No DHCP on pfSense VLAN with Cisco Smart Switch
-
Sorry for the delay in responding. Just got back into town after traveling. Thanks for the additional information. Very helpful!
I have an SG300 that arrived yesterday and still in a box. Will spark it up today to see what I find and report back. -
@Cannondale one thing nice about the sg300 is shows pvid info ;)
Both in the gui, and from cli
That the gui lists P in the legend, but then doesn't show it, and the cli showing this confusing as hell
Port : gi8 Port Mode: Gvrp Status: disabled Ingress Filtering: true Acceptable Frame Type: admitAll Ingress UnTagged VLAN ( NATIVE ): 1 Port is member in: Vlan Name Egress rule Added by ---- -------------------------------- ----------- ---------------- 10 10 Untagged SWhen I look at a interface with vlan on my sg300
Port : gi1 Port Mode: Access Gvrp Status: disabled Ingress Filtering: true Acceptable Frame Type: admitAll Ingress UnTagged VLAN ( NATIVE ): 99 Port is member in: Vlan Name Egress rule Added by ---- -------------------------------- ----------- ---------------- 99 wan Untagged S Forbidden VLANS: Vlan Name ---- --------------------------------That being said - I had no issues setting a interface to access in a vlan on the sg250, and it working as it should with the vlan tagged to pfsense via "trunk" port.. Even though the cli output is bonkers ;)
There is clearly room for improvement in the info they show in the gui and the cli on the 250.. Why is showing the ingress untagged vlan as 1, when clearly that could not be the case if the interface is access in vlan 10..
Notice on the 300, it shows the native same as the vlan used for egress as untagged.
-
@johnpoz Got the SG300 up and running. Firmware and boot code were quite old (fw 1.2.9.44 and bc 1.1.0.6).
Upgraded both to the latest releases (fw 1.4.11.5 and bc 1.3.5.06), which was a feat in it self! Too bad Cisco hasn’t upgraded the firmware in the last three years!P in the legend, but then doesn't show it, and the cli showing this confusing as hell
I definitely see what you mean!
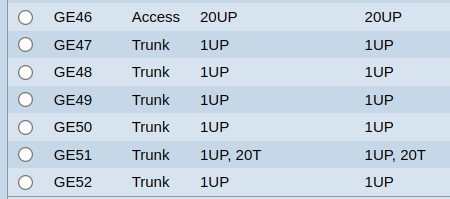
Created the following test vlans on the switch:
Note: igb1 is the Main Lan in pfSenseVLAN10 (Test1)
Switch port 23, Trunk mode, Tagged, connected to pfSense VLAN10 (igb2)
Switch port 24, Access mode, Untagged, connected to Linux workstation
Wide open firewall rule for VLAN10Test results: DHCP works as expected and provides Linux workstation IP
VLAN20 (Test2)
Switch port 51, Trunk mode, Tagged, connected to pfSense igb1 (Main Lan)
Switch port 46, Access mode, Untagged, connected to Linux workstation
Wide open firewall rule for VLAN20Test results: No DHCPREQUEST in pfSense DHCP log, no IP provided to Linux workstation
I must be missing something stupid simple?
-
@Cannondale said in No DHCP on pfSense VLAN with Cisco Smart Switch:
Upgraded both to the latest releases (fw 1.4.11.5 and bc 1.3.5.06), which was a feat in it self! Too bad Cisco hasn’t upgraded the firmware in the last three years!
Well, It has been in End-of-Sale since October 2018, End of Software Maintenance was October 2019 and End of Support is October 2023.
https://www.cisco.com/c/en/us/products/collateral/switches/small-business-300-series-managed-switches/eos-eol-notice-c51-740542.html
So the Main LAN still works from the igb1, but just not the VLAN using that same igb1?
-
Well, It has been in End-of-Sale since October 2018, End of Software Maintenance was October 2019 and End of Support is October 2023.
Interestingly, the SG250 has roughly the same End Dates and had a firmware date of 4/2023.
So the Main LAN still works from the igb1, but just not the VLAN using that same igb1?
Yes that is correct.
-
@Cannondale Hmm... Compared to mine, the pfSense config looks to be ok to me.
-
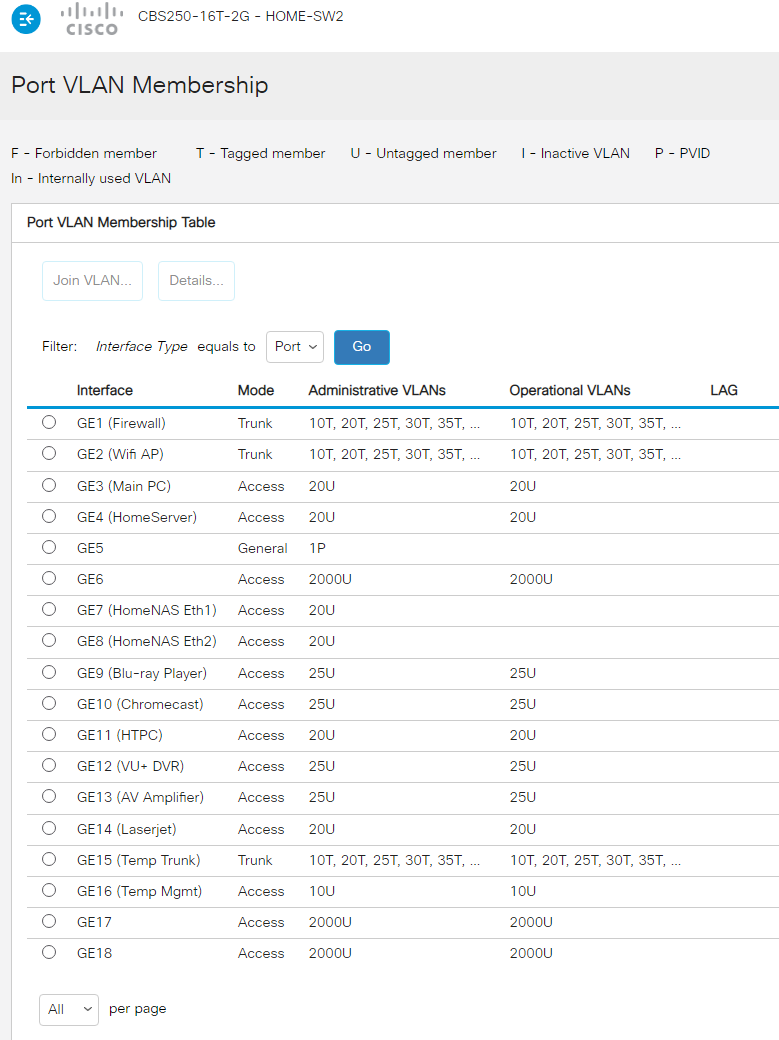
@johnpoz Looks like that the CBS-series (and probably also the SG250) only uses/shows the pvid when the port is set to General Mode...
I set GE5 into General Mode and it now shows 1P
-
Looks like that the CBS-series (and probably also the SG250) only uses/shows the pvid when the port is set to General Mode...
I set GE5 into General Mode and it now shows 1PI saw the same thing with theSG250.
-
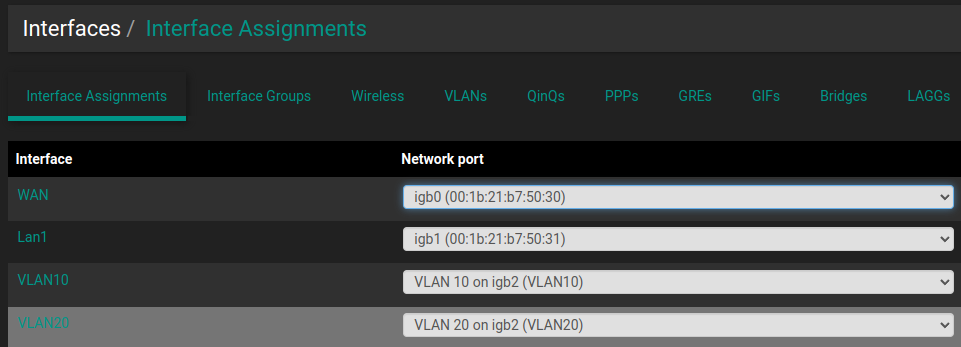
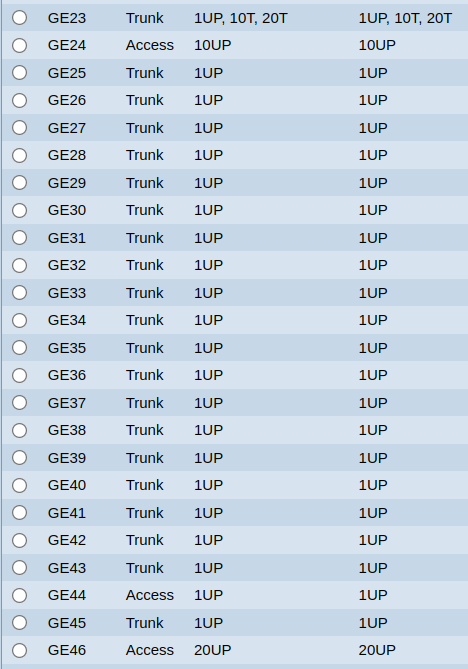
If you put both VLAN10 and VLAN20 on the igb2, can you get both to work through the switches untagged ports?
-
If you put both VLAN10 and VLAN20 on the igb2, can you get both to work through the switches untagged ports?
Yes. This works as expected.
-
Ok, so something gets messed up when there is both tagged and untagged traffic to the port.
I have all my LAN networks in pfSense as VLANS, so everything is tagged. I believe this is also the recommended method.
-
@mvikman Thanks for the additional information.
I have all my LAN networks in pfSense as VLANS, so everything is tagged.
To clarify, you have all of your vlans on switch port gi1, which is connected to your pfSense lan port?
If yes, I should be able to disable my vlan10 (on igb2), which would leave only vlan20 on my igb1 (pfSense lan) and would match your config. Correct?
Would be an easy test. -
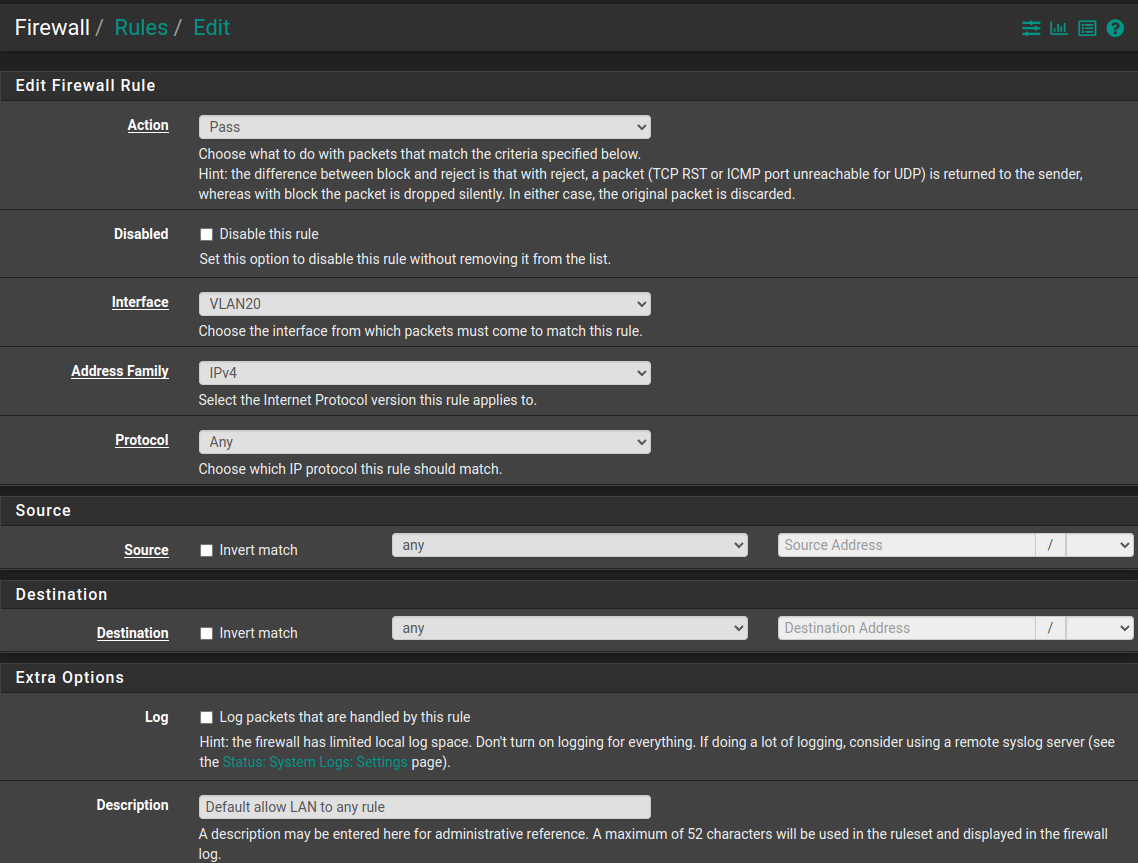
@Cannondale Yes GE1 port is a trunk to pfSense
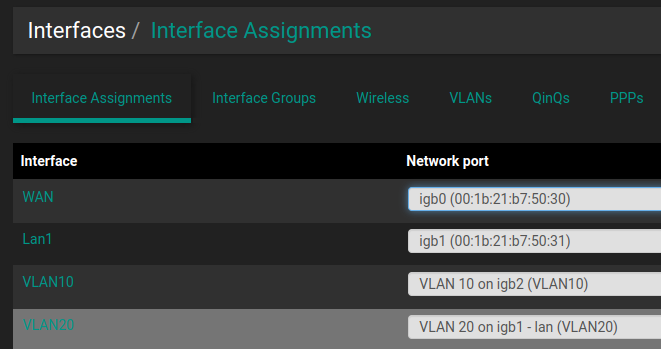
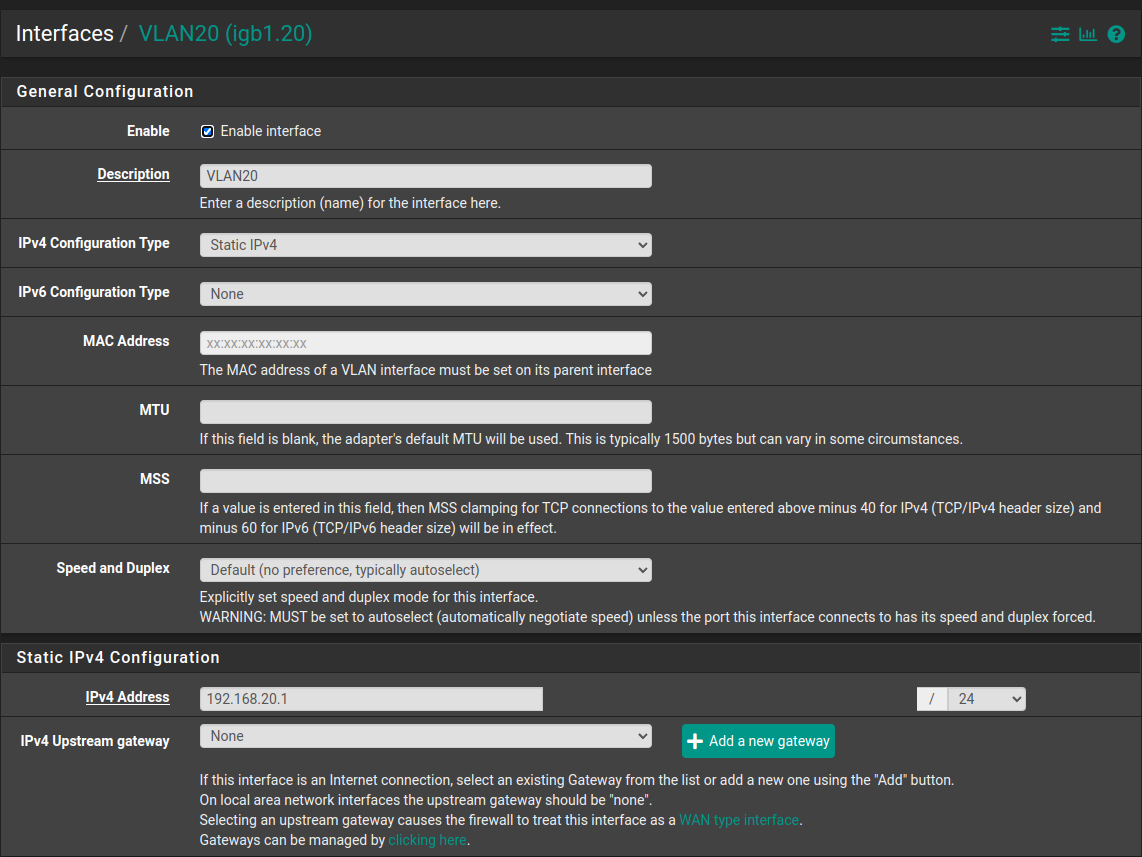
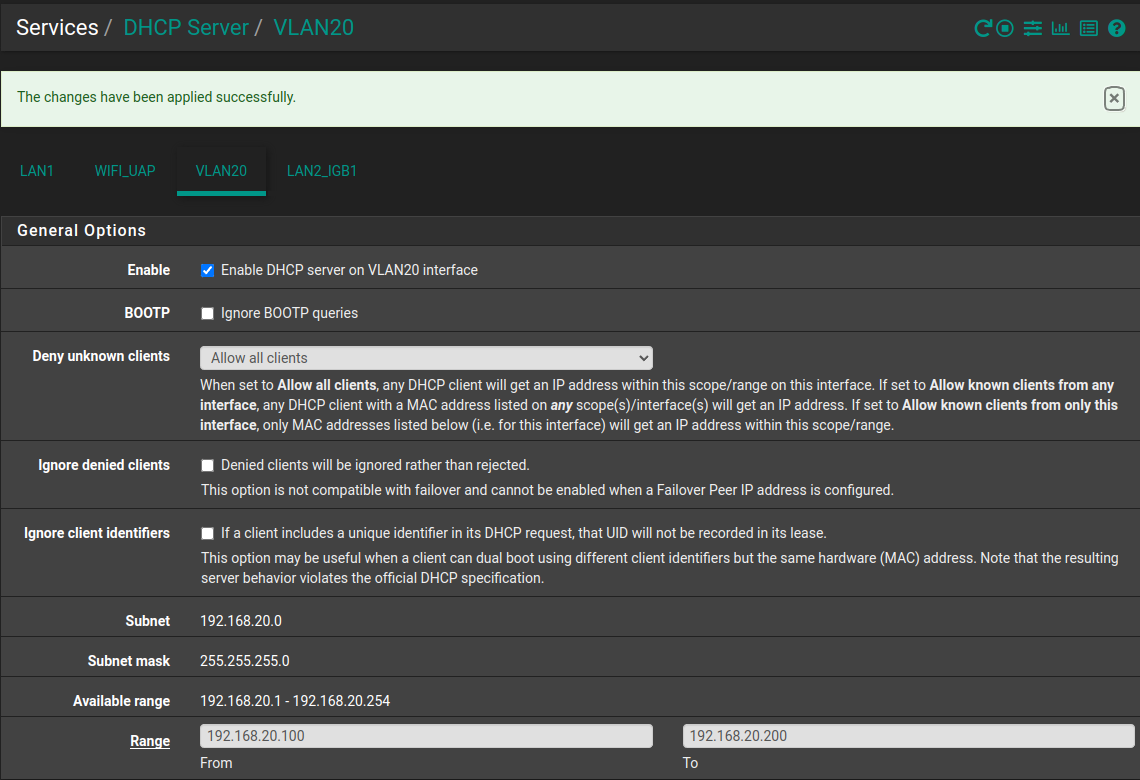
My pfSense interfaces
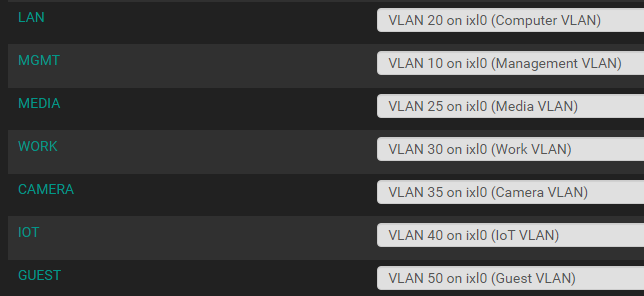
-
@mvikman Thanks for the confirmation.
As a test, I disabled the pfSense VLAN10 interface on igb2.
I also removed VLAN10 from port 23 on the switch.
This left only VLAN20 on my igb1 (pfSense lan) interface.
Unfortunately, the test failed. It didn't make a difference in getting an IP on VLAN20 from DHCP. -
@Cannondale
Somehow your switch configs are a miracle. Can you post your the routing table / standard gateway of that switch? Is routing disabled/enabled?Pls show all the firewall rules, not in edit mode.... also the floating rules just to see how the rules are in the rows.
-
Can you post your the routing table
#show ip route Maximum Parallel Paths: 1 (1 after reset) IP Forwarding: disabled Codes: > - best, C - connected, S - static D 0.0.0.0/0 [1/2] via 192.168.0.201, 47:42:32, vlan 1 C 192.168.0.0/24 is directly connected, vlan 1Is routing disabled/enabled?
What is the cli command to confirm?Pls show all the firewall rules, not in edit mode.... also the floating rules just to see how the rules are in the rows.
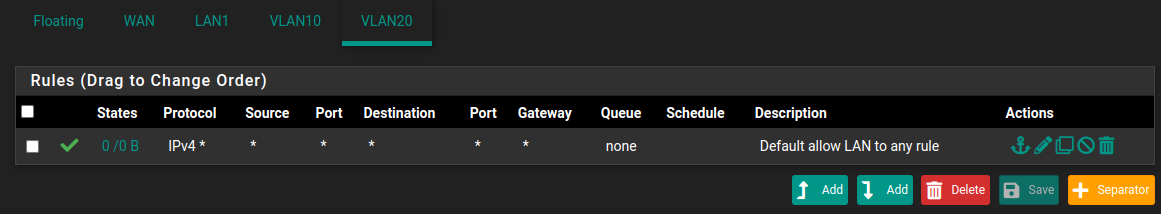
-
@Cannondale the rules have zero to do with dhcp.. Once you enable dhcp the hidden rules would allow it..
So your saying is when you have tagged 10 and 20 on igb2 with no native untagged nework on this interface both 10 and 20 work.
But if you put 10 and 20 tagged on igb1 that has a native network on it - the tagged vlans don't work?
Post the output of your ifconfig on pfsense..
example here is mine..
igb2: flags=8863<UP,BROADCAST,RUNNING,SIMPLEX,MULTICAST> metric 0 mtu 1500 description: WLAN options=4e120bb<RXCSUM,TXCSUM,VLAN_MTU,VLAN_HWTAGGING,JUMBO_MTU,VLAN_HWCSUM,WOL_MAGIC,VLAN_HWFILTER,RXCSUM_IPV6,TXCSUM_IPV6,NOMAP> ether 00:08:a2:0c:e6:20 inet6 fe80::208:a2ff:fe0c:e620%igb2 prefixlen 64 scopeid 0x3 inet 192.168.2.253 netmask 0xffffff00 broadcast 192.168.2.255 media: Ethernet autoselect (1000baseT <full-duplex>) status: active nd6 options=21<PERFORMNUD,AUTO_LINKLOCAL> igb2.4: flags=8843<UP,BROADCAST,RUNNING,SIMPLEX,MULTICAST> metric 0 mtu 1500 description: W_PSK options=4600003<RXCSUM,TXCSUM,RXCSUM_IPV6,TXCSUM_IPV6,NOMAP> ether 00:08:a2:0c:e6:20 inet6 fe80::208:a2ff:fe0c:e620%igb2.4 prefixlen 64 scopeid 0xb inet 192.168.4.253 netmask 0xffffff00 broadcast 192.168.4.255 groups: vlan vlan: 4 vlanproto: 802.1q vlanpcp: 0 parent interface: igb2 media: Ethernet autoselect (1000baseT <full-duplex>) status: active nd6 options=21<PERFORMNUD,AUTO_LINKLOCAL> igb2.6: flags=8843<UP,BROADCAST,RUNNING,SIMPLEX,MULTICAST> metric 0 mtu 1500 description: W_Guest options=4600003<RXCSUM,TXCSUM,RXCSUM_IPV6,TXCSUM_IPV6,NOMAP> ether 00:08:a2:0c:e6:20 inet6 fe80::208:a2ff:fe0c:e620%igb2.6 prefixlen 64 scopeid 0xc inet 192.168.6.253 netmask 0xffffff00 broadcast 192.168.6.255 groups: vlan vlan: 6 vlanproto: 802.1q vlanpcp: 0 parent interface: igb2 media: Ethernet autoselect (1000baseT <full-duplex>) status: active nd6 options=21<PERFORMNUD,AUTO_LINKLOCAL>I am curious to the options you have set on the parent interface mostly.
if you do a pcap with tcpdump on ig2 do you see the tags with the -e flag, but when you do that on igb1 you dont?
-
So your saying is when you have tagged 10 and 20 on igb2 with no native untagged nework on this interface both 10 and 20 work.
Correct
But if you put 10 and 20 tagged on igb1 that has a native network on it - the tagged vlans don't work?
Actually, what I tried first was vlan10 on igb2 and vlan20 on ibg1, In this config, only vlan10 works.
Second test was vlan10 and vlan20 on igb2. Both work.
Third test was disable vlan10 and put vlan20 on igb1. This does not work. Similar to first test.
How do I display the pfSense ifconfig? Don't see it in the menu.
-
Post the output of your ifconfig on pfsense
Found it.
igb0: flags=8943<UP,BROADCAST,RUNNING,PROMISC,SIMPLEX,MULTICAST> metric 0 mtu 1500 description: WAN options=e100bb<RXCSUM,TXCSUM,VLAN_MTU,VLAN_HWTAGGING,JUMBO_MTU,VLAN_HWCSUM,VLAN_HWFILTER,RXCSUM_IPV6,TXCSUM_IPV6> ether 00:1b:21:b7:50:30 inet6 fe80::21b:21ff:feb7:5030%igb0 prefixlen 64 scopeid 0x1 inet 71.46.127.170 netmask 0xfffff000 broadcast 255.255.255.255 media: Ethernet autoselect (1000baseT <full-duplex>) status: active nd6 options=21<PERFORMNUD,AUTO_LINKLOCAL> igb1: flags=8943<UP,BROADCAST,RUNNING,PROMISC,SIMPLEX,MULTICAST> metric 0 mtu 1500 description: Lan1 options=e100bb<RXCSUM,TXCSUM,VLAN_MTU,VLAN_HWTAGGING,JUMBO_MTU,VLAN_HWCSUM,VLAN_HWFILTER,RXCSUM_IPV6,TXCSUM_IPV6> ether 00:1b:21:b7:50:31 inet6 fe80::21b:21ff:feb7:5031%igb1 prefixlen 64 scopeid 0x2 inet 192.168.0.201 netmask 0xffffff00 broadcast 192.168.0.255 media: Ethernet autoselect (1000baseT <full-duplex>) status: active nd6 options=21<PERFORMNUD,AUTO_LINKLOCAL> igb2: flags=8943<UP,BROADCAST,RUNNING,PROMISC,SIMPLEX,MULTICAST> metric 0 mtu 1500 description: WiFiUAP options=e100bb<RXCSUM,TXCSUM,VLAN_MTU,VLAN_HWTAGGING,JUMBO_MTU,VLAN_HWCSUM,VLAN_HWFILTER,RXCSUM_IPV6,TXCSUM_IPV6> ether 00:1b:21:b7:50:34 inet6 fe80::21b:21ff:feb7:5034%igb2 prefixlen 64 scopeid 0x3 media: Ethernet autoselect (1000baseT <full-duplex>) status: active nd6 options=21<PERFORMNUD,AUTO_LINKLOCAL>igb2.10: flags=8943<UP,BROADCAST,RUNNING,PROMISC,SIMPLEX,MULTICAST> metric 0 mtu 1500 description: VLAN10 options=600003<RXCSUM,TXCSUM,RXCSUM_IPV6,TXCSUM_IPV6> ether 00:1b:21:b7:50:34 inet6 fe80::21b:21ff:feb7:5034%igb2.10 prefixlen 64 scopeid 0xf inet 192.168.10.1 netmask 0xffffff00 broadcast 192.168.10.255 groups: vlan vlan: 10 vlanpcp: 0 parent interface: igb2 media: Ethernet autoselect (1000baseT <full-duplex>) status: active nd6 options=21<PERFORMNUD,AUTO_LINKLOCAL> igb1.20: flags=8843<UP,BROADCAST,RUNNING,SIMPLEX,MULTICAST> metric 0 mtu 1500 description: VLAN20 options=600003<RXCSUM,TXCSUM,RXCSUM_IPV6,TXCSUM_IPV6> ether 00:1b:21:b7:50:31 inet6 fe80::21b:21ff:feb7:5031%igb1.20 prefixlen 64 scopeid 0x10 inet 192.168.20.1 netmask 0xffffff00 broadcast 192.168.20.255 groups: vlan vlan: 20 vlanpcp: 0 parent interface: igb1 media: Ethernet autoselect (1000baseT <full-duplex>) status: active nd6 options=21<PERFORMNUD,AUTO_LINKLOCAL> -
@Cannondale your not testing this with AP are you.. Your putting actual devices on the ports that are in access mode.. I see a description of wifiUAP..