WPA2-Enterprise (EAP-TLS) User Authentication finally works on Windows 10 - how to use Computer Authentication and strip out "host/" in username?
-
[Long time no post. In 2019, lightning struck either our house or just a few feet outside it, and despite using robust Zero Surge surge protectors, the lightning surge entered via coax cable --> cable modem --> ethernet and basically fried everything downstream via ethernet cable. I have since made sure our coax entrance is properly grounded (it wasn't... this isn't my house so I had no idea), plus out of an abundance of caution, I added a pair of TrendNET fiber media converters and a 2 meter OM3 cable to convert the incoming ethernet cable from the cable modem --> fiber --> back to ethernet. This way, if lightning does manage to sneak in via coax and ethernet again, it won't travel through the fiber gap. PM me for details.]
Anyway, my 2013 pfSense box got fried and I only just now rebuilt it in 2023 using an HP t740 thin client and Supermicro Intel i350 4-port NIC. Everything restored fine from the 2019 config (2.4.4p3?) to the latest 2.6.0 release.
My question: I have a Windows 10 Pro laptop (22H2), and I'd like to use WPA2-Enterprise EAP-TLS with it. I imported both the pfSense CA and the user certificate into the Certificates MMC snap-in. It's in 3 places:
- Local standard user's Personal Store (for user authentication)
- Local Admin user's Personal Store (for user authentication)
- Local machine's Personal Store (for computer authentication)
After dealing with an issue where Windows pre-pended "host/" to the username and FreeRADIUS rejecting that in PfSense, I figured out the solution. (Tag me here or PM and I'll do a write-up.) When I log into the laptop, WiFi automatically connects. Everything is great.
What I'd like to do is move from User Authentication to Computer Authentication in Windows. (This is a personal laptop used at home. No AD domain.) In other words, I want the laptop to connect to WiFi as soon as Windows 10 boots, before I even log in.
In the Advanced settings in the Wireless Properties, I changed it from User to Computer Authentication, but then it gives me the darn "host/" prefix again and doesn't prompt me to manually type in a username to fix that issue.
Any help?
-
That's a Windows question really.
Are you using wifi running in pfSense or external access points?You might be better asking in the off-topic sub to hear from Windows users.
Steve
-
@stephenw10 Running external APs. Very happy going with a used Ruckus AP off eBay and using the license-free Unleashed firmware.
Very true, this question is indeed a Windows config issue unless there's some FreeRADIUS regular expression config I can do to strip off the "/host/Dell Latitude 1234" to make it "Dell Latitude 1234" so the username matches the certificate CN.
Is it possible to move this thread over to off-topic?
-
 S stephenw10 moved this topic from Wireless on
S stephenw10 moved this topic from Wireless on
-
In case it's clear as mud, maybe some screenshots will help. The certificate I have installed on the laptop has a CN of "Dell Latitude 1234" (with the 1234 being the actual model of the laptop), and the user in FreeRADIUS is also "Dell Latitude 1234," so when I log into the laptop, it automatically connects to the WLAN. This is User-based authentication in Windows 10.
The original issue I got was Windows 10 would pre-pend "host/" to the username, making it "host/Dell Latitude 1234" which wouldn't match the certificate CN, so FreeRADIUS on pfSense would reject the authentication attempt.

I found a solution though:
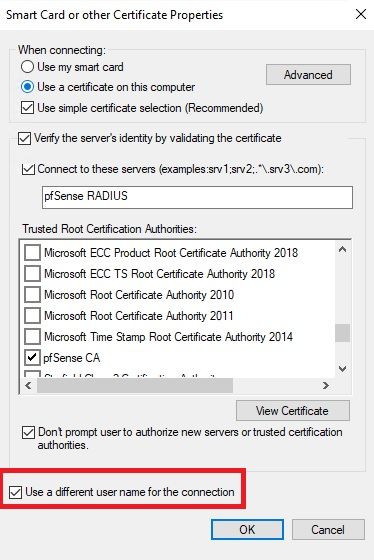
Checking that box then prompts me to type in a username when connecting to the WLAN network:
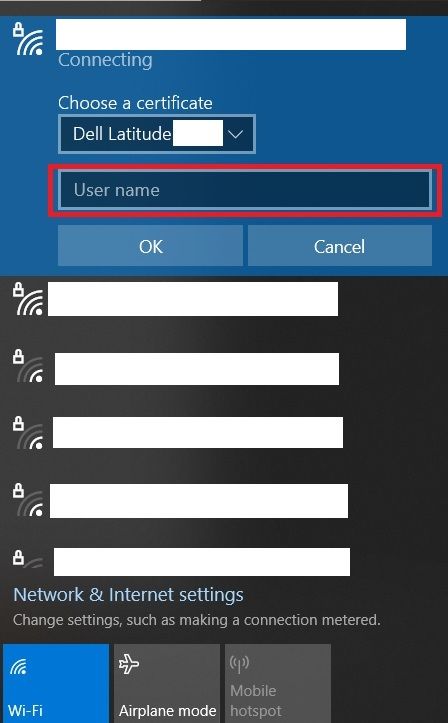
So in that dialog box, I simply type in "Dell Latitude 1234" and it remembers this setting forever, even across reboots. No more "host/Dell Latitude 1234" mismatches. WiFi works.
But it only works when I'm signed in. (This is User based authentication.) What I'd like is for Computer Authentication to also work so that WiFi automatically connects upon boot (which helps with things like RDP into the laptop), but there's no workaround to get rid of the pesky way Windows automatically prepends "host/" to the username. Still get the original error in FreeRADIUS:

-
Is there anywhere on the Web I can ask to get solutions to this? I can't for the life of me figure out where to ask or what to search for. Surely I can't be the only one here trying to get WPA3-Enterprise working on a Windows laptop. (The WPA2-Enterprise in the thread title is a compromise, but it's a separate issue trying to get WPA3-Enterprise to work, and I made a thread in the Ruckus Unleashed forums, which is also not getting any replies.)
Frustration all around.
My end goals are:
- WPA3-Enterprise (EAP-TLS) working on Windows 10 laptop and my phones instead of just WPA2-Enterprise.
- On the Windows laptop, I'd like for WiFi to connect before I log in. This helps with e.g. if I want to RDP to the laptop from my desktop PC to do maintenance.
-
@finger79 don't know if pfSense allows this , but freeradius has a scripting language called unlang which could possible deal with your issue for the
host/part
https://freeradius.org/radiusd/man/unlang.htmlhaven't used EAP-TLS myself , but would it possible to add a SAN to your certificate having
host/Dell ...as an alternative subject name ? -
@aduzsardi said in WPA2-Enterprise (EAP-TLS) User Authentication finally works on Windows 10 - how to use Computer Authentication and strip out "host/" in username?:
@finger79 don't know if pfSense allows this , but freeradius has a scripting language called unlang which could possible deal with your issue for the
host/part
https://freeradius.org/radiusd/man/unlang.htmlhaven't used EAP-TLS myself , but would it possible to add a SAN to your certificate having
host/Dell ...as an alternative subject name ?Thanks, that's a possible lead. I'll look into it.
Edit: Oof, I wish there were some easy examples. I just need a regular expression that's like:
"If you see a username that contains "host/foo" strip it out and only return foo for the username." I have no earthly idea where to insert this code in FreeRADIUS too. Surely there's some unlang experts on this forum.
-
@finger79 this might help https://lists.freeradius.org/pipermail/freeradius-users/2011-March/052744.html
-
Did you ever sort this one? I'm having the same issue
-
@jamesg246 said in WPA2-Enterprise (EAP-TLS) User Authentication finally works on Windows 10 - how to use Computer Authentication and strip out "host/" in username?:
Did you ever sort this one? I'm having the same issue
Nah, I put it on hold. Only User Authentication works so far in Windows 10, so WiFi only connects after I log in. It makes attempts to connect to WiFi before login via the Computer Authentication (since I have both checked), but it still prepends "host/" before the certificate Username and the FreeRADIUS implementation in pfSense rejects it.
-
@Finger79 I have this working with Computer authentication, but only with the Check Client Certificate CN option disabled in EAP settings. If I enable this, it stops working.
As you've said the authentication requests come as "host/CN" - I've added "host/CN" to the users table and this allows the device to pickup the vlan setting etc. At the moment I'm using the revoke lists to get around having Check Client Certificate CN disabled.
It looks like the following needs to be added to the hints file and using the pre-process module
DEFAULT Prefix == "/host", Strip-User-Name = Yes
DEFAULT Suffix == ".server.domain.com", Strip-User-Name = YesIn my case I don't need to add the suffix but I've no idea where to start with adding those attributes to the pfsense freeradius server.
-
@jamesg246 said in WPA2-Enterprise (EAP-TLS) User Authentication finally works on Windows 10 - how to use Computer Authentication and strip out "host/" in username?:
@Finger79 I have this working with Computer authentication, but only with the Check Client Certificate CN option disabled in EAP settings. If I enable this, it stops working.
That's interesting. The "Check Client Certificate CN" option in EAP settings doesn't seem to do anything to me. Thread here with the Redmine bug report linked: Longstanding FreeRADIUS EAP-TLS security bug on validating client certificate common name
In other words, even with "Check Client CN" enabled, I can completely delete the FreeRADIUS Users table and clients can still connect. Strange behavior.
-
@meii sending this in the original thread since there's a 1000 character "chat" limit.
(tl;dr: To others reading, this is maybe a workaround to fixing the issue I reported. Instead of messing with custom FreeRADIUS or pfSense settings, I just made sure there is only ONE copy of the user certificate installed in the Computer Account and NOT any local user accounts (Standard Users, Local Admin users, etc.). And Same with the root CA certificate: only installed in the Computer Account certificate store, and this is accessed by going to "mmc" and then adding the Certificates snap-in then selecting Computer Account)
- First thing I changed was made sure I installed certificates in only one trust store. So my current setup I have one "standard user" account that is my main account on Windows. And I have a "Admin" account that I only use for UAC prompts, etc. I think each one has its own certificate trust store. I.e. if you are logged in as regular/standard user, just do "certmgr.msc" and I made sure to delete the cert from Personal->Certificates and the pfSense root CA cert from Trusted Root Certification Authorities->Certificates. For the admin account, either log in locally or just do "certmgr.msc" again and right-click and "Run as administrator" and it makes another window. Even there, I made sure both the user certificate and the root CA certs were deleted. So now we want to access the actual computer's certificate trust store. I went to "mmc" and "Run as administrator" then File->Add/remove snap-in. Then add "Certificates" to the menu on the right and hit ok. Then make sure to select "Computer account" and Finish. I think (if I remember correctly) this is where I installed the user certificate for WiFi in Personal --> Certificates and the root CA in Trusted Root Certification Authorities --> Certificates.
I think doing all this makes sure there's no duplicate certificates. When there's two, Windows will pause and pop-up the drop-down thingy asking you to choose a cert before connecting, whereas with just one user cert (installed in the Computer account) it only has one choice.
- Second thing I did was in the WiFi network settings (using WPA2-Enterprise still, EAP-TLS)... one way I got there was Control Panel --> Network and Sharing Center --> click on the network if you're already connected. I think if you're not connected it only lets you change settings when you start from scratch...not sure. Anyway we want the old Windows 7 or so window, not the newer one. So "Wireless Properties" where it has the two tabs at the top: Connection and Security. On Security tab, where it says "Choose a network authentication method" I made sure it was Microsoft: Smart Card or other certificate. I have "Remember my credentials for this connection each time I'm logged in" checked. Click on Settings. When connecting, "Use a certificate on this computer" and "Use simple certificate selection (Recommended)" checked. Didn't bother with Advanced button. Below it I have "Verity the server's identity by validating the certificate" checked and also the one below it "Connect to these servers..." and I put in the FQDN for the server cert in pfSense I'm using for FreeRADIUS (in my case radius.home.internal). In the list of Trusted Root Certificate Authorities below, I made sure only my pfSense root CA was selected and nothing else. At the bottom I have "Don't prompt user to authorize new servers or trusted certification authorities" checked. Lot of these prevent WPA2-Enterprise Wi-Fi attacks in the wild. So I think the relevant part for what you're running into was in "Advanced Settings" from the main "Security" tab. "Specify authentication mode" is checked and I put "User or computer authentication". Down below, I do not have that part checked where it says "Enable single sign on for this network". On the 802.11 settings tab and "Fast roaming," I have "Enable Pairwise Master Key (PWK) caching" checked.
So I don't know if any of the above settings in Step 2 helped except maybe the "User or computer authentication," but I definitely think Step 1 above helped -- making sure I only installed the user Wi-Fi cert and the pfSense Root CA cert in the computer certificate store via mmc Certificates snap-in. And made sure to first delete those certs from the Standard and Admin user accounts. (Oh! Note: I made sure to delete all those WiFi certs first to start with a clean slate because once you install them to the computer certificate store, they also magically appear in the "certmgr.msc" for both Standard and Admin user accounts, so it gets confusing.
Either way, Windows no longer prompts me to select a cert when WiFi connects, and I don't see the stupid "host/" prepend string or whatever in the pfSense logs. I haven't really tested if it logs into WiFi when you first boot up the laptop before logging in -- I think it did it! So in the end I didn't even need to learn all the weird FreeRADIUS syntax since it looked like a giant pain getting custom config settings to work with the pfSense FreeRADIUS GUI. Yuck.
I hope all this helps! Uh if you need screenshots lemme know since it might be clearer than a bunch of words. Hope any of this helps!
-
This post is deleted!