Issues with IPV6
-
Related to your question: "Is there any noticeable pattern to when the disruptions occur, e.g. time of day, hours between occurrence? Are there any DHCP/DHCP6 logs in the time leading up to a disruption?"
I do not know, to analyze that I have to download the logs and analyze the them offline. I will consider that option.Related to the ARP messages, perhaps it is related to Synching firewall event. See below. There seems to be an relation. I have no idea to which device the mac-address belongs. I also wonder why there is the word "bogon".
Aug 23 21:59:58 pfSense arpwatch[58415]: bogon 0.0.0.0 7c:b0:c2:f2:df:55
Aug 23 21:59:57 pfSense arpwatch[58415]: bogon 0.0.0.0 7c:b0:c2:f2:df:55
Aug 23 10:55:00 pfSense sshguard[22416]: Now monitoring attacks.
Aug 23 10:55:00 pfSense sshguard[73281]: Exiting on signal.
Aug 23 10:53:29 pfSense check_reload_status[481]: Syncing firewallRelated to leases. I have one fixed IPV4 address and an /48 IPV6-range. So I will constantly have the same addresses.
The Zyxel switch is my 1G-main/central switch. Related to this, it is used to separate and forward vlans from the Fiber access point to pfSense. As example originally I did forward the internet vlan (vlan6) to pfsense but not the TV-vlan (vlan4).
-
@louis2 said in Issues with IPV6:
Related to the ARP messages, perhaps it is related to Synching firewall event. See below. There seems to be an relation. I have no idea to which device the mac-address belongs. I also wonder why there is the word "bogon".
For info Arpwatch reports bogons frequently
From what I make of it : DHCP clients broadcast intially with a 0.0.0.0.0.0 MAC to trigger a DHCP server reply.
The Arpwatch 'scanner' will detect this, and add a bogon line, as he knows that 0.0.0.0.0.0 is actually known as for example aa.bb.cc.dd.ee.ff.
The bogon messages are nearly always inoffensive. -
This morning I noticed that the IPV6-gateway was gone again
 Stopping and starting the wan does ^fix^ the problem, but of course that is not OK.
Stopping and starting the wan does ^fix^ the problem, but of course that is not OK.Since previous time this happened, I did setup a syslog server (graylog) in order to fetch all potential related alarms.
In the logging I found three messages which draw my attention. when filtering the log using message ^like "ppp"^
<12>1 2022-09-09T04:12:53.468066+02:00 pfSense.lan dpinger 76225 - - WAN_DHCP6 fe80::9217:3fff:fe7f:e4a1%pppoe1: Alarm latency 3558us stddev 4502us loss 22%
Using the time as new selection criteria I selected the alarms occurring around this time. Starting and ending with an alarm which IMHO is not related. Here they are:
<134>1 2022-09-09T04:12:35.879325+02:00 pfSense.lan filterlog 72340 - - 1316,,,1559467905,lagg0.13,match,pass,in,4,0x0,,1,64738,0,none,103,pim,46,192.168.13.1,224.0.0.13,datalength=26
<12>1 2022-09-09T04:12:53.468066+02:00 pfSense.lan dpinger 76225 - - WAN_DHCP6 fe80::9217:3fff:fe7f:e4a1%pppoe1: Alarm latency 3558us stddev 4502us loss 22%
<30>1 2022-09-09T04:12:53.474315+02:00 pfSense.lan rc.gateway_alarm 30961 - - >>> Gateway alarm: WAN_DHCP6 (Addr:fe80::9217:3fff:fe7f:e4a1%pppoe1 Alarm:1 RTT:3.558ms RTTsd:4.502ms Loss:22%)
<13>1 2022-09-09T04:12:53.474964+02:00 pfSense.lan check_reload_status 391 - - updating dyndns WAN_DHCP6
<13>1 2022-09-09T04:12:53.474990+02:00 pfSense.lan check_reload_status 391 - - Restarting OpenVPN tunnels/interfaces
<13>1 2022-09-09T04:12:53.474983+02:00 pfSense.lan check_reload_status 391 - - Restarting IPsec tunnels
<13>1 2022-09-09T04:12:53.474997+02:00 pfSense.lan check_reload_status 391 - - Reloading filter
<30>1 2022-09-09T04:12:55.499322+02:00 pfSense.lan unbound 21401 - - [21401:3] info: 2a02:a468:c48e:11::f051 printer.lan. AAAA IN
Note that I am a bit surprised to see messages related to OpenVPN as well .... since I am not using OpenVPN
-
@louis2 said in Issues with IPV6:
since I am not using OpenVPN
And neither IPSEC, right ?
When an interface event arrives, processes that use that interface are restarted.
If OpenVPN, or IPSEC are not running, then that's ok. Nothing happens.
You also saw "updating dyndns WAN_DHCP6" as it would be logical to do a DynDNS operation if the WAN_DHCP6 was used by the a Dyndns settings, the WAN IPv6 could have been changed, and the Dyndns (might) need an update.I don't know if dpinger triggers an interface event when the loss is 22 %, as 78 % of the v6 ping packets still made it back, so the IPv6 connection still working, but 'not for "100 %".
Was it slowly degrading, dpinger wioll take action : a simple IPv6 interface restart (down and up) could correct the situation. Or not .... all depends why IPv6 went down (upstream).
Your IPv6 was probably getting ok (long/some) time afterwards, but the immediate dpinger stop start on the interface didn't work out. It stays down, until far later on you restart it.My theory, of course.
-
I assume that Dyndns is related to a dynamic address, however .... I have a fixed IP{V4 address and a fixed IPV6-range.
I can imagine .... that there was a maintenance action at the provider leading (not sure at all that that is what happend), however, that the situation does not recover ...... is not ok ....
And yep simple interface restart ^fixes^ the issue ..... but that is not OK of course
-
Today the GUI again showed that the IPV6 was gone.
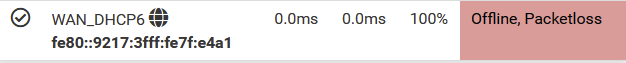
To test if the IPV6 was really gone, I did ping a couple of IPV6-addresses. And ..... I could reach them
Pinging 2a00:1450:400e:801::200e with 32 bytes of data:
Reply from 2a00:1450:400e:801::200e: time=4ms
Reply from 2a00:1450:400e:801::200e: time=4ms
Reply from 2a00:1450:400e:801::200e: time=4ms
Reply from 2a00:1450:400e:801::200e: time=4msPing statistics for 2a00:1450:400e:801::200e:
Packets: Sent = 4, Received = 4, Lost = 0 (0% loss),
Approximate round trip times in milli-seconds:
Minimum = 4ms, Maximum = 4ms, Average = 4msSo the conclusion seems to be that the gateway is available .... however that the GUI is not correctly updated ....
-
@louis2 said in Issues with IPV6:
So the conclusion seems to be that the gateway is available
It should be the gateway.
You've see many people people using (IPv4) 8.8.8.8 - ir 8.8.8.8 is not a gateway ;)Who are you pinging ?
To find out 'for sure' : use
grep ax | grep 'dpinger' and look at the command line used.
-
@gertjan said in Issues with IPV6:
grep ax | grep 'dpinger'
[2.7.0-DEVELOPMENT][admin@pfSense.lan]/root: nslookup google.com
Server: 127.0.0.1
Address: 127.0.0.1#53Non-authoritative answer:
Name: google.com
Address: 142.251.39.110
Name: google.com
Address: 2a00:1450:400e:800::200e[2.7.0-DEVELOPMENT][admin@pfSense.lan]/root: ping6 2a00:1450:400e:800::200e
PING6(56=40+8+8 bytes) 2a02:a468:c48e:1::1 --> 2a00:1450:400e:800::200e
16 bytes from 2a00:1450:400e:800::200e, icmp_seq=0 hlim=61 time=6.048 ms
16 bytes from 2a00:1450:400e:800::200e, icmp_seq=1 hlim=61 time=5.979 ms
16 bytes from 2a00:1450:400e:800::200e, icmp_seq=2 hlim=61 time=5.980 ms
16 bytes from 2a00:1450:400e:800::200e, icmp_seq=3 hlim=61 time=6.106 ms
16 bytes from 2a00:1450:400e:800::200e, icmp_seq=4 hlim=61 time=5.989 ms
16 bytes from 2a00:1450:400e:800::200e, icmp_seq=5 hlim=61 time=6.030 ms
16 bytes from 2a00:1450:400e:800::200e, icmp_seq=6 hlim=61 time=6.032 ms
16 bytes from 2a00:1450:400e:800::200e, icmp_seq=7 hlim=61 time=6.020 ms--- 2a00:1450:400e:800::200e ping6 statistics ---
12 packets transmitted, 12 packets received, 0.0% packet loss
round-trip min/avg/max/std-dev = 5.979/6.024/6.106/0.036 ms
[2.7.0-DEVELOPMENT][admin@pfSense.lan]/root: grep ax | grep 'dpinger'
^C
[2.7.0-DEVELOPMENT][admin@pfSense.lan]/root: -
@louis2 said in Issues with IPV6:
grep ax | grep 'dpinger'
sorry,
ps ax | grep 'dpinger'
My IPv6 interface (he.net' :
78401 - Is 2:11.06 /usr/local/bin/dpinger -S -r 0 -i HENETV6_TUNNELV6 -B 2001:470:beef:5c0::2 -p /var/run/dpinger_HENETV6_TUNNELV6~2001:470:beef:5c0::2~2001:470:beef:5c0::1.pid -u /var/run/dpinger_HENETV6_TUNNELV6~2001:470:beef:5c0::2~2001:470:beef:5c0::1.sock -C /etc/rc.gateway_alarm -d 0 -s 500 -l 2000 -t 60000 -A 1000 -D 500 -L 20 2001:470:beef:5c0::1
where 2001:470:beef:5c0::1 is actually my IPv6 gateway
I can ping it - like dpinger :
[22.05-RELEASE][admin@pfSense.overhere.net]/root: ping6 2001:470:beef:5c0::1
PING6(56=40+8+8 bytes) 2001:470:beef:5c0::2 --> 2001:470:beef:5c0::1
16 bytes from 2001:470:beef:5c0::1, icmp_seq=0 hlim=64 time=45.301 ms
16 bytes from 2001:470:beef:5c0::1, icmp_seq=1 hlim=64 time=43.746 ms
16 bytes from 2001:470:beef:5c0::1, icmp_seq=2 hlim=64 time=44.482 ms
^C -
[2.7.0-DEVELOPMENT][admin@pfSense.lan]/root: ps ax | grep 'dpinger'
31465 - Is 0:09.22 /usr/local/bin/dpinger -S -r 0 -i WAN_PPPOE -B 77.174.abc.def -p /var/ru
31795 - Is 0:07.53 /usr/local/bin/dpinger -S -r 0 -i WAN_DHCP6 -B fe80::6a05:caff:fe5a:813d
88478 1 S+ 0:00.00 grep dpinger
[2.7.0-DEVELOPMENT][admin@pfSense.lan]/root: -
L louis2 referenced this topic on
-
 S stephenw10 referenced this topic on
S stephenw10 referenced this topic on
-
A couple of months past after I did create this topic. I hoped it would be solved in the FreeBSD14 release.
However, I am running 2.7 FreeBSD14 now ...... and the problem is still there

-
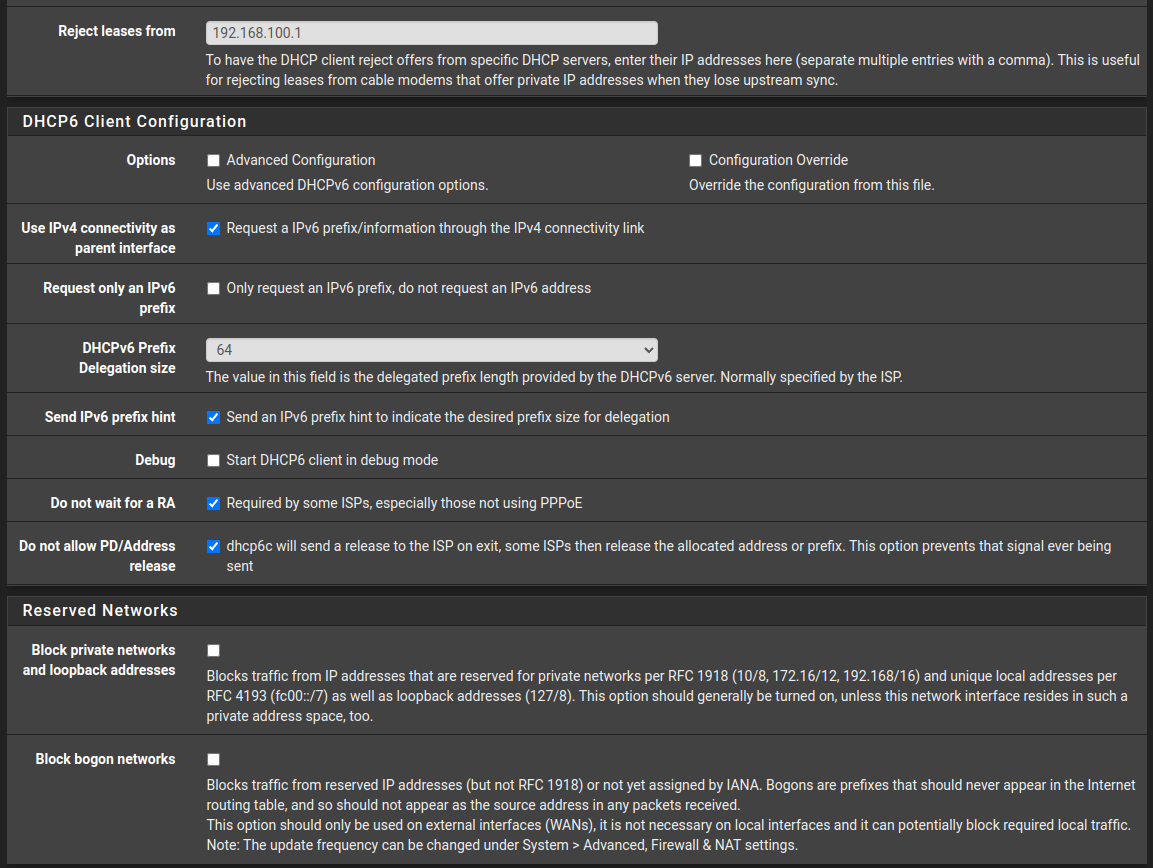
@louis2 I had the same issue and these settings fixed it. Make sure DHCP6 is selected in 'IPv6 Configuration Type' and Gateway Monitoring is turned off for IPv6. Then release and renew WAN in Status->Interfaces.
-
I do not fully understand the behavoir. But I was all ready trying take make a change, when I had some trouble and also a system crash. So I will perhaps try later.
However,
- turned off gateway monitoring for IPv6, seems a bad idea to me. And apart from that no idea where to find that setting
- my provider interface is ppoe based and some settings you are suggesting are strange in relation to ppoe
- I have a fixed /48 range
- when turning on advanced dhcp options, I noticed a field ^Prefix Interface^ really do not know what to imagine there. One of my many interfaces was listed there, no idea why that one. If there is something like a ^Prefix Interface^ what ever it may be, I would expect the WAN interface to have that functionallity
-
@louis2 You can find gateway monitoring in System->Routing->WAN_DHCP6 edit. You should do this for WAN_DHCP too just in case since it will prevent either interfaces from going down when you briefly lose a connection. For the prefix length keep /48 then. I still think it's worth trying all these settings, but also try them with and without 'Do not wait for a RA' enabled. If none of these work then maybe try changing some settings in your modem (bridge mode) and do a reboot on both devices.
-
 D Dobby_ referenced this topic on
D Dobby_ referenced this topic on