Port Forward over VPN not working....
-
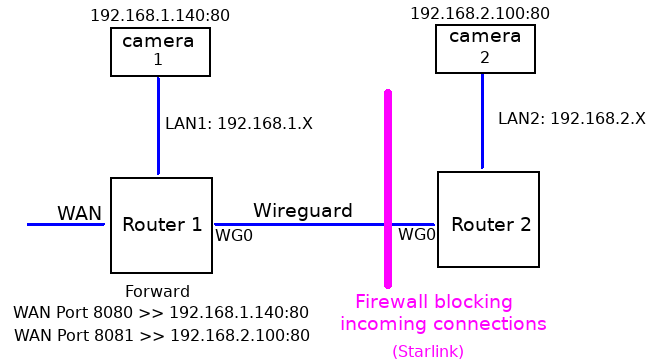
Wireguard is site to site... I can reach both cameras from either LAN.
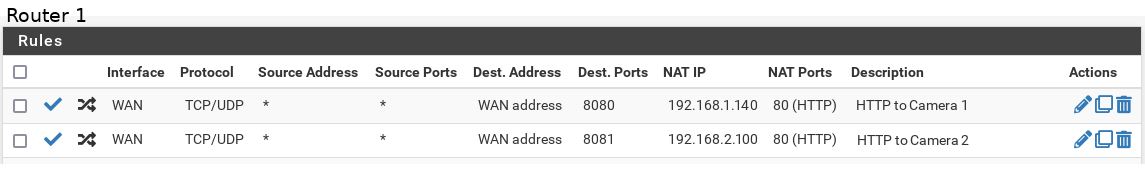
I set up Port Forwarding as shown w/ autogenerated firewall rules set to the top.
From the outside world, I can get to camera 1 no problems. Camera 2 is unreachable.
But, from inside either LAN, both cameras are reachable.
What is the key to getting Camera 2 seen through a forward and then through a VPN?
-
@JustAnotherUser
Generally it's not a good idea to expose the cameras to the internet. You should better consider to use a VPN to connect to them.If you want to go over WAN anyway, assign an interface to the wg instance and enable it at site 2. This brings up a new firewall rule tab for it then.
Now go to the "Wireguard" tab, edit the existing rules and change the interface to the new one.There must no pass rule be left on the Wireguard tab, which matches the forwarded traffic!
-
This post is deleted! -
You should better consider to use a VPN to connect to them.
The people who need to reach camera2 are all windows/tiktok users. They don't care about security so, I pretty much don't care about their security. Once I get this working I'm going to setup rules to keep them out of the rest of the network.
I REALLY don't want to have to administer their certificates and VPN connections.
Which is why I'm doing it this way.
If you want to go over WAN anyway, assign an interface to the wg instance and enable it at site 2. This brings up a new firewall rule tab for it then.
Now go to the "Wireguard" tab, edit the existing rules and change the interface to the new one.I'm not sure what you mean by your last sentence but, I've done the rest.
-
@JustAnotherUser said in Port Forward over VPN not working....:
If you want to go over WAN anyway, assign an interface to the wg instance and enable it at site 2. This brings up a new firewall rule tab for it then.
Now go to the "Wireguard" tab, edit the existing rules and change the interface to the new one.I'm not sure what you mean by your last sentence but, I've done the rest.
You mean, changing the interface in the filter rule?
In Firewall > Rules you will see a tab called "Wireguard". pfSense might have created a rule on this tab automatically, when you set up the Wireguard tunnel.
So go to this tab and edit the existing rule and change the interface from "Wireguard" to the interface, which you have assigned to the Wireguard instance before.
Then the rule disappears from the Wireguard tab and appear on the new interface tab.Also in the WG settings on router 2 you have to change the "allowed IPs" to 0.0.0.0/0 to accept public forwarded traffic.