VMware Workstation VMs Web Traffic Being Blocked
-
@dfinjr
It makes sense to me why going NAT would work but I did just verify that it makes the hosting services invisible on the network. So it does fix browsing but does break the availability of listening services. -
@daddygo
Thank you for all the help today! I am going to keep going but you've shed some light on things to say the least! -
@dfinjr said in VMware Workstation VMs Web Traffic Being Blocked:
but does break the availability of listening services.
Well this is how I hide my Ubuntu machine on WS16, yes indeed not a "bridge" type connection
-
@dfinjr said in VMware Workstation VMs Web Traffic Being Blocked:
but you've shed some light on things to say the least!
you're welcome,
if you keep testing, post it here so I can see it tomorrow
-
@stephenw10 said in VMware Workstation VMs Web Traffic Being Blocked:
I could imagine happening are the Cisco doing some fragmentation or reassembly pfSense is not.
Is there a way for me to enable something like this in pfsense?
-
@daddygo
Will do! -
@dfinjr There is one setting that might do something like that though the traffic you have there would not normally affected. In Sys > Adv > Firewall&NAT try setting 'IP Do-Not-Fragment compatibility'.
Make sure the Cisco router did not have jumbo frames set on any of it's interfaces.
To get a definitive diagnostic I would try to capture a failing connection on the pfSense LAN and the host VM at the same time so we can compare exactly what each is seeing.
Filter both by the external IP it's connecting to so we don't have to wade through a load of other traffic if possible.Steve
-
@stephenw10
Thank you for the advice. I'll perform that test as soon as I'm back onsite (tonight/tomorrow early AM) and also validate your inquiry about jumbo frames. -
@stephenw10
Good morning Steve, picking up where I left off this morning. Here is a screen shot from the Cisco device, which I failed over to yesterday afternoon for some work stuff but I just redid the test and then processed this output. I'll do a quick packet capture while I'm at it before I switch back over to the netgate appliance and resume testing. Let me know if you want a packet capture while the Cisco appliance is hooked up because I'll have it but won't send it to you unless you think it would be helpful:
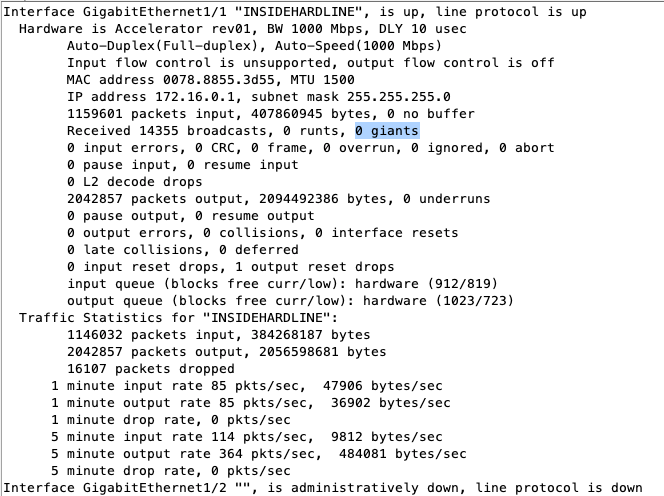
I'll resume testing after I switch over her shortly back to the netgate.
-
No that looks fine, nothing there looks like it would be doing anything different.
I think simultaneous pcaps form the pfSense LAN and the client should be revealing.
Steve
-
@stephenw10
Ok got it all done, noticed something interesting this morning that was a little different. Still sites failing but I tried bestbuy.com and amazon.com this morning and amazon super struggled to load but I think eventually completed and bestbuy also navigated. However, gmail, gmail webstore and speedtest.net (and the sites I use for work) all failed to load/render.Attached is from the client as well as the capture from the "labsystems" vlan where the client resides. packetcapture-3.cap clientcaptureshort.pcapng
-
@stephenw10
Just realized I didn't have that "IP Do-Not-Fragment compatibility" turned on so I turned it on and reran the test. Same results. packetcapture-4.cap clientcapture443-3.pcapng.gz Both perspectives are again attached. -
@dfinjr Yeah your frame size is all messed up!
Client capture
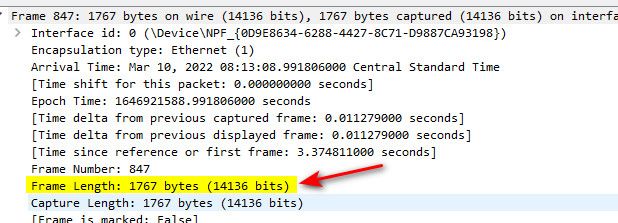
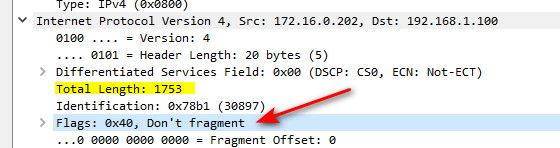
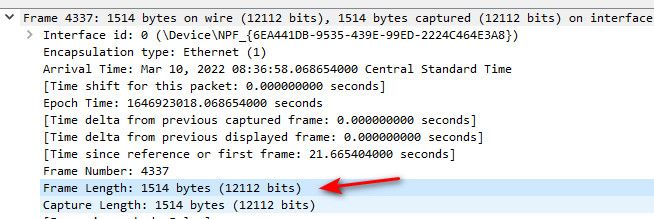
Here is from a normal client with your typical mtu of 1500. Talking to a local server
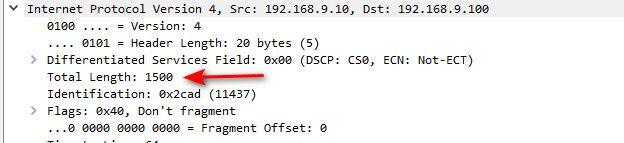
-
@johnpoz
Hello, thanks for jumping in!Is the fix for this then to bump up the MTU on the VLAN Interface? If yes, what value do you think I should use to best test?
-
@dfinjr why would your client have such an odd mtu set?
Your clients mtu should be the standard 1500...
-
@johnpoz
Honestly no idea at all. It is a stock VM build. The VM works on that Cisco appliance so never really considered it was anything to do with the client. Happy to try any and all suggestions for testing! -
@dfinjr well you got something messed up that is for sure.. Either on the vm itself on on the VM hosts interface.
That 172.16.0.202 shouldn't be putting that sized frame on the wire!
Here is a vm of mine... See the mtu of its interface is 1500
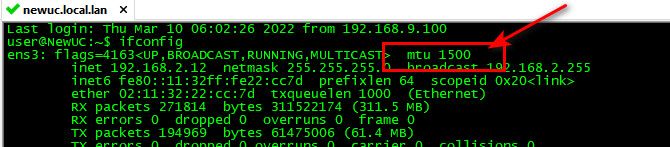
if I look at every possible interface on my vm host, they are all 1500, which is the standard ethernet frame size
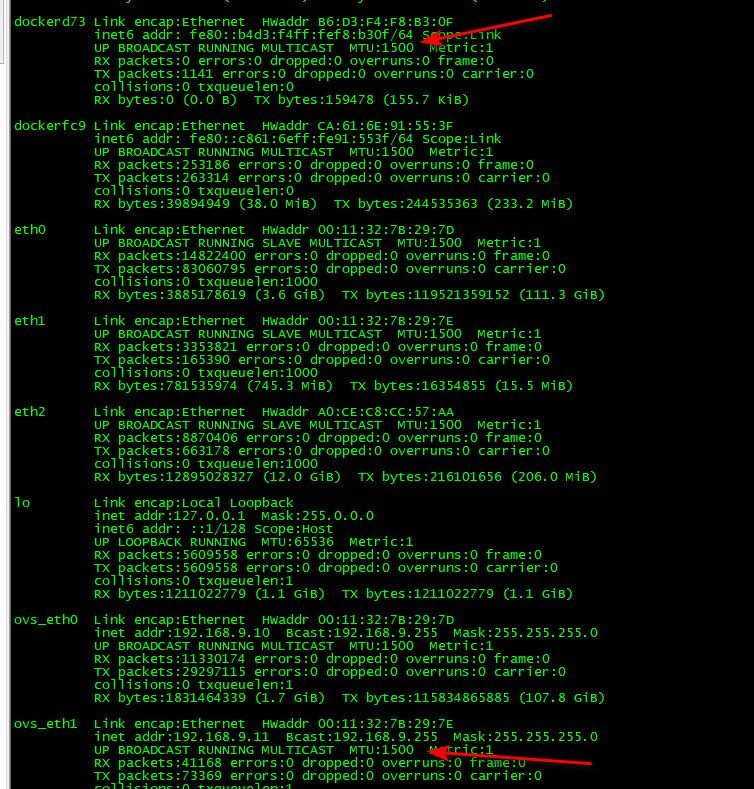
-
@johnpoz
Trying to understand a little more so please don't take this as anything but naivety on my part. Why would it work on a Cisco appliance and not the pfsense appliance? That same VM has been running to expectation for the last 2 years or so with 0 modification. If I were to fail back to the Cisco appliance it would work without me modifying any of the VM settings and then if I put it back on the pfsense this issue comes back.Not saying that there isn't something wrong on the stock load for the VM (which I am currently researching how to adjust based on what you said) but also my brain isn't letting go of that difference and is trying to understand it.
-
@dfinjr said in VMware Workstation VMs Web Traffic Being Blocked:
Honestly no idea at all.
for a test try going with vmxnet3 instead of E1000e, edit the vmx config file so:
ethernet0.virtualDev = "e1000" change to ethernet0.virtualDev = "vmxnet3"
-
@dfinjr Well that would only work on a network where that frame size was normal.. Maybe VM to VM traffic across only a VM switch, or on a network set for that.. But its not even a typical jumbo size frame.
I have no idea where that came from, but it sure and the hell isn't going to work on a normal ethernet network.. That uses standard frame sizes.