Upgrade to 2.6.0 causes voip to no longer work and I can't ping the internet
-
Your first three rules are taking all the traffic..
Anything below them has seen no traffic whatsoever since your box was rebooted.
Rules are parsed from top to bottom. If you are trying to block something totally it needs to go on top above any allow all type rule.Bottom rule.. are both of those addresses in the same subnet? If so that rule will do nothing for you. If you have two different subnets there then that is passing through your router to get there and legit. Otherwise addresses within the same subnet trying to reach each other never touch the router. And your allow all rule above that rule will trump it anyways.
How big is your subnet?
-
@chpalmer LOL .. I think the bottom rule was dropped there rather than delete it
The top two were written by me from an article I read primarily for when we were using 2 internet providers at the same timeThe bottom line is that these rules are not causing the problem?
-
Difficult to say as things seem fairly complicated. Can you move the default "allow all" to the very top and try it again some time? Just drag and drop. then save.
I would guess that you do not need any of those other rules at this point. But Im not there to look what else you have going. But the allow all rule will trump anything below it if at the top.
Another thing to consider is that something that was broke and allowed a mistake to work in 2.5 could have been fixed in 2.6 and visa versa.. 2.6 could have an issue with something you had working in the past.
That is why Im being a pain in the ass right now and asking you all these questions to try and make sure that is not the case.. or at least to learn and have some documentation here for others to search later should they run into the same issue you are having with 2.6
I started using pfsense pre 1.0 and had to go back and forth a bit until I learned how to make my particular VOIP company work with this router. Now I have about 22 of them out there becaused Ive finally started to understand them at a point that I usually don't have any trouble.. ;)
Looking at your LAN page.. what is "SingleIP"? I wonder if that has something causing the issues..
-
@chpalmer Subnet
The subnet mask is 255.255.254.0 and on the lan the ipaddresses are 172.17.16-17.1-254 -
@keithunder said in Upgrade to 2.6.0 causes voip to no longer work and I can't ping the internet:
@chpalmer Subnet
The subnet mask is 255.255.254.0 and on the lan the ipaddresses are 172.17.16-17.1-254Yeah so my SWAG is correct. You would never need a rule between two devices on your LAN..
I use 172.31.125.0/24 here myself as my primary LAN. My VOIP is on another interface and not allowed access to my LAN. Although with my "allow all" rule on my LAN I can reach my VOIP interface when needed.
VOIP Interface.
Block VOIP LAN
Allow VOIP ALLBasically that goes with all my interfaces.. if somehow I get a hacked camera (on their own interfaces as well) that camera can not see my LAN.
Cam Interface
Block CAM Lan
Allow CAM AllMake sense? This is good stuff to store in the back of your head in case you need it later.
-
@chpalmer You are not being a pain I am grateful for your responses!
Single ip just uses a different gateway group the other one is loadbalance.
Currently they are identical .. but they can come in useful for diagnostic purposes .. I can muck about with the 3 different ISPs without affecting anyone else.It may well be something broke that was fixed in the latest version. it would be nice to know what it was
this kept appearing in the system log
Feb 17 15:36:00 sshguard 30068 Now monitoring attacks.
Feb 17 15:36:00 sshguard 61375 Exiting on signal.I have no idea what this means
-
SSH is a terminal (for lack of a better word for it... stop typing now haters) connection. Have you ever used something like Putty to connect to your router? So has the rest of the world if you have port 22 open to on the WAN.
My guess is (because Im not sure) that SSHguard is the security program in place to keep that from happening.. If it is going up and down I wonder if your WAN is not stable.. I need to look at my logs and see if that is common between us..
Just looked and I do not have that in my logs. Keep forgetting I can see my router from this laptop while out and about via a VPN I have active..
That said I do not have that in the last 200 lines of my logs. That is interesting.
-
@keithunder said in Upgrade to 2.6.0 causes voip to no longer work and I can't ping the internet:
this kept appearing in the system log
Feb 17 15:36:00 sshguard 30068 Now monitoring attacks.
Feb 17 15:36:00 sshguard 61375 Exiting on signal.Look at thread https://forum.netgate.com/topic/169923/tons-sshguard-log-entries-and-its-not-enabled
-
The last two versions are available on the download servers still:
https://nyifiles.netgate.com/mirror/downloads/sshguard monitors the logs for failed login attempts, of any sort not just SSH, and reacts by blocking source IPs after a number of failures.
@keithunder said in Upgrade to 2.6.0 causes voip to no longer work and I can't ping the internet:
this kept appearing in the system log
Feb 17 15:36:00 sshguard 30068 Now monitoring attacks.
Feb 17 15:36:00 sshguard 61375 Exiting on signal.What you are seeing there is not an error it's sshguard restarting when the log files rotate to monitor the new log.
Steve
-
@chpalmer So either
- the old version is faulty and the new version fixes the problem causing my misconfiguation to block ping and voip
OR
2. The new version has a bug and my configuration is unusual and is causing the error.Assuming it is 1. what rules can I safely ditch on my Lan?
Which of these services can safely go?
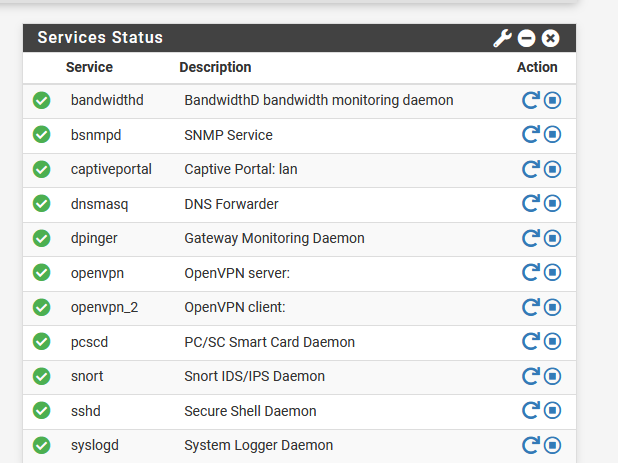
-
@keithunder said in Upgrade to 2.6.0 causes voip to no longer work and I can't ping the internet:
why can't I download a 2.5 version which worked?
2.5.2 is still available. Go to the download page, DO NOT SELECT AN ARCHITECTURE, simply hit download. You end up in a directory that still includes the 2.5.1 and 2.5.2 versions.
-
@revengineer Excellent thank you
-
@keithunder said in Upgrade to 2.6.0 causes voip to no longer work and I can't ping the internet:
Which of these services can safely go?
Did you enable pcscd? It's supposed to be disabled by default in 2.6/22.01 because it's rarely needed and had a memory leak in the prior version. If you're not using IPSec you can just stop it.
As for the others, you'll have to tell us which packages you have installed that you're not using.
-
@steveits It don't know what pcscd is if 2.6 had disabled it then I can't see that as the problem it does not appear on my 2.6.0 rig.
I have set up a test rig with 2.6 and have tried turning services and firewall rules off .. nothing seems to fix my problem
I am using captive portal and snort .. I am not using open vpn
I don't know what the other are and if I need them
-
@keithunder Interesting, pcscd is not listed on my 2.6 router after upgrading. Although I had at least stopped it...don't recall if I bothered putting in the patch on that one. If you leave it running check used memory every month or so in case it still has the leak.
Here's the release note section with the bullet point about it being optional.For OpenVPN you probably have a server and client configured. Presumably enabled SNMP and captive portal as well. Bandwidthd is a package to monitor bandwidth usage. The others I think are all defaults. Mine has these, besides a couple packages:
ntpd NTP clock sync
dpinger Gateway Monitoring Daemon
radvd Router Advertisement Daemon
sshd Secure Shell Daemon
syslogd System Logger Daemon
unbound DNS Resolver (instead of Forwarder) -
@steveits Thank everyone for the responses
I disabled all the firewall rules except the pass all one and shut down all the non vital services
I still can't ping 8.8.8.8
Is there anything I can do to work out why this is happening? I can ping 8.8.8.8 from the pfsense box so the problem must be with pfsenseI tried installing 2.6.0 from scratch but I could not log into the web interface ... so I gave up :(
Maybe I will try again :(I can't upgrade to 2.6.0 until I have resolved this
-
Start a ping to 8.8.8.8. Then check Diag > States to make sure the correct states are being opened. You should see a state on the internal interface and a state with NAT on the WAN.
Steve
-
@stephenw10 the states relating to 8.8.8.8 all say 0.0
I have no idea what this means though :)
-
@keithunder I don't see where you answered my question about having any limiters configured...? In that other thread limiters seem fine for some but problematic for others.
-
@steveits I don't think I have any limiters configured.. How would I find out if I had?