HA Proxy SSL Termination Forward To Traefik
-
I'm running a trunas scale server with Traefik installed. Traefik is required for one of the apps I'm using. I already use HA proxy and SSL termination on my pf sense router. I'm trying to route cloud.mydomain.com to my traffic service and set the host header to cloud.mydomain.com. cloud.mydomain.com is hosted behind Traefik on 10.10.0.2:443. I am able to mock this host header in postman and get a valid response, but I must have the settings wrong in pf sense. It doesn't seem to be setting the host header (I'm not sure of this. I'm having trouble getting logs to show me)
Here is my pfsense setup:
frontend settings
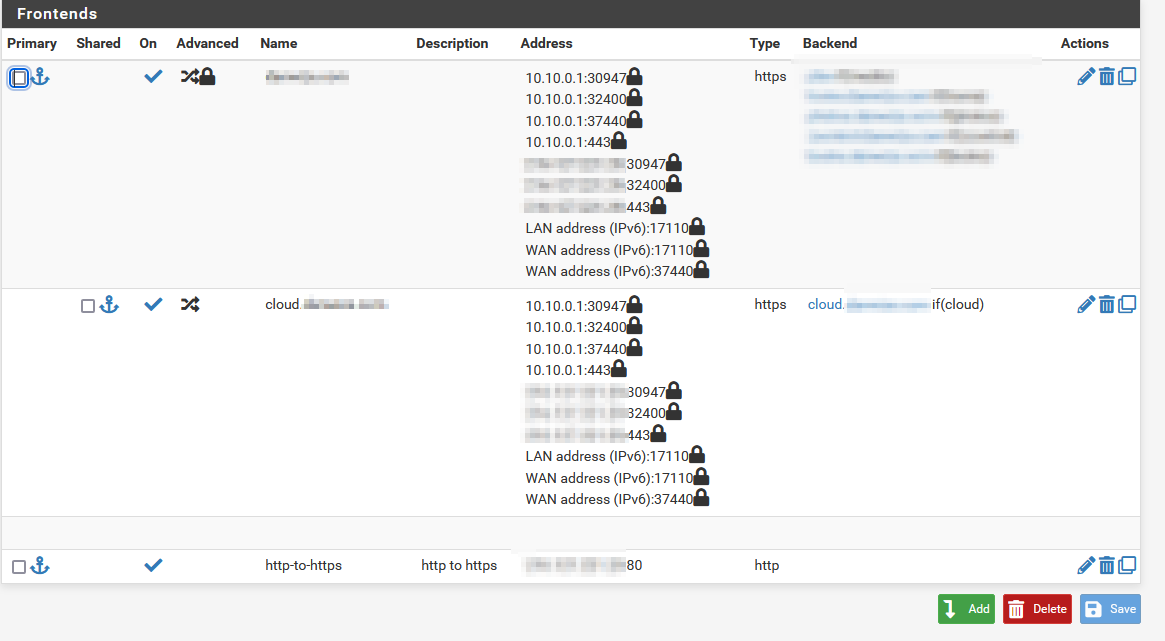
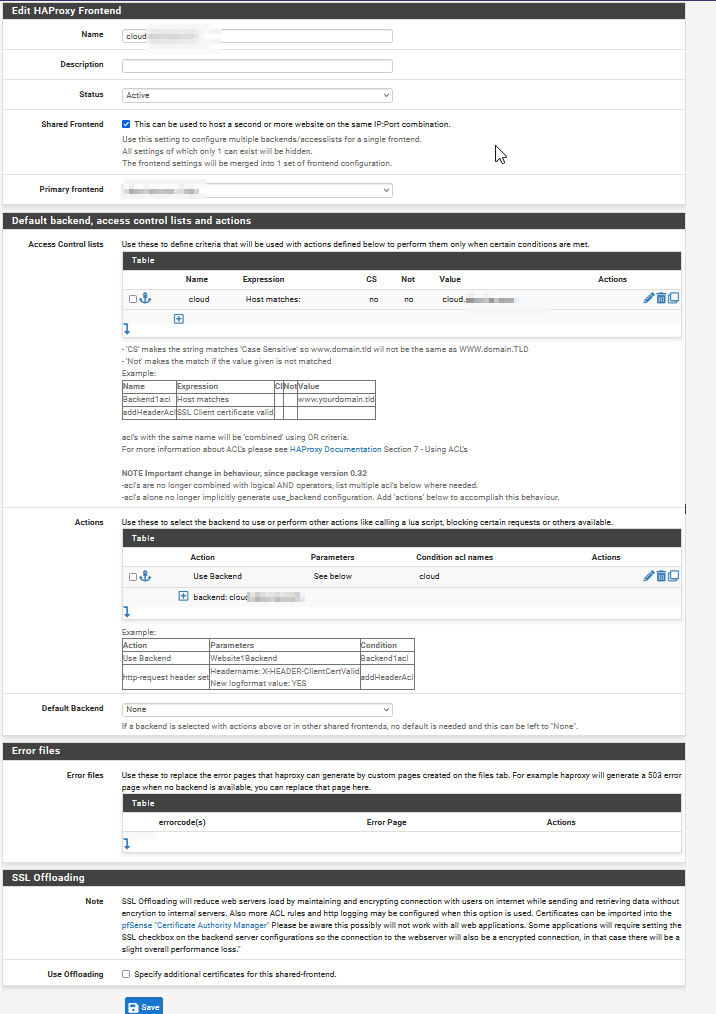
backend settings:
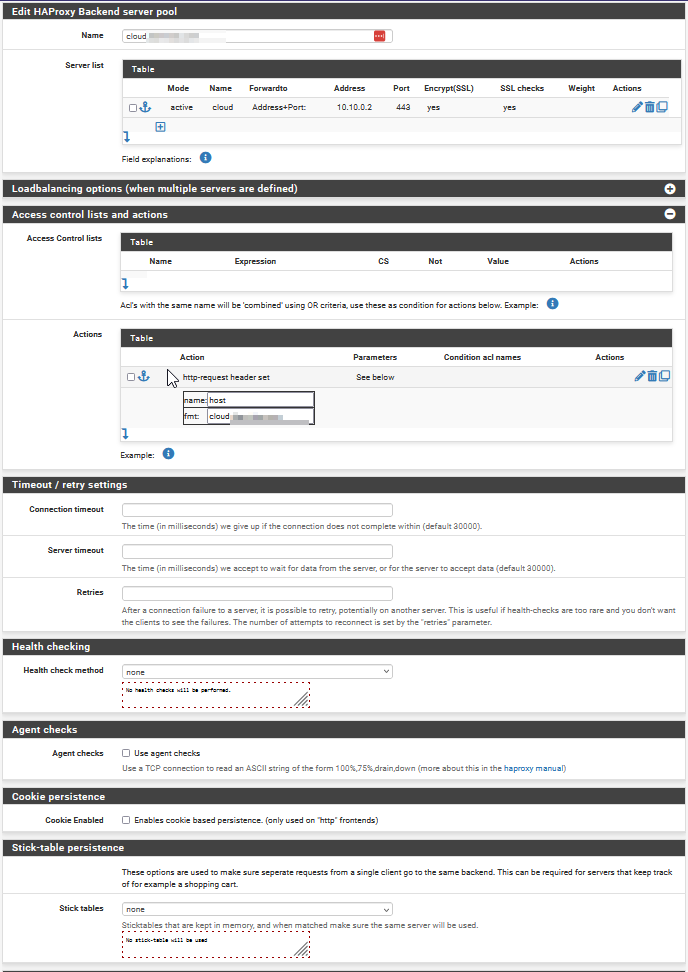
Postman Mock:
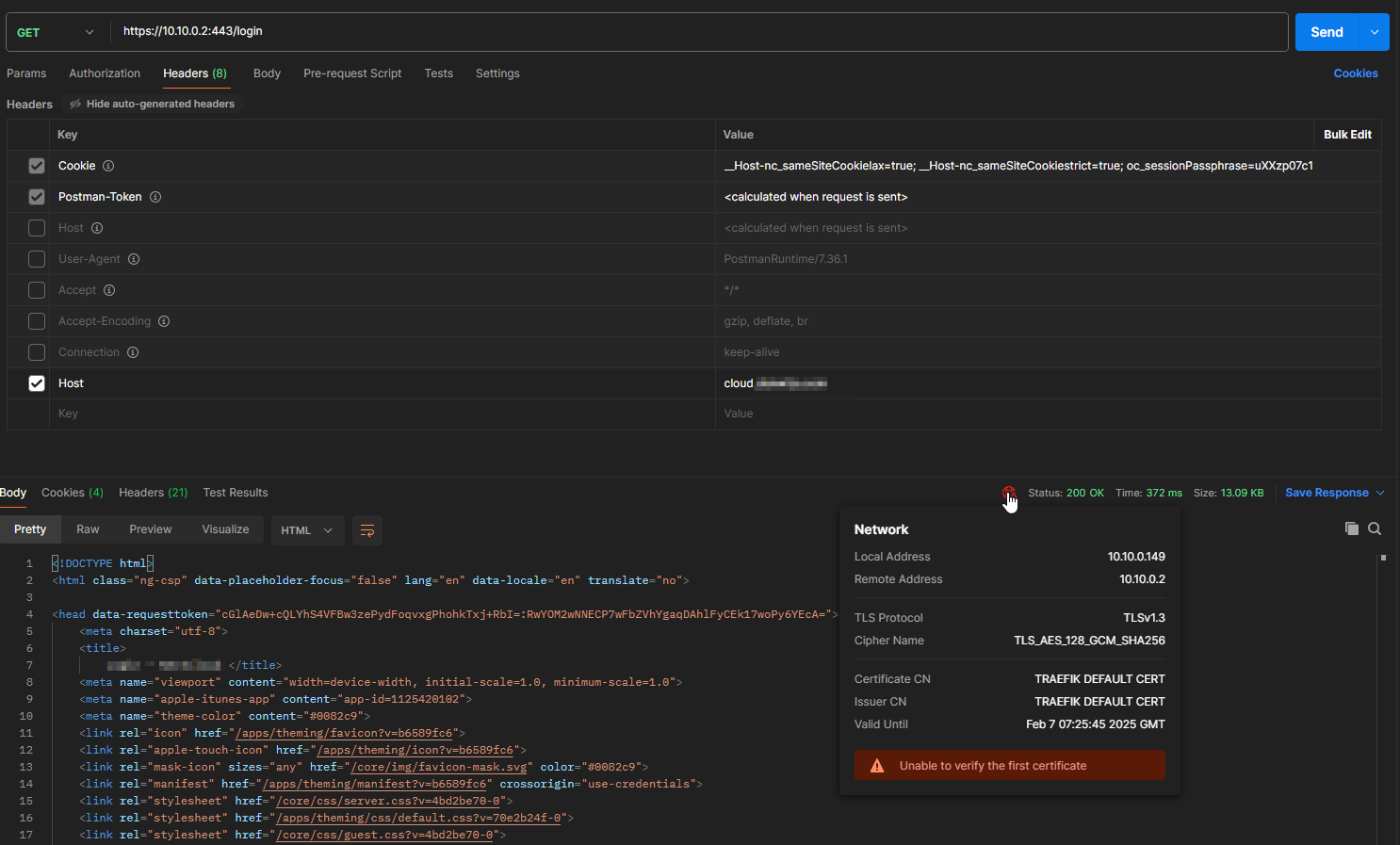
cloud.mydomain.com in browser:
cloud.mycomain.com resloves to my pfsense router on my local network.
Can anyone see what I'm missing in my ha proxy config? Or is what I'm trying to do not feasible?
-
@danwize said in HA Proxy SSL Termination Forward To Traefik:
I'm trying to route cloud.mydomain.com to my traffic service and set the host header to cloud.mydomain.com.
If the client calls "cloud.mydomain.com" it will set the host header already to this value, and the header will be passed through to the backend. So there is no need to reset it on HAproxy.
Postman Mock:
This goes directly to the backend. So what should it tell us?
cloud.mydomain.com in browser:
Did you try this from outside?
Is this access even forwarded to the backend? Check its log.
Possibly the ACL is never hit, since another one matched to request already as it's shared frontend.
Would need to see the other frontend settings and the order. -
I tried setting the host manually after reading this. I guess that scenario is different because they are trying to change the host header.
I originally had it all set up with one front end and I tried to add a second to try forcing cloud.mydomain.com to not use ssl termination since the traefik reverse proxy is doing that now. I found that I can't have a separate front end with the same ports so I just ticked the box to combine then.
Postman Mock:
Because of updates in my cloud app, It has to work behind traefik. the postman test is just to prove that setting that header and pointing to 10.10.0.2:443 causes traefik to route the request to my final back end cloud app. If I leave off the host header, traefik responds with the same 404 message that going through pfsense does.The ACL was being hit. I changed the back end in pfsense to point to a different port for another service and it worked.
-
@danwize @viragomann
I've got it working now. I changed to just use one front end and added my acl for cloud back. I removed my attempts to set the header and changed my could back end to point to 10.10.0.2:443 after I had changed it to 10.10.0.2:10223 for testing. After I did that, and after saving and applying the changes several times, cloud.mydomain.com was still resolving to 10223. I even tested in igognito windows and restarted the ha proxy service from the pfsense ui and it kept resolving to 10223.I finally got it routing to 443 after editing the front end settings for cloud to use a different backend, saved those changes, and then changed it back to my cloud.mydomain.com backed and saved again. Possibly my problem from the beginning was the fact that the settings didn't take initially.