv2 | | dlink1 dlink2 ||| ||| -
I have the 1100-08 (Rev1)
Sidenote:
When i installed i saw an issue w. DHCP (for management) seemed like they forgot to "renew" at times. So i just gave them a static ip.When you say unable to be reckognized by pfSense , do you mean the management IF ? - Or don't the ports work ??
Re: Vlan
Vlan (Tagging) has to be enabled along the "Full path" , meaning on all units ít passes.
So if you want pfSense Vlan 1 + 7 + 8 to be "seen" on the D-links , you need to enable those Vlans on (Vlan 1 is probably already enabled , as the native Vlan (untagged)) :
1: pfSense
2: Netgear
3: Dlink/Bingo
-
On switches you typically have to define the Vlans before you can use them
Packages/Frames to any Vlan not defined on the switch , will be dropped on entry.On my 1100-08 I add a vlan like this
Click on Add (VID = Vlan ID)
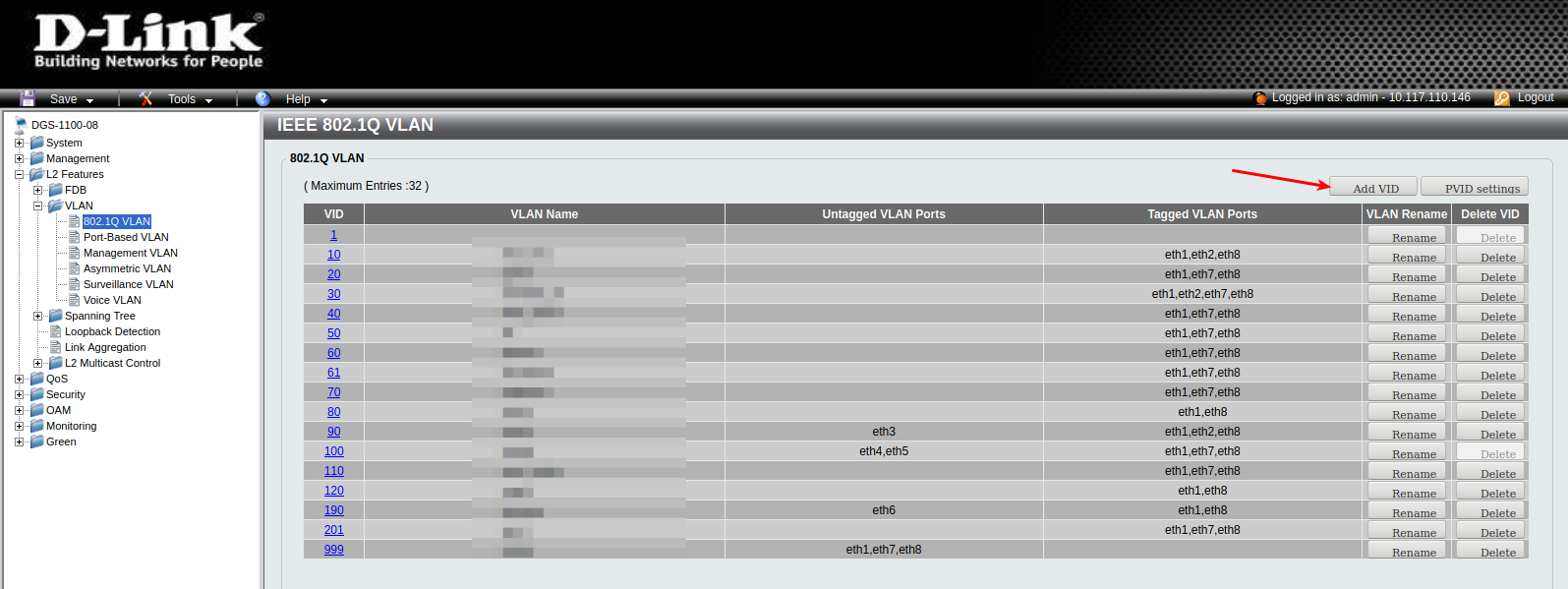
Enter Vlan Number
Enter Vlan Name (For your own sanity, use the same Vlan name on all units)
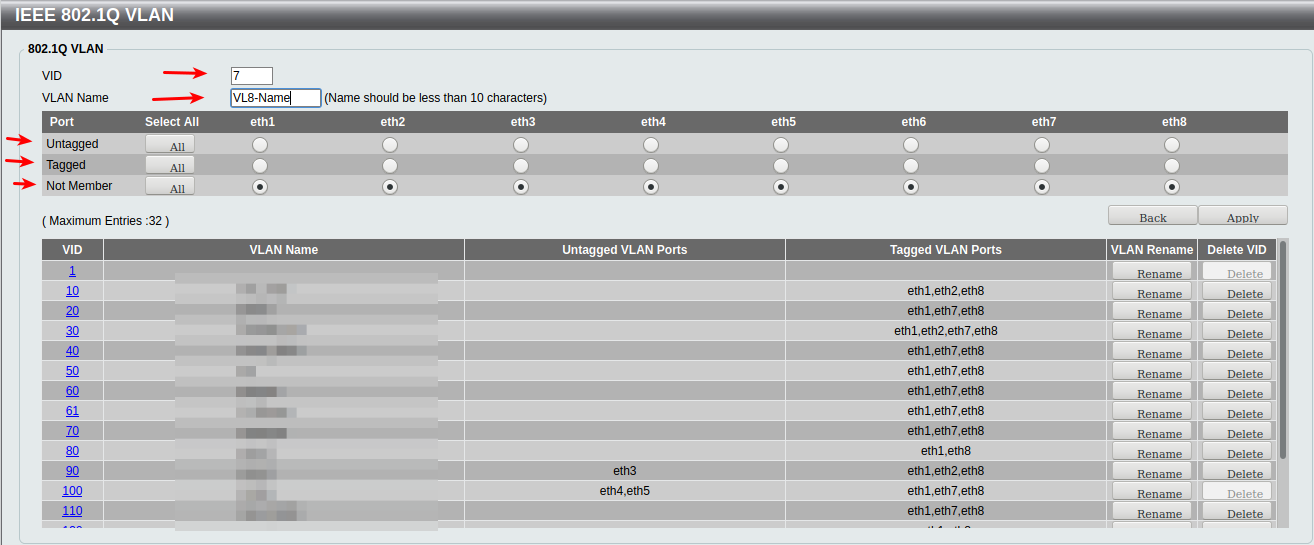
Here we are defining Vlan 7 , with a name of VL8-Name (i goofed)
And in the Port selection boxes below , you see 3 port member types (per port)Untagged :
If this port should behave as a Std. ethernet port (end device) in Vlan 7 , you would tick that.Tagged:
If this port should transport Vlan 7 as tagged frames (typically used if connected to another vlan capable device) - Ie. a switch , you would tick that.Not Member:
If this port has nothing to do with Vlan7 you would tick that.A switchport can ONLY transport (be member of) 1 Untagged Vlan , but can transport many tagged vlans.
Often a switch comes from the factory with a default setting of all ports are "member of Untagged Vlan 1" , that will drive you crazy when you want ie. port 2 , to be a member of untagged Vlan 7 instead. You are NOT allowed to do that !!!!.
Solution:
Go to the Vlan 1 definition , and make Port 2 "Not Member" of Vlan 1.
Now you can make it an Untagged member of Vlan 7./Bingo
-
I have made a dia drawing of what i think you want.
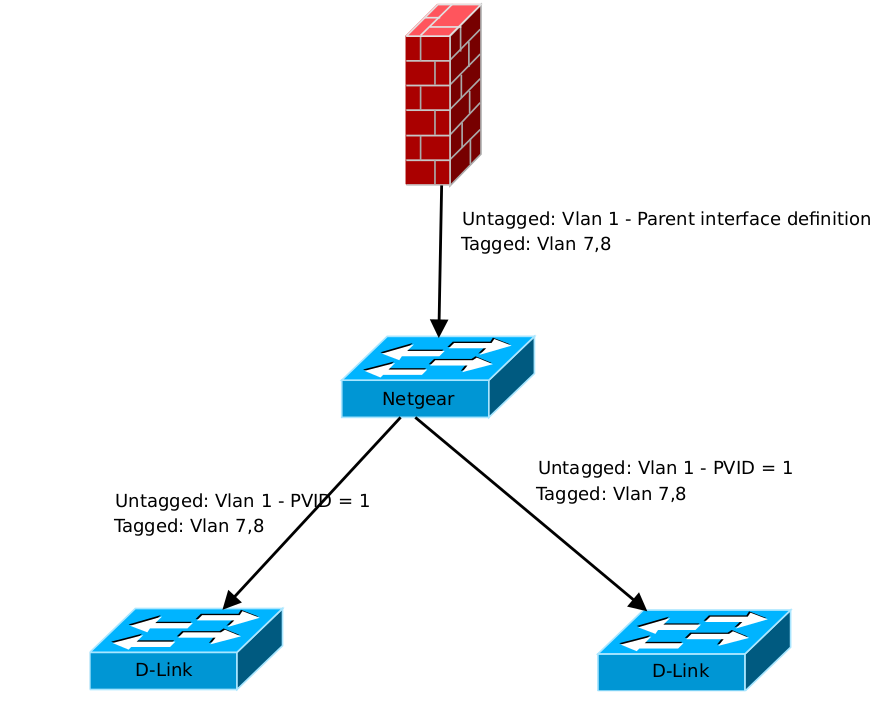
I recommend dia (when you don't have visio) , or are running linux like me.
Get dia here
http://dia-installer.de/And the shapes (symbols) here
http://dia-installer.de/diashapes/index.html.enOn my linux mint (ubuntu) they are in the std pkg repos.
Edit: I have no Netgears - So no idea about how2 configure that one.
Edit2: I made a super short vlan intro here.
https://forum.netgate.com/post/944383 -
@bingo600 said in segment wifi traffic (guest, IoT, trusted):
Everything seems to be working - thanks to your images and explanations. I like the dlink web UI more than the netgear, but the netgear GS108Tv2 was released many years ago.
So i just gave them a static ip.
is working for the moment - hopefully will be persistent.
Get dia here
I'll will try it as soon as my head stops hurting - thanks for making everything clear.
-
Glad you got it working ....
Now when you get the AP AC Pro's - You might have a bit of initial trouble.
Until recently the mgmt net of the AP AC Pro had to be "untagged" , and the Wifi-Vlans could be tagged. That's how i run mine.
But @johnpoz mentioned that with a recent firmware it would be possible to run mgmt as a tagged vlan too.
If/when you get them and have "challenges" give us a "ping" ....
/Bingo
-
@bingo600 said in segment wifi traffic (guest, IoT, trusted):
mentioned that with a recent firmware it would be possible to run mgmt as a tagged vlan too.
I have set up networks, with Adtran gear, where the management interface was on a VLAN. Not having that option is dumb for business installs.
-
@bingo600 said in segment wifi traffic (guest, IoT, trusted):
with a recent firmware it
Wasn't all that recent - quite some time ago that feature was added. I don't recall the min required firmware or controller software. But if your running the current version you can yes run tagged management...
Here you go
https://help.ui.com/hc/en-us/articles/360046773733-UniFi-Using-VLANs-with-UniFi-WirelessYou have to adopt via untagged.. But
"As of Controller software version 5.8, access points and switches can be set to tagged VLANs"While I concur it should be a requirement for equipment to support if expected to be use in a true enterprise.. Running a vlan untagged is not really an issue where unifi stuff would be most used, small business, small offices, homes, etc. It mostly would be a concern where some sort of company security policy required tags..
I have not bothered to change my home setup. While I have multiple tagged vlans, the vlan that my APs are on for managment is untagged for the connection to the APs
5.8.X was released stable over 3 years ago.