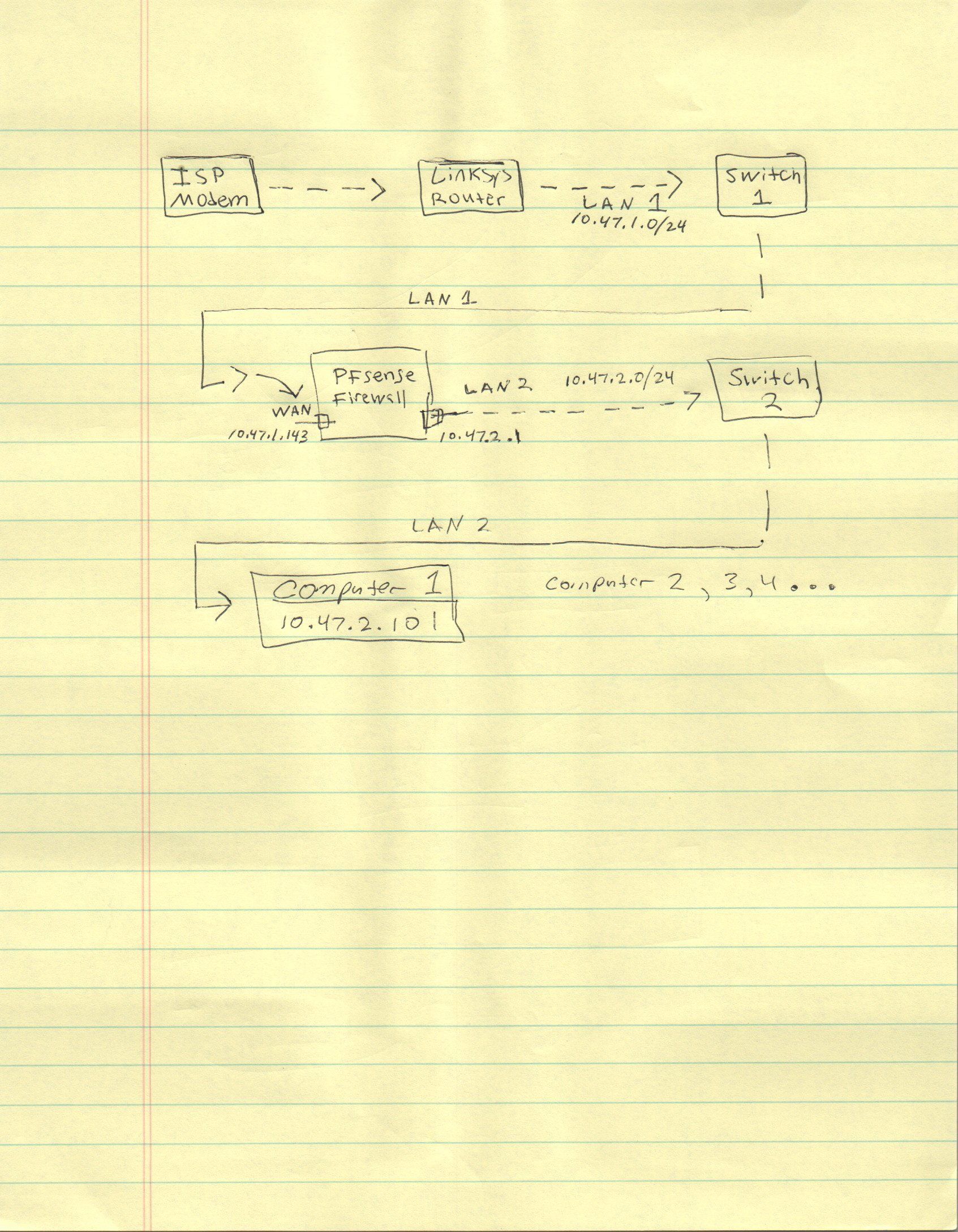
Routing between WAN and LAN
-
@brandon-lizard said in Routing between WAN and LAN:
LAN 1 cannot communicate with LAN 2
For your setup if you want lan1 (pfsense wan) to talk to stuff on lan2 (pfsense lan) you would need to setup port forwards on pfsense. And then access pfsense wan IP from your lan1 network on the port you have forwarded to something behind pfsense.
-
@brandon-lizard said in Routing between WAN and LAN:
My wan interface is connected to LAN 1 and gets and IP of 10.47.1.143
my lan interface is connected to a switch in LAN 2.It's on you to rename the interfaces accordingly.
LAN 1 cannot communicate with LAN 2 > What settings can achieve this?
In the WAN interface settings there is a check to "Block private networks" which is checked by default. Since you need to allow private sources to access on this interface, you have to remove it and add proper firewall rules to allow the access.
-
@viragomann said in Routing between WAN and LAN:
In the WAN interface settings there is a check to "Block private networks"
Yeah good point, but he will still need port forwards. Not firewall rules only.. He is not just routing.. He is just in a double nat setup.
-
@johnpoz said in Routing between WAN and LAN:
but he will still need port forwards
Why? As I got him, he would only separate the two LANs. So he could disable NAT and do only firewalling.
-
I setup a static route on my lan 1 router.
Destination network -> 10.47.2.0
Mask - > 255.255.255.0
Gateway - > 10.47.1.143Result:
Ping - > 10.47.2.1 - >>> Reply from 10.47.2.1 (that's good)
Now, trying to ping a device on that network.
Ping -> 10.47.2.101 - >>> Request timed out
What gives, I don't understand?
-
@brandon-lizard
I assume, pfSense is the default gateway on the destination device.So ensure that the ping is not blocked by its own firewall.
-
No, on the destination device (10.47.2.101), the default gateway is 10.47.2.1
-
@brandon-lizard said in Routing between WAN and LAN:
the default gateway is 10.47.2.1
So this is the LAN IP of pfSense, as you stated above. So it's ok.
-
@viragomann said in Routing between WAN and LAN:
So he could disable NAT and do only firewalling.
No not really - he would have an asymmetrical nightmare.
If he wanted to have pfsense be downstream, then he would need a transit network.. Soho routers not going to allow for such a setup.
But yeah sure, you could very easy setup pfsense as a downstream router/firewall if your equipment supported it. But trying to use a transit network between the upstream and downstream with host on it is going to be asymmetrical.
In his setup what he is calling lan1 is a transit between 2 routers - you can not have hosts on this network without either host routing or natting at the downstream router without having issues between the devices talking to each other because of the asymmetrical traffic flow.
-
@johnpoz
I think, I miss something here, what others see.
In the first post the second router wasn't mentioned. And now I still don't know, what its role...A drawing might be helpful.
-
He called it out here
something I need to change in my linksys router on lan 1
But yeah a drawing is always good! What I took from his statements is he has this.
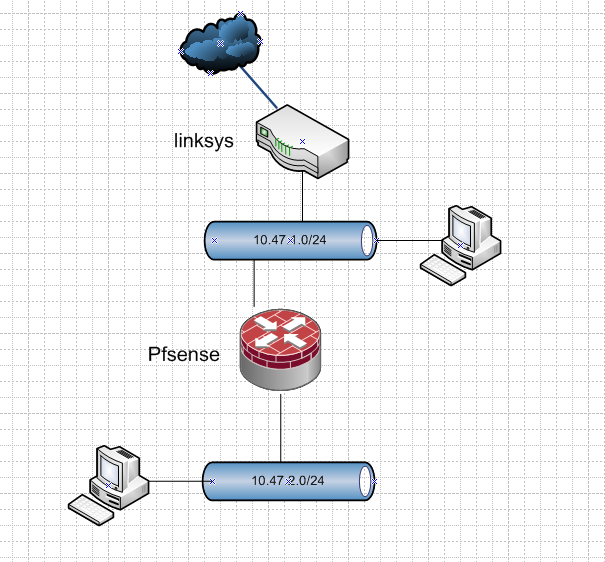
That is going to be asymmetrical unless you host route on every device in what he calls his lan1, or nat at pfsense.
-
@johnpoz
Ahh, yeah, didn't see it this way before, but absolutely agree. -
-
I'm not too familiar with nat and forwarding/routing stuff. I've been reading up on it, but it confuses me.
Are you saying it's not possible to access the computer at 10.47.2.101 from LAN 1?
-
I'm sure @johnpoz will suggest this soon.
What pfSense device do you have ?
Does it have possibility 3 netcards ??Here is a suggestion , that "keeps your" 10.47.1.x devices, no need to change ip addresses on the devices on that network (well except the linksys).
And introduces a "Pure Transit network" (No user devices on it) behind the Linksys.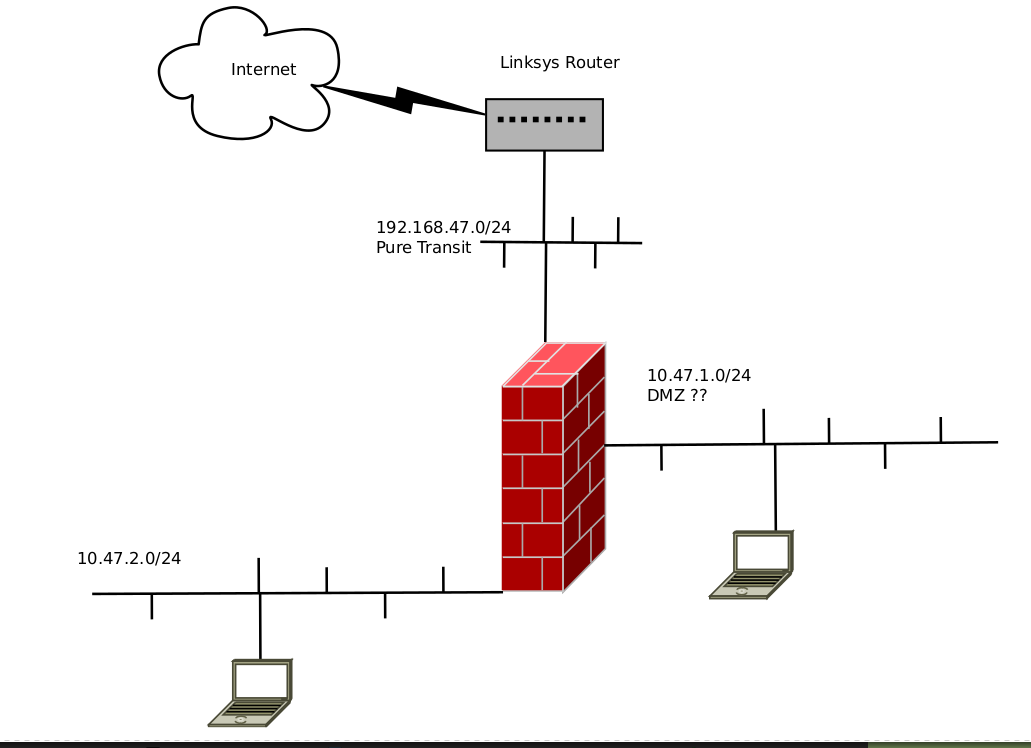
/Bingo
-
@brandon-lizard
@johnpoz already mentioned all options you have here.Best practice would be to set up a transit network between the Linksys and pfSense. So your LAN 1 devices simply send their packets to the Linksys and they get forwarded to pfSense.
But I assume, that router isn't capable of handling multiple subnets.The other options are NAT or adding a static route for LAN 2 to each LAN 1 device you want to enable to communicate with that network.
When doing NAT you have add virtual IPs to pfSense for each device behind you want to access and forwarded the packets to the destination devices.
Both not optimal, I think. Maybe you can exchange the Linksys and pfSense, then you could set up a transit network.
-
I do have 3 netcards available, yes. My pfsense is actually running in proxmox. I also have a nas and pbx. I'd like those to all be on the 10.47.2.0 network.
-
@brandon-lizard said in Routing between WAN and LAN:
My pfsense is actually running in proxmox
Yeah another complexity..
Which you left off your drawing.
I suggest you just do the double nat setup.. Which will work just fine, and would be default out of the box setup for pfsense.
Only thing you have to do is as mentioned turn off the block rfc1918 rule, and setup your port forwards for stuff you want lan1 to access on lan2.
https://docs.netgate.com/pfsense/en/latest/nat/port-forwards.html
-
Then i suggest you move the 10.47.1.x network "behind/into" the pfSense.
Tip: Keep all 10.47.x.x networks behind the pfSense (makes life easier).And make a 192.168.47.0/14 network as Transit.
Now you can still restrict the 10.47.1.x devices via pfSense rules , if 10.47.2.x devices needs to be "protected". And you don't have to bother with portforwarding , as 10.47.1.x is now "behind/inside pfSense".
-
Sorry ... for making another suggestion