[Solved] SG-3100 Switch Configuration - LAN on VLAN ID1?
-
First, let me start by saying that I have configured SG-3100 ports and VLAN, and everything seems to be working as I wanted. Still, after watching Netgate Video and reading this post, I'm starting to think that something is wrong with the way I've configured everything, and I don't have true layer 2 VLAN. Also, I have three questions about this switch on SG-3100.
Here is what I needed. I wanted to configure switch ports to have:
Port 1 and Port 2 for LAN.
Port 3 for access point including LAN, VLAN 43 (IoT) and VLAN 53 (Guest)
Port 4: only VLAN 64 for FreeBSD jailsHere is how I did it. Created three VLAN that I needed and added them to the interface:
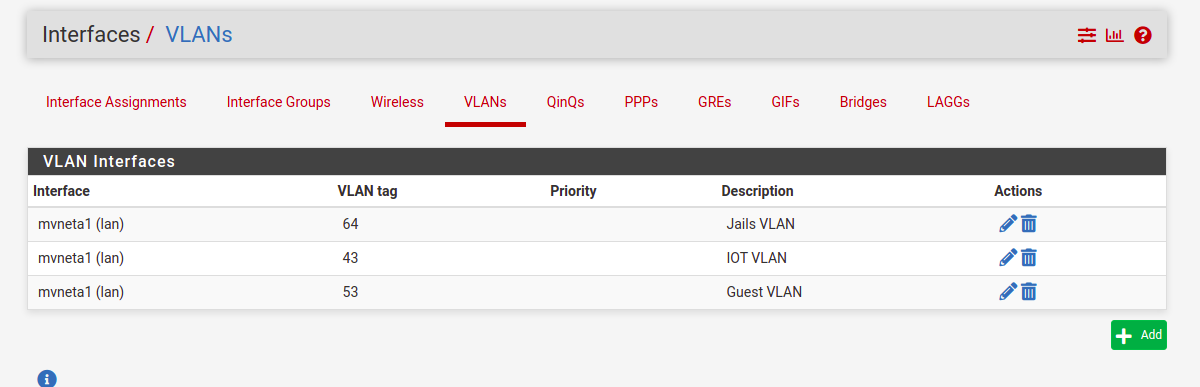
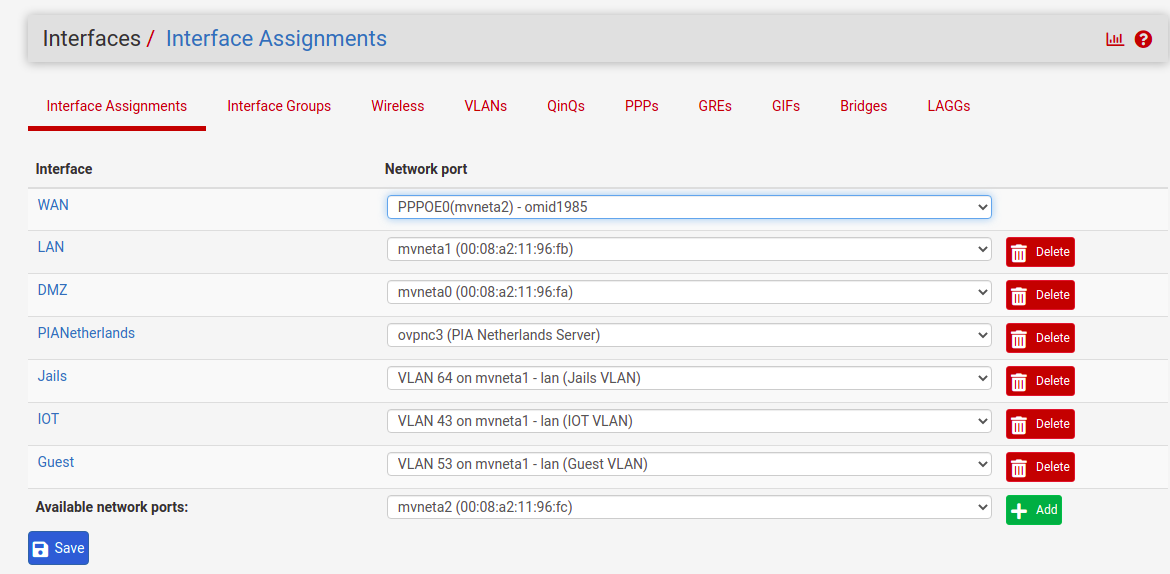
Then for switch configuration, I only removed member 4 and left my LAN in VLAN1 next to my uplink but created three VLAN IDs I wanted and added port members on each:
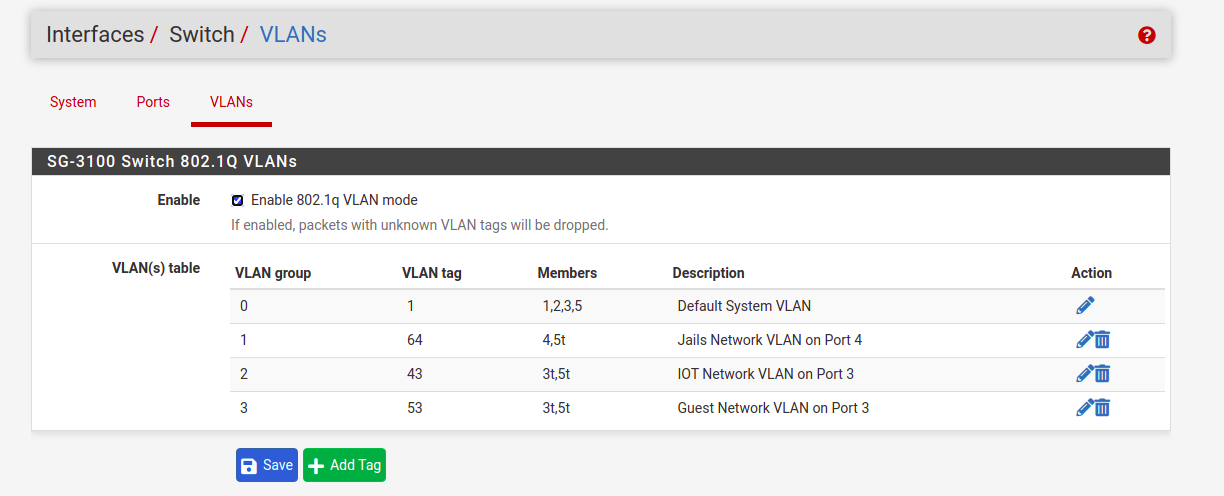
Also, assigned Port VID only on port 4: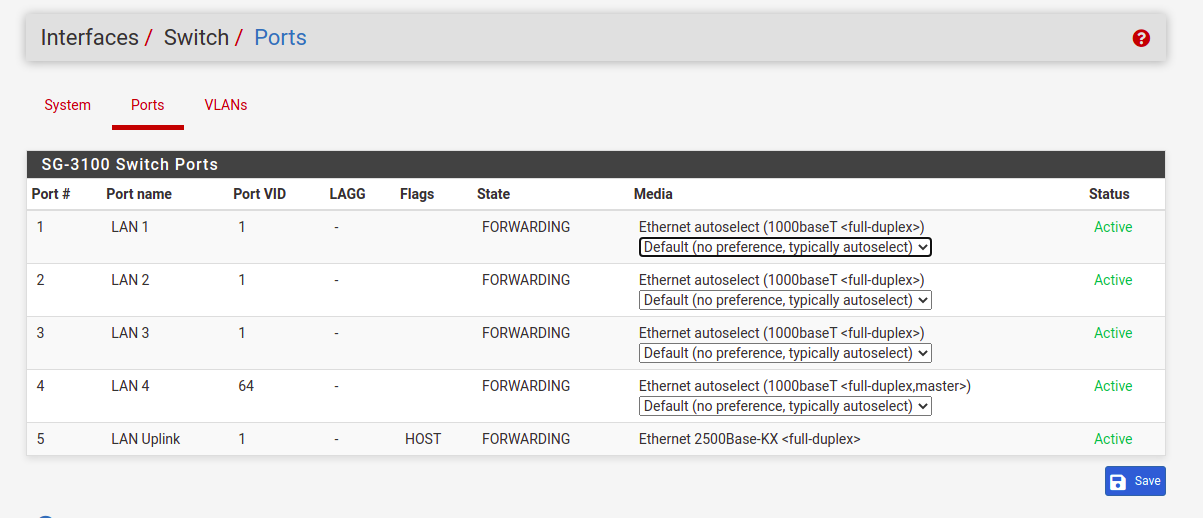
Now, It's working exactly the way I wanted to work:
If I connect clients to port 1 and port 2, they get an IP address from the LAN interface.
If I connect my access point to port 3, It will get an IP address from the LAN interface by default, but I also can specify VLAN ID 43 and 53 on AP to have two more SSID for guests and IoT.
If I connect clients to port 4, they only get an IP address from VLAN 64 for the Jails interface.First question:
Please correct me if I'm wrong:
After seeing those materials I've mentioned above, I see the correct way is to remove everything from VLAN group 0/VLAN ID 1 and only have the uplink 5 as a member. And then:- have a separate VLAN ID, say Vlan ID10 for LAN with members: 1,2,3,5 (all untagged)
Then the rest are similar to what I already have: - have a VLAN ID 64 with these members: 4,5t (4 is untagged)
- have a VLAN ID 43 with these members: 3t,5t (all tagged)
- have a VLAN ID 53 with these members: 3t,5t (all tagged)
To have separate and true layer 2 VLAN, Is this what I need to do?
Second Question:
When I have only one VLAN in a port, say port 4, where I have only VLAN 64, then I can choose my port number in the interface to monitor the states:
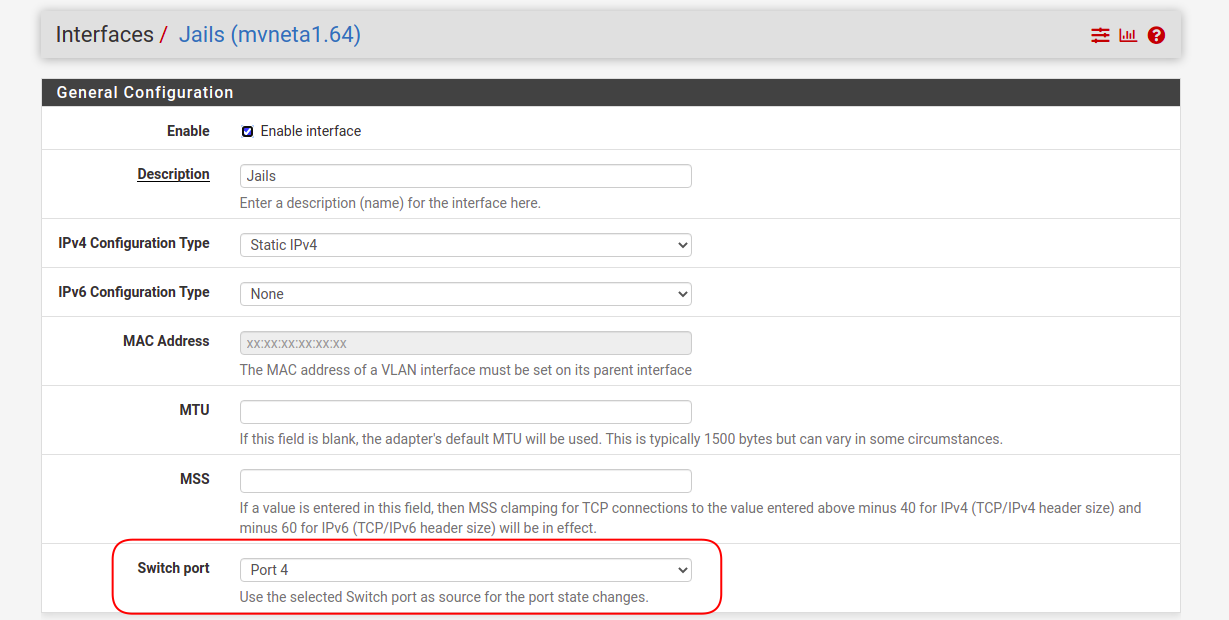
But how about when I have more than one VLAN in port 3? If I select port 3 for IoT, then the guest and LAN interface can't use the same one:
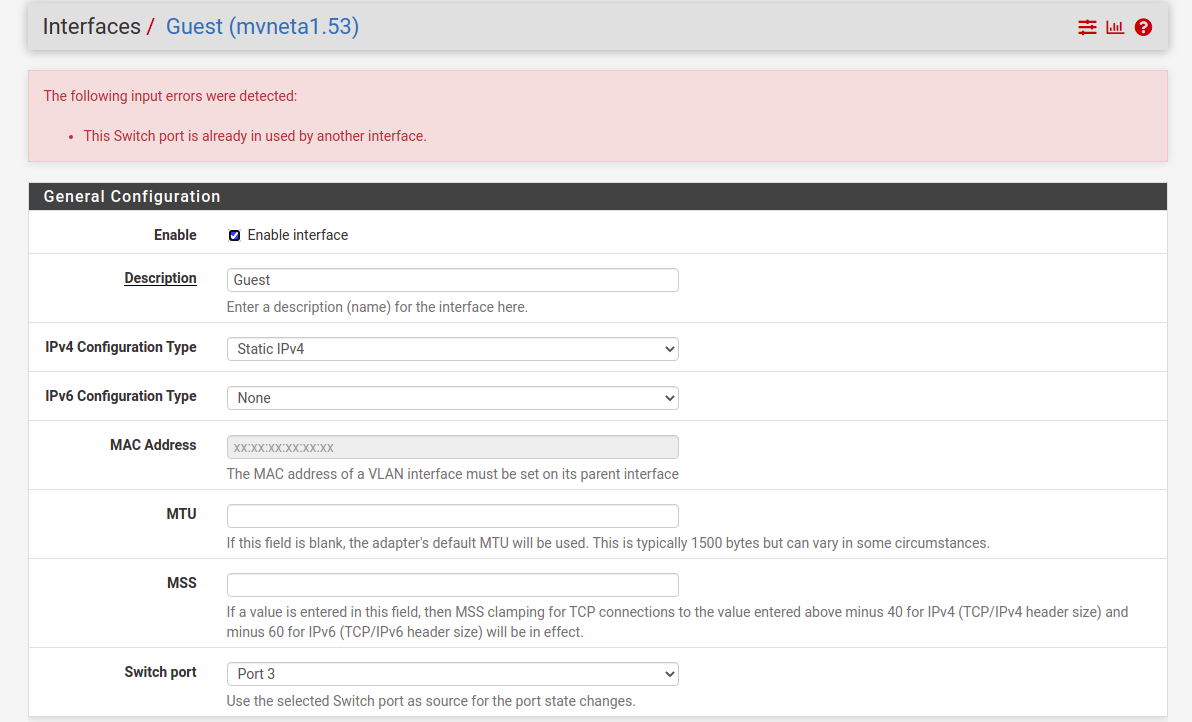
Should I leave all other first three ports on the default configuration below and don't worry about it?:
Third question:
Is there any functionality like Private VLAN in the SG-3100 switch?
Say I want to have all my guest clients be isolated from each other on VLAN 53. Even though I'm rejecting all RFC1918 addresses on VLAN, that doesn't make clients not talk to each other in the same VLAN.Please note that I don't have a separate managed switch, and I'm trying to achieve everything I mentioned above in the SG-3100 switch.
- have a separate VLAN ID, say Vlan ID10 for LAN with members: 1,2,3,5 (all untagged)
-
This post is deleted! -
Okay, regarding my first question, and thinking more about what @Derelict posted on here, I think the configuration I already have is correct, but I just don't understand why I need to remove all members from VLAN ID 1 and have a separate VLAN for LAN like this:
VLAN Group 0: with VLAN ID 1 and only this member: 5 (untagged)
VLAN Group1: with a separate VLAN ID for my LAN, say Vlan ID10 with members: 1,2,3,5t (only 5 tagged and 4 removed).
VLAN Group 2: with a VLAN ID 43 with these members: 3t,5t (both tagged)
VLAN Group 3: with a VLAN ID 53 with these members: 3t,5t (both tagged)
VLAN Group 4: with a VLAN ID 64 with these members: 4,5t (only 5 tagged)
-
Either would work fine there.
The only significant difference there is that you avoid having tagged and untagged traffic on the same link with the second method. That is generally recommended but since that link is only internal in the 3100 you're unlikely to hit an issue with it.If you have a number of switches with trunks between them to distribute VLANs over a large network it's a bigger issue. If you have tagged and untagged traffic on those links it's far easier to accidentally untag a VLAN where it will then be put onto the untagged subnet. If you only have tagged traffic there anything accidentally untagged would just be dropped.
Steve
-
Thank you @stephenw10 for a detailed reply. It does make sense now.
Your input on my 2nd and 3rd question also would be highly appreciated.
I assume for my 2nd question; it's safe to leave monitoring the states unassigned to any port? And for 3rd question, only a yes or no reply would be enough to put me on the right path. -
You can only choose a switch port on one interface as you found. If you leave unset it will use the actual VLAN status which takes it's state from the parent interface. In this case though that's the in internal port which is always UP.
No, there's no private VLAN type function. That would need to be on a switch where hosts are connected directly.
Steve