Wireless with VLAN not allowing traffic
-
@stephenw10 this is what i have on the DNS Server for VLAN 90 (i created a new one) and on LAN
and this is what i just did on the WAP:
and on the switch:
This way, the device can connect to VLAN 90 and it gets the correct ip address as i can see it on the DHCP Leases with the correct IP:
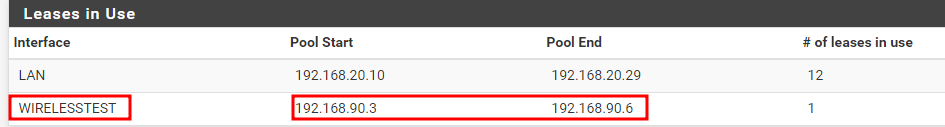
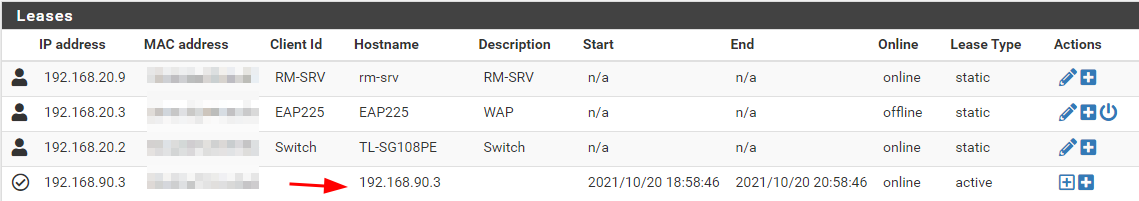
now, i cant get out to the internet on that VLAN... hehehe
-
@dridhas And what firewall rules did you put on this interface? is Unbound listening on that interface? When you create a new interface/vlan unlike lan, there will be no rules. So no until you create rule(s) to allow stuff nobody on that network is going anywhere.
Are you using automatic outbound nat, etc. Seen many a user following some "guide" on the internet for some vpn service switch their outbound rules to manual.. Which then no adding a new network/vlan is not going to work until outbound nat has been created for this new network, etc.
-
@johnpoz this is what im seeing on the firewall logs:
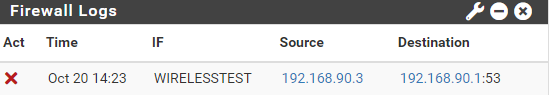
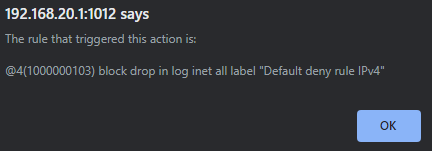
this is the Firewall rule for that particular VLAN:
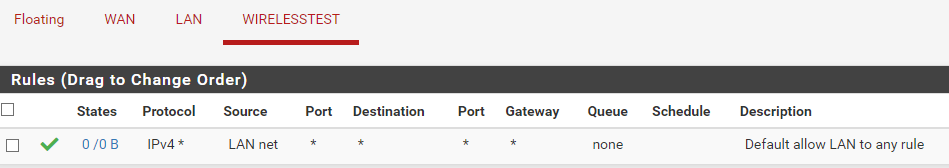
im trying to find that rule somewhere.
-
@dridhas and how would Lan Net be source of your wirelesstest net?? The source would be wirelesstest net
The default deny is on every interface (hidden) - if traffic is not allowed by a rule, then it would always be denied by the default rule.
192.168.90 is not Lan Net, so that rule would not match, and traffic would be blocked by the default deny.
Looks like you copied the default rule over - but did not change the source to the appropriate network for this interface.
-
@johnpoz yes, you are correct, i copied the rule over to the new VLAN.
after the change the traffic is flowing, but then again some sites are unreachable like duckduckgo among others.
-
@dridhas said in Wireless with VLAN not allowing traffic:
unreachable like duckduckgo among others.
Well does it resolve? Use your fav dns tool from the client.. Where its not loading.
$ nslookup duckduckgo.com Server: pi.hole Address: 192.168.3.10 Non-authoritative answer: Name: duckduckgo.com Address: 40.89.244.232Maybe they are blocking you? Sniff on your wan while you try and go there, do you see the syn go out, do you see a syn,ack come back..
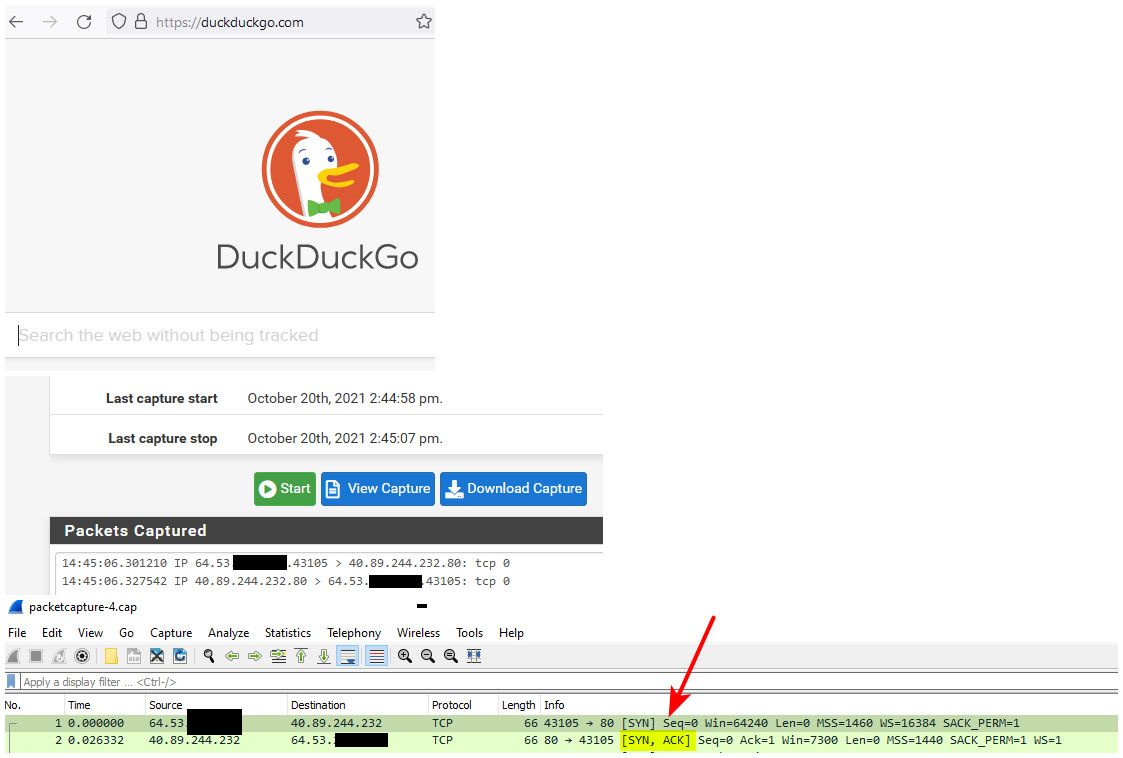
Maybe your browser is using doh for dns? There are many reasons why you might have an issue loading up websites - tags on a vlan or not tag is not one of them.
edit:
what specific sort of error are you getting in your browserCan see they send a 301 redirection, and then the browser connects via https (443)..
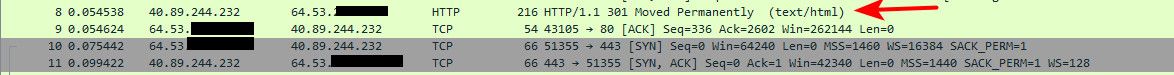
-
@johnpoz there is where i have some questions...
WAN outbound is the same for LAN and VLAN.
LAN works fine, but while on VLAN, several websites are unreachable. -
@dridhas first thing is do they resolve? Never getting anywhere if they do not resolve..
You need to troubleshoot the actual issue - not get hung up on this network is tagged this network is not - since that has NOTHING to do with the actual problem.
Now its possible this network is having issue, maybe your wifi connection just sucks and have zeroed in a specific websites not working? Why don't you take wifi out of the equation and plug something in on the switch and put it on vlan 90..
-
@johnpoz said in Wireless with VLAN not allowing traffic:
Bad idea to use 2 different dns that can respond differently - 222.222 does filtering, while 1.1.1.1 does not..
I have my main LAN configured to use the pfsense DNS server, but my guest WiFi points to Google's DNS. Separate subnets, no problem. However, they shouldn't be mixed on the same subnet.
-
Pointing different devices to 1 dns, and other device to a different dns is not what I was talking about at all.. That is fine.
The problem is if a client can use more than 1 NS, you have really no control over which one might be asked, be it your actual client, or the forwarder your pointing to (unbound/dnsmas) etc..
If the NS you could ask for something might resolve differently - filtered or not filtered, your going to have a bad day. Because you never know which one might get asked, it could be filtered when you don't want it to be, or or could be allowed when you want it filtered.
-
@johnpoz im starting to believe the switch might be the culprit.
im getting hardwire to port1 where the WAP was and im getting a non-vlan ip.
and if i untag the port, i dont get any ip addresses...

-
@dridhas said in Wireless with VLAN not allowing traffic:
and if i untag the port, i dont get any ip addresses...
If your going to plug a computer into a port, this port would almost always be set to 1 vlan with it being untagged. Just put a port in vlan 90, untagged (cisco world calls this access port).
If you plugged some computer into the port where your WAP was connected where vlan 1 was untagged, and 90 was tagged. It should get an IP from your dhcp on the vlan 1..
For it to use vlan 90 where its tagged, you would have to tell the OS to use tag - which can be done in windows (depending on the driver for that nic)
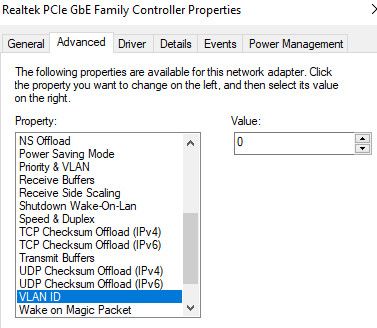
But your mileage might very depending on the nic, and driver, etc. etc..
-
It's not a switch or VLAN issue. Clients are getting a DHCP lease in the correct subnet.
It's probably not a firewall issue either now that you have added a rule with the correct source.
What happens when you try to visit one of these sites? What is the exact error you see?
Steve
-
@stephenw10 he said " i dont get any ip addresses"
So who knows what he has going on or how he is setting it up... If he had 1 untagged and 90 tagged on the wap port, and he plugged just a PC into that port - then he should of gotten an IP on whatever the untagged vlan network is.. 192.168.20 I believe..
-
@johnpoz this is the result of the nslookup on wifi/lan via VLAN90
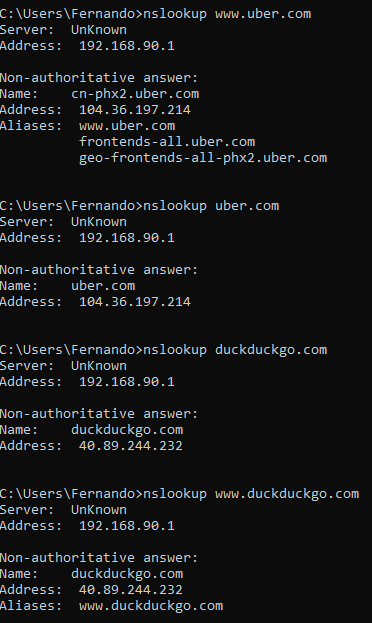
and this is the error message on the browser:
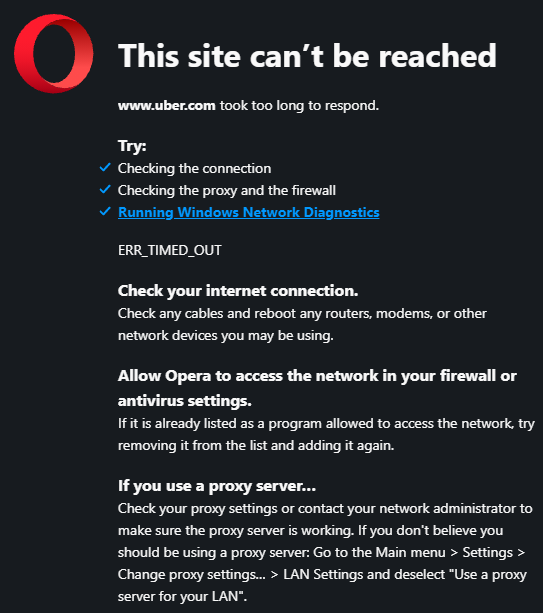
-
@johnpoz said in Wireless with VLAN not allowing traffic:
@stephenw10 he said " i dont get any ip addresses"
But that's only when VLAN 90 is untagged, which is expected.
When it's tagged correctly it gets an IP. And we can see the client is able to connect to the VLAN 90 interface address and resolve those FQDNs.
So that looks like not DNS or the switch or anything vlan related.
Do you see the same thing with different browsers?
Can you traceroute to uber.com? Or ping it?
Steve
-
@dridhas well your clearly resolving them - but how ever your setup is borked if you ask me.. If you were asking unbound running on pfsense directly. It should resolve your pfsense name, not come back unknown.
like so
> duckduckgo.com Server: sg4860.local.lan Address: 192.168.9.253 Non-authoritative answer: Name: duckduckgo.com Address: 40.89.244.232But that error is time out error.. So you looked it up, got an IP - and I show the same IP for duckduck.. So now you need to figure out why your having time out getting an answer. I would first sniff on wan and make sure traffic went out or not.. If you don't see it go out, then sniff on your pfsense lan side interface.. Do you see it get there? If so then pfsense should of sent it out..
-
@stephenw10 ping does not work, im guessing uber has ICMP disabled.
on Edge i see something similar:
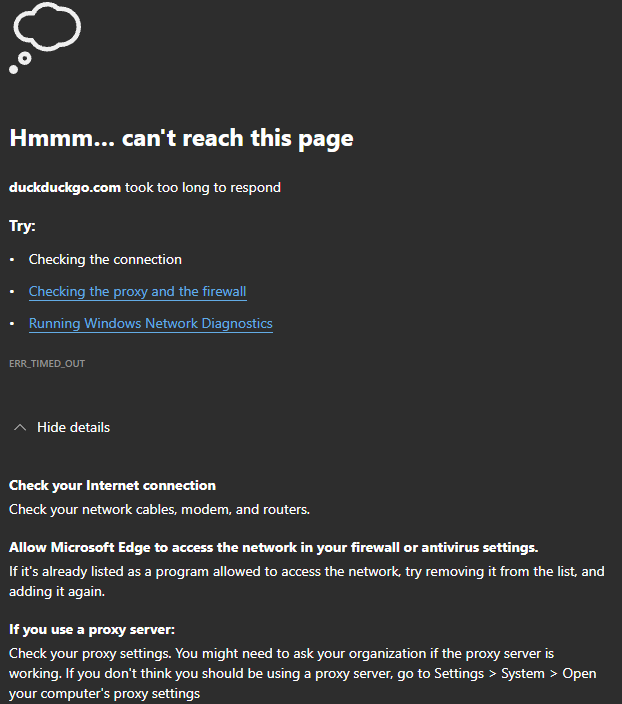
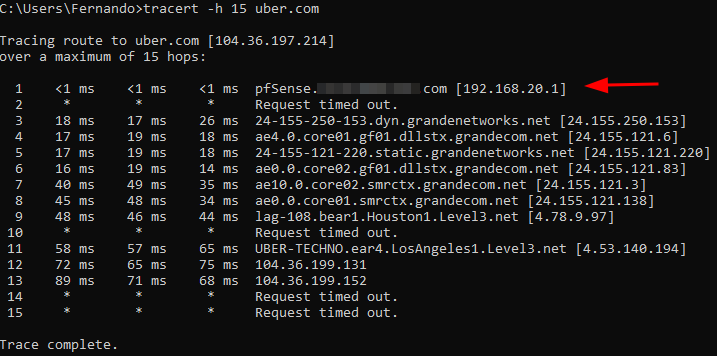
here are the results of tracert:
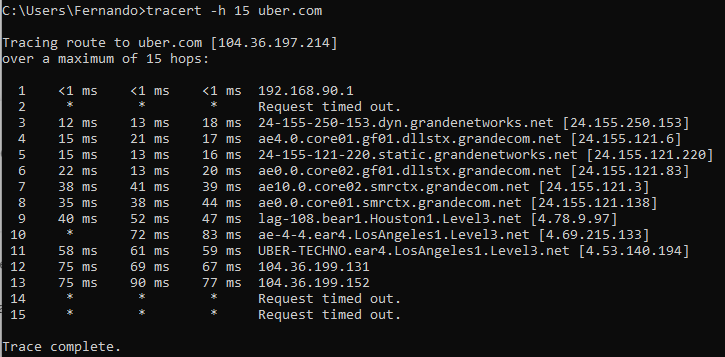
This is ping:
-
Hmm, interesting. That all looks OK.
And, to be clear, if you connect that same client to the LAN you can then reach those sites as expected?
-
@stephenw10 yes, i can access it normally when im on the LAN network.
i ran a traceroute while on LAN and these are the results.
The only difference is the first hop: