freeradius / eap-tls / Android 13
-
@johnpoz said in freeradius / eap-tls / Android 13:
What versions of android are you using @mcury and your using eap-tls?
Tested with Android 11, 12, Macbook air M1, Iphone 11 pro (I'm almost sure it is an iphone 11) and Windows 10 and 11 22H1.
Yes, using EAP-TLS (lets encrypt certificate), I just renew it within a 90 day period and upload it to freeradius server.
Let me enable the server here in my lab so I can post the debug for you.
-
@mcury Yeah not having any issues with iphone (13), ipad (air 5th gen) both running ios 16.5, windows 10 pro 22H2, acer chromebook running whatever latest os is as of day or two ago, and android lenovo p11+ tablet running 12.
Not sure what the issue is with his.. He got his android 7 working with wpa2 enterprise..
@furom did you get your windows test box working? Did you say you found an issue on your switch? So I assume you got your linux and windows and old tablet all working with wpa2-ent
I don't use amce for my certs for eap-tls, all certs via cert manger in pfsense (23.01) using ECDSA with prime256v1 for both the CA and the server and client certs.
Running unifi controller 7.4.156 and uap-ac-pro, lite and lr AP all on 6.5.54 firmware.
edit: here is output of rad -X and my tablet connecting.
Looks like this time it authed connecting to my LR - so have seen valid connections on all 3 of my different APs.
-
@johnpoz said in freeradius / eap-tls / Android 13:
@mcury Yeah not having any issues with iphone (13), ipad (air 5th gen) both running ios 16.5, windows 10 pro 22H2, acer chromebook running whatever latest os is, and android lenovo p11+ tablet running 12.
Not sure what the issue is with his.. He got his android 7 working with wpa2 enterprise..
@furom did you get your windows test box working? Did you say you found an issue on your switch? So I assume you got your linux and windows and old tablet all working with wpa2-ent
I gave up on the windows client. Issue I had with the Netgate switch was not assigning the correct lan, so when corrected old tablet started working (issue then was it did not get an IP), which is the only client so far
-
@furom well maybe you want to try the amce certs, there shouldn't be anyway the tablet doesn't trust those.. Not exactly sure how you get a client cert, would assume just need to be able to validate your fqdn via dns would get you the client cert, just like your server cert, etc.
-
@johnpoz said in freeradius / eap-tls / Android 13:
@furom well maybe you want to try the amce certs, there shouldn't be anyway the tablet doesn't trust those.. Not exactly sure how you get a client cert, would assume just need to be able to validate your fqdn via dns would get you the client cert, just like your server cert, etc.
I have though of it before, but that would require a domain and public DNS, which I don't have.
I really do appreciate you guys trying to find some sense in this. There is a beta of Android 14, not sure if I could load that on my tablet, but could be something. Hopefully this would be fixed in 14, but will hold my breath just a little while longer... :)But as said earlier, 13 is a lot pickier with trusting the CA's. So I would not be surprised if 'let's encrypt' would work right away, as it is trusted by browsers by default
-
I took so long due because this VM wasn't powered on in six months..
My administrator account password expired, users account passwords expired, certificates expired...
More than 160 packages to update in Ubuntu..
Then I got my user stuck in SQL database since simultaneous use is set to one.
What a mess to get this lab working again..With EAP details, ldap and SQL working.. (Android 12 Galaxy S10 connecting to a nandoHD).
full_test.txt -
So found some info last night that said the only way to make Android >11/12 accept a self-signed CA is now to use an MDM (Mobile Device Manager) or a secure app such as Knox to handle the certs.
Edit: Well... put it this way... It was yet another rabbit-hole... A pure nightmare for an average person like myself. Why would I want a full scale mobile deployment environment just to use decent security using certificates - for ONE lousy tablet?? :(
I even tried to get a secure folder working, it would possibly make it work too, but that is not available any longer... bummer...
-
@furom but isn't this line a bit interersting...
Sat May 27 09:36:29 2023 : ERROR: (4) eap_tls: (TLS) Failed reading from OpenSSL: /var/jenkins/workspace/pfSense-Plus-snapshots-23_01-main/sources/FreeBSD-src-plus-RELENG_23_01/crypto/openssl/ssl/record/rec_layer_s3.c[1621]:error:14094438:SSL routines:ssl3_read_bytes:tlsv1 alert internal errorIt is clearly a path from building pfSense 23.01, or looks that way at least... Perhaps if I try using same certs but with a separate radius server... after all this it could not cause more grief (hopefully)
-
@furom said in freeradius / eap-tls / Android 13:
Perhaps if I try using same certs but with a separate radius server.
Why would that work? Its the client that has to trust the CA.
-
@johnpoz said in freeradius / eap-tls / Android 13:
@furom said in freeradius / eap-tls / Android 13:
Perhaps if I try using same certs but with a separate radius server.
Why would that work? Its the client that has to trust the CA.
I know that. :) But thus far a lot less errors at least. :)
-
@furom what about this
https://aboutssl.org/how-to-create-and-import-self-signed-certificate-to-android-device/
Doesn't say what version of android, but it has it adding an option to the CA via openssl
openssl x509 -req -days 3650 -in CA.pem -signkey priv_and_pub.key -extfile ./android_options.txt -out CA.crt
Or I would assume the acme way would work - this isn't a self signed CA, etc. So for like the 10 you could get a domain you could use.. Or you can always get cheap domain like .xyz for like the first year for like 99 cents ;)
edit: guess I am lucky my tablet is only running 12, which accepts my CA.
edit2: also came across this
Android will not allow a Certificate Authority to be installed from certain locations. The SSL cert must be stored in local storage, but not in the "Downloads" folder and not in Google Drive. Even though this is permitted for user certificates, CA certificates won't work unless moved to a local folder that is not the downloads folder.
Where exactly are you putting the CA cert when you try to install it?
-
@johnpoz said in freeradius / eap-tls / Android 13:
@furom what about this
https://aboutssl.org/how-to-create-and-import-self-signed-certificate-to-android-device/
Doesn't say what version of android, but it has it adding an option to the CA via openssl
openssl x509 -req -days 3650 -in CA.pem -signkey priv_and_pub.key -extfile ./android_options.txt -out CA.crt
Or I would assume the acme way would work - this isn't a self signed CA, etc. So for like the 10 you could get a domain you could use.. Or you can always get cheap domain like .xyz for like the first year for like 99 cents ;)
edit: guess I am lucky my tablet is only running 12, which accepts my CA.
edit2: also came across this
Android will not allow a Certificate Authority to be installed from certain locations. The SSL cert must be stored in local storage, but not in the "Downloads" folder and not in Google Drive. Even though this is permitted for user certificates, CA certificates won't work unless moved to a local folder that is not the downloads folder.
Where exactly are you putting the CA cert when you try to install it?
In the Downloads folder... Was too lazy to create another one. I figured when installed it gets copied anyways, but is perhaps just linked... worth a try! :)
-
@furom This is where I'm at now;
(3) eap_tls: (TLS) EAP Done initial handshake (3) eap_tls: (TLS) recv TLS 1.2 Alert, fatal unsupported_certificate (3) eap_tls: (TLS) The client is informing us that it does not understand the certificate presented by the server. (3) eap_tls: ERROR: (TLS) Alert read:fatal:unsupported certificate (3) eap_tls: (TLS) Server : Need to read more data: error (3) eap_tls: ERROR: (TLS) Failed reading from OpenSSL: error:0A000413:SSL routines::sslv3 alert unsupported certificate (3) eap_tls: (TLS) In Handshake Phase (3) eap_tls: (TLS) Application data. (3) eap_tls: ERROR: (TLS) Cannot continue, as the peer is misbehaving. (3) eap_tls: ERROR: [eaptls process] = fail (3) eap: ERROR: Failed continuing EAP TLS (13) session. EAP sub-module failed (3) eap: Sending EAP Failure (code 4) ID 25 length 4I tried with a .crt cert when it needs .pem, so will convert and try again
-
@furom a .crt file is a pem.. That error could mean it its not trusting the cert, because the CA that signed it isn't trusted.
When you look in the crt does its show in the first line when open with text editor?
-----BEGIN CERTIFICATE-----
-
@johnpoz said in freeradius / eap-tls / Android 13:
@furom a .crt file is a pem.. That error could mean it its not trusting the cert, because the CA that signed it isn't trusted.
When you look in the crt does its show in the first line when open with text editor?
-----BEGIN CERTIFICATE-----
It does. Both CA & cert
also, just tried moving the certs on the tablet out of Downloads and reinstalled them, then trying against freeRad/pfSense same issue as before...
(4) eap_tls: (TLS) EAP Done initial handshake (4) eap_tls: (TLS) recv TLS 1.2 Alert, fatal internal_error (4) eap_tls: ERROR: (TLS) Alert read:fatal:internal error (4) eap_tls: (TLS) Server : Need to read more data: error (4) eap_tls: ERROR: (TLS) Failed reading from OpenSSL: error:14094438:SSL routines:ssl3_read_bytes:tlsv1 alert internal error (4) eap_tls: (TLS) In Handshake Phase (4) eap_tls: (TLS) Application data. (4) eap_tls: ERROR: (TLS) Cannot continue, as the peer is misbehaving. (4) eap_tls: ERROR: [eaptls process] = fail (4) eap: ERROR: Failed continuing EAP TLS (13) session. EAP sub-module failed -
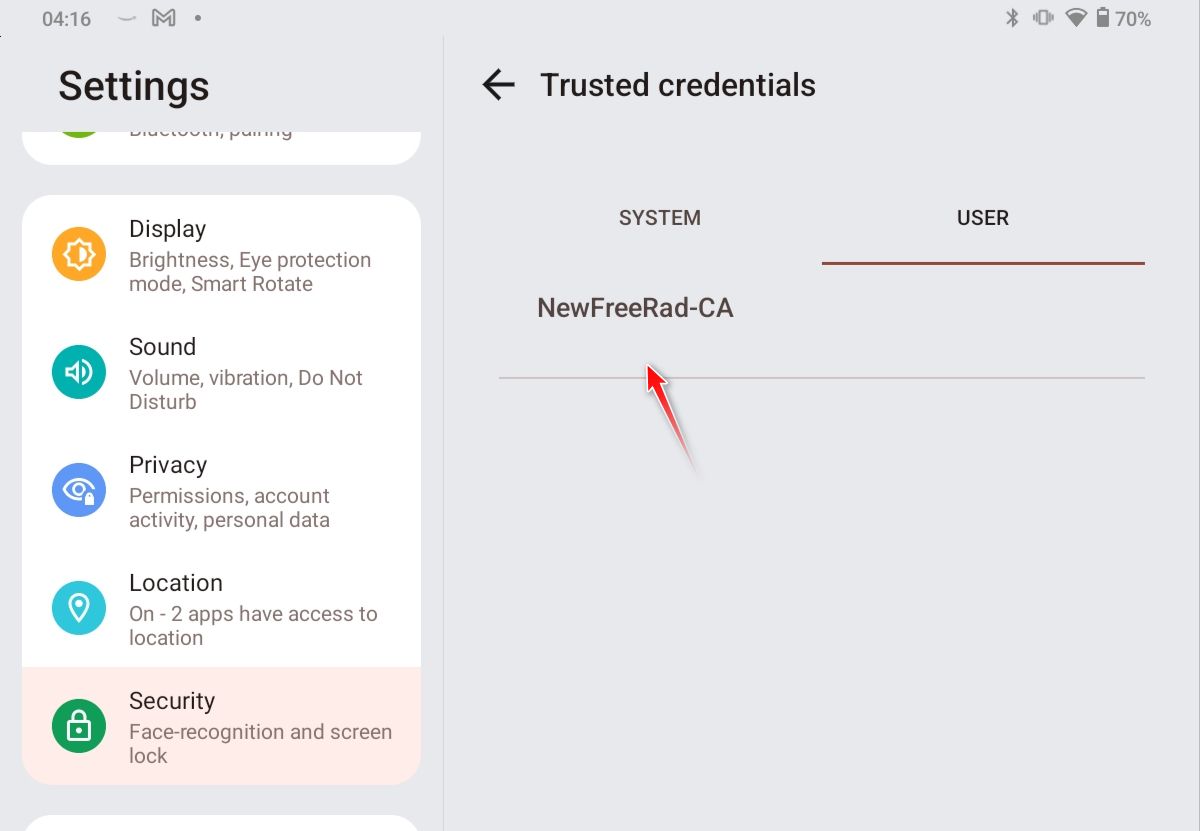
@furom you should see your CA as trusted in your user section..
Did you try it with the link I provided that has adding some sort of option to the CA cert.
-
@johnpoz said in freeradius / eap-tls / Android 13:
@furom you should see your CA as trusted in your user section..
Well, it does not show up there... :( Under 'User certificates' both show though, but not whats matter here...
Did you try it with the link I provided that has adding some sort of option to the CA cert.
Not yet. much going on now, but will attend that now :)
-
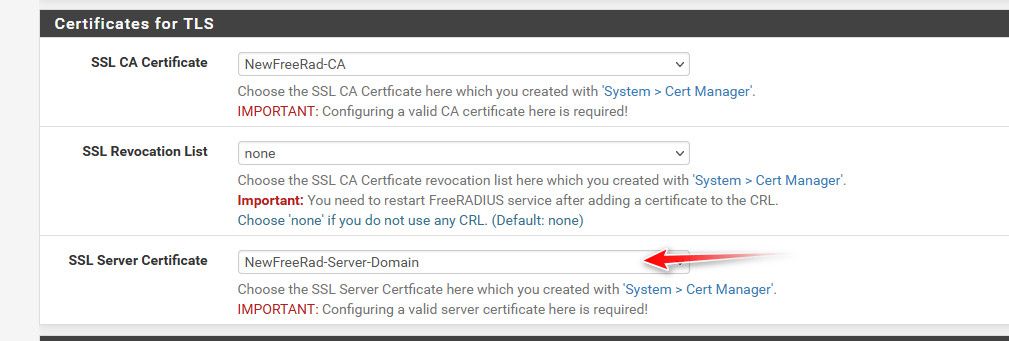
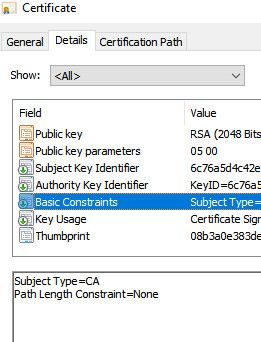
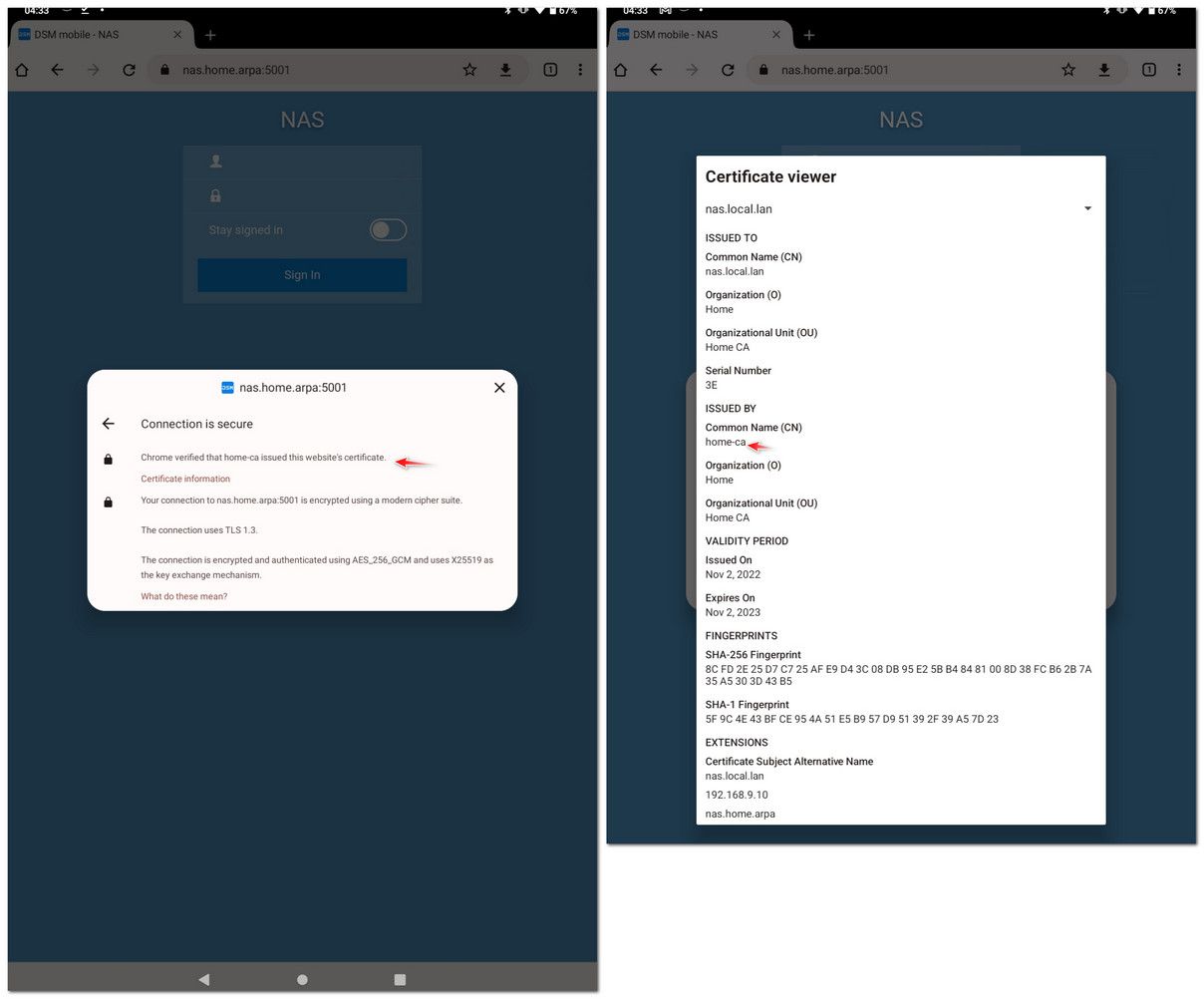
@furom on my tablet I don't have to do anything special with the cert, I mean a CA created in pfsense would already have the basic constraint of CA already set
I am able to install just from the download folder - I emailed myself the CA.crt - then just installed it, and there it is listed.
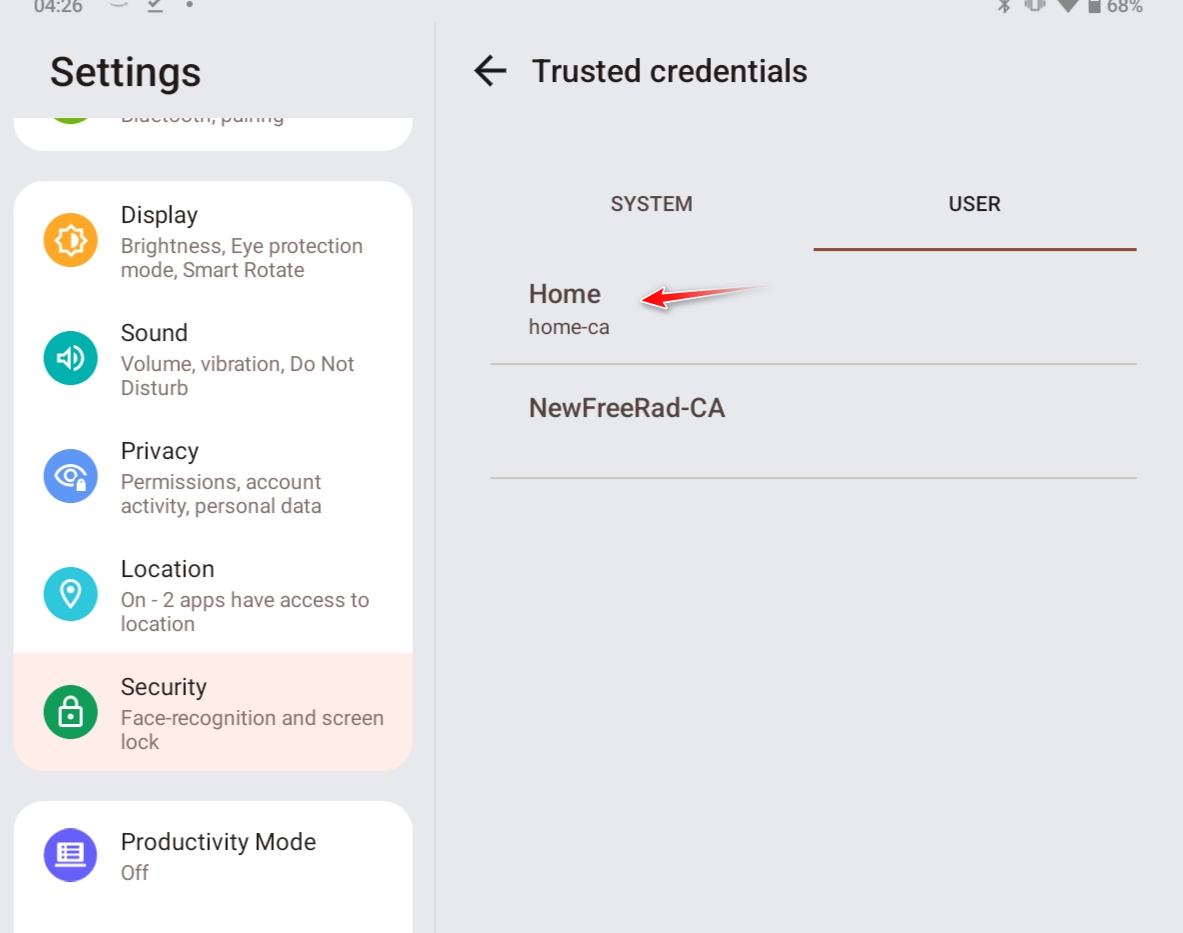
edit: you can then see the tablet trusts this certs signed by this CA
-
@johnpoz Well then, if basic constrains is already included... :/
-
@furom but possible android 13 is looking for it elsewhere? Not really an android guy, but you should be able to check on your tablet if it trusts this CA, you should see it in your user section of trusted CAs - like the 2 I have installed.
I have a few different CAs, one for home that I create certs for stuff like my nas, my printer, my pfsense gui, my switches gui's etc..
I also have another one for openvpn, and then the one I created for freerad use.
If you don't see it there - then yeah its highly unlikely that it would trust the cert your freerad server presents, etc.
But its possible wifi stuff using its own settings? Like said not an android guy, notice it doesn't show my homeca as possible ca for my wireless?
So for wireless you might have to install the CA under the wireless settings, but I would think if you have it installed and shown under your user for the system that using the use system certs should work.
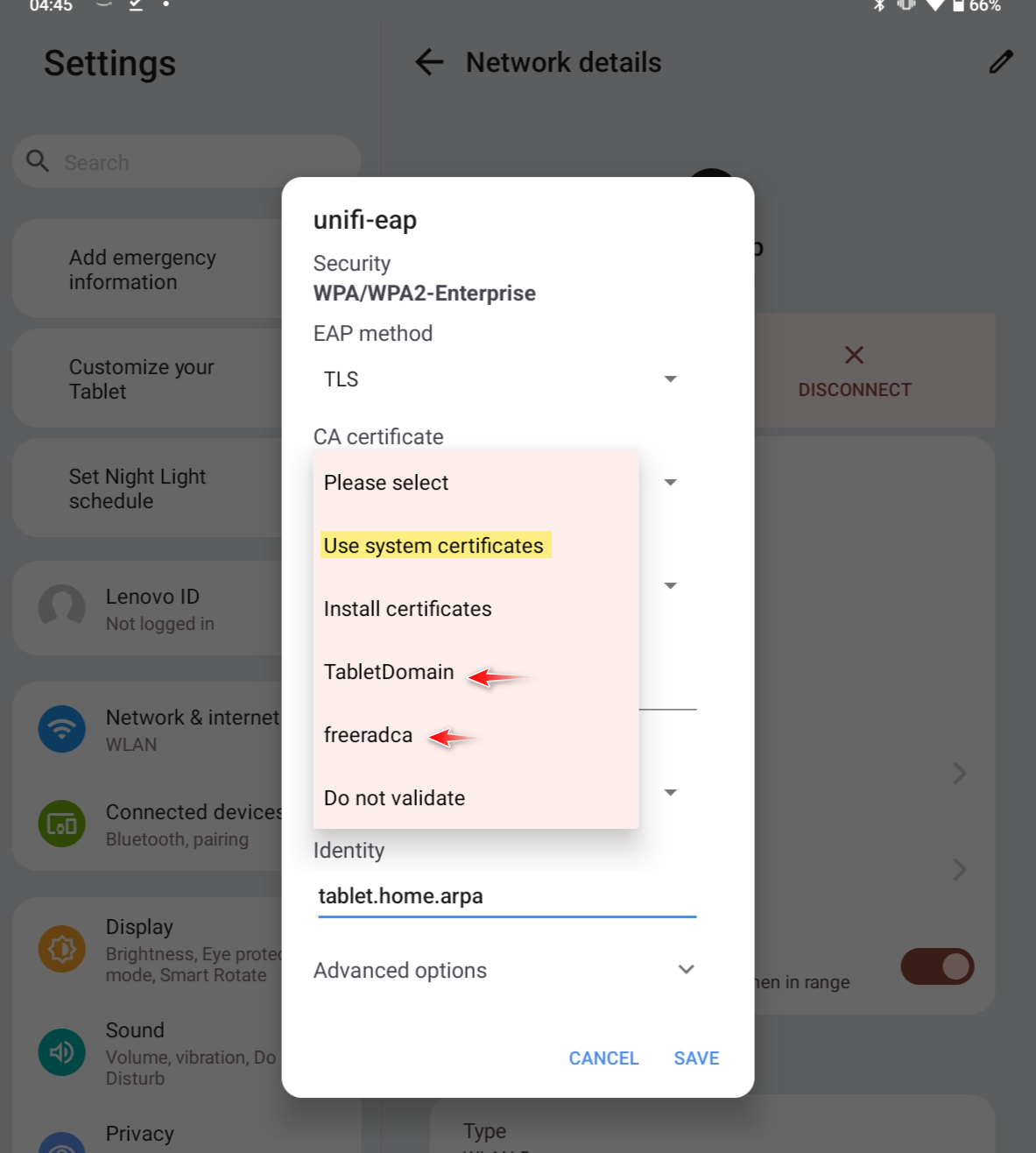
I tried using "system" in wifi and didn't work - I have to select the CA I installed using wifi