Do you use dhcp reservations?
-
My decision and arguments for using “IP static mapping” in middle-size companies or small firms with @johnpoz answers and arguments You may read here: Static IP - MAC mapping inside DHCP dynamic pool - how to?.
Thank You all!
-
I use them for every single device on my network. My 48 bit addresses and layer 2 addresses are all purple here because I do not want any mac address cloning going on. That is a cool pen testing tool to see that done.
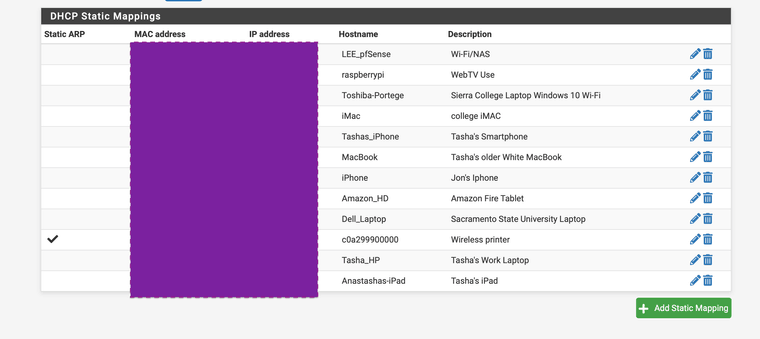
-
@JonathanLee said in Do you use dhcp reservations?:
I do not want any mac address cloning going on.
Who is going to clone your macs? And for what purpose? Mac cloning is only a thing if they are already on your network..
Here is my pc mac.. Clone away ;)
Connection-specific DNS Suffix . : home.arpa Description . . . . . . . . . . . : Killer E2600 Gigabit Ethernet Controller Physical Address. . . . . . . . . : B0-4F-13-0B-FD-16 DHCP Enabled. . . . . . . . . . . : Yes Autoconfiguration Enabled . . . . : Yes IPv4 Address. . . . . . . . . . . : 192.168.9.100(Preferred) Subnet Mask . . . . . . . . . . . : 255.255.255.0 Lease Obtained. . . . . . . . . . : Wednesday, March 6, 2024 2:02:01 PM Lease Expires . . . . . . . . . . : Monday, March 18, 2024 2:02:00 PM Default Gateway . . . . . . . . . : 192.168.9.253 DHCP Server . . . . . . . . . . . : 192.168.9.253 DNS Servers . . . . . . . . . . . : 192.168.3.10 NetBIOS over Tcpip. . . . . . . . : EnabledI would love to hear your theory how anyone could use that to do anything? That doesn't already have full access to my network anyway..
-
@johnpoz bro now I can run airsnort on your network and packet sniff hahahaha. Jk
-
@Sergei_Shablovsky said in Do you use dhcp reservations?:
give You flexibility when hardware changes
New hardware? What's that?? My company runs on Dell blades from 2012. We don't ever get new hardware because that would cost more than zero. Same with our desktops.
-
@johnpoz Yes, I use dhcp reservations for my wireless clients, but sometimes it does not quite work as I would Like. It works hand in hand with my macsec implementation and hardens my certificate based user auth and aids in my acl implementation.
-
@Epimpin
That means you are going to spend a lot of time chasing MACs for all devices that come into your network. I have better things to do with my time than track every iPhone or whatever IP devices that comes into my network. Those devices are not going to work without you setting up the MAC for a DHCP reservation. Create a setup so it can be automated. And that means don't use DHCP reservations as it is too limiting. Use DHCP for a general class of devices. You can use scopes to separate devices and classes. -
@coxhaus
Well it all starts with having a good understanding of what a mac address consists of. For instance, the first 6 digits(3 octets) tell you who manufacures the device and when and is called an OUI.I have a locally stored OUI database installed in my auth scheme and I have ACL'S that block any device made by Huawei for instance and sends them to a walled garden with a message regarding Huawei devices with specific information.
You should know what type of devices you should expect on your network. With some simple network automation you don't have to "chase" mac addresses.
Then for things like switch to switch communications in your core, you should only ever see mac addresses of the neighboring switch. It doesn't have to be hard.
The dhcp reservations work well for allowing my roaming clients in my wireless networks to maintain a consistent connection and also allows my gigamon boxes to assign an identifier and gives good deduplication and solid subscriber tracking and less logging without having to implement a complex gtp/gprs configuration.
It works for me.
-
@Epimpin
I am glad it works for you. If you work on a network with 4 or 5 thousand PCs plus devices you are not going to be able to do that and do your job.You are building a structure that is going to be limited.
-
@coxhaus the reservations is more for tracking specific devices and or needs. Smaller networks yes it’s ok, but for thousands it gets harder to keep track of. A way around this is to set the dhcp pool lease timers really high so devices get the same IP address each time.
-
@JonathanLee
Plus using long DHCP lease times reduces your broadcast traffic immensely. Reducing the loads on your network. -
Number one reason for using dhcp reservation in my house is to allow me to direct the kids to different Pi-holes as they get older. This allows me to control YouTube restrictions and filter settings by maturity. All outside dns is blocked and I have a lot of fail safes in place that land “new” devices in the most restrictive Pi-hole group. This has worked really well until they get savvy. Then I have to decide if it is worth playing the cat and mouse game.
The pi-hole remote app is great because it has built in blocking controls for things like Roblox and discord. I can switch one kid off if they aren’t doing their homework or whatever.
-
@cwagz I also have controls set up with mine and the LEDs on the firewall change if someone is on devices at night that should be sleeping. I customized the LEDs to state specific activation.
-
DHCP reservations allow us to have the ease, simplicity and benefits of DHCP without some of its pitfalls allowing us to rely on and use persistence of IP as a tool in other implementations and tools.
Ive seen how it works on other systems and it almost never works the way it should or how you think it should, but on pfsense it just simply works and as you would expect (most of the time).
-
@JonathanLee Why not use time based rules instead of LED lights you have to monitor?
https://docs.netgate.com/pfsense/en/latest/firewall/time-based-rules.html
-
@ahking19 shared devices sometimes I want to watch a streaming movie at night is all
-
@johnpoz said in Do you use dhcp reservations?:
@JonathanLee said in Do you use dhcp reservations?:
I do not want any mac address cloning going on.
Who is going to clone your macs?
Hackers. Black hackers.
Or cyber warriors from China, Iran, russia. (They are in 120-180ms distance from Your data ;)And for what purpose?
Steal money. Or steal some info about Your clients to steal MUCH MORE money from them.
2.
Make damage for Your country.Mac cloning is only a thing if they are already on your network..
Because around 80% of devices at home, work and office are connected by WiFi, airsnort, fake DHCP server for MITM doing work well.
I would love to hear your theory how anyone could use that to do anything? That doesn't already have full access to my network anyway..
Hm. Are You serious? I do not believe that You say that…
BTW, I prefer to using “IP reservation “ feature ONLY as some sort of helpful feature in administration and of pf rules work.
And THIS IS NOT AS A SECURITY BARRIER any way!When planning infrastructure each one need to keep in mind that MAC/IP - NOT MAKE DEVICE TRUSTED, this is just ID.
And like Your passport w/o photo or biometric chip,- may be stealing by someone.One of the basic rules nowadays must be: EACH DEVICE MUST HAVE OWN SERTS. NO SERTS,- NO ANY RIGHTS, NO ACCESS ANYWHERE !
Am I wrong?
-
 G Gertjan referenced this topic on
G Gertjan referenced this topic on
