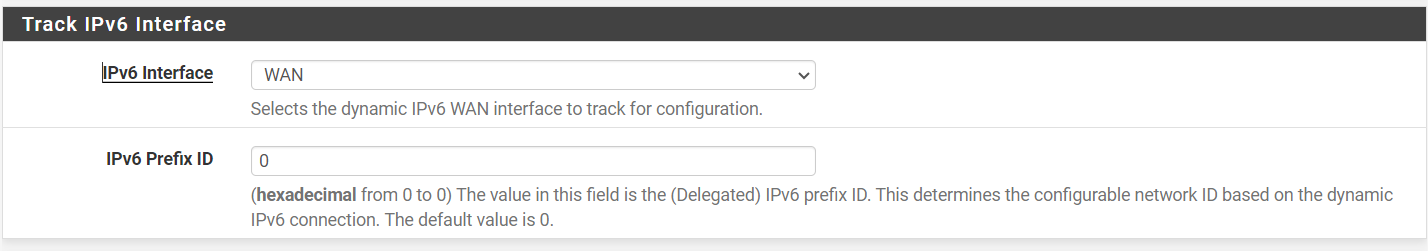
Configure IPv6 on multiple LAN interfaces
-
@DrPhil prefixes can be a bit harder to spot with IPv6.. do you mind posting what you got on your lan and dmz? You can PM them too me.
Just PMed those over to you.
How are you trying to hand your clients on your dmz IPv6, dhcpv6? just SLAAC?
dhcpv6.
-
@DrPhil said in Configure IPv6 on multiple LAN interfaces:
Just PMed those over to you.
I don't see anything.
Just post it in the thread, so it will be available to others.
-
@DrPhil said in Configure IPv6 on multiple LAN interfaces:
Just PMed those over to you.
Yeah those are not right if they have a /128 on them..
@JKnott he sent me the IPs he has on lan and dmz, but they show a /128
-
@johnpoz said in Configure IPv6 on multiple LAN interfaces:
he sent me the IPs he has on lan and dmz, but they show a /128
That's fine for the WAN, but not a prefix. I have a /128 for my WAN too.
I guess he sent the file to you but not me.
-
@JKnott no he didn't send any file, just the ips with /128 on them.
Those sure can not work for a lan side network - sure as a transit on the wan no problem..
-
Just to clarify, what I sent to @johnpoz were not prefixes but v6 IPs that clients on my LAN and DMZ got assigned by the respective DHCPv6 servers.
Here is the output line from
ip addresson each network (for a single client).
On LAN (client 1)
inet6 2600:4040:a30c:8801::2d83/128 scope global dynamicOn DMZ (client2)
inet6 2600:4040:a30c:8801::23ec/128 scope globalI am just reading the first 16 hex characters and calling it the same prefix (not sure that's a technically sound conclusion).
-
@DrPhil they are not the "same" prefix with the /128 on them..
if they had a /64 on them - then they would yeah be the same network/prefix
a /128 in IPv6 land, is the same as a /32 in IPv4.. Its a single IP.. There is no "network" if you will. Its just that IP..
-
a /128 in IPv6 land, is the same as a /32 in IPv4.. Its a single IP.. There is no "network" if you will. Its just that IP..
That much I figured. What I provided are IP addresses assigned to individual client machines (one on each network).
I am looking at the first 16 characters on each:
2600:4040:a30c:8801They're identical. Which is why I was saying that both networks are getting the same prefix (I don't have any confidence in my observation though).
-
@DrPhil said in Configure IPv6 on multiple LAN interfaces:
hey're identical. Which is why I was saying that both networks are getting the same prefix
They are not on the same network, because with a /128 there is no network.
Like saying 192.168.0.1/32 is on the same network as 192.168.0.2/32 - there is no network with a /128
Now if the mask was say /30 then those 192.168.0.x address would be on the same network, since /30 would be
192.168.0.0 - 192.168.0.3Where .0 is the wire, and 3 is the broadcast for that network.
if your client shows /128 on it - there is no "network"
-
@johnpoz said in Configure IPv6 on multiple LAN interfaces:
sure as a transit on the wan no problem
Actually, it's not a transit. It's just a target for VPNs, etc.. The transit network is through the link local address.
-
@JKnott said in Configure IPv6 on multiple LAN interfaces:
he transit network is through the link local address.
ok - its still an IP on the transit connection, be it you want to call it a loopback or whatever..
-
@DrPhil said in Configure IPv6 on multiple LAN interfaces:
I am looking at the first 16 characters on each:
2600:4040:a30c:8801
They're identical. Which is why I was saying that both networks are getting the same prefix (I don't have any confidence in my observation though).With a /128, the entire address is prefix. With IPv6, the number after the / tells how many of the address bits are prefix, with the remainder being the host portion. Typically, a LAN would have a /64 prefix, the ISP can provide a range of sizes, typically /56 or /48 and a point to point link, such as a VPN can be a /127
Anyway, I asked for the capture file, so that I could see what size prefix you're asking for and getting back.
-
@johnpoz said in Configure IPv6 on multiple LAN interfaces:
ok - its still an IP on the transit connection, be it you want to call it a loopback or whatever..
I think you're still stuck on the IPv4 way of thinking. It's just an address that identifies an interface, nothing more. Loop back is ::1. You don't have a block of loopback addresses, as on IPv4. All traffic from the WAN goes through the link local address and you don't even need a global WAN address. This is why, in another thread, I mentioned the LAN interface IPv6 address could be used for a VPN, when a WAN address isn't available. The packet comes in via the link local address and pfSense sees it's for one of it's own interfaces and handles it appropriately. The link local is usually used for routing, as a router only has to know how to reach the next hop and that can be specified with the link local address or even just the interface name, on a point to point link.
-
Here's what I got from the packet capture.
23:43:31.108177 IP6 fe80::290:bfe:fe8c:d94a.546 > ff02::1:2.547: UDP, length 68 23:43:31.114808 IP6 fe80::f6b5:2ff3:fe05:71bc.547 > fe80::290:bfe:fe8c:d94a.546: UDP, length 160 23:43:32.110114 IP6 fe80::290:bfe:fe8c:d94a.546 > ff02::1:2.547: UDP, length 133 23:43:32.116112 IP6 fe80::f6b5:2ff3:fe05:71bc.547 > fe80::290:bfe:fe8c:d94a.546: UDP, length 160 23:43:32.177601 IP6 fe80::290:bfe:fe8c:d94a.546 > ff02::1:2.547: UDP, length 52 23:43:32.188806 IP6 fe80::f6b5:2ff3:fe05:71bc.547 > fe80::290:bfe:fe8c:d94a.546: UDP, length 115 23:43:33.213495 IP6 fe80::290:bfe:fe8c:d94a.546 > ff02::1:2.547: UDP, length 52 23:43:33.227805 IP6 fe80::f6b5:2ff3:fe05:71bc.547 > fe80::290:bfe:fe8c:d94a.546: UDP, length 115 23:43:35.178384 IP6 fe80::290:bfe:fe8c:d94a.546 > ff02::1:2.547: UDP, length 52 23:43:35.184419 IP6 fe80::f6b5:2ff3:fe05:71bc.547 > fe80::290:bfe:fe8c:d94a.546: UDP, length 115 23:43:39.142830 IP6 fe80::290:bfe:fe8c:d94a.546 > ff02::1:2.547: UDP, length 52 23:43:39.154548 IP6 fe80::f6b5:2ff3:fe05:71bc.547 > fe80::290:bfe:fe8c:d94a.546: UDP, length 115 23:43:46.871171 IP6 fe80::290:bfe:fe8c:d94a.546 > ff02::1:2.547: UDP, length 52 23:43:46.886915 IP6 fe80::f6b5:2ff3:fe05:71bc.547 > fe80::290:bfe:fe8c:d94a.546: UDP, length 115 23:44:01.359117 IP6 fe80::290:bfe:fe8c:d94a.546 > ff02::1:2.547: UDP, length 52 23:44:01.368737 IP6 fe80::f6b5:2ff3:fe05:71bc.547 > fe80::290:bfe:fe8c:d94a.546: UDP, length 115 23:44:30.227734 IP6 fe80::290:bfe:fe8c:d94a.546 > ff02::1:2.547: UDP, length 52 23:44:30.237568 IP6 fe80::f6b5:2ff3:fe05:71bc.547 > fe80::290:bfe:fe8c:d94a.546: UDP, length 115 23:45:27.693592 IP6 fe80::290:bfe:fe8c:d94a.546 > ff02::1:2.547: UDP, length 52 23:45:27.699768 IP6 fe80::f6b5:2ff3:fe05:71bc.547 > fe80::290:bfe:fe8c:d94a.546: UDP, length 115 23:47:17.062566 IP6 fe80::290:bfe:fe8c:d94a.546 > ff02::1:2.547: UDP, length 52 23:47:17.070276 IP6 fe80::f6b5:2ff3:fe05:71bc.547 > fe80::290:bfe:fe8c:d94a.546: UDP, length 115 23:49:26.790775 IP6 fe80::290:bfe:fe8c:d94a.546 > ff02::1:2.547: UDP, length 52 23:49:26.801422 IP6 fe80::f6b5:2ff3:fe05:71bc.547 > fe80::290:bfe:fe8c:d94a.546: UDP, length 115 -
No, what I need is the actual capture file, which I can then examine with Wireshark. Here's the sort of thing I'd be able to find:
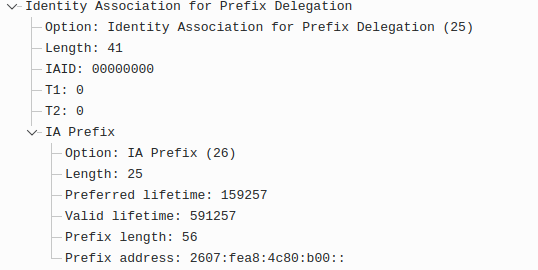
This shows I am requesting a /56 prefix and the prefix I was asking for. I'd be able to see similar for the reply from the ISP.
-
@DrPhil yeah vis posting what is in the window, download the capture and post the pcap file here.
-
I downloaded the pcap file, and ran the output through tshark. (I didn't want to post the whole pcap here for privacy reasons - fear of the unknown).
From the tshark output, I have copied below the relevant sections of two packets - a request from my router and a reply from the ISP server. Based on my layperson reading of this, it seems like pfsense is requesting a /56 prefix (even though in my settings I said /60). And that the ISP is in fact giving a /56 prefix.
Please take a look and let me know if you would like to see any other sections or packets.
DHCPv6 Message type: Request (3) Transaction ID: 0x996ddc Client Identifier Option: Client Identifier (1) Length: 14 DUID: 000100012ceadexxxxxxxxxxxxxx DUID Type: link-layer address plus time (1) Hardware type: Ethernet (1) DUID Time: Nov 17, 2023 21:31:59.000000000 EST Link-layer address: 00:90:0b:xx:xx:xx Server Identifier Option: Server Identifier (2) Length: 26 DUID: 00020000058366343a62353a32663a30353axxxxxxxxxxxxxxxx DUID Type: assigned by vendor based on Enterprise number (2) Enterprise ID: Juniper Networks/Funk Software (1411) Identifier: 66343a62353a32663a30353axxxxxxxxxxxxxxxx Identity Association for Non-temporary Address Option: Identity Association for Non-temporary Address (3) Length: 18 IAID: 00000000 T1: 0 T2: 0 Status code Option: Status code (13) Length: 2 Status Code: NoAddrAvail (2) Elapsed time Option: Elapsed time (8) Length: 2 Elapsed time: 0ms Option Request Option: Option Request (6) Length: 4 Requested Option code: DNS recursive name server (23) Requested Option code: Domain Search List (24) Identity Association for Prefix Delegation Option: Identity Association for Prefix Delegation (25) Length: 41 IAID: 00000000 T1: 0 T2: 0 IA Prefix Option: IA Prefix (26) Length: 25 Preferred lifetime: 7200 Valid lifetime: 7200 Prefix length: 56 Prefix address: 2600:4040:xxxx:xx00:: ================ DHCPv6 Message type: Reply (7) Transaction ID: 0x996ddc Client Identifier Option: Client Identifier (1) Length: 14 DUID: 000100012ceadexxxxxxxxxxxxxx DUID Type: link-layer address plus time (1) Hardware type: Ethernet (1) DUID Time: Nov 17, 2023 21:31:59.000000000 EST Link-layer address: 00:90:0b:xx:xx:xx Server Identifier Option: Server Identifier (2) Length: 26 DUID: 00020000058366343a62353a32663a30353axxxxxxxxxxxxxxxx DUID Type: assigned by vendor based on Enterprise number (2) Enterprise ID: Juniper Networks/Funk Software (1411) Identifier: 66343a62353a32663a30353axxxxxxxxxxxxxxxx Identity Association for Non-temporary Address Option: Identity Association for Non-temporary Address (3) Length: 59 IAID: 00000000 T1: 0 T2: 0 Status code Option: Status code (13) Length: 43 Status Code: NoAddrAvail (2) Status Message: No addresses have been assigned for IA_NA Identity Association for Prefix Delegation Option: Identity Association for Prefix Delegation (25) Length: 41 IAID: 00000000 T1: 3600 T2: 5760 IA Prefix Option: IA Prefix (26) Length: 25 Preferred lifetime: 7200 Valid lifetime: 7200 Prefix length: 56 Prefix address: 2600:4040:xxxx:xx00:: -
@DrPhil like I said the ISP doesn't always pay attention to what you ask for..
if your getting a /56 and your tracking and using the 0 and 1 you sure shouldn't have a /128 on the actual interface.. So when you look on pfsense it shows the /64 ?
Was that IP you showed with the /128 from a client on the network?
Under status interfaces what does the pfsense interface show - I don't use track, but it should show you a /64
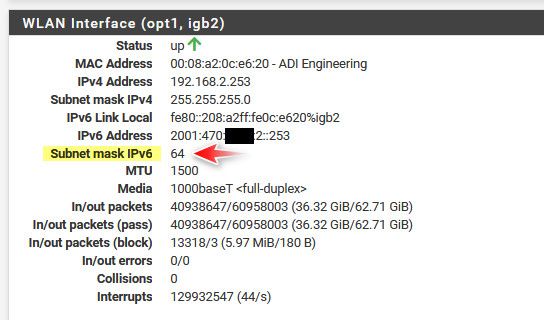
edit, did you maybe set something odd in your RA?
edit: none of my linux boxes are currently using Ipv6, but I enabled it real quick on my windows pc, and via netstat -rn showing the routes I can see that its a /64
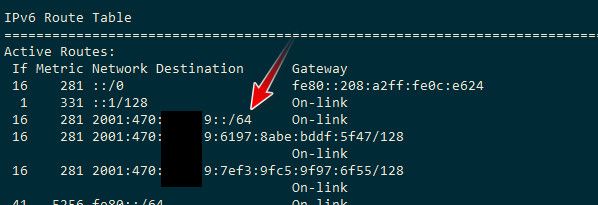
-
It would appear you're requesting and receiving a /56. I agree with @johnpoz there's something strange. When you're trying to resolve a problem, try to keep things simple. For example, use only SLAAC on the LAN.
As for the /128, that's fine on the WAN interface, but nowhere else. Your LAN should definitely be a /64.
BTW, why are you worried about revealing your prefix? Each /64 contains 18.4 billion, billion addresses, which means it's virtually impossible for an attacker to find anything. When disguising an actual device address, I will often just change some of the characters. In the capture I provided above, it was a capture I did years ago and has a different prefix from what I have now.
-
@JKnott said in Configure IPv6 on multiple LAN interfaces:
Each /64 contains 18.4 billion
While I agree with you there, might as well hide part of my prefix.. I have been seeing quite a bit of IPv6 noise of late.. To an address that yeah is in my space but I don't use - while scanning all of ipv6 space is an exercise in futility I agree..
But they find a way to scope out IP space to what is being used and then trim down the address space they query for.. For example I see bunch of scans to this IP.

not sure where they came up with this IP, maybe it use to be someone elses? But while that is in the prefix for my tunnel network to HE, and I have an IP on my gif interface in that prefix, it isn't that..
https://www.shadowserver.org/news/hello-ipv6-scanning-world/
So while scanning all of Ipv6 is pretty impossible - they find stuff to narrow down the search.. So makes sense not to spread your IPv6 or even its prefixes about.. Just to hope to keep the scanning to your prefixes down, even if it falls on deaf ears on yourside.