Ipsec Configuration not Working!
-
@rcoleman-netgate since I am not very strong on how to read the logs and understand what is wrong, could you please help me on that?
concerning the version is that mean I must have same version on both sides?
-
This post is deleted! -
Anyone can help me please, I am 100% sure that use in both sides IKEv2, simplest PSK which is "123" and everything is matched but still I am not able to establish the connection?!!!
Jun 10 11:57:55 charon 08[IKE] <con2000|146> IKE_SA con2000[146] state change: CONNECTING => DESTROYING
Jun 10 11:57:55 charon 08[CHD] <con2000|146> CHILD_SA con2000{165} state change: CREATED => DESTROYING
Jun 10 11:57:55 charon 08[IKE] <con2000|146> received AUTHENTICATION_FAILED notify error
Jun 10 11:57:55 charon 08[ENC] <con2000|146> parsed IKE_AUTH response 1 [ N(AUTH_FAILED) ]Any help would be really appreciated :)
-
@ibnkamala I don't have direct advice for you but note 2.6 made several changes to IPSec, did you review those?
Possibly, upgrade the 2.4.5 which is a few versions old?
-
Would be super helpful if you would show screenshots of the P1 and P2 settings for both sides. And while you’re at it, update the 2.4.5 box. Not really interested in trying to troubleshoot an unsupported version of pfsense.
-
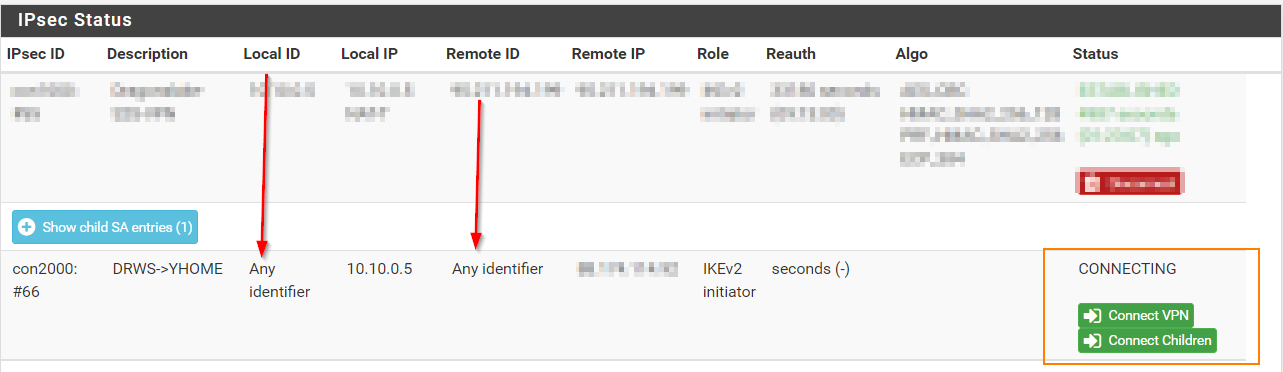
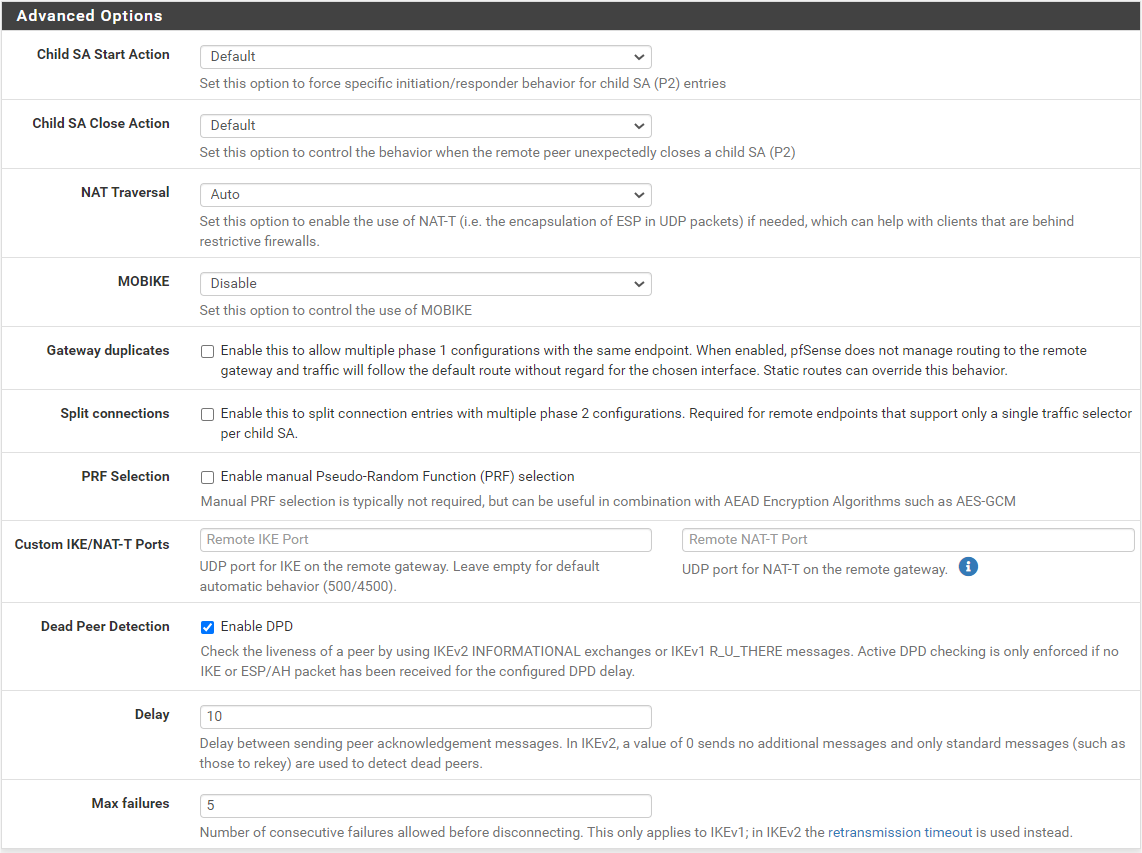
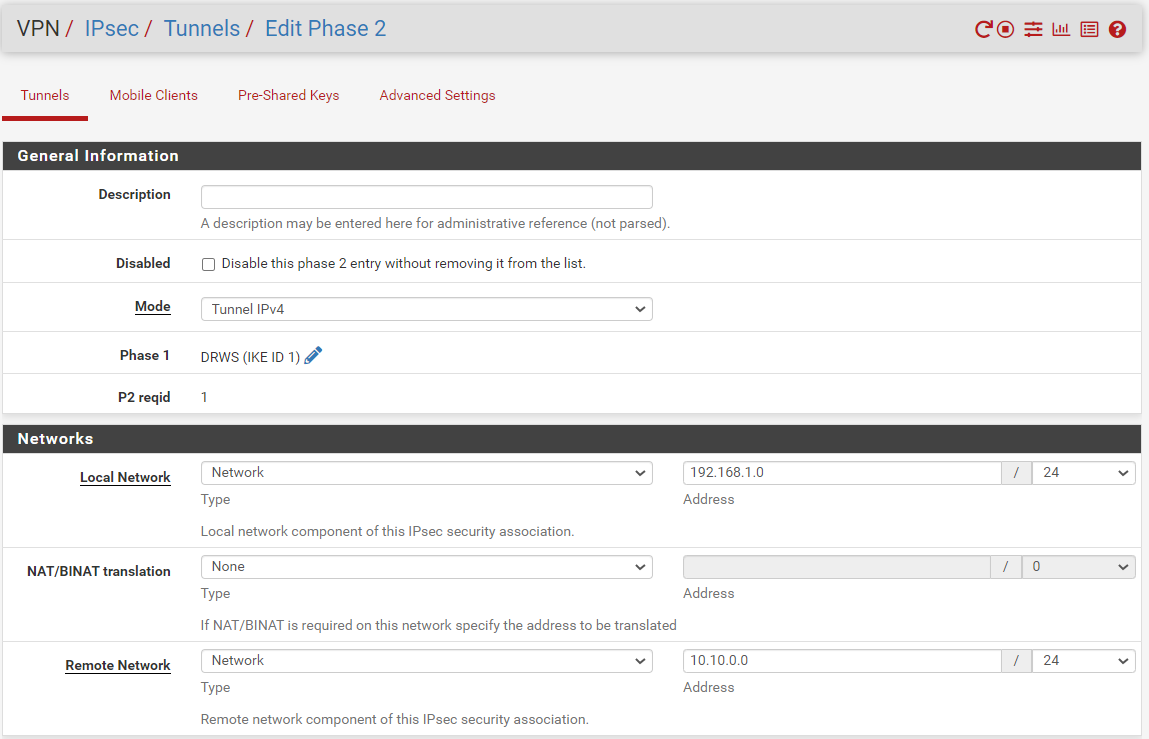
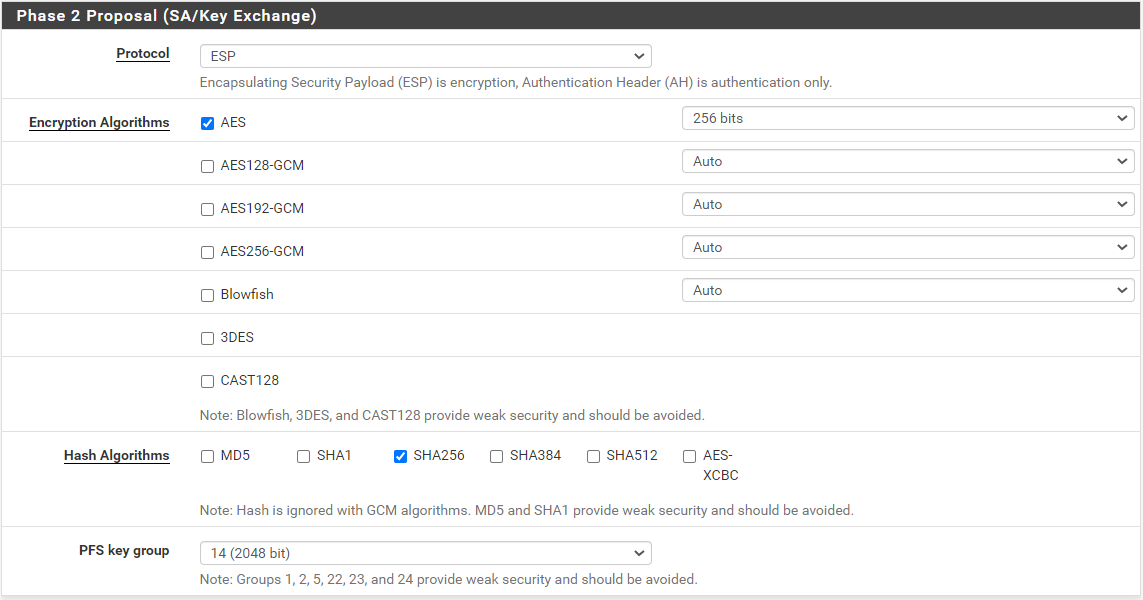
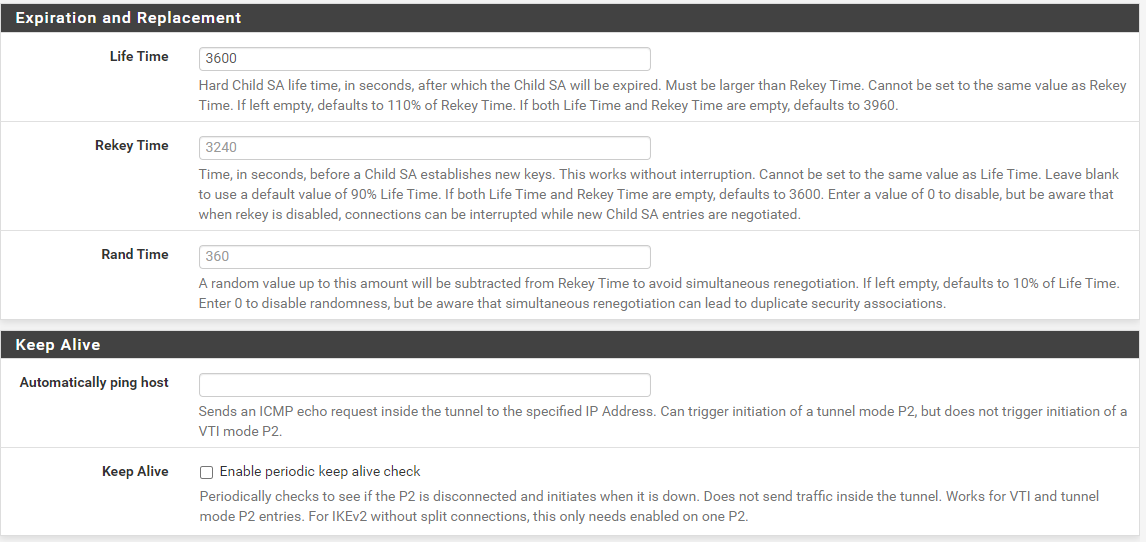
@gabacho4 thanks for your reply I am going to share both sites configurations and here is the screenshot when I try to connect the tunnel.
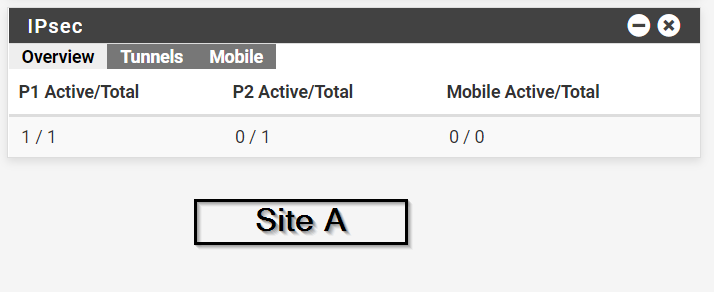
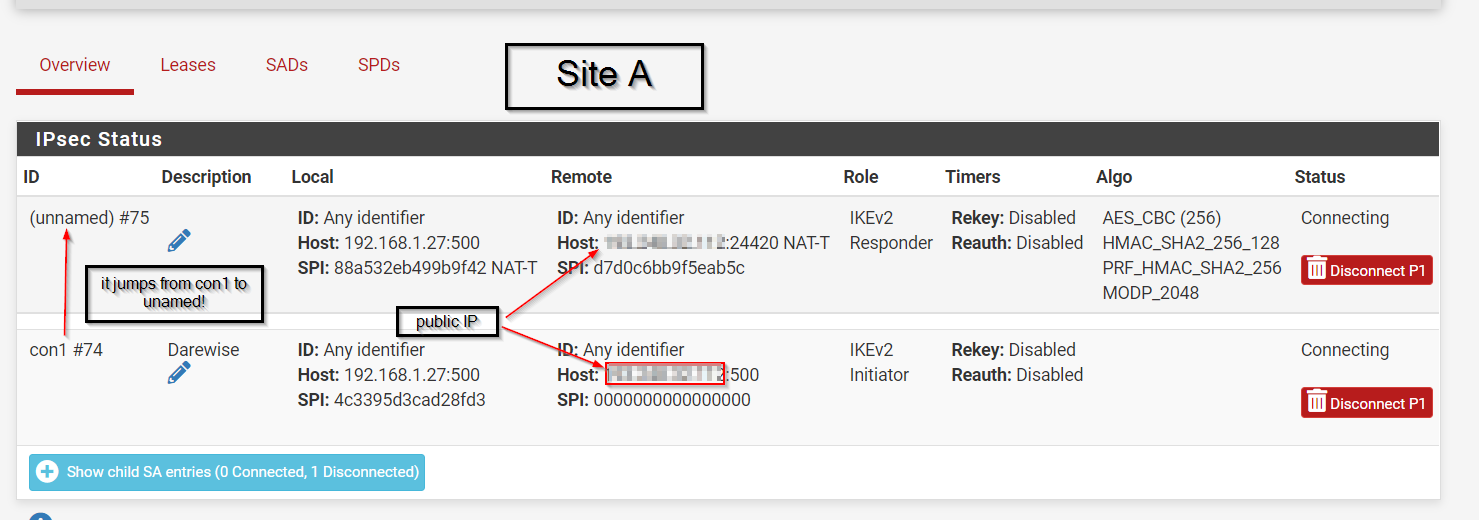
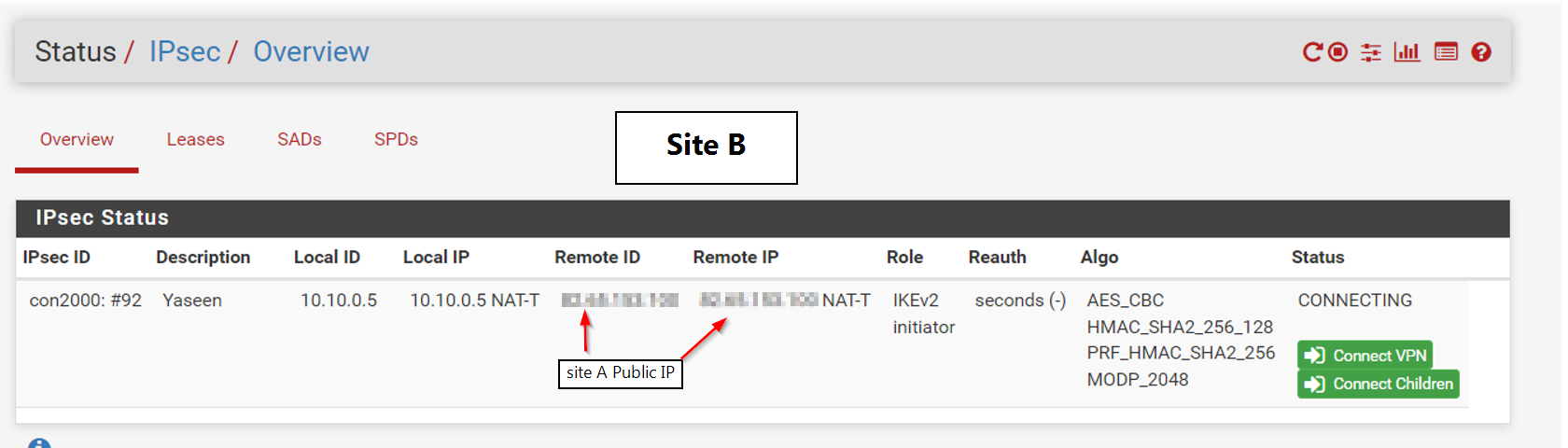
Thanks for your help, for sure I am going to update to a newer version but I wanted to test it first.
-
@ibnkamala those are not the p1 and p2 settings. What you’ve sent is a screenshot of the ipsec status. It tells me nothing other than the fact that your IPSec connection isn’t working which has already been established by your other posts. Please send screenshots of the actual p1 and p2 configurations for both sides of the tunnel. Those are what you configured when you went to VPN - IPSec and then created the p1 and p2.
-
-
@ibnkamala you’re killing me bro. And what about side B?! I need both sides to compare. Come on.
-
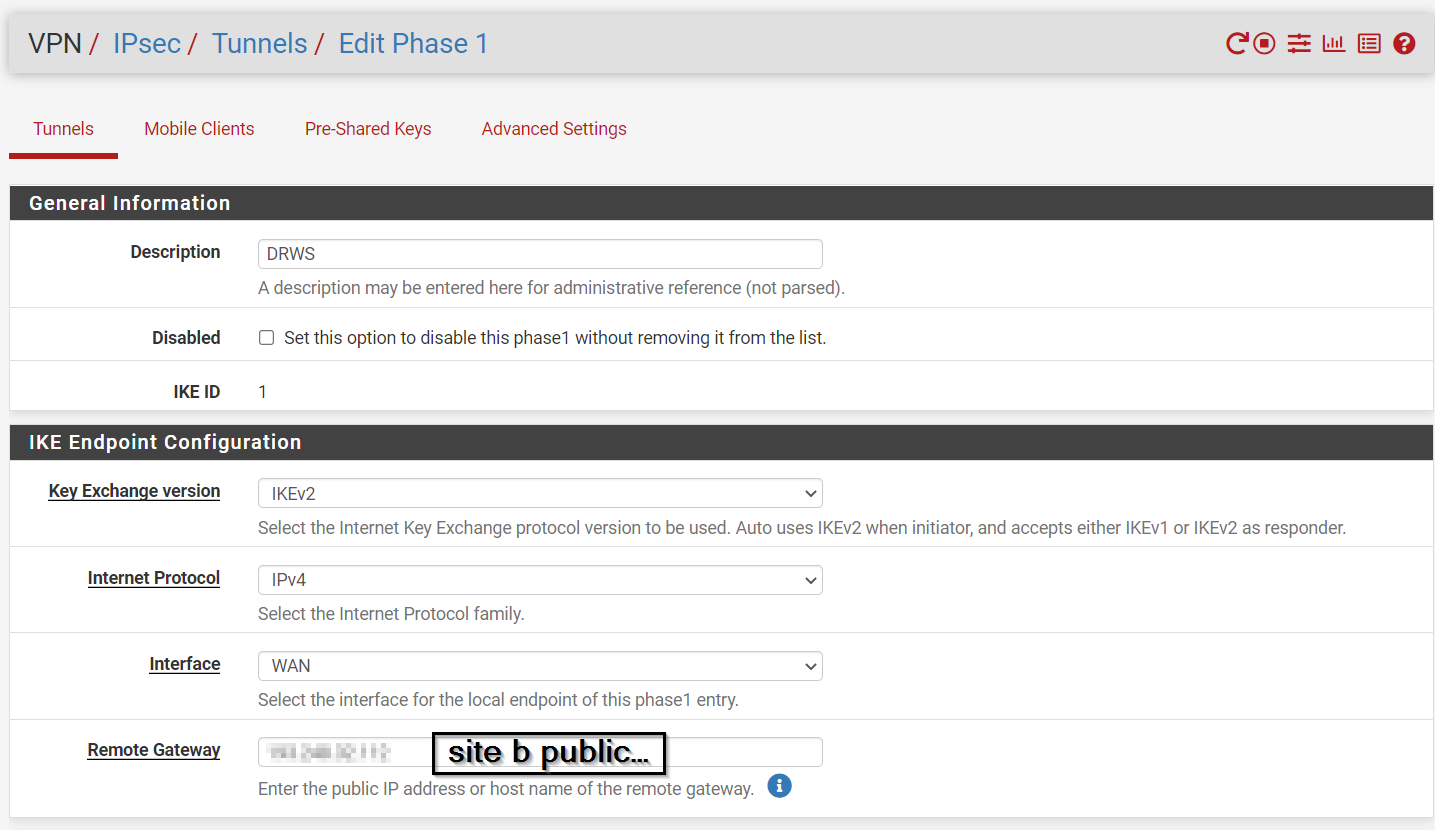
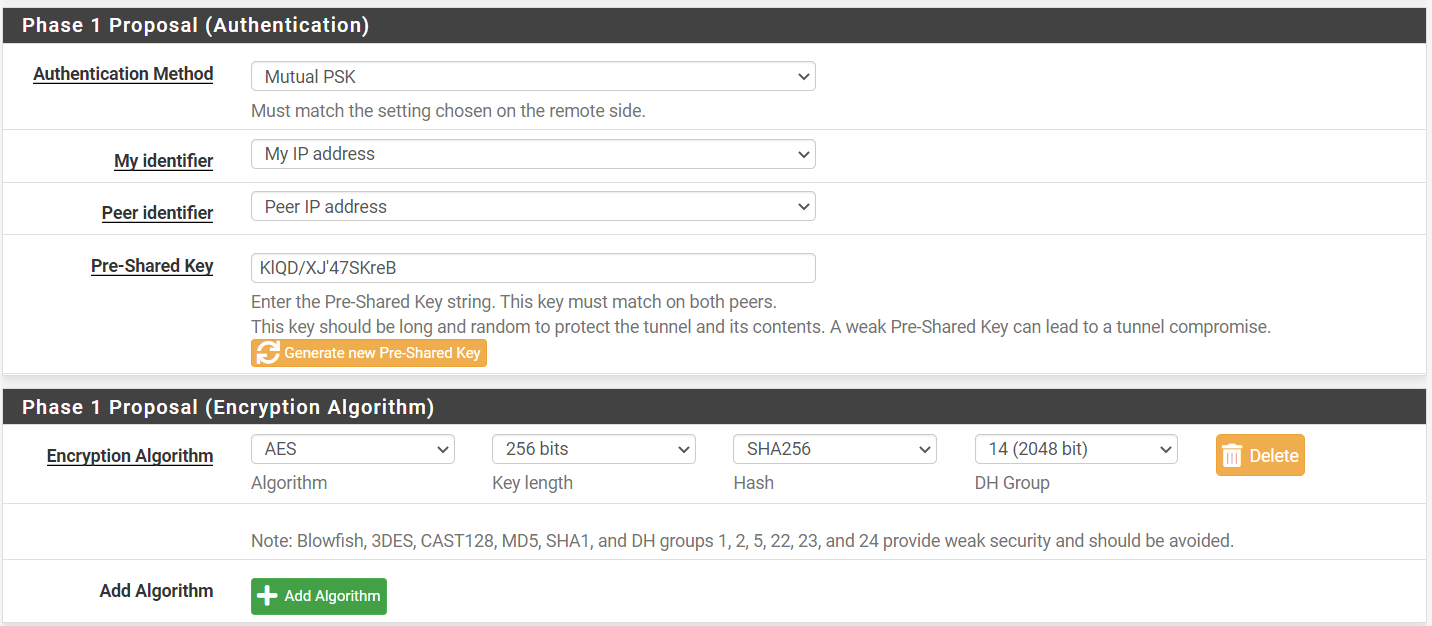
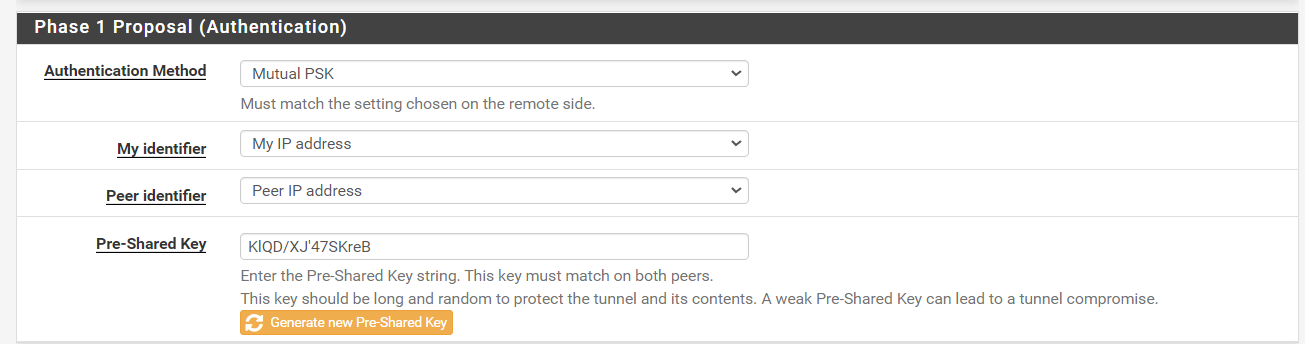
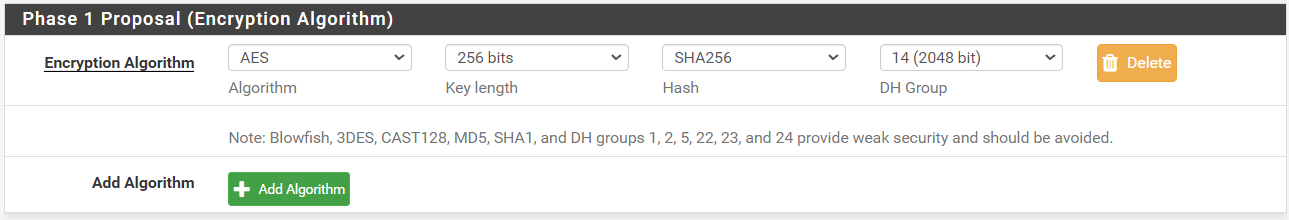
here are phase 1 and 2 configs for siteB:
Phase 1:
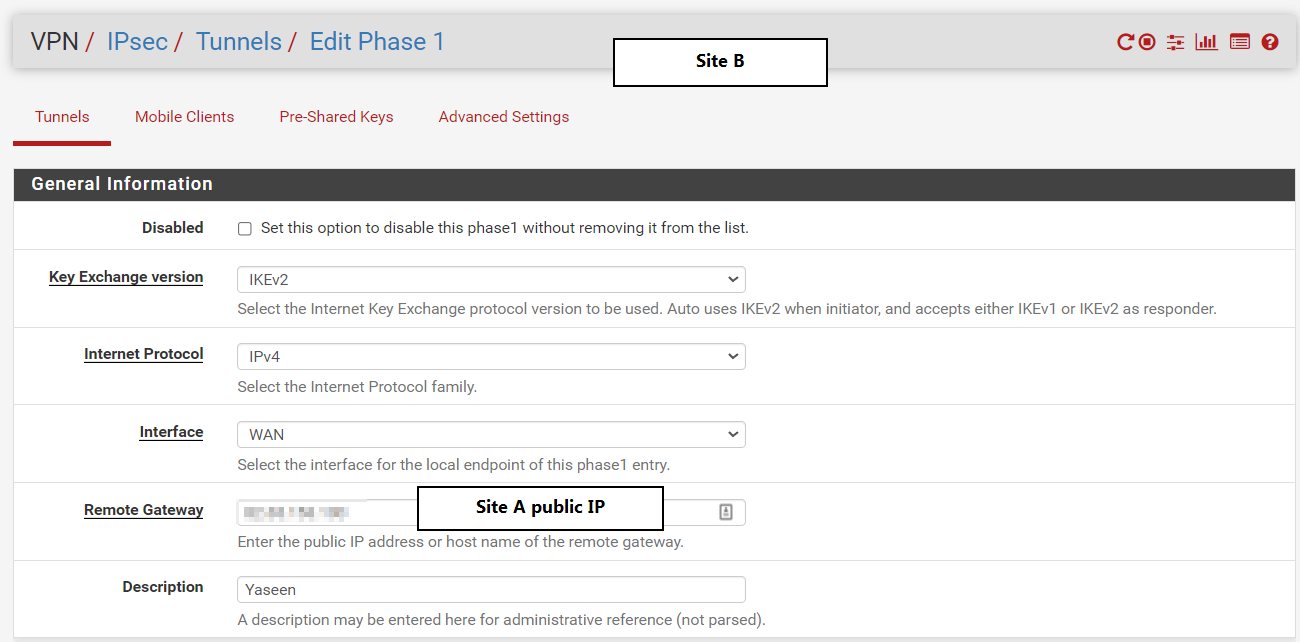
Phase 2
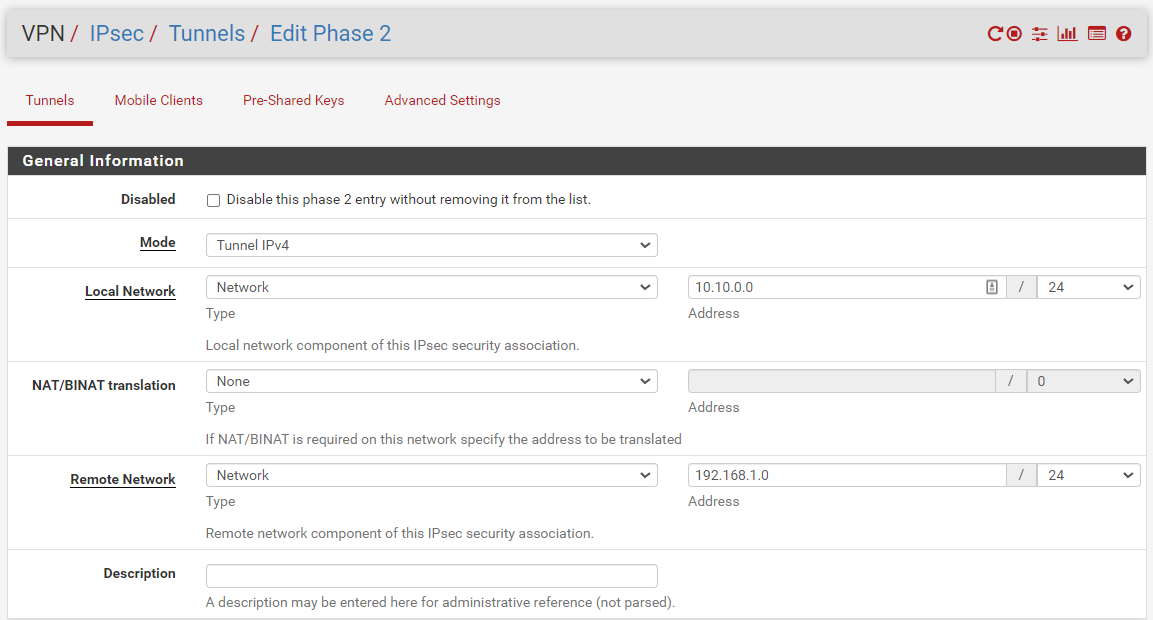
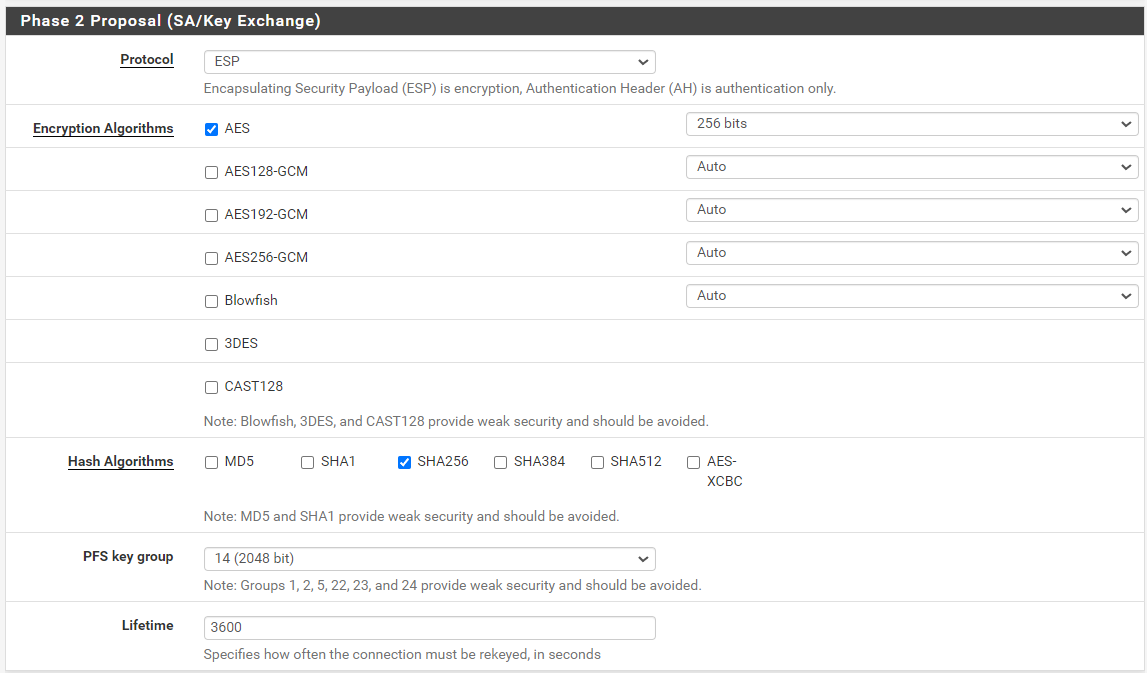
Thanks a lot for your help
-
@ibnkamala ok so one side is behind NAT if I recall right. Try this. For the “my identifier” and “peer identifier” change from IP address to KeyID tag for both. Then make the id for the local router “SideA” and the remote “SideB”. On the remote side make the my identifier “SideB” and the peer identifier “SideA”. Be sure to change the other side to use KeyID tag as well of course.
-
@gabacho4 both sides are behind the NAT
-
@ibnkamala ok. Make those changes. Also you’re positive that the routers in front of the pfsense boxes allows IPSec pass through?
-
@gabacho4 in both side routers IPsec is allowed to pass through,
Could you please tell me, what do you mean by "Then make the id for the local router “SideA” and the remote “SideB""?I really appreciate you great help
-
Also, just to emphasize, you really need to update the other side to pfsense 2.6.0. The IPSec settings and configuration between 2.4.5 and 2.6 have changed. It’s possible this will never work until you update.
-
@ibnkamala said in Ipsec Configuration not Working!:
@gabacho4 in both side routers IPsec is allowed to pass through,
Could you please tell me, what do you mean by "Then make the id for the local router “SideA” and the remote “SideB""?I really appreciate you great help
Under:
Phase 1 Proposal (Authentication) - change My Identifier to KeyID tag from My IP Address. Also change the Peer identifier to KeyID. Make My identifier KeyID tag value SiteA and peer identifier KeyID tag value SiteB. Then do the same thing on the other router except the My identifier will be SiteB and the peer will be SiteA
-
@gabacho4 is this correct?
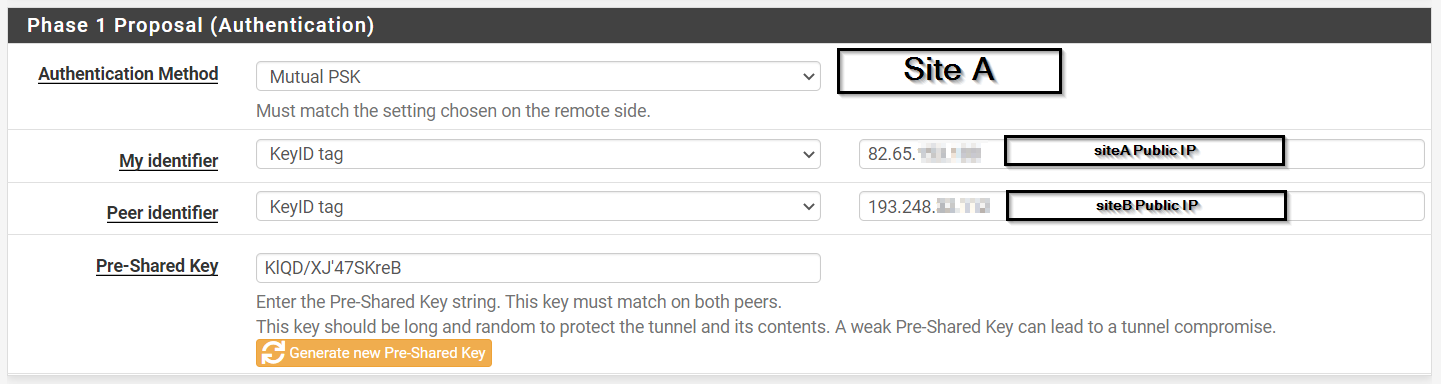
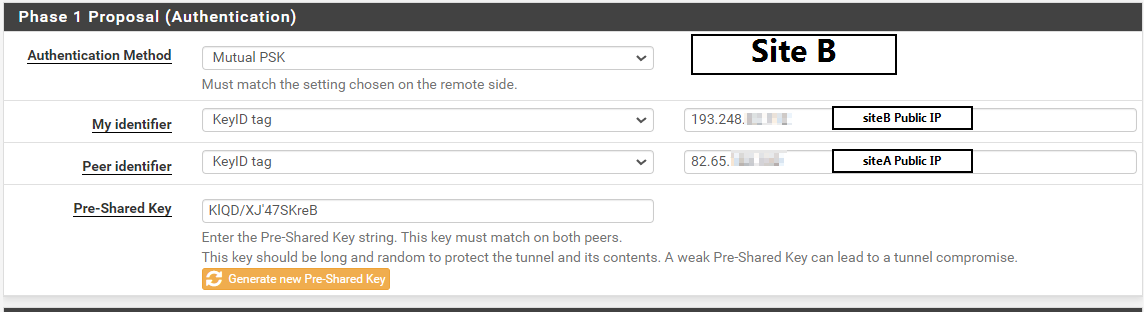
-
@ibnkamala almost. Don't use the public IP. Literally just put SiteA and SiteB on the local machine and SiteB and SiteA on the remote one.
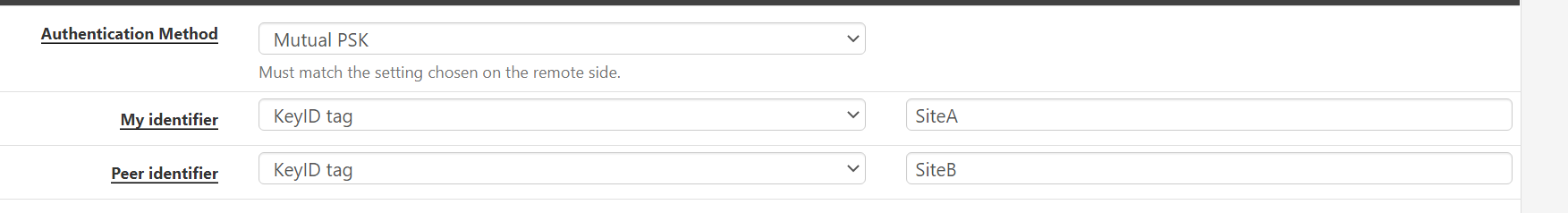
-
@gabacho4 still not working,
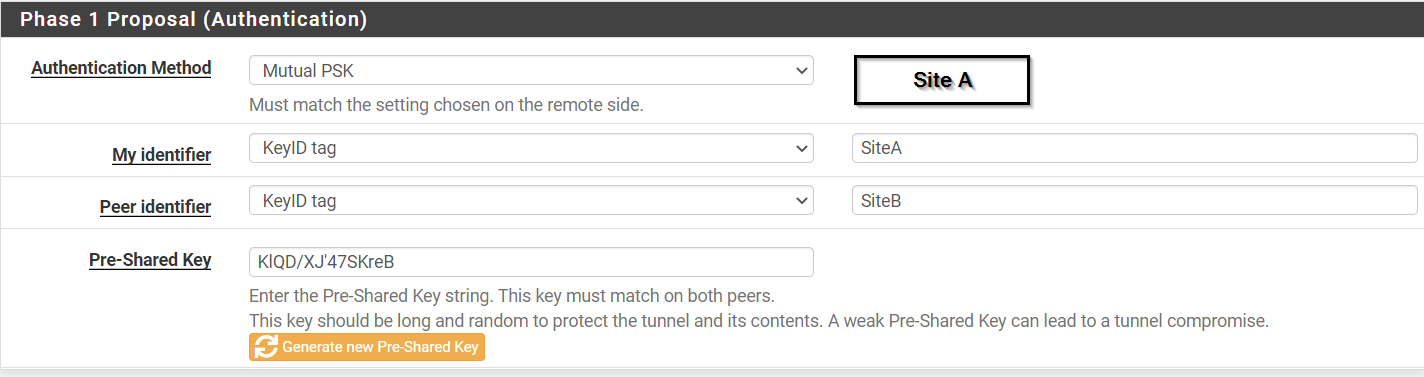
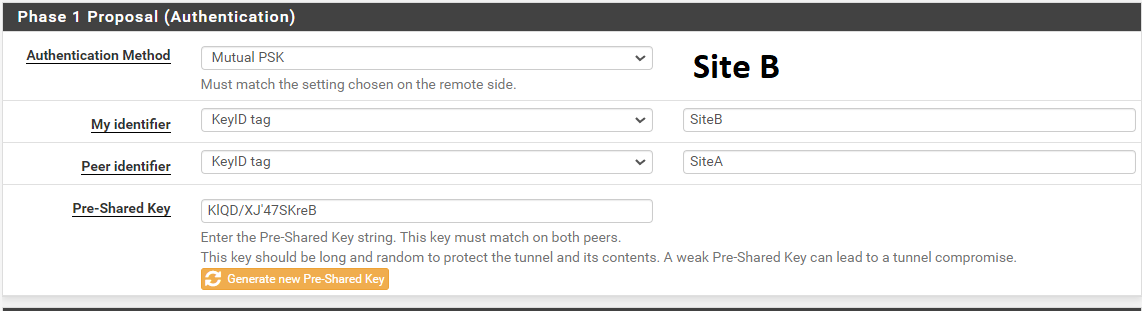
For more information I am already having a tunnel active on Pfsense 2.4.5 as we can see in the below photo!
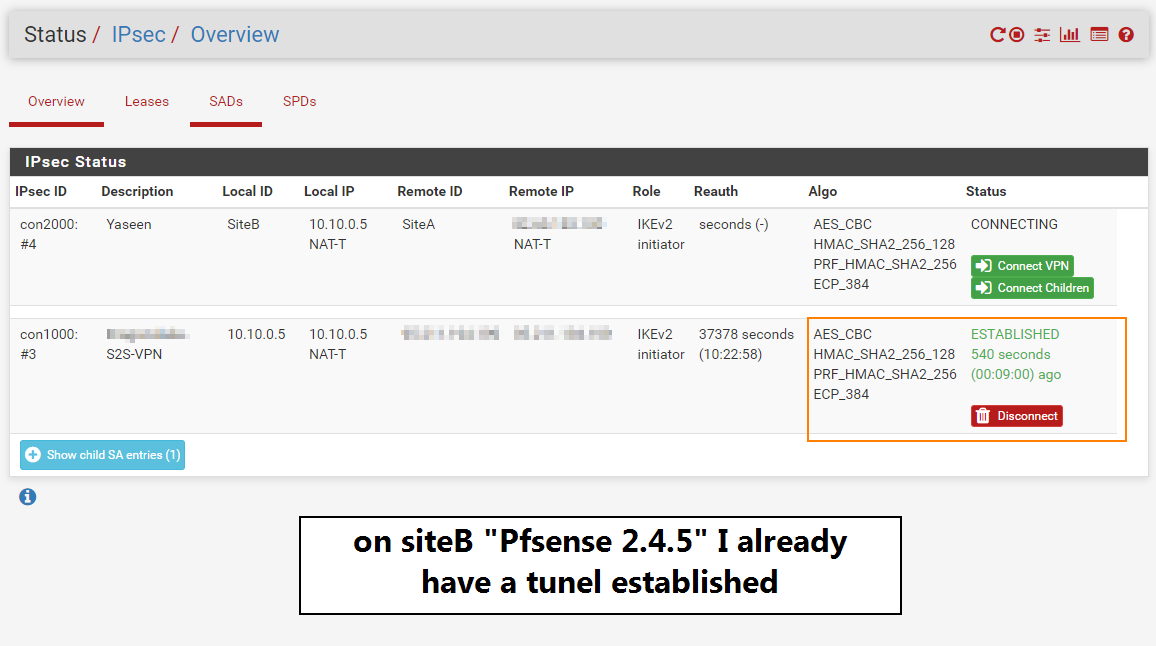
-
@ibnkamala can you disable the other ipsec connection and see if the one we're working on comes up? What version of PfSense is the S2S-VPN device running?
Also would like to see the ipsec logs for both sides. You can get them at Status - System Logs - then click on IPsec.