Ipsec Configuration not Working!
-
-
@ibnkamala you’re killing me bro. And what about side B?! I need both sides to compare. Come on.
-
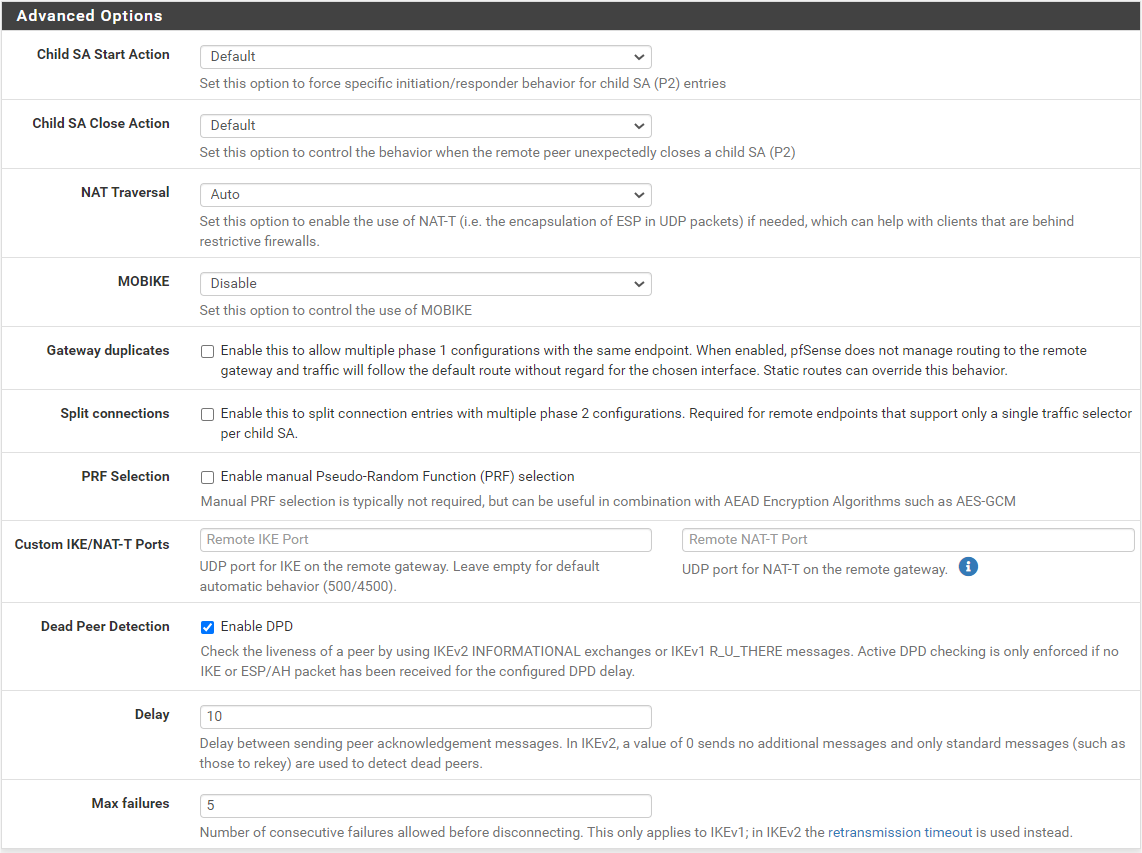
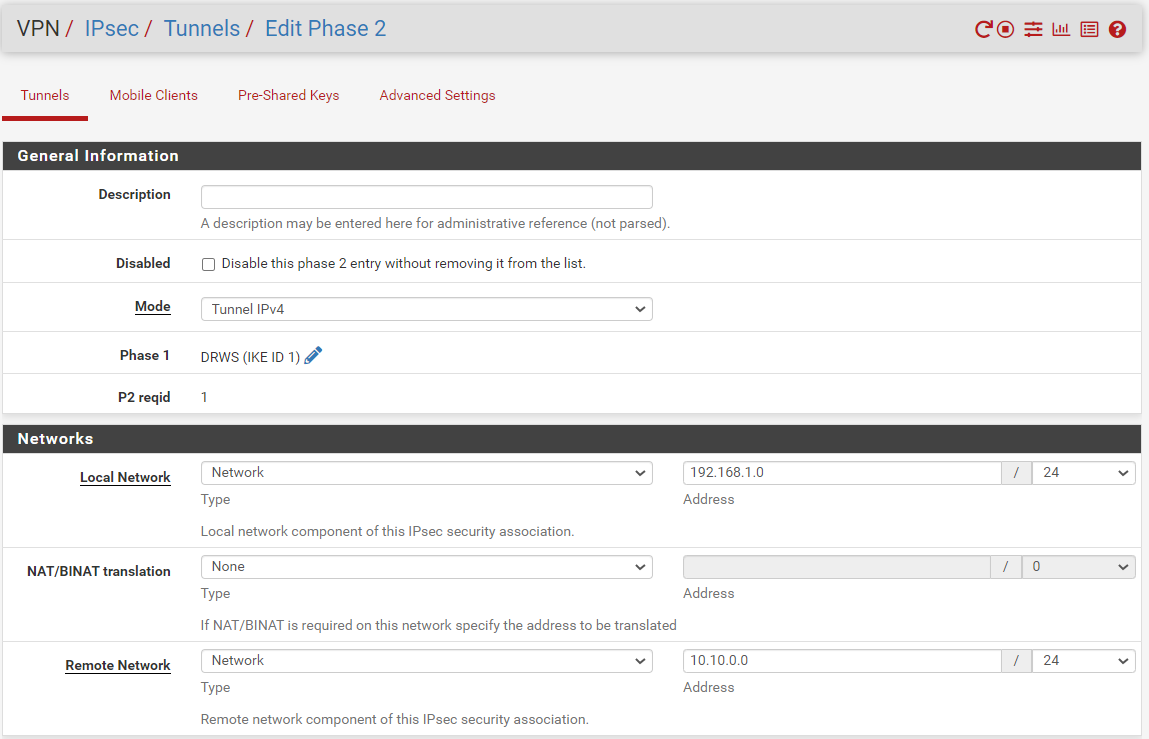
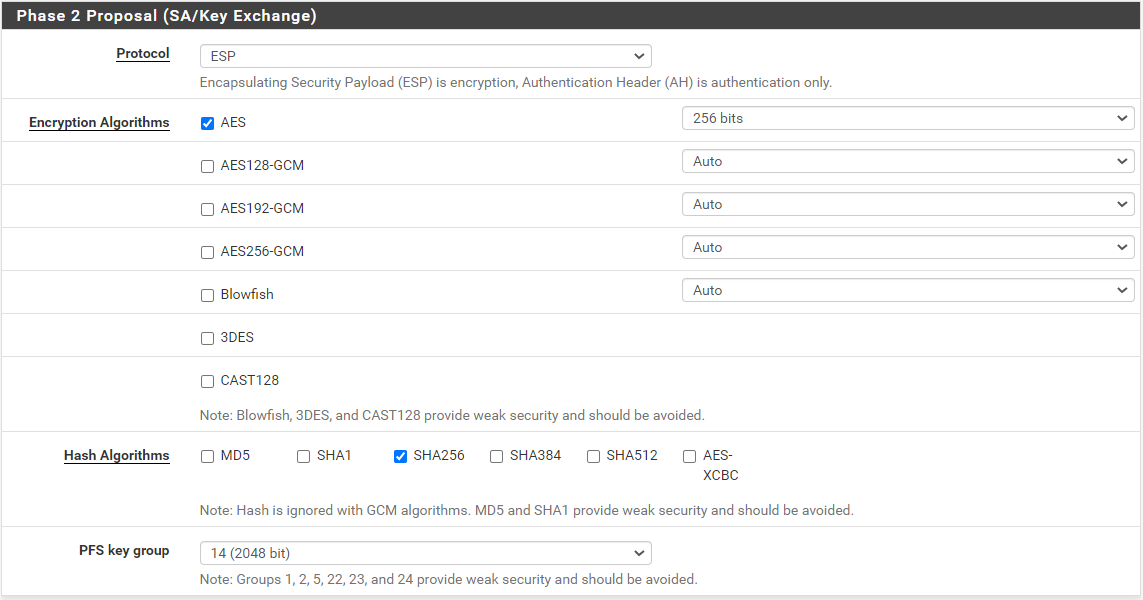
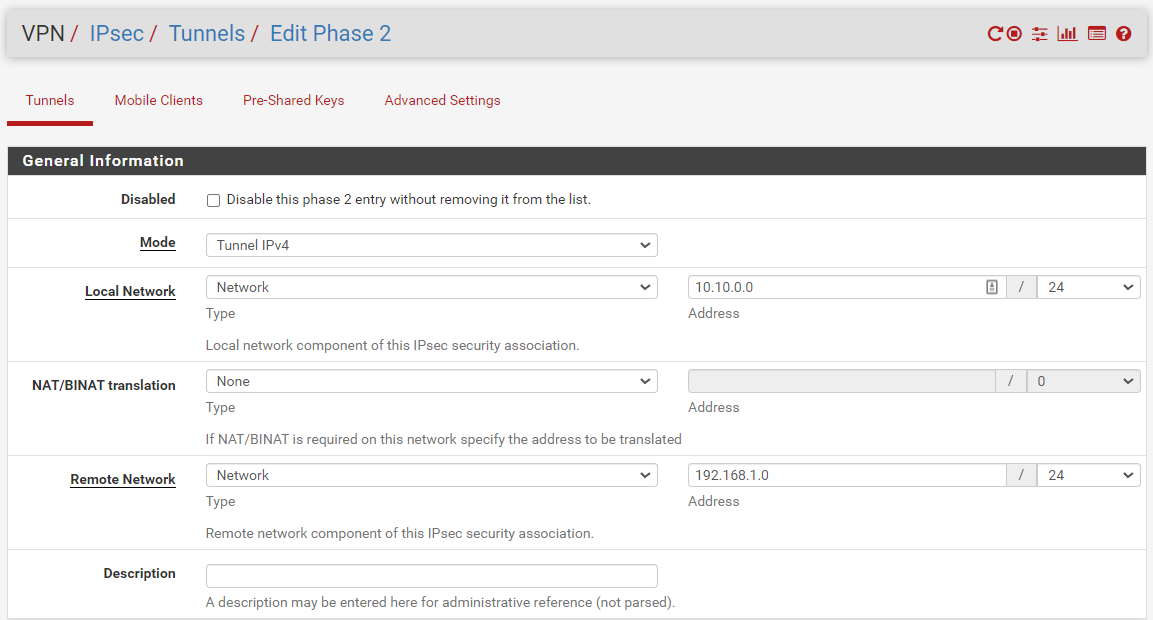
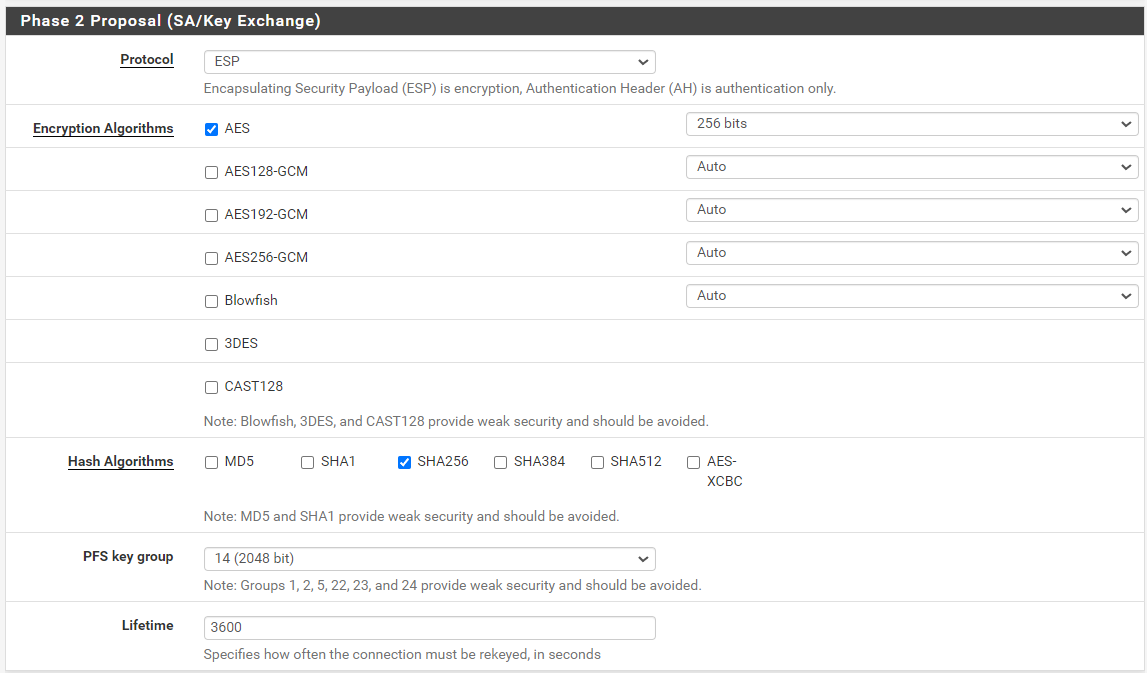
here are phase 1 and 2 configs for siteB:
Phase 1:
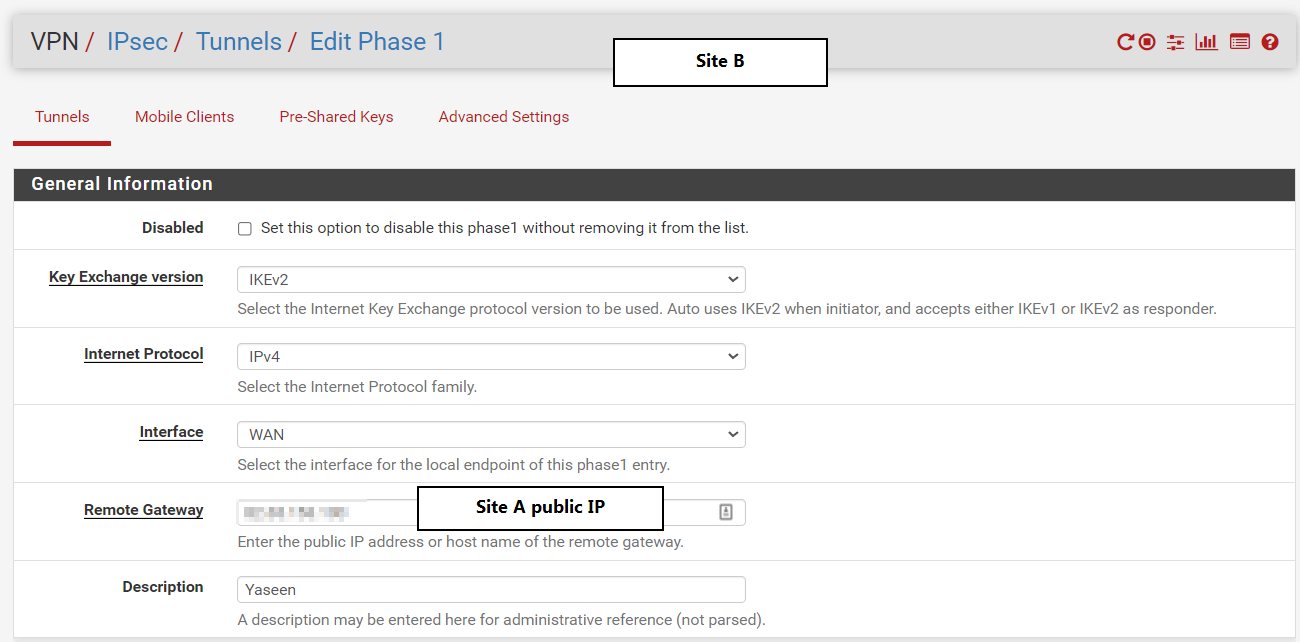
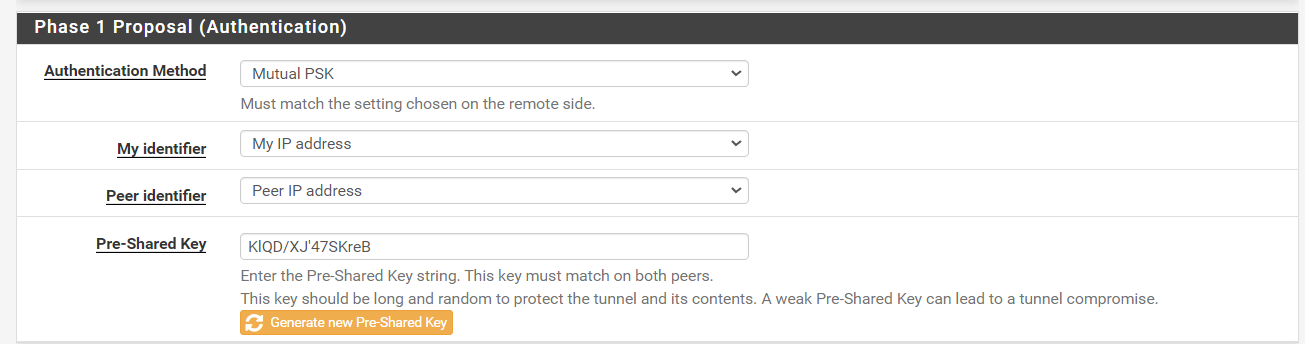
Phase 2
Thanks a lot for your help
-
@ibnkamala ok so one side is behind NAT if I recall right. Try this. For the “my identifier” and “peer identifier” change from IP address to KeyID tag for both. Then make the id for the local router “SideA” and the remote “SideB”. On the remote side make the my identifier “SideB” and the peer identifier “SideA”. Be sure to change the other side to use KeyID tag as well of course.
-
@gabacho4 both sides are behind the NAT
-
@ibnkamala ok. Make those changes. Also you’re positive that the routers in front of the pfsense boxes allows IPSec pass through?
-
@gabacho4 in both side routers IPsec is allowed to pass through,
Could you please tell me, what do you mean by "Then make the id for the local router “SideA” and the remote “SideB""?I really appreciate you great help
-
Also, just to emphasize, you really need to update the other side to pfsense 2.6.0. The IPSec settings and configuration between 2.4.5 and 2.6 have changed. It’s possible this will never work until you update.
-
@ibnkamala said in Ipsec Configuration not Working!:
@gabacho4 in both side routers IPsec is allowed to pass through,
Could you please tell me, what do you mean by "Then make the id for the local router “SideA” and the remote “SideB""?I really appreciate you great help
Under:
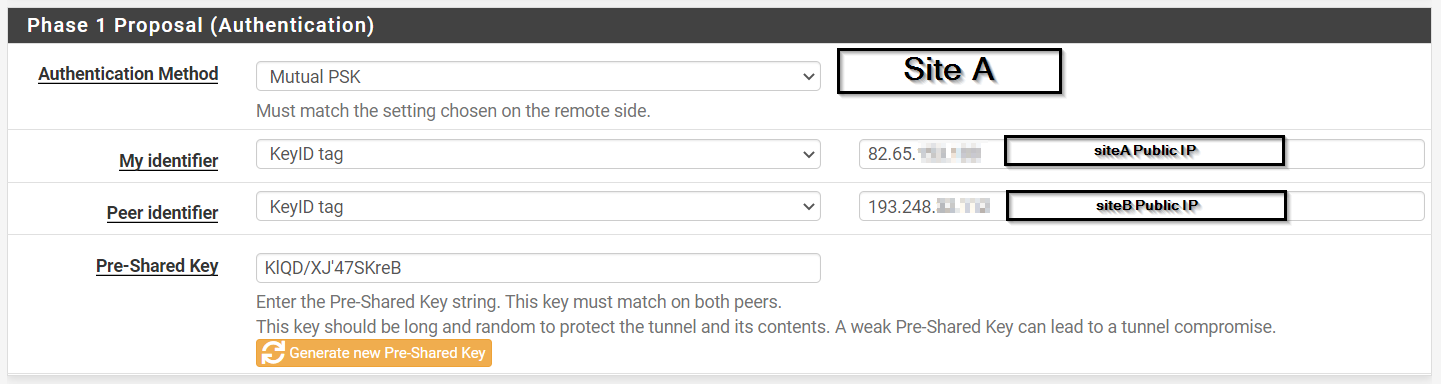
Phase 1 Proposal (Authentication) - change My Identifier to KeyID tag from My IP Address. Also change the Peer identifier to KeyID. Make My identifier KeyID tag value SiteA and peer identifier KeyID tag value SiteB. Then do the same thing on the other router except the My identifier will be SiteB and the peer will be SiteA
-
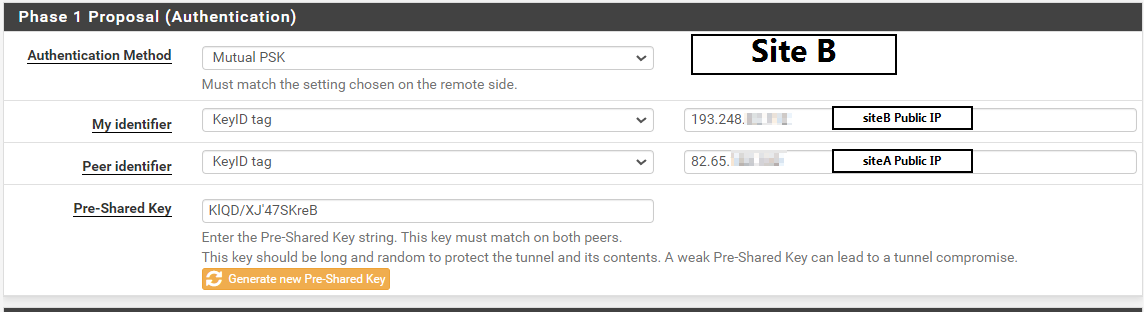
@gabacho4 is this correct?
-
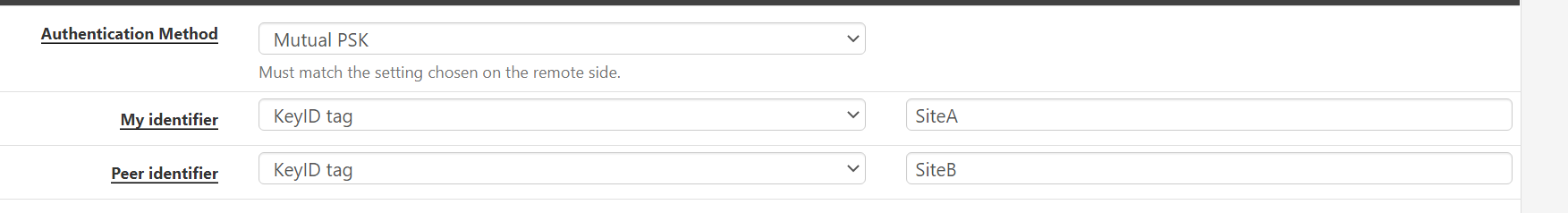
@ibnkamala almost. Don't use the public IP. Literally just put SiteA and SiteB on the local machine and SiteB and SiteA on the remote one.
-
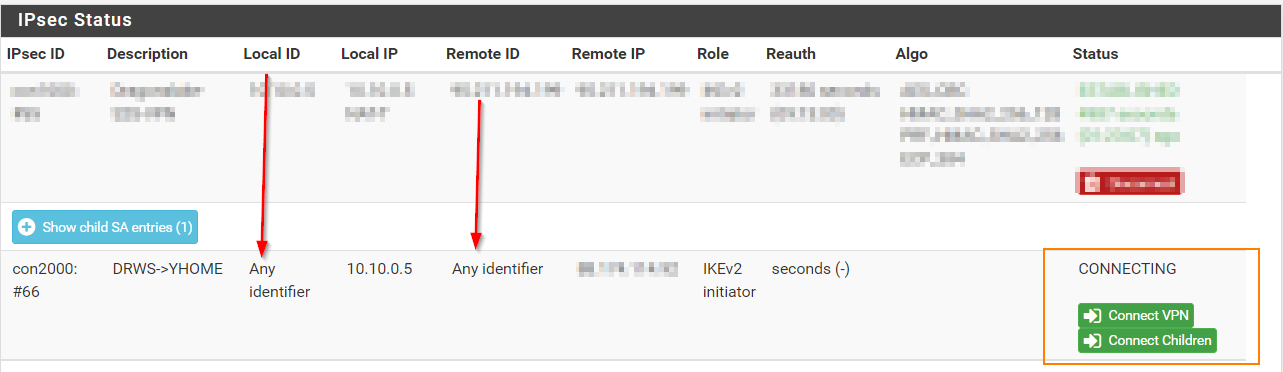
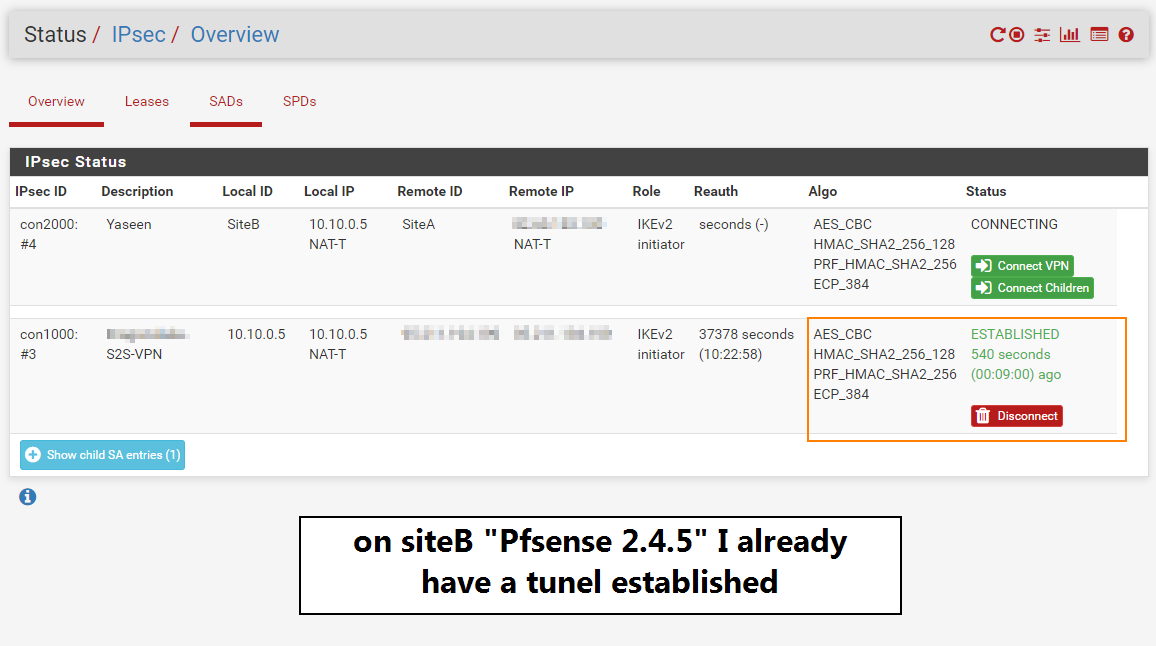
@gabacho4 still not working,
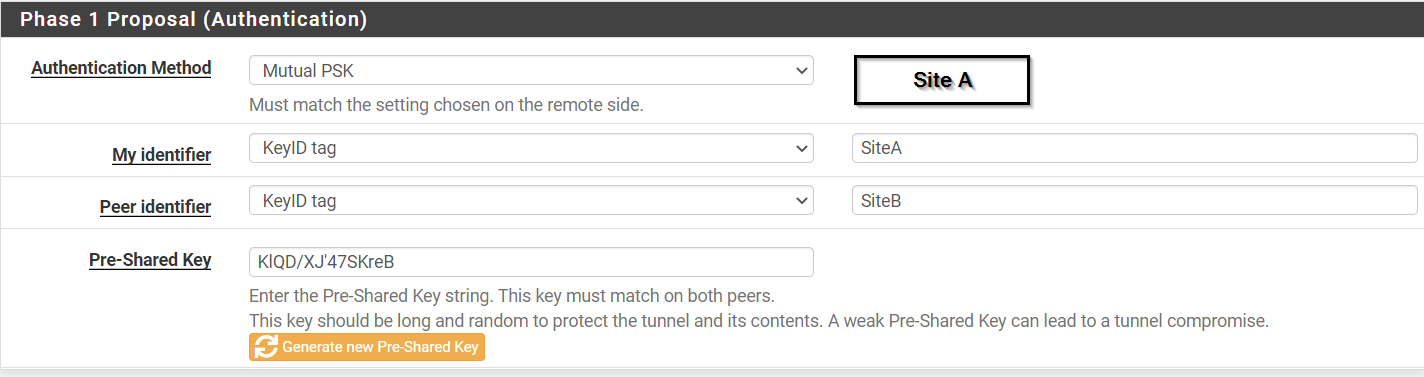
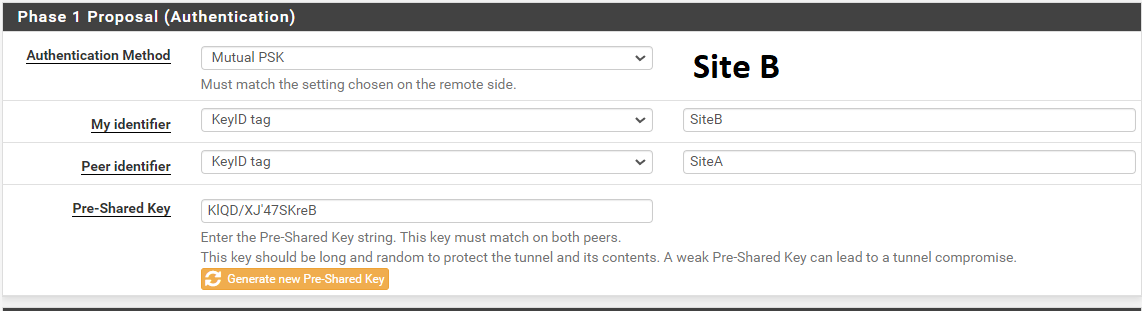
For more information I am already having a tunnel active on Pfsense 2.4.5 as we can see in the below photo!
-
@ibnkamala can you disable the other ipsec connection and see if the one we're working on comes up? What version of PfSense is the S2S-VPN device running?
Also would like to see the ipsec logs for both sides. You can get them at Status - System Logs - then click on IPsec.
-
@gabacho4 I have disabled the other connection however no change, I really don't know what our partner uses in the other side of the tunnel but I know they are in Ukraine.
Here are logs for both sites:
SiteA Logs
Last 500 IPsec Log Entries. (Maximum 500)
Time Process PID Message
Jun 11 12:17:38 charon 69927 10[CFG] <con1|17> sending supported signature hash algorithms: sha256 sha384 sha512 identity
Jun 11 12:17:38 charon 69927 10[ENC] <con1|17> generating IKE_SA_INIT request 0 [ SA KE No N(NATD_S_IP) N(NATD_D_IP) N(FRAG_SUP) N(HASH_ALG) N(REDIR_SUP) ]
Jun 11 12:17:38 charon 69927 10[NET] <con1|17> sending packet: from 192.168.1.27[500] to SiteB[500] (304 bytes)
Jun 11 12:17:41 charon 69927 14[CFG] vici client 213 connected
Jun 11 12:17:41 charon 69927 14[CFG] vici client 213 registered for: list-sa
Jun 11 12:17:41 charon 69927 15[CFG] vici client 213 requests: list-sas
Jun 11 12:17:41 charon 69927 08[CFG] vici client 213 disconnected
Jun 11 12:17:42 charon 69927 15[IKE] <con1|17> retransmit 1 of request with message ID 0
Jun 11 12:17:42 charon 69927 15[NET] <con1|17> sending packet: from 192.168.1.27[500] to SiteB[500] (304 bytes)
Jun 11 12:17:43 charon 69927 14[CFG] vici client 212 disconnected
Jun 11 12:17:46 charon 69927 13[CFG] vici client 214 connected
Jun 11 12:17:46 charon 69927 16[CFG] vici client 214 registered for: list-sa
Jun 11 12:17:46 charon 69927 16[CFG] vici client 214 requests: list-sas
Jun 11 12:17:46 charon 69927 14[CFG] vici client 214 disconnected
Jun 11 12:17:46 charon 69927 13[JOB] <16> deleting half open IKE_SA with SiteB after timeout
Jun 11 12:17:46 charon 69927 13[IKE] <16> IKE_SA (unnamed)[16] state change: CONNECTING => DESTROYING
Jun 11 12:17:50 charon 69927 14[IKE] <con1|17> retransmit 2 of request with message ID 0
Jun 11 12:17:50 charon 69927 14[NET] <con1|17> sending packet: from 192.168.1.27[500] to SiteB[500] (304 bytes)
Jun 11 12:17:51 charon 69927 14[CFG] vici client 215 connected
Jun 11 12:17:51 charon 69927 11[CFG] vici client 215 registered for: list-sa
Jun 11 12:17:51 charon 69927 11[CFG] vici client 215 requests: list-sas
Jun 11 12:17:51 charon 69927 05[CFG] vici client 215 disconnected
Jun 11 12:17:56 charon 69927 06[CFG] vici client 216 connected
Jun 11 12:17:56 charon 69927 12[CFG] vici client 216 registered for: list-sa
Jun 11 12:17:56 charon 69927 12[CFG] vici client 216 requests: list-sas
Jun 11 12:17:56 charon 69927 06[CFG] vici client 216 disconnected
Jun 11 12:18:01 charon 69927 14[CFG] vici client 217 connected
Jun 11 12:18:01 charon 69927 12[CFG] vici client 217 registered for: list-sa
Jun 11 12:18:01 charon 69927 07[CFG] vici client 217 requests: list-sas
Jun 11 12:18:01 charon 69927 14[CFG] vici client 217 disconnected
Jun 11 12:18:03 charon 69927 07[IKE] <con1|17> retransmit 3 of request with message ID 0
Jun 11 12:18:03 charon 69927 07[NET] <con1|17> sending packet: from 192.168.1.27[500] to SiteB[500] (304 bytes)
Jun 11 12:18:06 charon 69927 09[CFG] vici client 218 connected
Jun 11 12:18:06 charon 69927 07[CFG] vici client 218 registered for: list-sa
Jun 11 12:18:06 charon 69927 07[CFG] vici client 218 requests: list-sas
Jun 11 12:18:06 charon 69927 07[CFG] vici client 218 disconnected
Jun 11 12:18:11 charon 69927 08[CFG] vici client 219 connected
Jun 11 12:18:11 charon 69927 10[CFG] vici client 219 registered for: list-sa
Jun 11 12:18:11 charon 69927 15[CFG] vici client 219 requests: list-sas
Jun 11 12:18:11 charon 69927 08[CFG] vici client 219 disconnected
Jun 11 12:18:16 charon 69927 16[CFG] vici client 220 connected
Jun 11 12:18:16 charon 69927 16[CFG] vici client 220 registered for: list-sa
Jun 11 12:18:16 charon 69927 10[CFG] vici client 220 requests: list-sas
Jun 11 12:18:16 charon 69927 16[CFG] vici client 220 disconnected
Jun 11 12:18:21 charon 69927 10[CFG] vici client 221 connected
Jun 11 12:18:21 charon 69927 10[CFG] vici client 221 registered for: list-sa
Jun 11 12:18:21 charon 69927 05[CFG] vici client 221 requests: list-sas
Jun 11 12:18:21 charon 69927 10[CFG] vici client 221 disconnected
Jun 11 12:18:26 charon 69927 11[CFG] vici client 222 connected
Jun 11 12:18:26 charon 69927 11[CFG] vici client 222 registered for: list-saSiteB Logs
Last 50 IPsec Log Entries. (Maximum 50)
Time Process PID Message
Jun 11 15:35:14 charon 05[CFG] ignoring acquire, connection attempt pending
Jun 11 15:35:14 charon 08[KNL] creating acquire job for policy 10.10.0.5/32|/0 === SiteA/32|/0 with reqid {1}
Jun 11 15:35:08 charon 08[CFG] ignoring acquire, connection attempt pending
Jun 11 15:35:08 charon 05[KNL] creating acquire job for policy 10.10.0.5/32|/0 === SiteA/32|/0 with reqid {1}
Jun 11 15:35:07 charon 07[NET] <con2000|1> sending packet: from 10.10.0.5[4500] to SiteA[4500] (272 bytes)
Jun 11 15:35:07 charon 07[IKE] <con2000|1> retransmit 3 of request with message ID 1
Jun 11 15:35:01 charon 07[CFG] ignoring acquire, connection attempt pending
Jun 11 15:35:01 charon 05[KNL] creating acquire job for policy 10.10.0.5/32|/0 === SiteA/32|/0 with reqid {1}
Jun 11 15:34:55 charon 06[CFG] ignoring acquire, connection attempt pending
Jun 11 15:34:55 charon 05[KNL] creating acquire job for policy 10.10.0.5/32|/0 === SiteA/32|/0 with reqid {1}
Jun 11 15:34:54 charon 11[CFG] vici client 1 disconnected
Jun 11 15:34:54 charon 11[CFG] vici client 1 requests: list-sas
Jun 11 15:34:54 charon 11[CFG] vici client 1 registered for: list-sa
Jun 11 15:34:54 charon 11[CFG] vici client 1 connected
Jun 11 15:34:54 charon 11[NET] <con2000|1> sending packet: from 10.10.0.5[4500] to SiteA[4500] (272 bytes)
Jun 11 15:34:54 charon 11[IKE] <con2000|1> retransmit 2 of request with message ID 1
Jun 11 15:34:49 charon 13[CFG] ignoring acquire, connection attempt pending
Jun 11 15:34:49 charon 13[KNL] creating acquire job for policy 10.10.0.5/32|/0 === SiteA/32|/0 with reqid {1}
Jun 11 15:34:46 charon 13[NET] <con2000|1> sending packet: from 10.10.0.5[4500] to SiteA[4500] (272 bytes)
Jun 11 15:34:46 charon 13[IKE] <con2000|1> retransmit 1 of request with message ID 1
Jun 11 15:34:42 charon 15[NET] <con2000|1> sending packet: from 10.10.0.5[4500] to SiteA[4500] (272 bytes)
Jun 11 15:34:42 charon 15[ENC] <con2000|1> generating IKE_AUTH request 1 [ IDi N(INIT_CONTACT) IDr AUTH N(ESP_TFC_PAD_N) SA TSi TSr N(MULT_AUTH) N(EAP_ONLY) N(MSG_ID_SYN_SUP) ]
Jun 11 15:34:42 charon 15[IKE] <con2000|1> establishing CHILD_SA con2000{2} reqid 1
Jun 11 15:34:42 charon 15[CFG] <con2000|1> configured proposals: ESP:AES_CBC_256/HMAC_SHA2_256_128/NO_EXT_SEQ
Jun 11 15:34:42 charon 15[CFG] <con2000|1> 192.168.1.0/24|/0
Jun 11 15:34:42 charon 15[CFG] <con2000|1> proposing traffic selectors for other:
Jun 11 15:34:42 charon 15[CFG] <con2000|1> 10.10.0.0/24|/0
Jun 11 15:34:42 charon 15[CFG] <con2000|1> proposing traffic selectors for us:
Jun 11 15:34:42 charon 15[IKE] <con2000|1> successfully created shared key MAC
Jun 11 15:34:42 charon 15[IKE] <con2000|1> authentication of 'SiteB' (myself) with pre-shared key
Jun 11 15:34:42 charon 15[IKE] <con2000|1> IKE_AUTH task
Jun 11 15:34:42 charon 15[IKE] <con2000|1> IKE_CERT_PRE task
Jun 11 15:34:42 charon 15[IKE] <con2000|1> reinitiating already active tasks
Jun 11 15:34:42 charon 15[IKE] <con2000|1> remote host is behind NAT
Jun 11 15:34:42 charon 15[IKE] <con2000|1> local host is behind NAT, sending keep alives
Jun 11 15:34:42 charon 15[CFG] <con2000|1> received supported signature hash algorithms: sha256 sha384 sha512 identity
Jun 11 15:34:42 charon 15[CFG] <con2000|1> selected proposal: IKE:AES_CBC_128/HMAC_SHA2_256_128/PRF_HMAC_SHA2_256/ECP_384
Jun 11 15:34:42 charon 15[CFG] <con2000|1> configured proposals: IKE:AES_CBC_128/HMAC_SHA2_256_128/PRF_HMAC_SHA2_256/ECP_384
Jun 11 15:34:42 charon 15[CFG] <con2000|1> received proposals: IKE:AES_CBC_128/HMAC_SHA2_256_128/PRF_HMAC_SHA2_256/ECP_384
Jun 11 15:34:42 charon 15[CFG] <con2000|1> proposal matches
Jun 11 15:34:42 charon 15[CFG] <con2000|1> selecting proposal:
Jun 11 15:34:42 charon 15[IKE] <con2000|1> received CHILDLESS_IKEV2_SUPPORTED notify
Jun 11 15:34:42 charon 15[IKE] <con2000|1> received SIGNATURE_HASH_ALGORITHMS notify
Jun 11 15:34:42 charon 15[IKE] <con2000|1> received FRAGMENTATION_SUPPORTED notify
Jun 11 15:34:42 charon 15[ENC] <con2000|1> parsed IKE_SA_INIT response 0 [ SA KE No N(NATD_S_IP) N(NATD_D_IP) N(FRAG_SUP) N(HASH_ALG) N(CHDLESS_SUP) N(MULT_AUTH) ]
Jun 11 15:34:42 charon 15[NET] <con2000|1> received packet: from SiteA[500] to 10.10.0.5[500] (312 bytes)
Jun 11 15:34:42 charon 15[NET] <con2000|1> sending packet: from 10.10.0.5[500] to SiteA[500] (304 bytes)
Jun 11 15:34:42 charon 15[ENC] <con2000|1> generating IKE_SA_INIT request 0 [ SA KE No N(NATD_S_IP) N(NATD_D_IP) N(FRAG_SUP) N(HASH_ALG) N(REDIR_SUP) ]
Jun 11 15:34:42 charon 15[CFG] <con2000|1> sending supported signature hash algorithms: sha256 sha384 sha512 identity
Jun 11 15:34:42 charon 15[CFG] <con2000|1> configured proposals: IKE:AES_CBC_128/HMAC_SHA2_256_128/PRF_HMAC_SHA2_256/ECP_384 -
@ibnkamala so, the logs should match up. I understand that site A and site B might be in different places geographically and thus the logs will show a different hour, but the minutes:seconds should match. Really can't follow the connection activities when you've given me logs with timestamps that are like 15 minutes apart.
-
@ibnkamala also, have you created firewall rules on the ipsec tab on both site? Preferably just a simple allow any protocol from any source to any destination rule?
-
@gabacho4 Yes, Any to Any rule is applied on both sites within IPsec interface
-
@ibnkamala OK so now is about the point at which I say, update the 2.4.5 box to 2.6 before we can do any more troubleshooting. I don't want to spend any more time trying to force this and hope that both versions are speaking the same ipsec language. Please update and then let us know where things stand.
-
@gabacho4 I wanted to post you the logs while time is matched but couldn't it says it's a SPAM. I don't know if there is a way to upload them as a PDF?
but Monday I will update 2.4.5 to 2.6 and for sure will update you of the outcome
-
@gabacho4 SiteA and SiteB Logs.zip
Here are the logs if you have some time please let me know if you get something from !