hacking SSID
-
@aledio said in hacking SSID:
tp link TL-WA801ND
I have one of those and it has problems because TP-Link doesn't understand VLANs. If you suspect someone has broken WPA2 (do you have proof?), then replace your password with a strong one. I get mine from www.grc.com and use a 63 character random string.
I replaced the TP-Link with a Unifi AC-Lite AP, which not only works properly with VLANs, but also supports 5 GHz. -
@johnpoz said in hacking SSID:
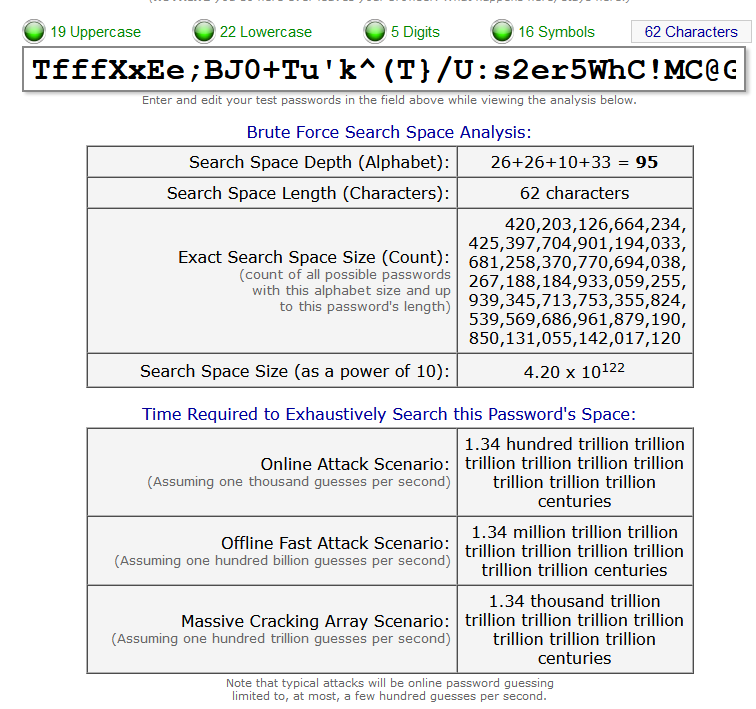
This would be a good psk ;)
5pp6ZH@DSccetrWvbhj#I uses ones like this:
BTTD7f21Zu1hLx0LwYwthJLUfJFj9rtKX696npf0jHlak8JryFpzGYqFRaLBghC -
@nogbadthebad said in hacking SSID:
I had a play with a couple of Aruba Instant APs 345 ( not the InstantOn one I run at home ) was very impressed with the abillity to use one of the APs as the controller as well as an AP.
With Cisco, dumb APs connect to a controller running on a switch.
-
@stephenw10 said in hacking SSID:
The number of times I have to transfer a lot of data locally is just insignificant
If I was moving significant data locally - I would use a wire ;) heheh even if my laptop supported AX... Sorry while AX is cool and all, and hey speeds are getting pretty impressive to be sure.
Not going to beat a wire, my wire can do 2.5.. If my wifi could do 2.5, then my wire would be able to do 10, etc..
Wire is always going to trump wireless.. It will always be the right bower, if any Euchre players about ;)
-
@jknott said in hacking SSID:
I uses ones like this:
BTTD7f21Zu1hLx0LwYwthJLUfJFj9rtKX696npf0jHlak8JryFpzGYqFRaLBghCOops, not good enough, no symbols...

-
@akuma1x said in hacking SSID:
Oops, not good enough, no symbols...
TfffXxEe;BJ0+Tu'k^(T}/U:s2er5WhC!MC@GHC]Hc(yC}oa<p1mqz5OmCo&z_
-
@jknott said in hacking SSID:
With Cisco, dumb APs connect to a controller running on a switch.
I didn't want Cisco to decide when my 2702i's should be obsoleted, so i am on Autonomous not Lite/CapWAP.
No biggie for me .... I was using them before "Lite".
And i just have 5 active AP's @home / summerhouse.I even have an old C1242 doing 54Mb coverage in the garden via an ext antenna (have no C2702E's) , works fine for light browsing & a web-radio.
-
-
@ciscox
And 10min with (when) enough QBIT's -
@akuma1x said in hacking SSID:
no symbols
Character 47 is nonprintable? Maybe?
 While more secure those are definitely harder to manually put into a TV or something without a keyboard or copy/paste. I have a bit of ASCII art as my SSID and found once it's rather annoying to enter manually.
While more secure those are definitely harder to manually put into a TV or something without a keyboard or copy/paste. I have a bit of ASCII art as my SSID and found once it's rather annoying to enter manually.@Aledio per https://www.tp-link.com/us/user-guides/tl-wa801n_v6/chapter-3-customize-your-network#ug-sub-title-5 that model has Wireless MAC Filtering so you can block the MAC address, or as noted if they start changing MACs you can allow just your devices' MACs.
@CiscoX said:
I think you are safe for some time
yes well now he's posted it for us. :)
-
@bingo600 said in hacking SSID:
I didn't want Cisco to decide when my 2702i's should be obsoleted, so i am on Autonomous not Lite/CapWAP
It would be nice if more APs went with a central controller. With 802.11r you still have to disconnect and reconnect as you move between APs. With the Cisco central controller, you connect to it, instead of the APs, which become little more than bridges.
-
@steveits said in hacking SSID:
While more secure those are definitely harder to manually put into a TV or something without a keyboard or copy/paste.
My Sharp/Roku TV won't accept 63 characters. It chokes somewhere after 40 or so. So, it's on my guest WiFi, which has a much shorter password than my main SSID.
-
@steveits said in hacking SSID:
yes well now he's posted it for us. :)
I don't use that one. I just got it from www.grc.com.
-
@ciscox
I guess it will keep someone busy for a while.

BTW, it should have had 63 characters, but I guess I missed one when copying it.
-
@jknott
hehe, that would be one more century for your extra character
-
@ciscox
Actually, a bit longer I think. Another character means 96 times what's listed. I'd better grab a beer first.

-
try to set up wifi aps instead of repeaters.
use the maximum of 63 chars long password (not supported at all vendors)small raspberry pi with linux and install
- OpenLDAP for wired devices
- FreeRadius for wireless devices.
put all wifi clients into vlans, e.g.
vlan10 for family = radius certificate - internet & LAN
vlan20 for guests = vouchers - internet onlyAlternatively:
Install a small wifi card into your pfsense and turn on
hotspot with voucher system for guests, can also be a
solutiongive all clients a static IP address in the entire network
and then narrow down the DHCP address space to them,
that means no other free dchp addresses will be able to given out.Setting up snort and/or suricata on pfsense and OSSec
on any other devices, you may need another small server
but also another security line.Turning on wireshark and sniff on your wifi for a while
perhaps on an rapi or notebook or your laptop at the weekend. Watch out any other IPs then your own ones.try narrow down the entire signal strength of your wifi
so it is enough for you but only in the near area of you
house or apartment. Try to implement WPA3 where ever
you can do it.Alternatively you may be also able to get hands on
UBNT wifi aps and then you may get also a small
edge router from them and install there the radius
server. -
If your wireless access point allows user control over transmit and receive power levels lower it so it only works in your home. I would also use snort on the LAN interface with AppID enabled with full manually created text rules and only approve what you normally use. It takes a while but if he is hacking your network and say normally uses ESPN and you don't it will block it until you approve it. Use AES it's harder to break into. He will eventually spoof a device in your homes mac address to get back on also some pen testing software allows you to spoof mac addresses. Another option is to get a cheap AP configure it to the same SSID you used before and leave it blocked for everything and change your SSIDs to something else that you use with lower transmit power. Or just hard wire some RJ45 cables up and disconnect all of the wifi he is using. Wifi is not really safe. Windows 10 for a long time didn't even care what bssid it was using as long as the SSID was the same it would connect. You can also vlan the wireless access point like @johnpoz does that way everything on the wireless lan is inspected at the firewall too.
-
You guys all scare the hell out of me.
I've loads of APs without any passwords at all.And at home neither, as I haven't seen yet any rabbits with some BYOD ....