No internet on LAN
-
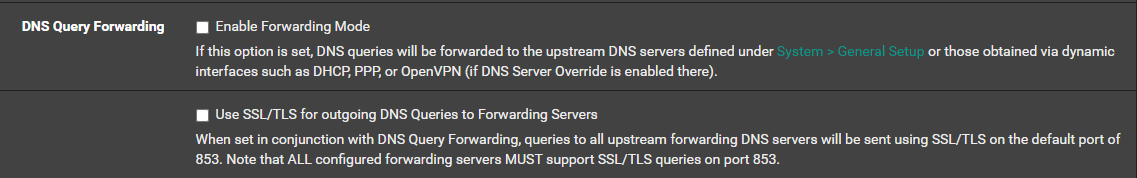
@stephenw10 Unbound is running, and I found the following when doing the lookup
Somehow the issue is not present in the VMs LAN interface, but both my laptop and phone are unable to connect to the internet when hooked up to the VMs LAN -
@stephenw10 said in No internet on LAN:
Try resolving something in Diag > DNS Lookup.
Do that^. It will show how all the configured DNS servers are responding.
-
This post is deleted! -
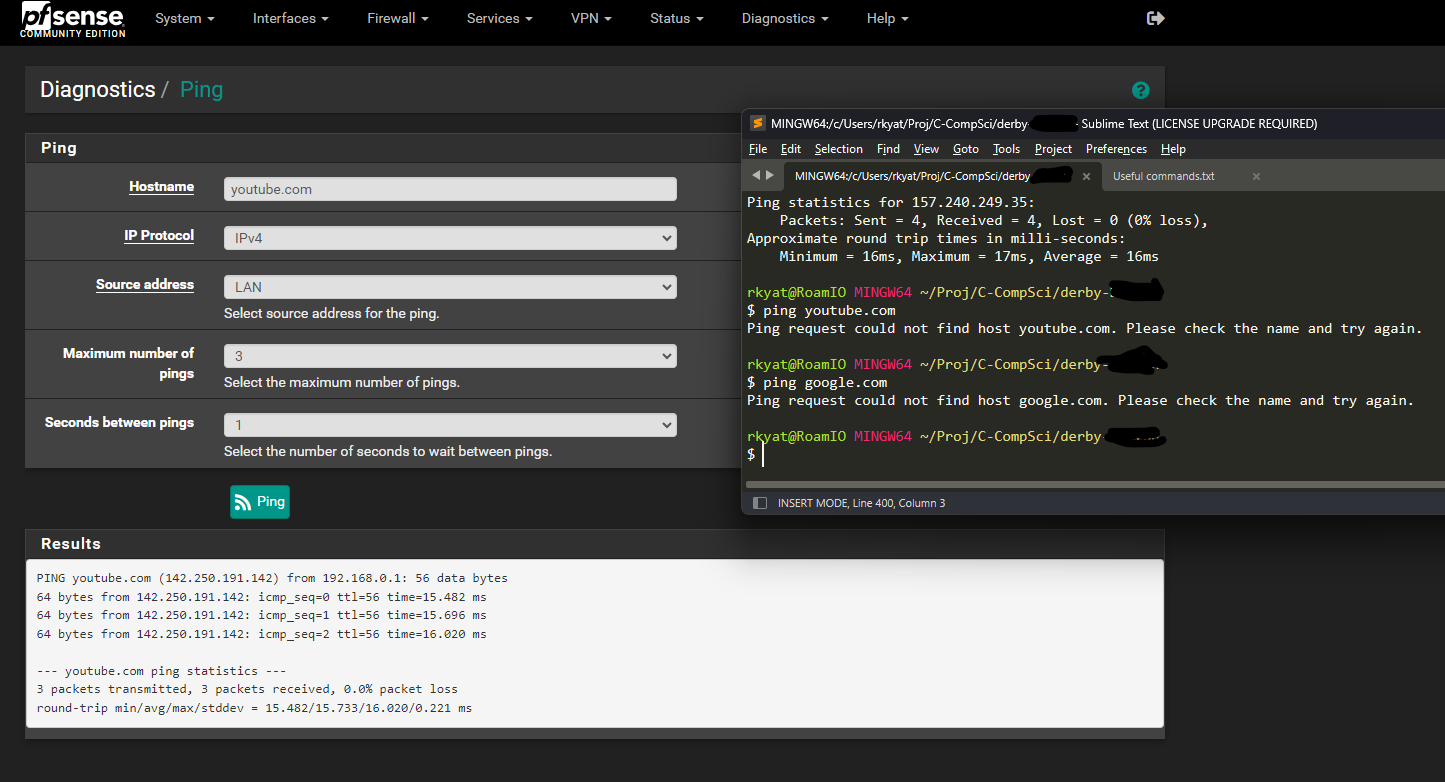
@stephenw10 Here is the lookup
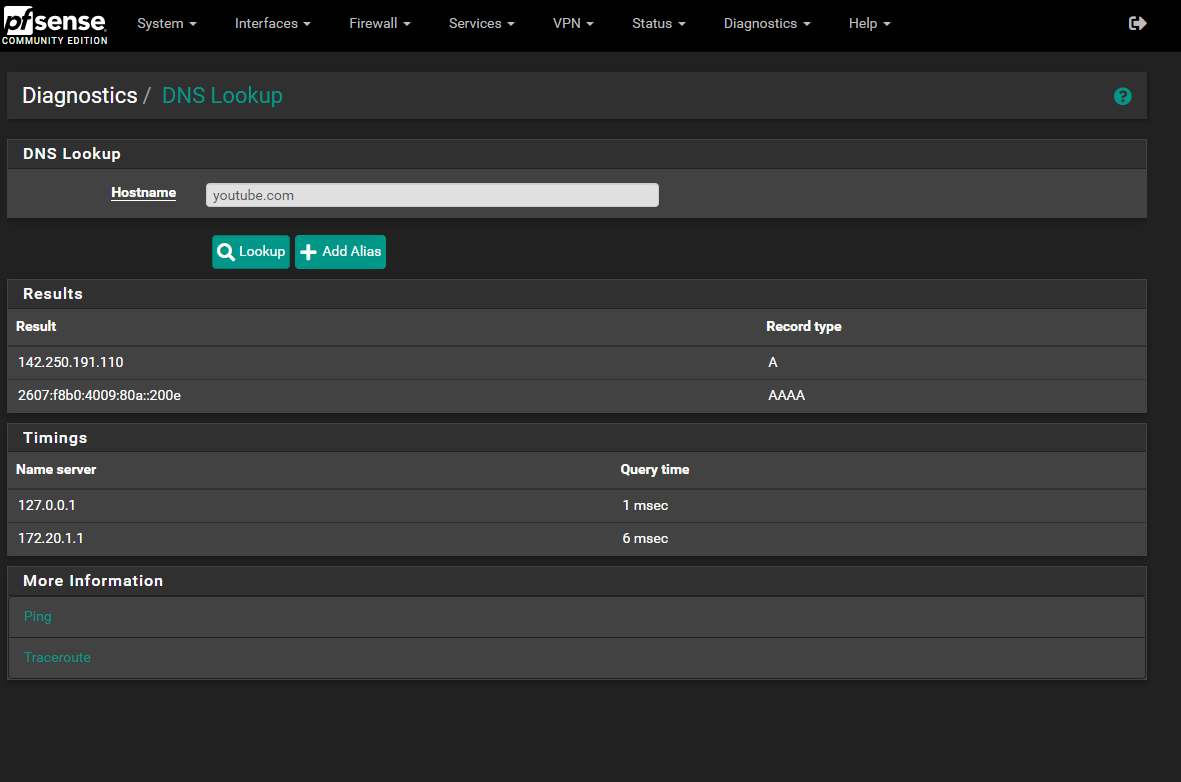
and I also did a traceroute
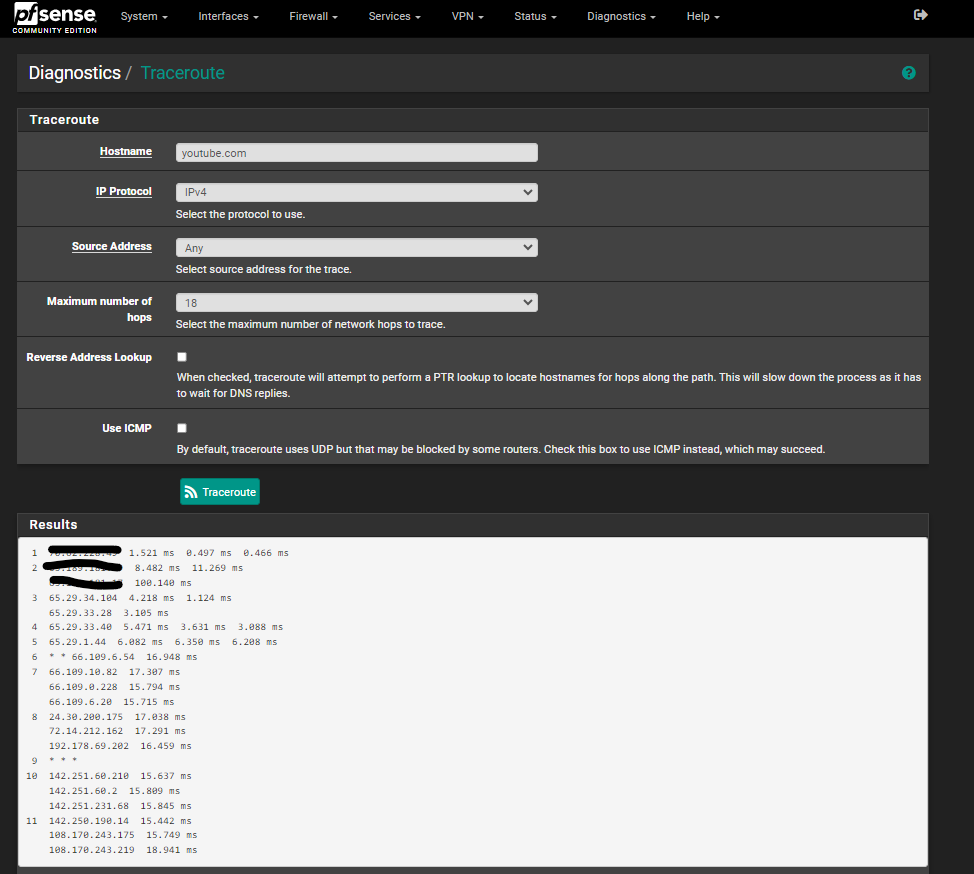
-
@rakya so what is not working.. You clearly can get to the internet if you can ping 8.8.8.8 and you can lookup something.. So what is not working?
-
DNS is failing on the LAN side client.
So check what the client is using for DNS. It would normally be passed the pfSense LAN IP to use via DHCP but that can be ignored/overridden on the client.
-
@stephenw10 I did a
ipconfig/allon my laptop and it seems to be saying the pfSense LAN IP is correctly set as the DHCP, and DNS provider, but i am still unable to ping google.com
@johnpoz in addition to being unable to ping google.com, i cannot browse the web, that is why I had believed that DNS was the issue, but am now unsure again... everything seems to be working great from within the VM, but the 2 clients I have tried are unable to navigate to anything except the webconfigurator. I will try a different ethernet cable.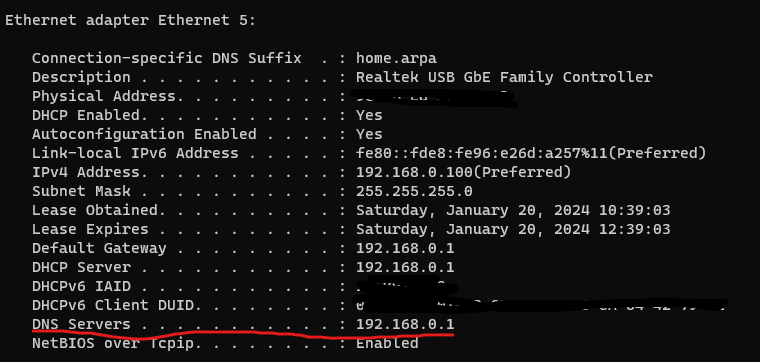
-
switching cables made no difference
-
@rakya so can you actually do a dns query via say nslookup on your machine?
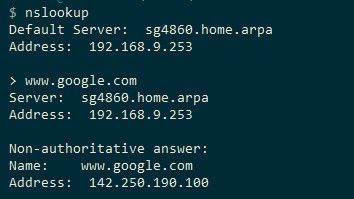
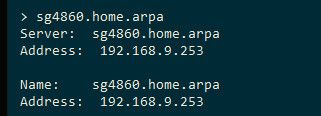
Do you see your pfsense name by the address.. See how mine tells me that 192.168.9.253 (pfsense IP on my lan) that its name is sg4860.home.arpa
If your not seeing that - that points to not being able to talk to pfsense IP for dns, or unbound isn't even running.. What error or timeout do you see? If you get back name for pfsense with nslookup but queries for like www.google.com don't work what about asking about pfsense name.. like this
Did you happen to mess with the acls? Pfsense will normally auto add all your local networks to the ACL of unbound to allow your local networks to query it, but if you turned that off? Under unbound / advanced near the bottom
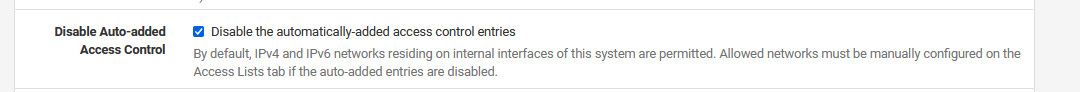
If you did that you would have to manually create your acls, which is what I do.
The output of nslookup should be informative to what is going on. If you can talk to unbound for dns, etc.
You don't have any rules in floating do you? That could be blocking dns? But again if you had that, it wouldn't log as the default deny rule.
And yeah without working dns, internet not going to work ;)
-
@johnpoz Here is the output of
nslookup
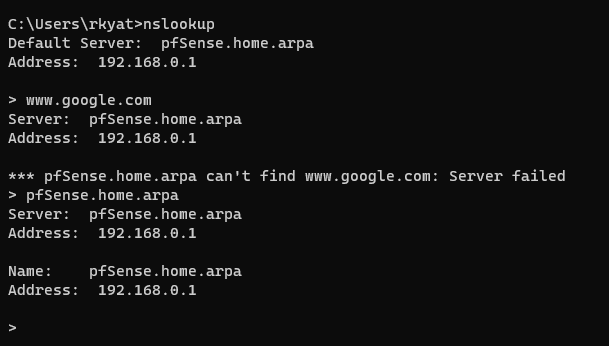
however if I go to Diag/DNS lookup google.com, it works and I get a 142.x.x.x
I didnt mess with the ACLs, but mine is unchecked, as opposed to your pic.
I dont have any floating rulesIll be afk for a couple hours, thanks for your continued help!
-
@rakya ok so your able to talk to unbound.. Be it responded with servfail - for some reason it says it can't look that up..
Are you using anything like pfblocker?
What about that youtube.com you looked up in diag.. Can it find that? Maybe your resolving isn't actually working, I would do say a dig +trace on pfsense itself..
So for example on mine.
[23.09.1-RELEASE][admin@sg4860.home.arpa]/root: dig www.google.com +trace ; <<>> DiG 9.18.16 <<>> www.google.com +trace ;; global options: +cmd . 53022 IN NS a.root-servers.net. . 53022 IN NS l.root-servers.net. . 53022 IN NS m.root-servers.net. . 53022 IN NS g.root-servers.net. . 53022 IN NS b.root-servers.net. . 53022 IN NS k.root-servers.net. . 53022 IN NS j.root-servers.net. . 53022 IN NS h.root-servers.net. . 53022 IN NS f.root-servers.net. . 53022 IN NS c.root-servers.net. . 53022 IN NS e.root-servers.net. . 53022 IN NS d.root-servers.net. . 53022 IN NS i.root-servers.net. . 53022 IN RRSIG NS 8 0 518400 20240202050000 20240120040000 30903 . CTewF1Ps34mxmQNsY2egNalTgiHJ2bgGrfl6vqIVoEDi9h0Y8SfEweK0 a7lKlksKjOBOwXIqY0zFYbavNxBWUiMgmvlxRz0cOrQIGmZKcRcm3U9M eKF0AK3ZanCAGBl9JxgiHsErlW+aE55UgKouQGW2E7HQ9+FhYpYSUXft KSn8Dh8pEfzCwKjxAF7KYY2/UeFw6iDH9EvL8YTJvqXIcmISv+mwa1U8 R6uFy/Lj/f84cU20DNDfEH2H6zNGVu+sjkCNOJhCzRgbgILTsEVC4Vix UB9JRWWEoorGusWYj6eKbVFnI1LoPX1lBdP3T7jg3ZlofihNaBlG2Aye kAsdYA== ;; Received 525 bytes from 127.0.0.1#53(127.0.0.1) in 0 ms com. 172800 IN NS j.gtld-servers.net. com. 172800 IN NS e.gtld-servers.net. com. 172800 IN NS a.gtld-servers.net. com. 172800 IN NS m.gtld-servers.net. com. 172800 IN NS k.gtld-servers.net. com. 172800 IN NS i.gtld-servers.net. com. 172800 IN NS h.gtld-servers.net. com. 172800 IN NS b.gtld-servers.net. com. 172800 IN NS d.gtld-servers.net. com. 172800 IN NS f.gtld-servers.net. com. 172800 IN NS g.gtld-servers.net. com. 172800 IN NS c.gtld-servers.net. com. 172800 IN NS l.gtld-servers.net. com. 86400 IN DS 19718 13 2 8ACBB0CD28F41250A80A491389424D341522D946B0DA0C0291F2D3D7 71D7805A com. 86400 IN RRSIG DS 8 1 86400 20240202050000 20240120040000 30903 . aM4F4/AGcBOqkGKmZBzVH+7MZ2j31PkhcTY4PhYL2JpMcj/+4VmWujq4 Dp5wFkkR/A0zjuXTkhIXL1ybVLvlC2ULXA95ER6Ci5XODkO/95Vm3ZKl ZzDgJgTOHKBcMB2YsFtUPl1U104uY9u7ekNAxl/6UJRBqKAHRC4iwX0N To0B47K2Wk0DBpax7jhYcC6l8jJ8V9THLXTA6N+xy8YxYqBwtpwjC1W0 r23G54R8fOsq7/9vewt6QUlMRtpaKIjKbiT6bz1LhonC4wmlF+E1DG5z WaDC9D+c9hImD/CQQRYxveHt53xdlUyy5HW+9/2tM8inDwYPUPo171O9 W58eEQ== ;; Received 1205 bytes from 192.33.4.12#53(c.root-servers.net) in 11 ms google.com. 172800 IN NS ns2.google.com. google.com. 172800 IN NS ns1.google.com. google.com. 172800 IN NS ns3.google.com. google.com. 172800 IN NS ns4.google.com. CK0POJMG874LJREF7EFN8430QVIT8BSM.com. 86400 IN NSEC3 1 1 0 - CK0Q2D6NI4I7EQH8NA30NS61O48UL8G5 NS SOA RRSIG DNSKEY NSEC3PARAM CK0POJMG874LJREF7EFN8430QVIT8BSM.com. 86400 IN RRSIG NSEC3 13 2 86400 20240125052629 20240118041629 4534 com. ykfYgHHugNyHP7+geKoIrJKpkbPB/yuIEn6/vtfQoY6/j1BYd6oVV31c pPSVMcC1vzyGVQtwdfwiInvV9K/ZjA== S84BKCIBC38P58340AKVNFN5KR9O59QC.com. 86400 IN NSEC3 1 1 0 - S84BR9CIB2A20L3ETR1M2415ENPP99L8 NS DS RRSIG S84BKCIBC38P58340AKVNFN5KR9O59QC.com. 86400 IN RRSIG NSEC3 13 2 86400 20240126053742 20240119042742 4534 com. nVkxHFIPFvfEgs6nZi5frFPlGUQoh5ACiLJuqYNIIrTxHinPrqbx3RTy dWhmFUF2wpZCbB13rZ3xbyHc8QRe3A== ;; Received 648 bytes from 192.31.80.30#53(d.gtld-servers.net) in 41 ms www.google.com. 300 IN A 142.250.190.100 ;; Received 59 bytes from 216.239.36.10#53(ns3.google.com) in 21 ms [23.09.1-RELEASE][admin@sg4860.home.arpa]/root:This is how unbound would resolve whatever your looking for..
-
@rakya If you have forwarding enabled in DNS Resolver, disable DNSSEC.
-
@johnpoz I didnt setup any pfBlocker (no idea how)
also the diag DNS lookup can find youtube as well
This is the result of my dig+trace
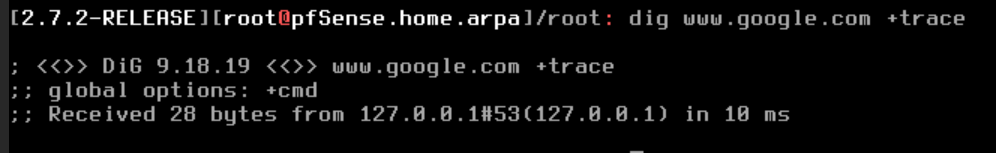
are you using some kind of verbose option by default? -
^yup if your forwarding that could be very problematic.
-
-
@rakya said in No internet on LAN:
are you using some kind of verbose option by default?
no.. you got something wrong there.. what you should get back from 127.0.0.1 is the root servers.
; <<>> DiG 9.18.16 <<>> www.google.com +trace ;; global options: +cmd . 53022 IN NS a.root-servers.net. . 53022 IN NS l.root-servers.net. . 53022 IN NS m.root-servers.net. . 53022 IN NS g.root-servers.net. . 53022 IN NS b.root-servers.net. . 53022 IN NS k.root-servers.net. . 53022 IN NS j.root-servers.net. . 53022 IN NS h.root-servers.net. . 53022 IN NS f.root-servers.net. . 53022 IN NS c.root-servers.net. . 53022 IN NS e.root-servers.net. . 53022 IN NS d.root-servers.net. . 53022 IN NS i.root-servers.net. . 53022 IN RRSIG NS 8 0 518400 20240202050000 20240120040000 30903 . CTewF1Ps34mxmQNsY2egNalTgiHJ2bgGrfl6vqIVoEDi9h0Y8SfEweK0 a7lKlksKjOBOwXIqY0zFYbavNxBWUiMgmvlxRz0cOrQIGmZKcRcm3U9M eKF0AK3ZanCAGBl9JxgiHsErlW+aE55UgKouQGW2E7HQ9+FhYpYSUXft KSn8Dh8pEfzCwKjxAF7KYY2/UeFw6iDH9EvL8YTJvqXIcmISv+mwa1U8 R6uFy/Lj/f84cU20DNDfEH2H6zNGVu+sjkCNOJhCzRgbgILTsEVC4Vix UB9JRWWEoorGusWYj6eKbVFnI1LoPX1lBdP3T7jg3ZlofihNaBlG2Aye kAsdYA== ;; Received 525 bytes from 127.0.0.1#53(127.0.0.1) in 0 msYeah if don't know who to start talking to, its going to fail that is for sure.
Be curious what this shows
Also curious what this outputs
"unbound-control -c /var/unbound/unbound.conf lookup ."
See the dot/period at the end, this is asking hey where would you look up the root which is the .
[23.09.1-RELEASE][admin@sg4860.home.arpa]/root: unbound-control -c /var/unbound/unbound.conf lookup . The following name servers are used for lookup of . ;rrset 49813 13 1 11 5 . 49813 IN NS g.root-servers.net. . 49813 IN NS b.root-servers.net. . 49813 IN NS k.root-servers.net. . 49813 IN NS j.root-servers.net. . 49813 IN NS h.root-servers.net. . 49813 IN NS f.root-servers.net. . 49813 IN NS c.root-servers.net. . 49813 IN NS e.root-servers.net. . 49813 IN NS d.root-servers.net. . 49813 IN NS i.root-servers.net. . 49813 IN NS a.root-servers.net. . 49813 IN NS l.root-servers.net. . 49813 IN NS m.root-servers.net. . 49813 IN RRSIG NS 8 0 518400 20240202050000 20240120040000 30903 . CTewF1Ps34mxmQNsY2egNalTgiHJ2bgGrfl6vqIVoEDi9h0Y8SfEweK0a7lKlksKjOBOwXIqY0zFYbavNxBWUiMgmvlxRz0cOrQIGmZKcRcm3U9MeKF0AK3ZanCAGBl9JxgiHsErlW+aE55UgKouQGW2E7HQ9+FhYpYSUXftKSn8Dh8pEfzCwKjxAF7KYY2/UeFw6iDH9EvL8YTJvqXIcmISv+mwa1U8R6uFy/Lj/f84cU20DNDfEH2H6zNGVu+sjkCNOJhCzRgbgILTsEVC4VixUB9JRWWEoorGusWYj6eKbVFnI1LoPX1lBdP3T7jg3ZlofihNaBlG2AyekAsdYA== ;{id = 30903} ;rrset 49793 1 0 8 3 m.root-servers.net. 49793 IN A 202.12.27.33 ;rrset 83191 1 0 8 3 l.root-servers.net. 83191 IN A 199.7.83.42 ;rrset 83191 1 0 8 3 a.root-servers.net. 83191 IN A 198.41.0.4 ;rrset 83191 1 0 8 3 i.root-servers.net. 83191 IN A 192.36.148.17 ;rrset 83191 1 0 8 3 d.root-servers.net. 83191 IN A 199.7.91.13 ;rrset 83191 1 0 8 3 e.root-servers.net. 83191 IN A 192.203.230.10 ;rrset 83191 1 0 8 3 c.root-servers.net. 83191 IN A 192.33.4.12 ;rrset 83191 1 0 8 3 f.root-servers.net. 83191 IN A 192.5.5.241 ;rrset 83191 1 0 8 3 h.root-servers.net. 83191 IN A 198.97.190.53 ;rrset 83191 1 0 8 3 j.root-servers.net. 83191 IN A 192.58.128.30 ;rrset 83191 1 0 8 3 k.root-servers.net. 83191 IN A 193.0.14.129 ;rrset 83191 1 0 8 3 b.root-servers.net. 83191 IN A 170.247.170.2 ;rrset 83191 1 0 8 3 g.root-servers.net. 83191 IN A 192.112.36.4 Delegation with 13 names, of which 0 can be examined to query further addresses. It provides 13 IP addresses. 192.112.36.4 expired, rto 3613560 msec, tA 0 tAAAA 0 tother 0. 170.247.170.2 expired, rto 3613560 msec, tA 0 tAAAA 0 tother 0. 193.0.14.129 expired, rto 3613560 msec, tA 0 tAAAA 0 tother 0. 192.58.128.30 expired, rto 3613560 msec, tA 0 tAAAA 0 tother 0. 198.97.190.53 expired, rto 3613560 msec, tA 0 tAAAA 0 tother 0. 192.5.5.241 expired, rto 3613560 msec, tA 0 tAAAA 0 tother 0. 192.33.4.12 expired, rto 3613560 msec, tA 0 tAAAA 0 tother 0. 192.203.230.10 expired, rto 3613560 msec, tA 0 tAAAA 0 tother 0. 199.7.91.13 expired, rto 3613560 msec, tA 0 tAAAA 0 tother 0. 192.36.148.17 expired, rto 3613560 msec, tA 0 tAAAA 0 tother 0. 198.41.0.4 expired, rto 3613560 msec, tA 0 tAAAA 0 tother 0. 199.7.83.42 expired, rto 3613560 msec, tA 0 tAAAA 0 tother 0. 202.12.27.33 expired, rto 3613560 msec, tA 0 tAAAA 0 tother 0. [23.09.1-RELEASE][admin@sg4860.home.arpa]/root:In resolving mode - which is unbound default, it needs to know where to go ask (the roots) to start the process.. If it can't or doesn't know where to go for the roots, then yeah any resolving will fail..
-
@rakya Out of the box it should just work implying something changed. Can you compare an earlier config file? There’s a recent history : https://docs.netgate.com/pfsense/en/latest/backup/restore.html#restoring-from-the-config-history
Or post your Resolver page(s).
-
@SteveITS said in No internet on LAN:
Or post your Resolver page(s).
really more interested in seeing the output of
"unbound-control -c /var/unbound/unbound.conf lookup ."
that trace should of shown the roots.. why it isn't if in resolving mode would explain why dns is not working.. If in forwarding mode it would show where to forward.. For example I switched it to forward mode, but didn't put in anything forward, it showed error.
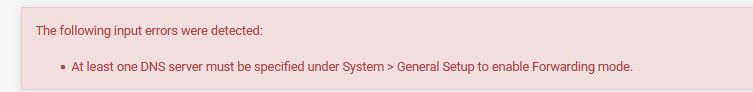
I then setup up to forward to 9.9.9.9, so the output of the above cmd shows that
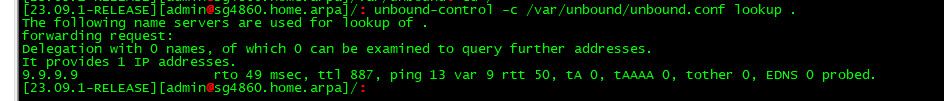
So if unbound is trying to forward, where you forward should be in that output, if your resolve, then the roots should be in there. If there is nothing then no its never going to work.
-
@johnpoz @SteveITS
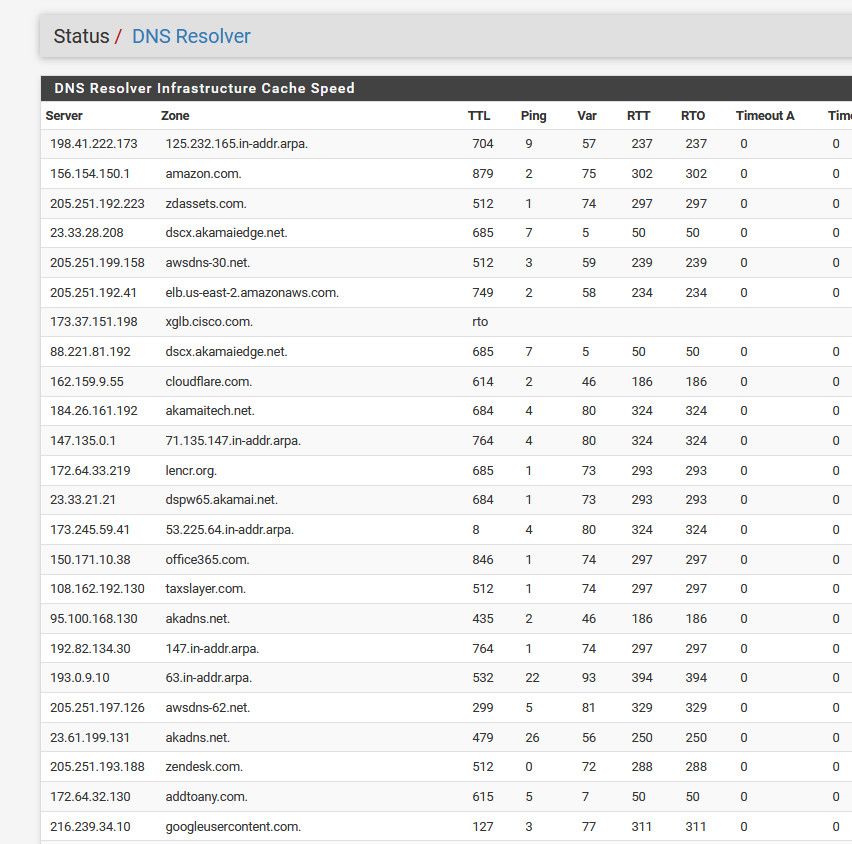
Here is my DNS resolver Status page (is this what you meant by Resolver page(s)?)
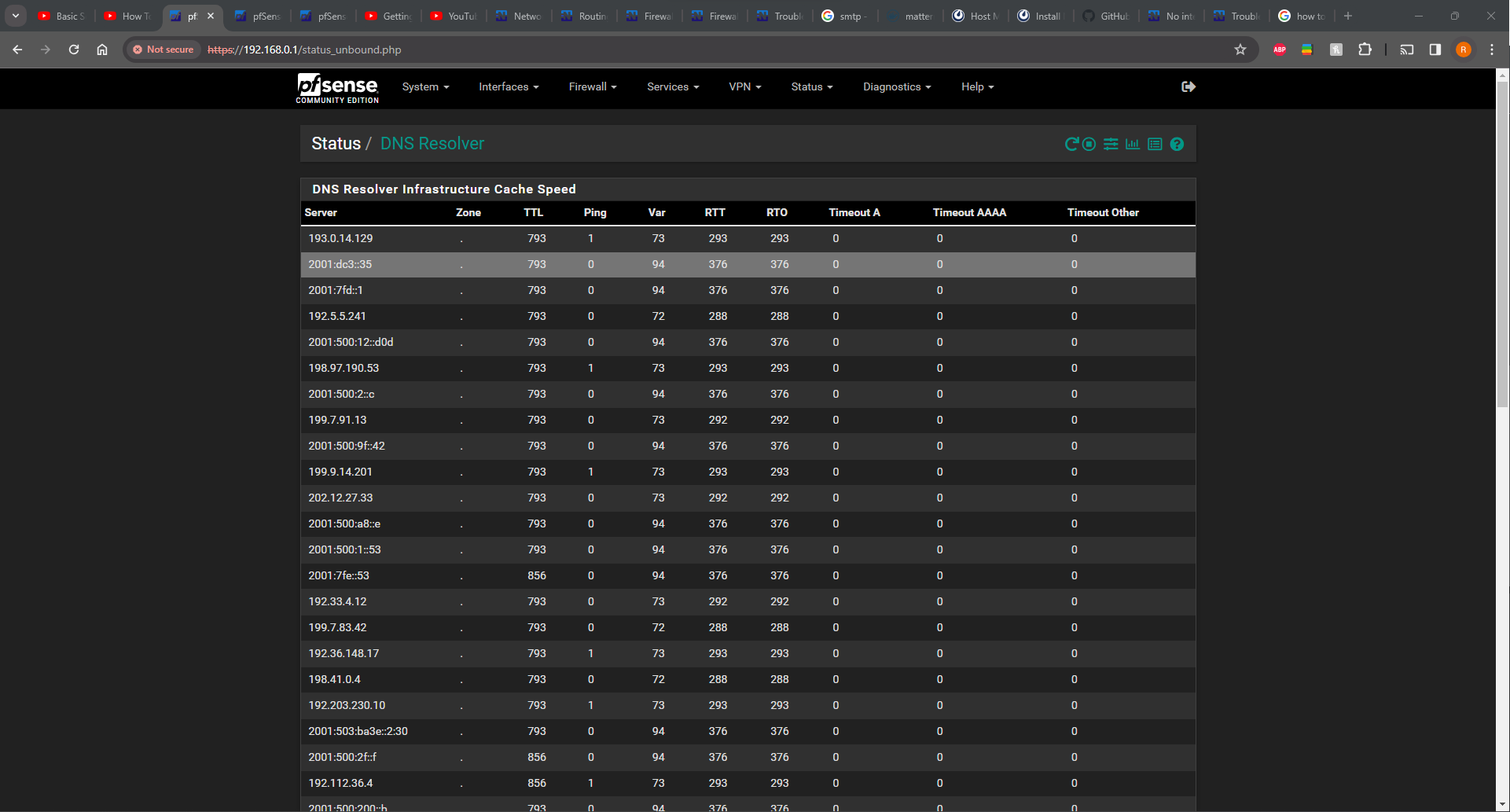
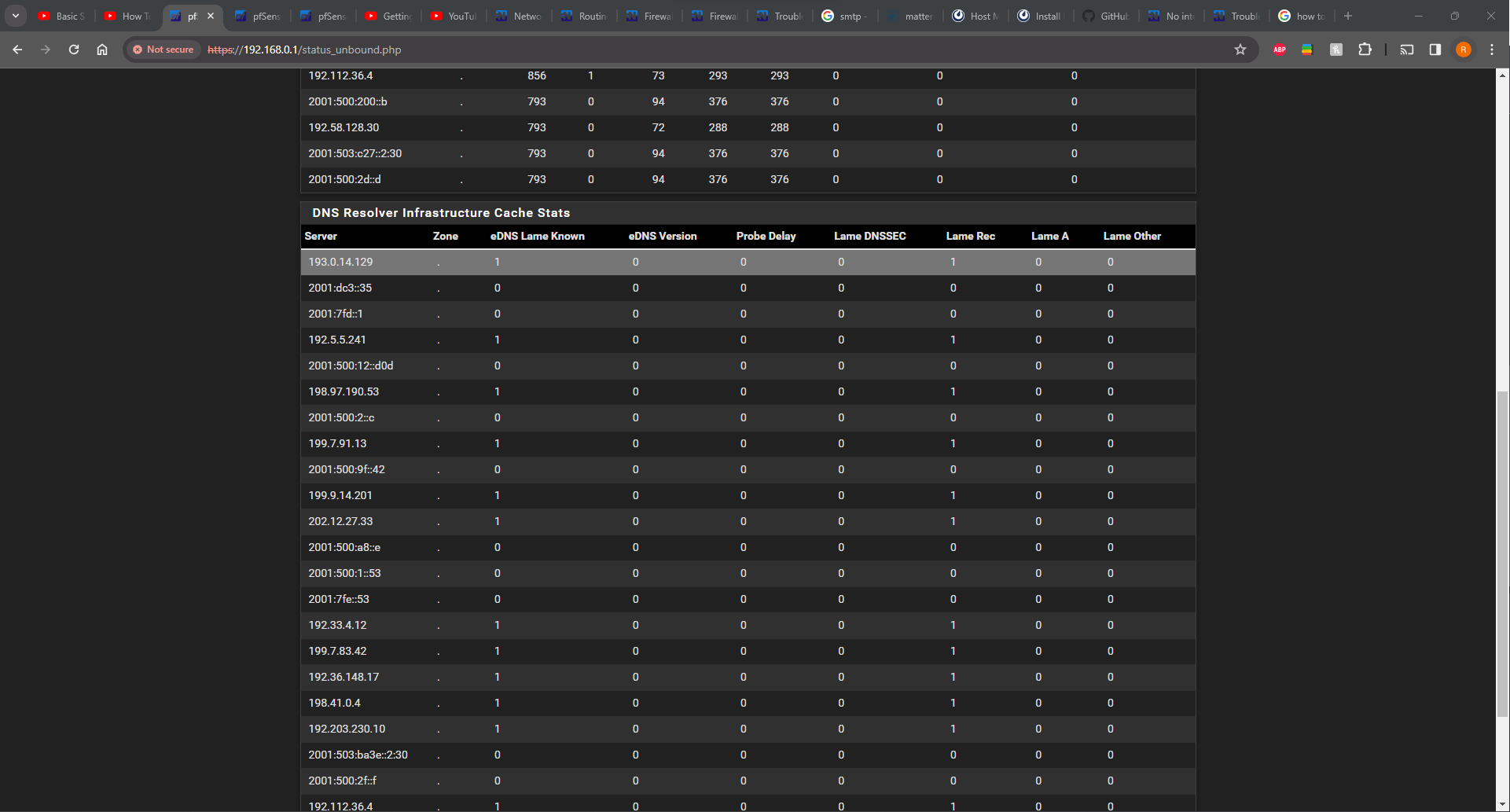
This is the result of
unbound-control -c /var/unbound/unbound.conf lookup .
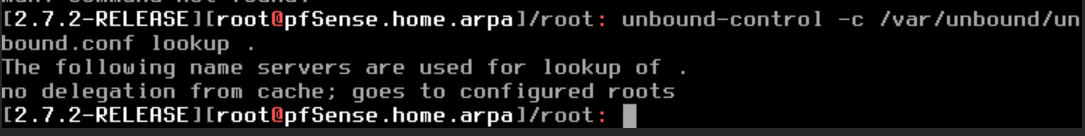
so it looks like it has no clue who to talk to, but then why is the Diag/DNS lookup able to get proper addresses? Also is there a way to investigate further on what are the "configured roots"?In terms of earlier configs, here is a diff file for as far back as the system goes (9 days)
jan20_pfSense-total.diff -
@rakya I meant, all the settings :)