DNS Resolution of server failing... but I can ping the box?
-
Hello,
I am attempting to connect to my firewall with a wireguard tunnel and have it put the devices in a VLAN of their own with only access to that network. The address space I've chosen for that is 172.16.0.0/12.
I have allowed ICMP echo reply requests to hit the firewall, and can ping it via my no-ip domain name no problem. However, when I attempt to connect to the firewall via wireguard, I get the following message.
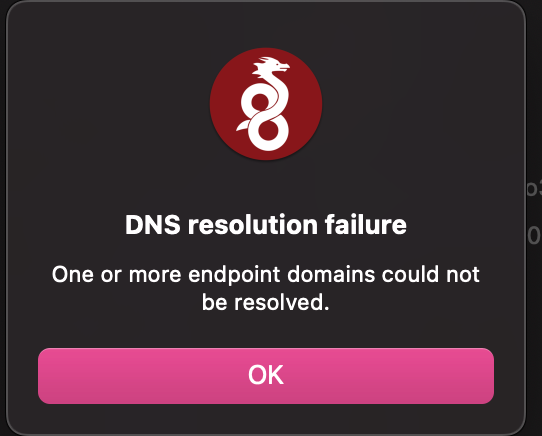
As far as I can tell, my configurations are correct. I'll include screenshots of my firewall rules as they are.
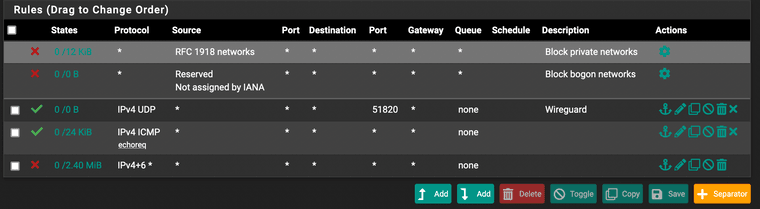
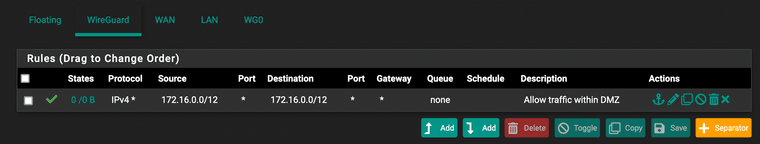
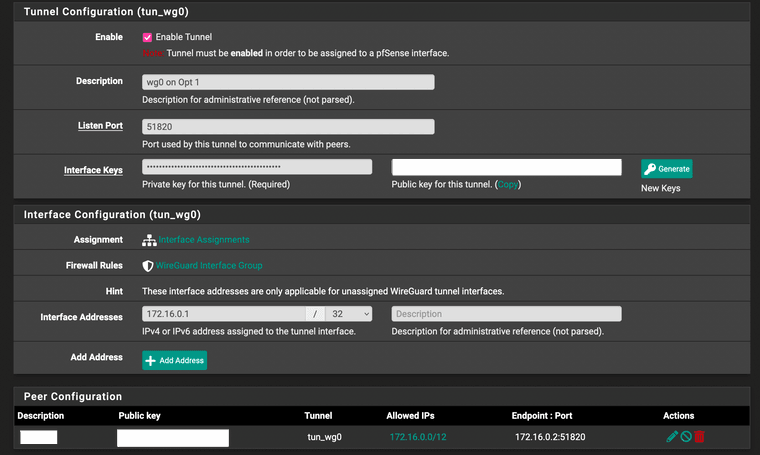
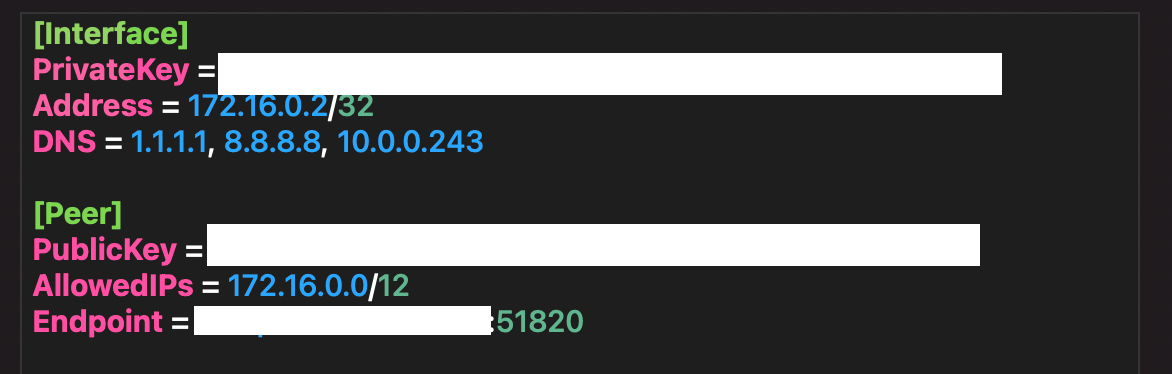
Any suggestions are welcome. I'm pretty stumped. I can ping the wireguard server on both the lan and wan interfaces using the domain name from my intended client, but no dice on actually resolving the server via the wireguard software for some reason.
-
@lukeclover21 The client is using the WireGuard interface as its DNS? I think you need a rule on that to allow port 53 TCP+UDP to This Firewall, or at least the WireGuard IP. (saying this having never used WireGuard)
-
@steveits No, the client should be using 1.1.1.1, then 8.8.8.8 as it's dns servers. Ideally I'd like to host my own dns, but right now I'm focused on getting this wireguard thing working first. I attempted to open that port externally but got the same result as before, cannot resolve the domain.
-
@lukeclover21 So if you're connecting out to the Internet then you should need a rule allowing devices on WireGuard to get out to those two IPs. And optionally the Internet. Interfaces are "deny by default."
https://docs.netgate.com/pfsense/en/latest/recipes/wireguard-ra.html#firewall-rules
"Next, add a rule to pass traffic inside the WireGuard tunnel" -
So, after some further digging, I discovered a couple things.
- You have to actually assign the tunnel to an interface
- The MacOS Wireguard app doesn't support .ddns.net domains
Thank you for your help, once I assigned the interface correctly everything worked like a charm.