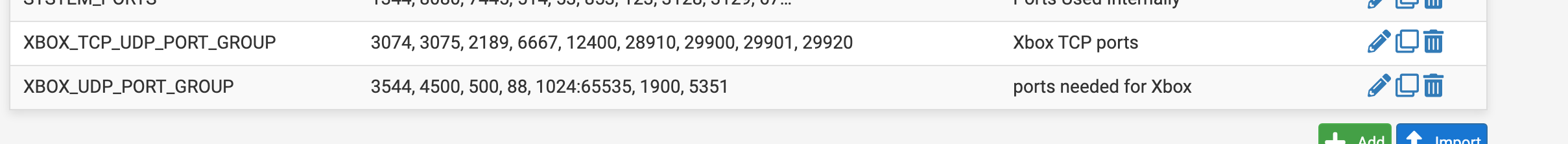
Nintendo Switch connection issue Error code
-
@JonathanLee What you gain with using a PAC file is the possibility to bypass destinations by domains, regex..
You don't need to know the destination address as you would need to know when using transparent proxy.
Browsers also have a builtin option to make use of that, that you can use with or without a .pac file.
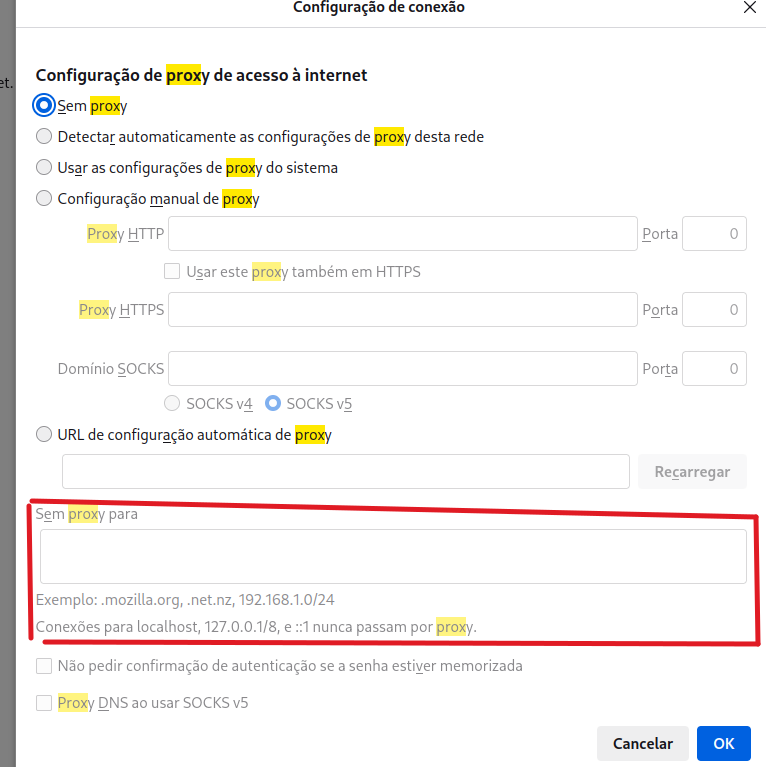
So, as I see it, Nintendo switch proxy implementation is poor, I mean, only an IP and address, port and a switch ON/OFF ?
-
The usage of Squid (to no ones surprise) is now deprecated.
https://www.netgate.com/blog/deprecation-of-squid-add-on-package-for-pfsense-software
-
@michmoor said in Nintendo Switch connection issue Error code:
The usage of Squid (to no ones surprise) is now deprecated.
https://www.netgate.com/blog/deprecation-of-squid-add-on-package-for-pfsense-software
I can't say I'm surprised indeed.. Thanks for the info.
-
What is an alternative ???
Dang looks like I will have to stay with 23.09 until 2100 hardware twightlighted. I spent years getting this to actually work =(, it's just sad to me. :(
-
This post is deleted! -
What is the next official Netgate product that will continue to support a proxy with SSL intercept that can be purchased? Now that this is being twightlighted?
What version should I upgrade too for proxy cacheing abilities? I have a SG-2100 currently. Should users move to Palo Alto?
-
@JonathanLee There is nothing after Squid. Squid is really the only Forward proxy application that i know of. Your alternatives are going to be DNS blocklist or DNS server that can handle content filtering(OpenDNS or NextDNS).
Within my home, ive loaded up AdGuard within a container and pointed my "Family_VLAN" toward it. AdGuard has features to block content of various degrees and you can also upload blocklists. So its handy and arguably better than Squid.Squid is just a very unsupported project without a lot of updated features and lots of CVEs. Its long past its prime and it had a good run. Im sad to see it go but there just isnt a better or any OSS alternative.
-
@JonathanLee said in Nintendo Switch connection issue Error code:
Should users move to Palo Alto?
Palos/Fortinet/Ciscos all have heavy subscription fees to use their products. Assuming you can get a PA-440 with a home lab license for a "cheap" price it's going to be very costly.
I suspect that if there are folks out there that need to MITM traffic flows they are probably within an enterprise or Financial space or even military and could well afford the pricey security vendors. I can't say what you should do but if you really need that feature set and you are willing to pay then the options you have are vast.
It all comes down to what your security/network requirements are. -
if (! isResolvable(host)) {
return "PROXY proxy.example.com:3128";
}In the mean time I wonder if this would help with the WPAD.
Ref:
https://wiki.squid-cache.org/KnowledgeBase/ProxyPacSlowSquid's website states there next upgrade to resolve bugs every 2 years.
"Major stable releases follow a two-year schedule. Beta branches are spawned six months before the corresponding major stable release."
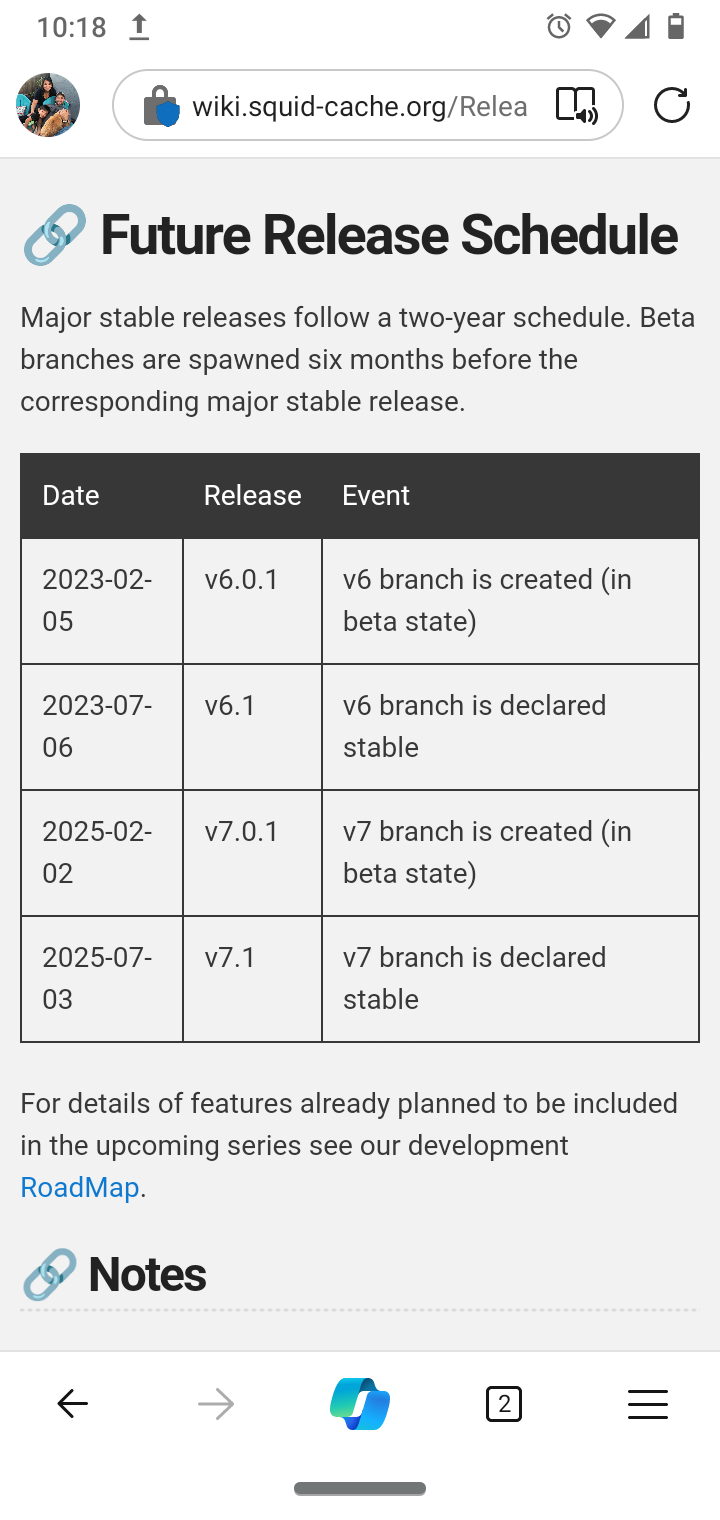
So Feb 2025 is when the security issues will be resolved?Good run it's still running great. I am not at all concerned with the security issues from it. I am going to keep running it personally. It's million times better from day one of setting up my 2100. It's like a dream to see it run now on my system. I have one issue with a time out connection.
I actually feel like I have control of my privacy. I have asked many times per CCPA for sites to stop tracking me. Again they don't, this gave me the ability to force privacy with block lists. I am to invested in the configurations and stuff with it to give up on it. Yes it has some bugs like anything.
I keep thinking about Microsofts enteral blue bug. It's been abused over and over and patched and reopened for NSA tools and released.
pfSense and Squid provided me everything I needed in a firewall. So much so I would buy a new Netgate if it had the ability to run it still. It's perfect. Sure I block some advertising abuse from tracking us, that's them not following CCPA and GDPR laws.
I am on a tangent sorry because I personally Iove Squid Squidguard and lightsquid.
There run is not over yet... Squid keeps on protecting my GDPR and CCPA rights. It really took the Zoo/panopticon feeling out of advertising company abuses.
Again for the average users it's a living nightmare to configure, something that requires a cyber security degree and years of configuration changes after with a team of open source community members coding and searching for any issue.
It really was an amazing product.
-
@JonathanLee
IMO, you are taking a huge gamble running an insecure application.
https://www.theregister.com/2023/10/13/squid_proxy_bugs_remain_unfixedNo one on the development side of the Squid project is taking ownership of these vulnerabilities. There is no roadmap to fix.
"He also acknowledged that the Squid proxy's maintainers – like most open source developers – are largely volunteers and may not have the support necessary to quickly fix all these problems.
"The Squid Team have been helpful and supportive during the process of reporting these issues," Rogers conceded. **"However, they are effectively understaffed, and simply do not have the resources to fix the discovered issues. Hammering them with demands to fix the issues won't get far."
As Netgate suggested, i would highly advise you to not use it anymore. If you really need more control over devices that are other methods availble today with less overhead.
-
@michmoor I am a computer science student, after I take a C++ class and php class I can start helping fix the issues. I just don't know how to debug something like this yet. I also will learn that soon, I think GitHub has virtual instances where it's a VM. I have to learn about better GitHub use also in class soon.
-
@JonathanLee
What I don’t understand is why isn’t this a project that Netgate supports? They advertise a free project in all marketing. They fully utilize an open source tool to make money . IMO, Netgate should have a role in fixing this or offering an alternativehttps://www.netgate.com/pfsense-plus-applications/content-filtering
-
https://docs.opnsense.org/manual/proxy.html
Opensense is another alternative I can see once Squid is removed. However I really don't want to go to a new vendor. I bet Netgate will find a great SSL intercept web cache replacement in the end.
-
@michmoor I admit Squid was a reason I went with Netgate also the great community.
-
Not saying a switch of vendors is appropriate BUT...the ability to offer per network blocklist is available.
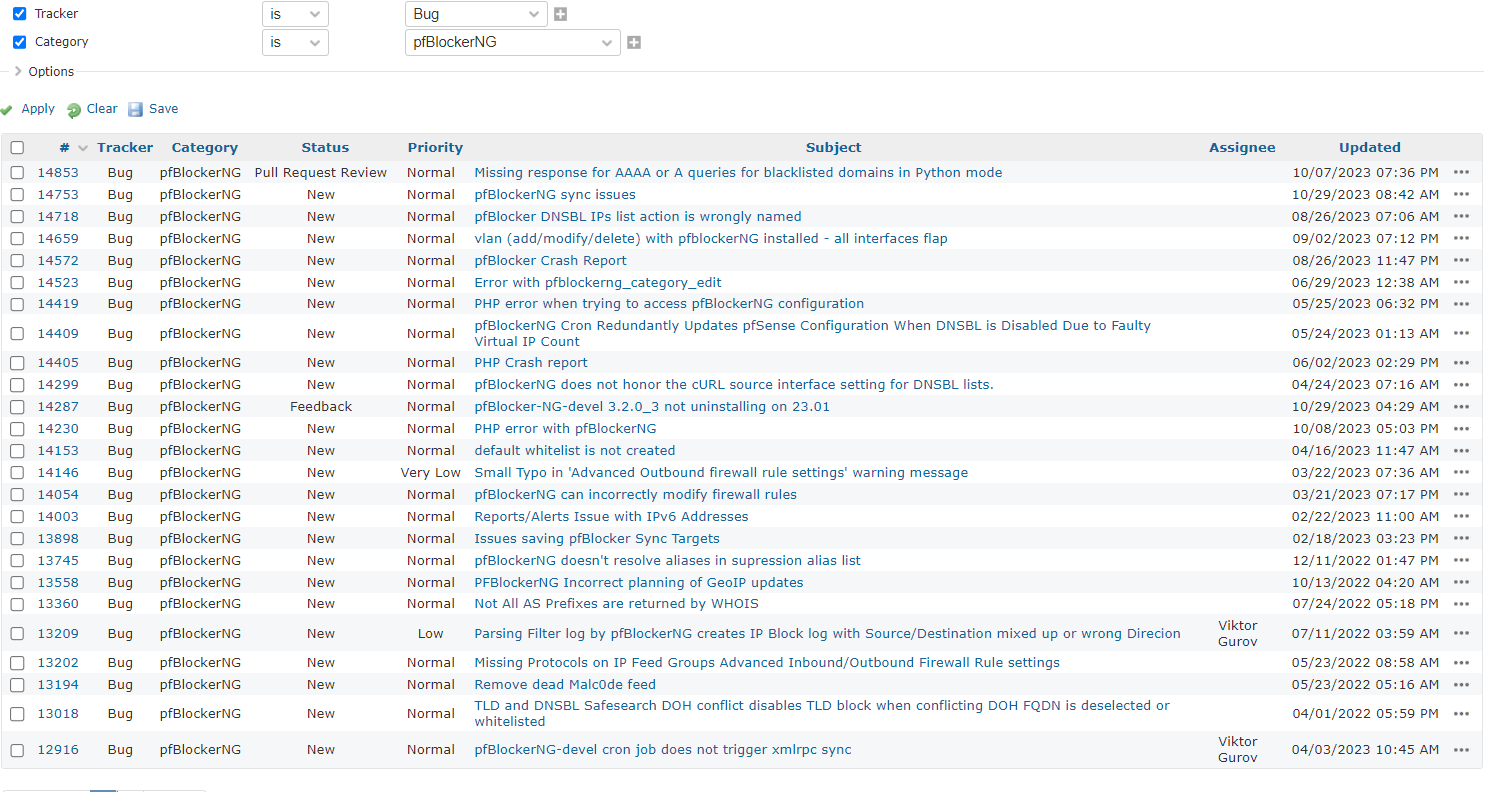
Looks like they paywall that feature. https://docs.opnsense.org/vendor/deciso/extended_dnsbl.htmlNevertheless, its possible but pfBlocker only has a single maintainer and we havent had a package update in quite a while. If you check the redmines, there are quite a few feature requests open and unassigned.
I did call it with Squid and im calling it with pfBlockerNG. The lack of any ticket updates on a package is usually a bad sign that the maintainer has left. I told everyone that this /409 issue with Squid breaks the package and a pretty detailed write up on the redmine along with a potential solution but no one from Netgate picked it up.
The pattern is repeated again, this time with pfblocker. I hope im wrong but with a single maintainer and unassigned redmines, the writing is on the wall for the package.Features requests pile up...
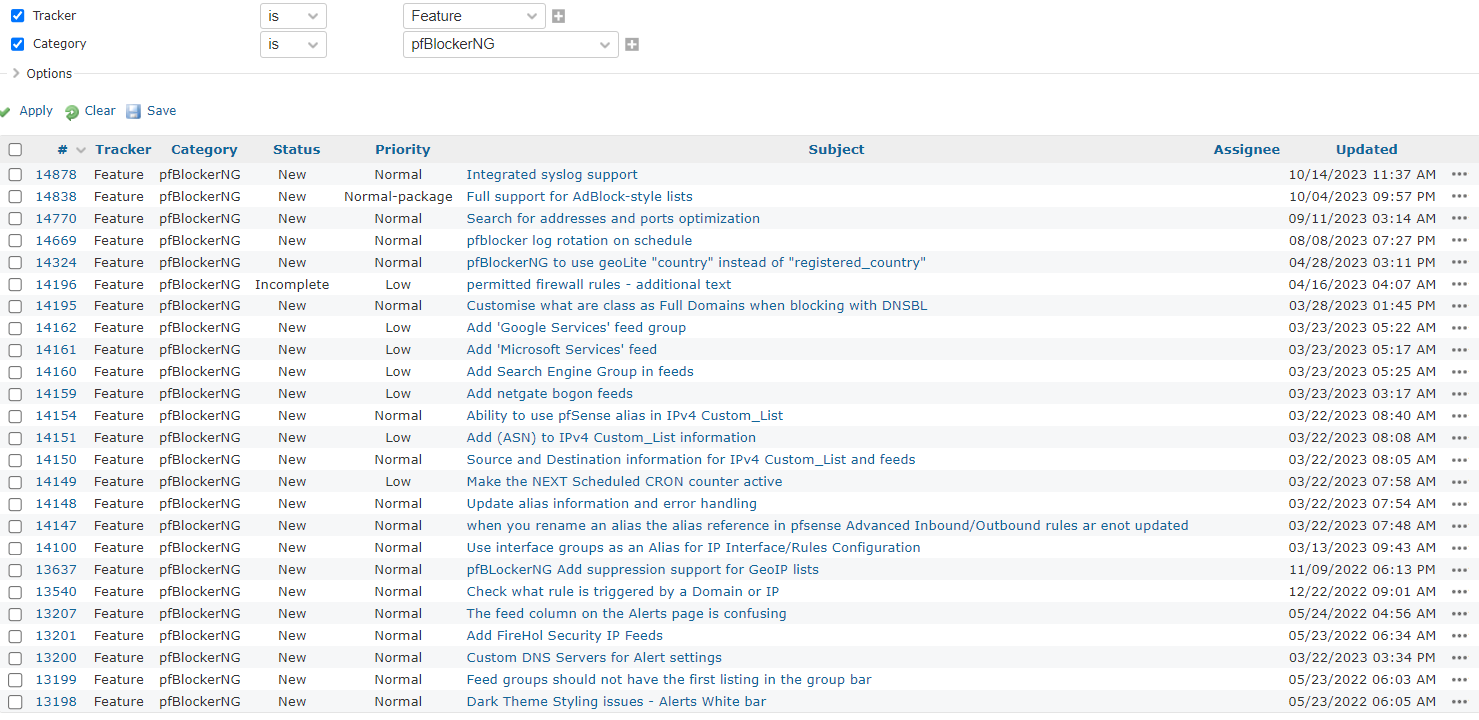
Bug tickets pile up...
-
@michmoor I personally never used pfblocking because of DoH DoT and HTTPS3 QUIC. It was changing every 3 months with ways around DNS based filtering. I use to work with government clearances so I have a target on my back for anything at home. It was so bad one year I couldn't get through a single Netflix film without getting hit with denial of service attacks. I found a solution.
I use the SG-2100 internal wifi card for the Nintendo switch on a separate unfiltered WiFi. And all my my university stuff and home NAS sits on the RJ45 based external AP with a different subnet.
With AppID and the full text rules I could see the Nintendo switch doing Curl all the time on my network, now it can do it all day on a separate subnet and never see my firewalles LAN.
-
@JonathanLee 1. Nintendo Switch's upload test cannot function through Squid Proxy correctly because it uses a combination of DNS over HTTPS, your DNS, NTP over HTTPS and other security measures. It won't even allow you to use DNS that goes out of a different gateway, or do anything asymmetrical in general unless it is an HTTP proxy. Because HTTP is being proxied, if other services in your house are also being proxied, it can interfere with the Nintendo's Port 80 services.
I have found that many services do not operate as they appear in pfTop. For instance, if you block port 80, the Nintendo may not allow you to do anything, even if you aren't supposedly using a service related to port 80 to begin with; cloud services are weird, and contain a conflaguration of services going to multiple ports, even via 1 IP address over port 443 (NTP, DNS etc).
-
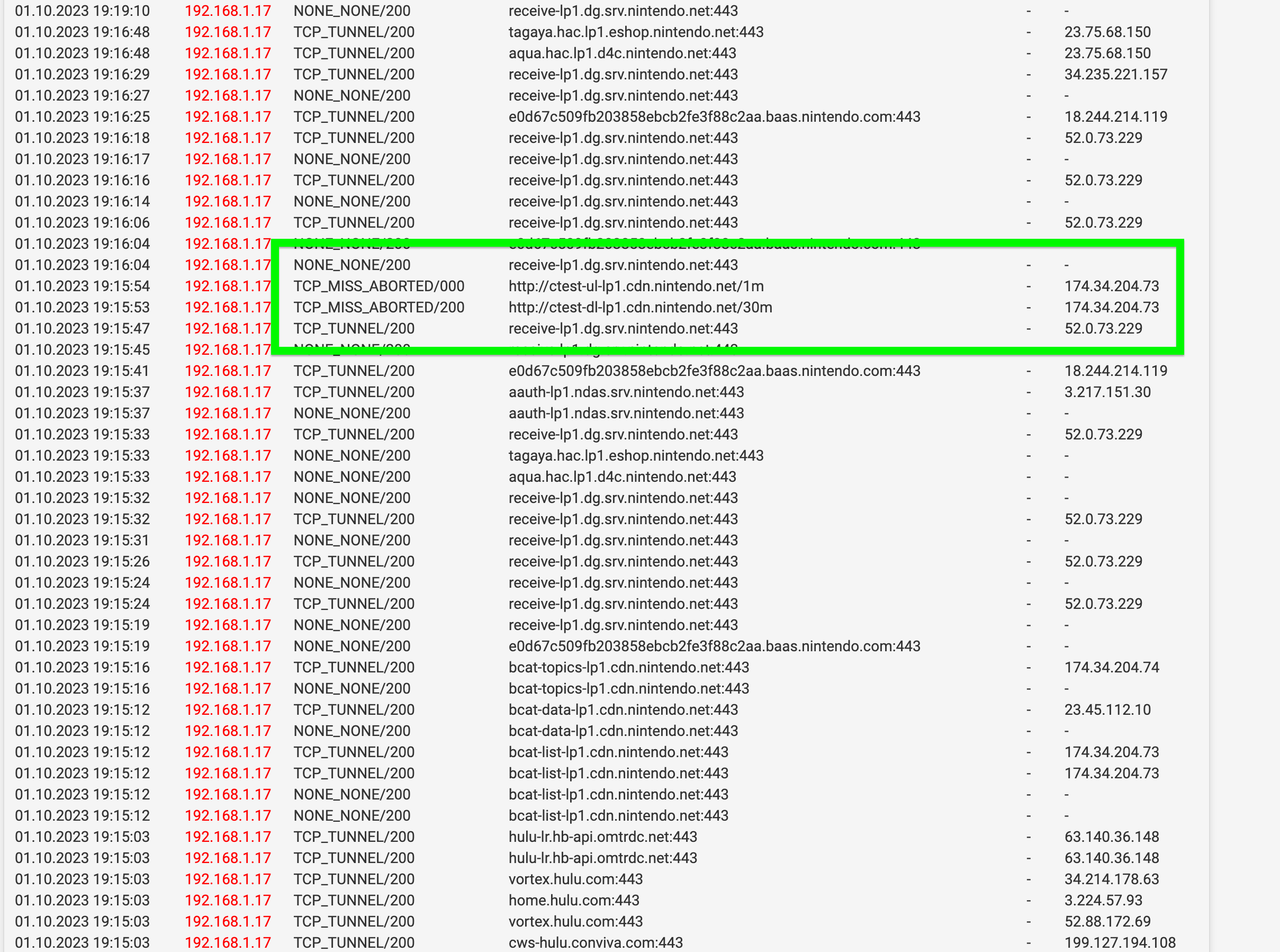
I have never seen the Nintendo Switch use cURL, however it does so much stuff that avoids firewall detection (UDP over HTTP and HTTPS, conficker, sharing data between UDP and HTTP connections) that I don't have doubts. I would be extremely suspicious of Squid Proxy.
-
The Stun Traversal Utility may be entirely dependent on the game you play, however, I have never seen STUN used by the Nintendo Switch. It is likely your Xbox or a Windows PC making those requests.
-
@mcury , I have found that I can force the Nintendo Switch to only use source Ports 49152-65535 on the WAN after NAT, outbound, and can additionally force it to only communicate with players that also are using the same ephemeral port range. And have found it safe to port forward all of those ephemeral ports directly to the Nintendo Switch. I cannot do the same with TCP, but can restrict the destination ports to 80 and 443, and the source ports to 1024-65535 on outbound WAN. Additionally, I have found it necessary to port forward and/or static NAT 10024:10025, 33334:33335, which seem to be Nintendo's connection test UDP ports, and are required to be forwarded for the system's nat to actually count as "open".
Rejecting all other UDP ports other than DNS seems to be safe, and I have additionally successfully created a custom NAT only allowing the Nintendo the same source and destination ephemeral ports over UDP, to complement the Layer 3 floating rules. I have found it useful to create these rules as outbound pass rules, WITH fqcodel, and FIFO.
Currently my net.inet.ip.dummynet.tick_delta_sum counter slowly accumulates to -900, rendering games like smash ultimate unplayable if fqcodel is limiting UDP. And have to reset every 40 minutes of playtime to reset the dummynet timer. I have found that the round-robin nature of the Quantum parameter in FQ-Codel causes out of order UDP and TCP packets if set too low, and instead of a 300 Quantum like recommended by some people online (who can actually saturate their connections), I recommend a quantum above 18000 to never see that behavior, or using fqcodel only for TCP, and instead FIFO for UDP.
I have also found it best to:
-
use a Queue of 50 on fqcodel limiters and children, even over fiber (unlike people's recommendations) because of how little bandwidth is used by the Nintendo, and because dummynet is designed by default to use a queue length of 50.
-Today I iperfed a cloud server to see the behavior of the dummynet timer while saturated with UDP, and the timer does not improve. However, when saturated with TCP from waveform's bufferbloat test, the timer magically fixes itself and floats around zero. I think this has to do with dummynet being able to apply timestamps to TCP packets, but maybe not all UDP packets (or something). -
It is also highly recommended to set your localhost MTU to 1500 while using anything related to dummynet, and also disabling all offloading. It isn't fq codel that breaks, but instead dummynet, Unbound/other localhost connections, services like squid, because localhost's MTU is defacto 16k bytes. The problems are even more crazy when your ISP assigns your public IP over VLAN 0 like mine. Chances are, their stupid default router also has a localhost MTU of 16k.
-
Use a lower number of RX and TX descriptors, like 256 and try using lower pipe byte limits in dummynet while using fqcodel; sysctl net.inet.ip.dummynet.pipe_byte_limit, and set net.inet.ip.dummynet.expire=0 to avoid dropping dummynet pipes for idle TCP connections that haven't received a rexmit or keep alive probe, otherwise services/games can freak out when their pipe "lazily" collapses. Someone online said you should try setting the byte queue limit equal to your number of descriptors, multiplied by your MTU. net.inet.ip.dummynet.pipe_byte_limit=768000, aka 256x2x1500.
FiFo limiting for UDP is a very nice feature instead of fqcodel, however, if UDP is built on an applications TCP/TLS/HTTPS Connection, and the TCP is being Control Delayed, it is an issue, one I have solved by blocking all UDP on ports 80 and 443 (gRPC, which the Nintendo Switch uses in addition to Akamai is weird). Doing so can break some cloud services but can make some games work much better.
Any positive benefits I have gained from Squid, I have also seen from Synproxying port 80, and DNS sinkholing edgesuite.net and edgekey.net. I don't know why, but their Akamai servers are very brutal to some games. Unfortunately if you block Akamai, you cannot play some games or even use pokemon home, even if they seem to be connecting to Amazon Servers. I have found that instead of using Akamai servers, the Nintendo will instead use Cloudfront servers in some games, which are likely less overloaded load balancers.
Sorry I do not have any technical advice using tools. I am somewhat new to networking, and rather brute force everything. I have been trying different combinations and permutations of settings and router programs while I play every day for a couple of years now (frustrated the whole time when fqcodel would work great, but then stop.) I have TCP dumped the Switch a few times, and found flow control multicast packets, and that their servers do not support ECN. Their USB ethernet dongles are pretty garbage, and their USB 3.0 is artificially limited to USB 2.0 speeds, and they only "officially" support 100BASE-TX to begin with (no clue if that is full or half duplex, but I'd leave it on auto-negotiate as it may vary depending on the applicaiton.) I have found it helpful to disable flow control on every interface, and block their weird flow control servers by simply not NATtting to them. Here is a list of servers I allow via NAT while playing Smash and don't NAT any others:
Allow, by only NATting to these hosts on 443: <name>Nintendo_TCP</name>
<type>host</type>
<address>54.165.43.236 ec2-54-165-43-236.compute-1.amazonaws.com 44.228.255.28 ec2-44-228-255-28.us-west-2.compute.amazonaws.com 54.164.48.41 ec2-54-164-48-41.compute-1.amazonaws.com 54.234.230.189 ec2-54-234-230-189.compute-1.amazonaws.com 3.87.70.104 ec2-3-87-70-104.compute-1.amazonaws.com 3.171.168.228 3.85.164.15 ec2-3-85-164-15.compute-1.amazonaws.com ec2-54-146-70-182.compute-1.amazonaws.com 54.146.70.182 54.87.47.225 ec2-54-87-47-225.compute-1.amazonaws.com 54.25.120.81 nintendo.net 100.24.27.200 ec2-100-24-27-200.compute-1.amazonaws.com 35.83.110.155 ec2-35-83-110-155.us-west-2.compute.amazonaws.com 44.194.110.147 ec2-44-194-110-147.compute-1.amazonaws.com 44.212.21.196 ec2-44-212-21-196.compute-1.amazonaws.com 35.83.110.155 ec2-35-83-110-155.us-west-2.compute.amazonaws.com 18.238.171.73 18.238.171.72 18.238.171.78</address>fqcodel and fifo respectively probably work better over wifi because the wifi chip isn't necessarily constrained to 100Base-TX lan driver firmware, and while there is a chip that can technically report as 1000Base-T, it still has a tendency to repeatedly send flow control frames, even when limited to less than 100mbps. (lame)
I have ran suricata against the Nintendo quite a bit and haven't seen much of concern other than conficker, and google quic packets plus pfSense zcolo cloud packets flowing across the wrong threads in Suricata Worker Mode.
Some sysctls help a lot. And I have found it helpful to disable the scrub's IP random number assignment because of random id collisions, and disable ecn max retries because of no support by some players routers and the servers in general.
-
-
Thanks for the reply,
I block all dns over https. I do proxy both http and https. I also use dns over tls it worked fine except some games.
My solution to this in the end was simple I have a separate guest network different broadcast domain and private network that is blocked from my private secure system.
AppID did see many curls from Nintendo. That is interesting right as this was a new out of the box device.
My solution to this was a complete separate network for it. Nintendo can curl all it wants and do what it wants and my network is safe. When curls are running for no reason it’s a red flag.
Thank you for your reply. I trust Squid it has been in use for many years now.
-
@JonathanLee said in Nintendo Switch connection issue Error code:
running for no reason
Just because you don't understand or agree with reason, doesn't mean there isn't one ;)
-