pfSense with OpenWRT Guest logon with VLAN
-
@ramosel said in pfSense with OpenWRT Guest logon with VLAN:
So what would be your best thoughts
If me - I would just get a unifi wifi 6 pro for $149 and call it a day.. I show those WRT3200ACM for $249 on amazon. I sure hope you didn't pay that much..
Click click and you can run whatever vlans you want on any ssid, like a 2 minute setup ;) How many hours you got playing with this currently ;)
-
@ramosel said in pfSense with OpenWRT Guest logon with VLAN:
So what would be your best thoughts on what needs to be filitered?
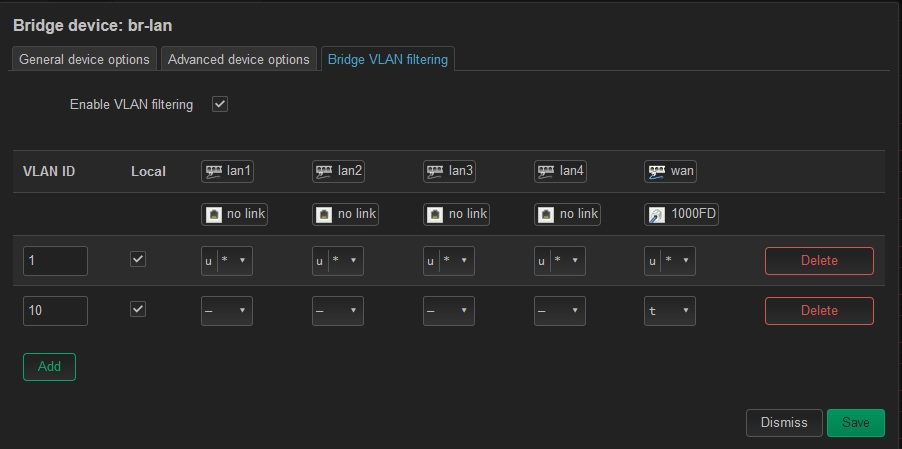
To use DSA as expected you should have VLAN 1 untagged on all ports and also the PVID on all ports. Local should be checked so the router itself can use it
VLAN 10 should be tagged on the WAN port only.
Local can be set there too so you get an IP in the vlan 10 range but it doesn't have to be. You will probably want to change that later so guest wifi clients can't connect to OpenWRT (and OpenWRT cannot route between the subnets).Steve
-
@johnpoz If I were smart... I'd have gone that way too.
All joking aside, I have always been partial to Linksys in the plastic box world. Been running them since the WRT54G v2. (and for 20 years on DD-WRT). I'm retired and one of the kids who used to work for me, who I picked to fill my position has a buddy who works for a company that buys equipment coming off lease. He saw pallets of these WRT3200ACMs at his buddy's warehouse and called me. I picked up half a dozen for (a little) less than your Amazon price. Other than this @$?#&(#/!! VLAN issue, they really are working well for their intended purpose.That said, if you'd still like to help, I have one built out to my current config I can still send your way. Either DM me or use my email (on my profile) to get me Mailing address and I'll pop it in the mail to you today when I venture down off the mountain to go to town.
Rick
-
@stephenw10 said in pfSense with OpenWRT Guest logon with VLAN:
@ramosel said in pfSense with OpenWRT Guest logon with VLAN:
So what would be your best thoughts on what needs to be filitered?
To use DSA as expected you should have VLAN 1 untagged on all ports and also the PVID on all ports. Local should be checked so the router itself can use it
VLAN 10 should be tagged on the WAN port only.First of, Thank You and John for all your help. It really is appreciated and I know you guys are busy.
Well, we made two steps forward, one backward. That is the first VLAN filtering config that hasn't locked me out and caused a revert.
DSA did successfully create the br-lan.1 device
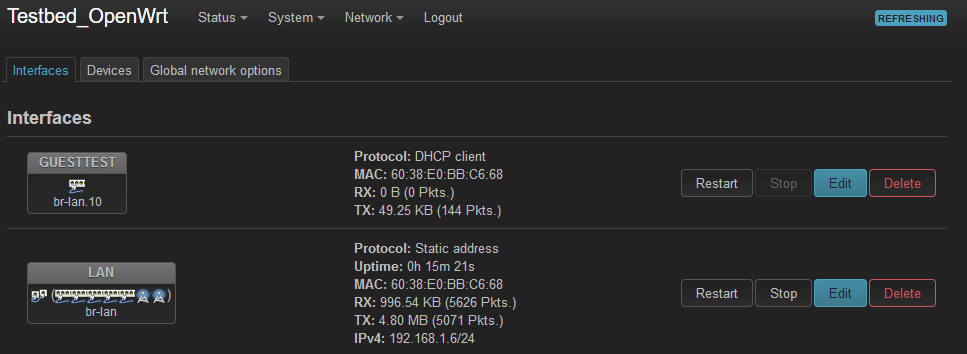
But now... the DHCP client on the GuestTest Interface is no longer getting an address.
-
@ramosel While I do really appreciate the offer and would be happy to play with it to help you figure out if you didn't have much better help in such matters already helping you @stephenw10 - if you were going to ship one for someone to help you - he would be the guy for sure..
If you have a bunch of them to spare, and were not expecting it back I would say send to Steve for his collection of hardware - he seems to collect all kinds of stuff, he always seems to have something in his lab to fiddle with when helping users..
Back in the day I use to love to fiddle with getting the most out of soho stuff, I had a few of those original wrt54g - I believe first router I had was their BEFSR41..
But now getting older and more money to play with - I like my shit to just do what I tell it to, without having to "fiddle" with it ;)
But Steve would be a good choice for sending one out to - it will prob be able to help many more fellow pfsense users in the future that is for sure, when the next guy comes along trying to do something with their WRT3200ACM, or something very sim..
-
@johnpoz said in pfSense with OpenWRT Guest logon with VLAN:
But Steve would be a good choice for sending one out to - it will prob be able to help many more fellow pfsense users in the future that is for sure, when the next guy comes along trying to do something with their WRT3200ACM, or something very sim..
Thanks for the response and I will certainly make that offer in that direction.
Steve, I do have a WRT3200ACM built up to my configuration. I'll certainly donate it to the cause to help get this fixed. If you can get an address to me, I'll get it on it's way.
I'm in the pfSense database somewhere. I have one of your SG-4860s that you have warranteed once. Send me an email, call me... what ever is easiest for you and I'll get this moving.
Rick Moseley
-
I'm in the UK which makes shipping something like that... more of an issue!
I may be able to get one locally. I think there is only one hardware version?What I don't see in your screenshot there is a wireless device on the GUESTTEST interface.
Try editing the wireless network and moving it to LAN and then back to GUESTTEST. It's possible it never got added to the bridge as the correct VLAN because VLAN filtering wasn't enabled at that point.I would have expected the GUESTTEST interface to pull an IP itself though since it's enabled as local.
Otherwise try installing ip-bridge and running
bridge vlanas I showed above to see how it's currently configured.Steve
-
@stephenw10 Cost is not an issue... one of my best friends runs Cosworth (from Texas). I can get it to you one way or another.
-
Ah, OK.

Well let me see what I can do locally anyway since it would probably be quicker.It looks the Espressobin image is now DSA too and have multiple SG-1100s that will run on.
However the fastest thing will be if we can just see what's not happening on your setup.
Are you able to install the ip-bridge package and runbridge vlan?Can I assume setting the guest wireless back in the interface didn't change anything?
Steve
-
@stephenw10 said in pfSense with OpenWRT Guest logon with VLAN:
Ah, OK.

Well let me see what I can do locally anyway since it would probably be quicker.It looks the Espressobin image is now DSA too and have multiple SG-1100s that will run on.
However the fastest thing will be if we can just see what's not happening on your setup.
Are you able to install the ip-bridge package and runbridge vlan?Can I assume setting the guest wireless back in the interface didn't change anything?
OK, but if you find something local, please allow me to pay for it.
Yes, I have just installed ip-bridge. "bridge vlan" gets a return but it's useless right now. I need to rebuild the devices, filtering and interface. One other piece came up in research. Since I'm running as a Dumb AP, I have plenty of headspace on resources so it was recommended that the default (minimal) wpad be removed and the full featured wpad be installed. It has. But one of the suggested steps was to remove the bridging, vlans and disable the wireless before installing it.
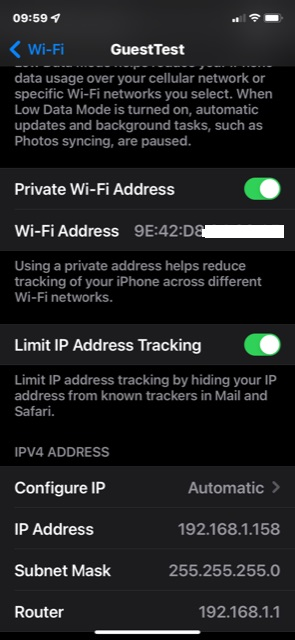
Before I did the above, I did put the GuestTest back on the br-lan to see if anything we had done caused the DHCP client to grunge... it was still good and I got an address on the default LAN immediately. I was able to get my iPad to log onto the Guest network as well. But it's on the wrong network...
I just rebooted and it's up clean. But I have to run to dinner. I'll get back on this when I get home.
Thanks,
Rick -
Hmm, interesting. I would advise not making any changes until you get the VLAN/VAP config nailed down. It could easily confuse things further.
-
@stephenw10 said in pfSense with OpenWRT Guest logon with VLAN:
Hmm, interesting. I would advise not making any changes until you get the VLAN/VAP config nailed down. It could easily confuse things further.
Sorry for my absence. We had a death in the family (expected).
Agree with your statement. I had backups and am doing the secondary testing on my #2 spare (that I was offering up).
So, back to where we were:
- bridge VLAN filtering is applied per your configuration
- no lockout, config holds
- system auto creates br-lan.1
- GuestTest Interface no longer gets a DHCP address.
New discovery:
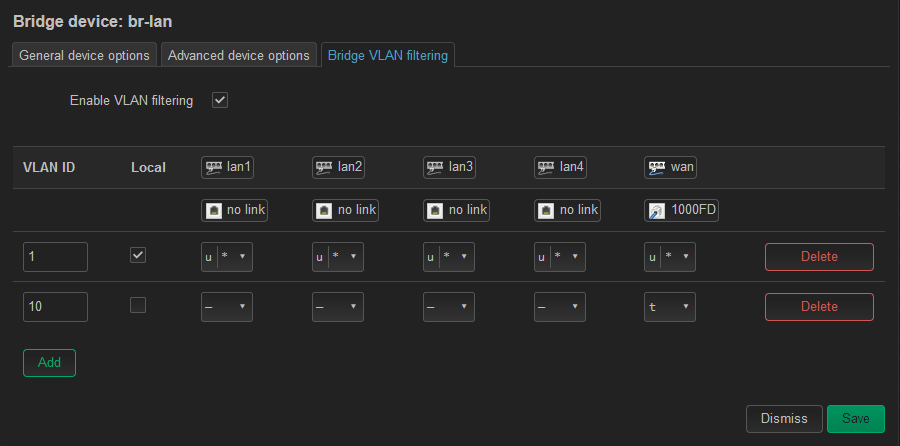
- even though I have the Guest WLAN1-1 linked to the "GuestTest" Network interface I can log onto the Guest Network successfully - WTF? But on closer look, it is getting an address on the LAN network 192.168.1.x. I do now have the Local unchecked for the VLAN.10 I'm not sure how?
Here are the results you asked for from ip-bridge:
I expected br-lan.1 and br-lan.10port vlan-id lan4 1 PVID Egress Untagged lan3 1 PVID Egress Untagged lan2 1 PVID Egress Untagged lan1 1 PVID Egress Untagged wan 1 PVID Egress Untagged wlan0 1 PVID Egress Untagged br-lan 1 PVID Egress Untagged wlan1 1 PVID Egress Untagged wlan1-1 1 PVID Egress UntaggedOne last piece of information:
I noticed when you had me create the VLAN filtering, I had the br-lan.10 created prior and when I configured the 1 and 10 VLANs in filtering and set the tag/untag PVID the system auto created the device for br-lan.1. So as I was putting this test box back in config, I tried to delete the br-lan.10 and see if it would auto create both the .1 and .10 devices... it does not. And it goes into lockout and I have to revert. I don't expect that to make sense, but I hope my explanation is clear. -
Ok, I spent some time looking at this yesterday. I fired up OpenWRT on an 1100, which I haven't tried in a while. It's the same target (mvebu) and includes much of the same hardware as the WRT3200ACM. Crucially including the same type of Marvel e6XXX switch.
I was able to observe exactly the same things you are seeing. It's broken!
Tellingly when you enable bridge VLAN filtering you should have to reassign the LAN interface to the auto-generated vlan device, br-lan.1 here. But you don't. And in fact if you do you will lose connection. I've yet to find a way to actually see how the switch is configured but it's almost certainly failing to add the internal port as a tagged member of those VLANs. Which is why any additional VLANs fail to pull an IP. And also why you can end up with both interfaces in the same subnet since all VLANs that are added as 'local' end up untagged to the same internal port. Though presumably that port uses PVID 1 so one way traffic...
Luckily you are not really using the switch, you only need to get a VLAN interface passed out to the WAN and be available as an interface to attach the VAP.
An additional complication here is that at some point in the future the OpenWRT stable release may become unbroken at which point your current config will stop working because LAN would then need to be assigned as the VLAN. So I recommend using a config with bridge vlan filtering disabled at least for now.There are at least two configs that should work:
As I initially described, creating a vlan on eth0. Unclear if the vridge is required there for the wifi to work. I suspect it isn'tOr creating a VLAN on the WAN port, so:
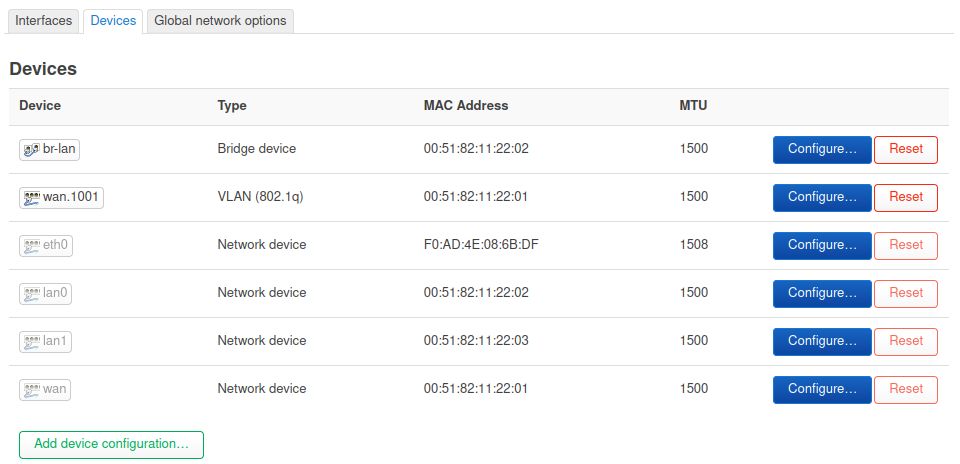
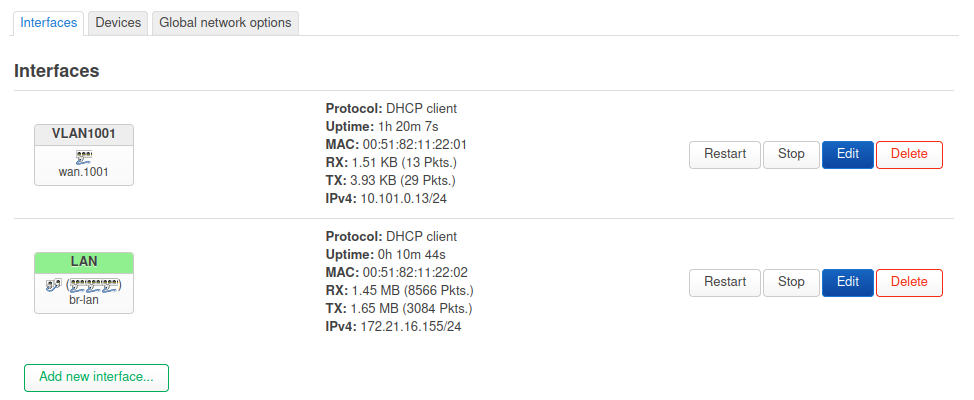
I'll try to confirm that with a wifi interface when I can.
Steve
-
@stephenw10 Thanks Steve!
I've killed the VLAN filtering on br-lan and removed the created/auto created br-lan.1 and br-lan.10
I've put my VLAN 10 onto the wan device as wan.10
Assigned the new wan.10 as the base device for the GuestTest interface. (as a DHCP client)GuestTest gets an IP from the appropriate pfSense network and packets flow on the interface.
I still cannot get a full logon to the Guest WiFi at WLAN1-1.The wireless device MAC shows as an Associated Station on the GUI, but after the login passes auth, it just stalls. On the wireless device the connection just pinwheels.
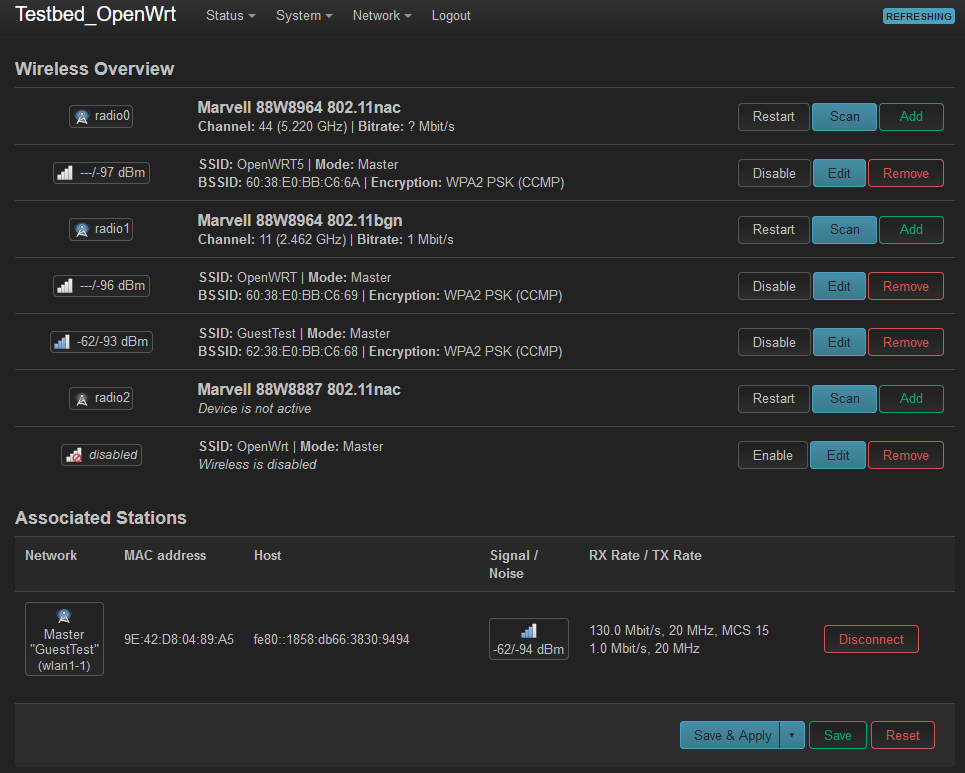
root@Testbed_OpenWrt:~# logread -f Mon Jun 6 09:08:39 2022 daemon.info hostapd: wlan1-1: STA 9e:42:d8:04:89:a5 IEE E 802.11: associated (aid 1) Mon Jun 6 09:08:39 2022 daemon.notice hostapd: wlan1-1: AP-STA-CONNECTED 9e:42: d8:04:89:a5 Mon Jun 6 09:08:39 2022 daemon.info hostapd: wlan1-1: STA 9e:42:d8:04:89:a5 RAD IUS: starting accounting session 661FAB1509F64A01 Mon Jun 6 09:08:39 2022 daemon.info hostapd: wlan1-1: STA 9e:42:d8:04:89:a5 WPA : pairwise key handshake completed (RSN)I'll back out and try the eth0 path.
-
Mmm, I guess it needs the bridge to add the wireless then and doesn't get it without the DSA backend bits.
As an alternative you could use a current snapshot. I can confirm that in yesterdays snapshot the DSA setup works (almost) exactly as described in the docs. There's a bug in 21.02.3 for mvemu and it's now fixed.
The resulting bridge looks like you might expect:
root@OpenWrt:/# bridge v port vlan-id lan1 1 PVID Egress Untagged lan0 1 PVID Egress Untagged wan 1 PVID Egress Untagged 1001 br-lan 1 1001 wlan0 1 PVID Egress Untagged wlan0-1 1001 PVID Egress Untagged root@OpenWrt:/# uname -a Linux OpenWrt 5.10.115 #0 SMP Sun Jun 5 14:58:48 2022 aarch64 GNU/LinuxSteve
-
@stephenw10 said in pfSense with OpenWRT Guest logon with VLAN:
As an alternative you could use a current snapshot. I can confirm that in yesterdays snapshot the DSA setup works (almost) exactly as described in the docs. There's a bug in 21.02.3 for mvemu and it's now fixed.
Steve,
I am sorry for the lack of response yesterday. Had family issues on my mind and let myself go down a rabbit hole.... I should have known better. I did assign the VLAN 10 to the eth0 device and again the interface lost connection. So I went after the Snapshot route you spoke of (that turned into a rabbit hole).
I loaded the snapshot for June 6 and it appeared I had bricked the router. I did the power switch dance and got back to the good partition and tried again as a factory overwrite. Same outcome. Played the power switch cycle again and went back to Linksys, then the factory overwrite snapshot... no response. Surely there is something wrong with the other partition... nope, I was just not thinking clearly. Took the case apart and got my TTL cable out. Was all setup to recover that partition and watched it boot up to a full install. ??? Then I realized that they don't include LuCI in the snapshots... put the case back together, bodged up a connection to the wan interface and loaded LuCI. All's well, I wasted a couple of hours.
I have doctor appointments this morning and will get back on this after I get home... -
@ramosel That is a lot of fiddling for something as simple as assigning a ssid to vlan ;)
And its not even a wifi 6 AP - you know you could pick up a wifi 6 lite model from unifi for $99 ;) Clickity Clickity whatever vlan ID you want to be on.. And it mounts in the ceiling and poe as a AP should be not some ancient relic from by gone days.
-
@johnpoz said in pfSense with OpenWRT Guest logon with VLAN:
$99 ;) Clickity Clickity
But where's the fun in that?

And, yes, sorry @Ramosel, I should have mentioned that LuCI is not in snapshots. I think I also installed luci-ssl separately. And had to install ath9k and the required WPAD stuff since the Espressobin has no wireless hardware by default.
I was looking through the bug list and couldn't find any one thing that matched this exactly. Super frustrating though when you're doing everything right and it turns out a bug stopped it working.
Steve
-
@stephenw10 said in pfSense with OpenWRT Guest logon with VLAN:
But where's the fun in that?
True - but it works without frustration. And now can spend time using my wifi vs trying to get it to work.. And you can barely see it up in the ceiling vs some blue monster sitting in the corner..
I think I'm just getting old ;)
My idea of fiddling these days is running beta firmware on my AP... if something doesn't work, I roll back.. 6.2.19 which is suppose to make iot connections on 2.4 better. Not so much - had bulbs not turning off when told.. Rolled back to 6.2.18 - this is my idea of fiddling these days ;) hehehe
I reported on their forums what make and model of the bulbs, and what AP I was on.. But haven't gotten around to setting up syslog and sending specific logs there.. They have plenty of other people doing that.. It was too much fiddling ;)
-
@johnpoz said in pfSense with OpenWRT Guest logon with VLAN:
@ramosel That is a lot of fiddling for something as simple as assigning a ssid to vlan ;)
And its not even a wifi 6 AP - you know you could pick up a wifi 6 lite model from unifi for $99 ;) Clickity Clickity whatever vlan ID you want to be on.. And it mounts in the ceiling and poe as a AP should be not some ancient relic from by gone days.
John, does unify have a model with (4) LAN ports? I need that for one location.