Pfsense 1:1 NAT with site-to-site ipsec
-
Hi all,
I have two pfsense boxes on two sites which connected together using ipsec tunnel. and the site_1 pfsense installed openvpn server which I use to access the remote networks of both sites. My setup works perfectly fine except issue with one overlapping VLAN
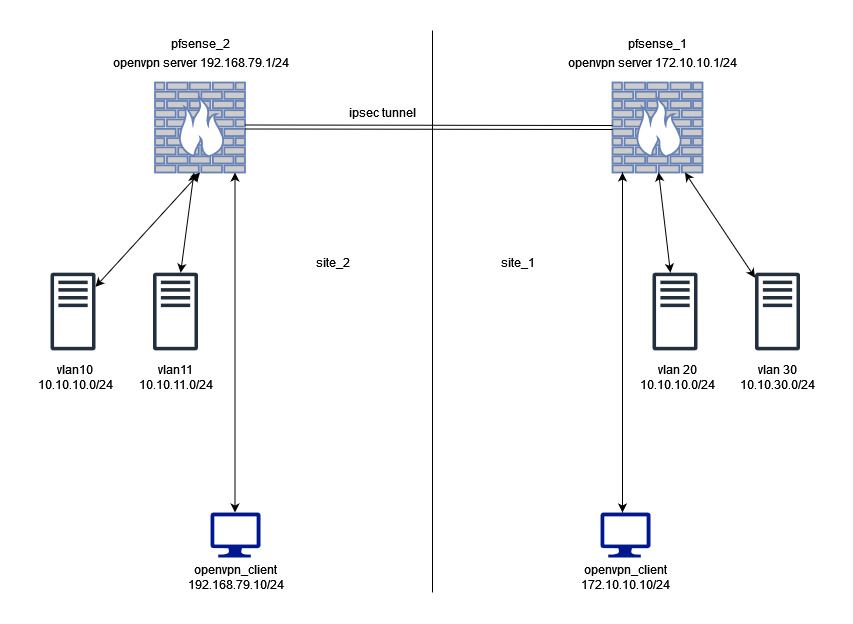
As you can see from this diagram, VLAN10 subnet from the site_2 is conflicting with VLAN20 subnet of site_1. due to this I cannot add this VLAN to the pfsese_1 ipsec phase 2 configuration.
Now there is vpn server running on site_2 pfsense_2 as well. which is used by engineers from the site_2. but site_2 engineers not required to access site_1. only the site_1 engineers require to access site_2 networks.
For now I need to switch the site_2 vpn every time I need to access the site_2 VLAN10. all the other networks can accessible from site_1 pfsesne_1 openvpn.
I tried to add 1:1 NAT on site_2 pfsesne_2 to overcome this.
10.10.13.0/24 : 10.10.10.0/24this works when I connect from site_2 pfsense_2 openvpn. I can connect the VLAN10 subnet using 10.10.13.0/24
but this wont work when I try to reach the VLAN10 from site_1pfsense_1.
pfsense_1
-ipsec phase2
--src=172.10.10.0/24
--dst=10.10.13.0/24pfsense_2
-ipsec phase2
--src=10.10.13.0/24
--dst=172.10.10.0/24
NAT
-1:1
--10.10.13.0/24 : 10.10.10.0/24 interface ipsec
-Outbound
--src=any dst=10.10.10.0/24 interface=vlan10How can I fix the issue and access VLAN10 also from site_1 pfsense_1 openvpn client
Thanks.
-
You cannot use NAT rules across an IPSec tunnel like that.
You can only use the BI-NAT option in the phase 2 config.
In this situation you would need to binat on a P2 at both ends to prevent the conflict.
So something like:10.10.10.0/24:10.200.10.0/24 ====== 10.100.10.0/24:10.10.10.0/24
Steve
-
Thanks for the reply,
Could you explain how exactly I need to add this ?
which address pair on which side of the tunnel ?
"You cannot use NAT rules across an IPSec tunnel like that.a"
Also, could you point some links to read why this is not possible -
So the P2 will effectively end up being (in my example) 10.200.10.0/24 to 10.100.10.0/24.
Each side 'hides' it;s local 10.10.10.0/24 subnet behind another, same sized, subnet. You could use any unused subnet for that I just chose 10.100.10.0 and 10.200.10.0.So on each side that would be the Binat address.
https://docs.netgate.com/pfsense/en/latest/vpn/ipsec/phase-2-nat.html
However if you do not need access between the two subnets dircetly but only from the pfSense_1 OpenVPN subnet this becomes easier. You only need to BiNAT on the pfSense_2 side like:
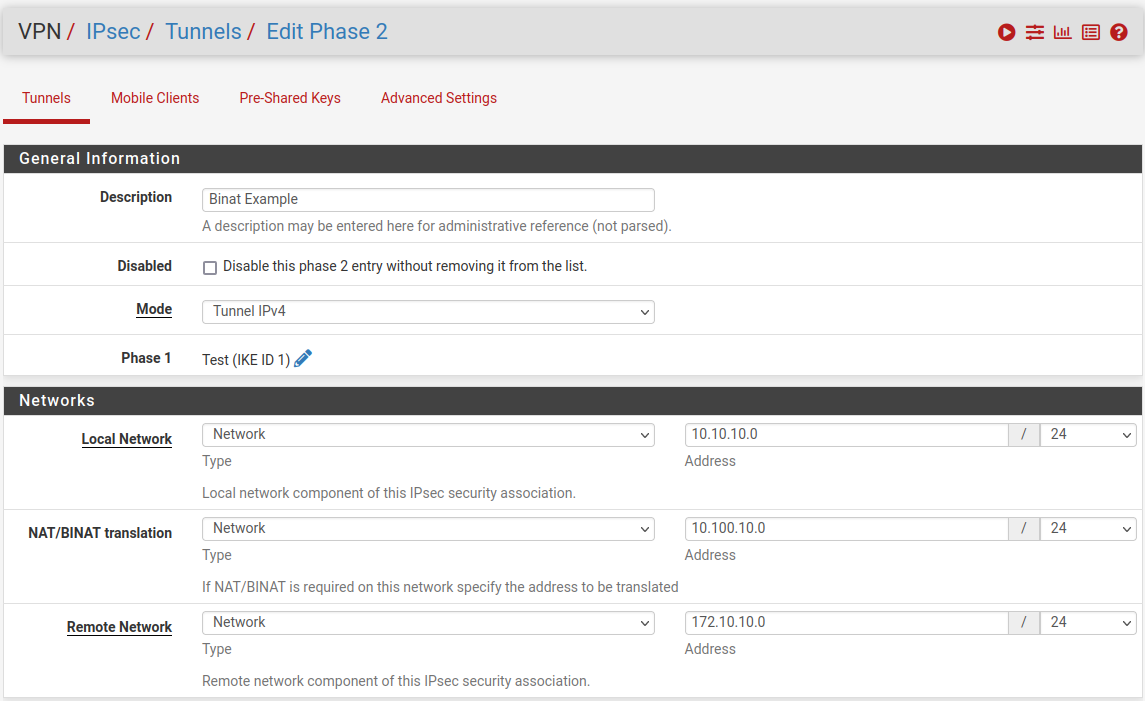
On the pfSense_1 side the P2 would be just be 172.10.10.0/24 to 10.100.10.0/24
To access the remote side VPN clients would need to use the equivalent NAT address.
Steve