Verizon CR200a in ip passthrough?
-
The rule should route all traffic unless you specifically set it for TCP only.
Interesting. Do you see any unexpected blocked traffic in the firewall logs?
-
@stephenw10 Your example showed TCP only, and that's the default, so I assumed that was the correct option. Should I change it to "any"?
@stephenw10 said in Verizon CR200a in ip passthrough?:
Do you see any unexpected blocked traffic in the firewall logs?
I guess it depends on what you mean by 'unexpected'. I have no idea I'm looking at, so it's all unexpected to me. lol
Seriously, though, I have to revert my settings to default back to the DSL between messages, so that my whole network isn't unusable and my wife kills me. ;)
Let me go try it an see what happens and I'll post a screenshot. You can tell me what you see... -
@stephenw10 said in Verizon CR200a in ip passthrough?:
Do you see any unexpected blocked traffic in the firewall logs?
This does look suspicious. It appears to pop up when I attempt to open a ZeroTier session.
I know my IP is visible. There are just too many to redact. :/
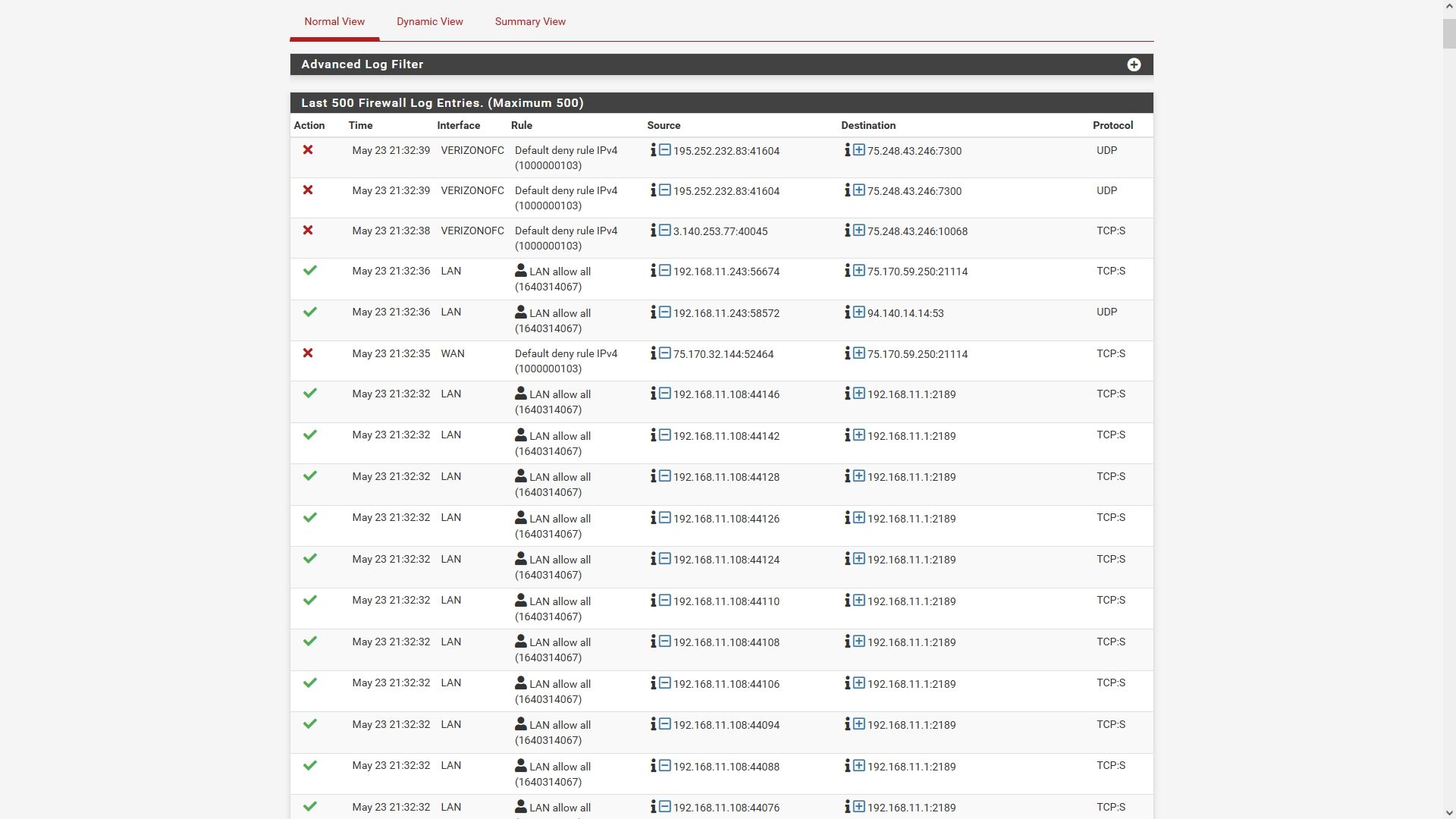
-
@Elmojo said in Verizon CR200a in ip passthrough?:
Your example showed TCP only,
Doh! So it did. Yeah set that to any protocol and retest.
-
@stephenw10 I did. The image above is with it set to "any".
-
Ok does Zerotier work now?
Nothing in that log looks unexpected. Though you are logging passed traffic on LAN so that is most of the log. Try filtering it by only blocked traffic. Anything blocked on LAN or blocked outbound would be unexpected.
-
@stephenw10 said in Verizon CR200a in ip passthrough?:
Anything blocked on LAN or blocked outbound would be unexpected.
So sorry for the long delay. I was out of town over the weekend.
Yeah, I don't see anything blocked on LAN or outbound, but youtube still isn't working on Verizon.
I've added an easyrule for a certain port I saw popping up when I tried to access ZeroTier, and now that's kinda working, but not as smooth or quickly as it does on the DSL.
Here's a new log, with a 'block' filter applied. Looks like a lot of blocked incoming traffic to me, given the short time span shown, and the fact that I'm not actively doing anything at the time, but maybe that's normal these days?
I just can't figure what would be causing these roadblocks, but I won't be able to keep Verizon as my ISP if it's going to cause issues with certain services and sites.
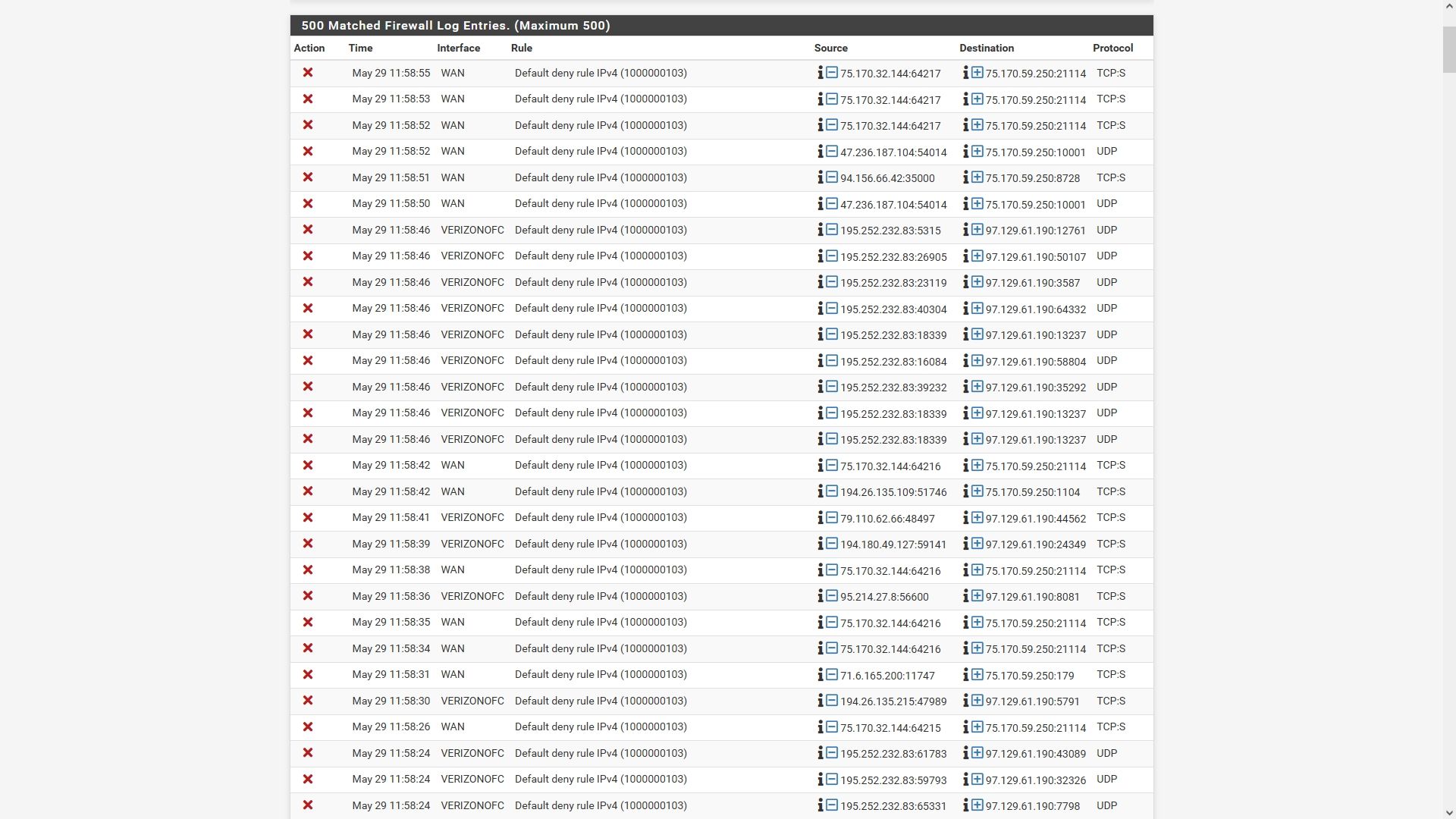
-
Hmm, so with the policy routing rule sending al traffic from the test host via the DSL WAN you are still seeing some issues connecting from that?
-
@stephenw10 said in Verizon CR200a in ip passthrough?:
Hmm, so with the policy routing rule sending al traffic from the test host via the DSL WAN you are still seeing some issues connecting from that?
@Elmojo said in Verizon CR200a in ip passthrough?:
With the rule in place, and the Verizon gateway set as default, my desktop works...sorta. Youtube videos play, but my ZeroTier tunnel is still broken
No, if I enable that policy routing rule, then my desktop mostly works. But that's just a temporary test, since the idea is for eventually the DSL WAN to go away, and only to have the Verizon WAN.
It appears that whatever the issue is, it's some sort of conflict between the Verizon ISP and the configuration of my desktop. I just can't imagine what it would be. I've tried changing my DNS servers back to defaults, turning my software firewall off, and even disabling my antivirus temporarily. None of it makes any difference.
-
Right. But that fact that test host doesn't work it did before even when it's traffic is routed via DSL implies the problem could be due to the existence of the dual WANs rather than which WAN it's using.
For example if the DNS is broken because that is all going via WAN2.
You see all configured DBS servers responding in Diag > DNS Lookup still though?
-
@stephenw10 said in Verizon CR200a in ip passthrough?:
For example if the DNS is broken because that is all going via WAN2.
WAN2 being the new Verizon ISP?
I'm not sure what exactly I'm seeing when I perform a DNS lookup. This looks weird to me. Does it look correct to you?
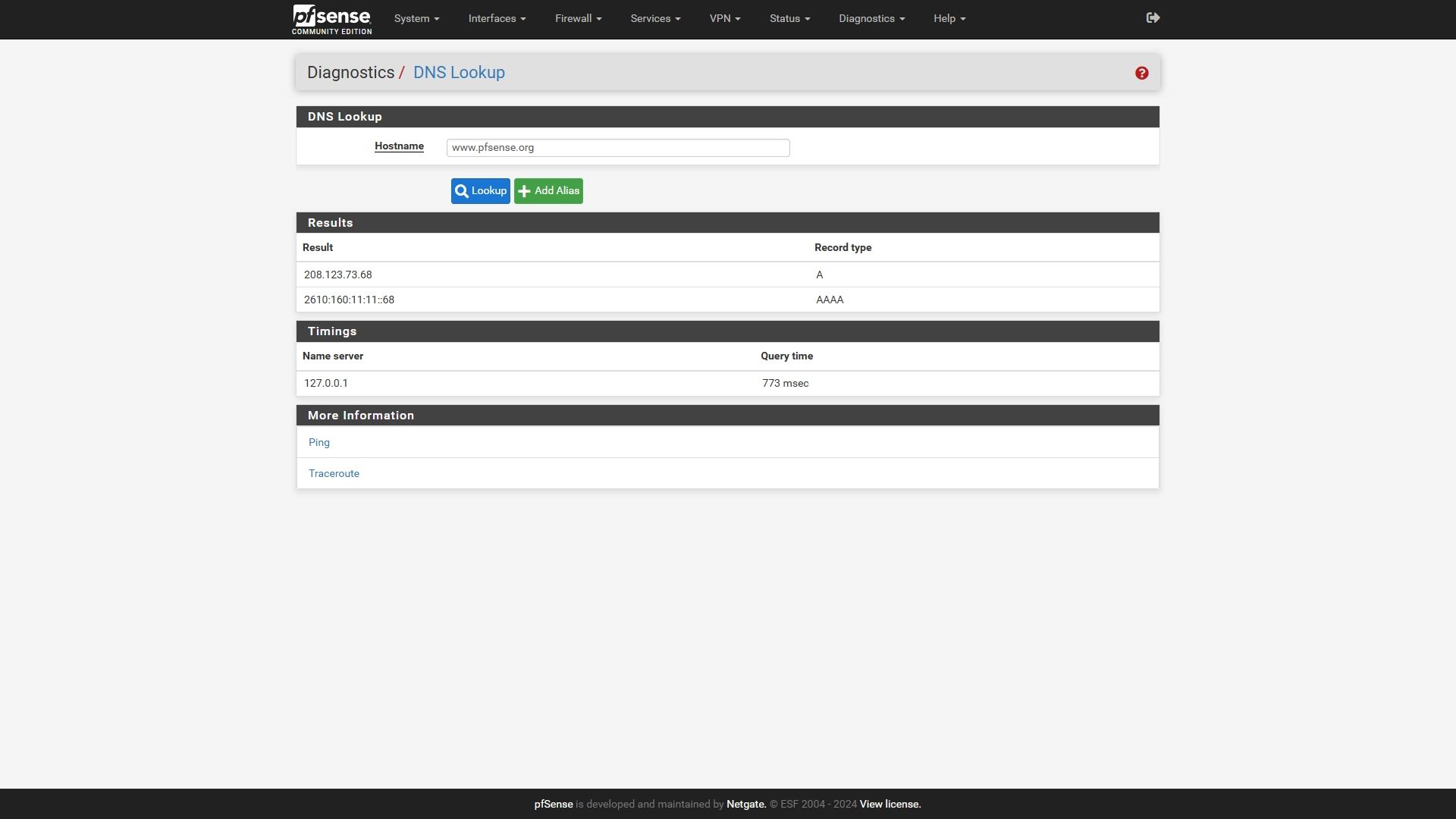
I mean, should I be seeing the localhost address under the name server?
-
Yes localhost is the default. That means the system queries Unbound running locally.
The slightly odd thing there is that there are no other DNS servers set. Usually servers would be passed to the system from the ISP when the WAN connects via DHCP or PPPoE. So in your case I'd expect to that from both WANs.
-
@stephenw10 Where would you expect the DNS servers to be set? Is that something that I would have config'd in unraid, in pfsense, or on an individual machine? I am running specific DNS servers on my desktop (adguard for ad blocking), but I don't recall setting anything special anywhere else. If I was ever asked to specify DNS servers, it would have been either Google (8.8.8.8/8.8.4.4) or maybe Cloudflare (1.1.1.1).
-
I expect them to be passed to pfSense over DHCP or PPPOE when they connect. That wouldn't happen if your WANs are both statically assigned?
-
@stephenw10 said in Verizon CR200a in ip passthrough?:
I expect them to be passed to pfSense over DHCP or PPPOE when they connect. That wouldn't happen if your WANs are both statically assigned?
So they should be automatically assigned by the ISP(s)? Is there any way for me to check?
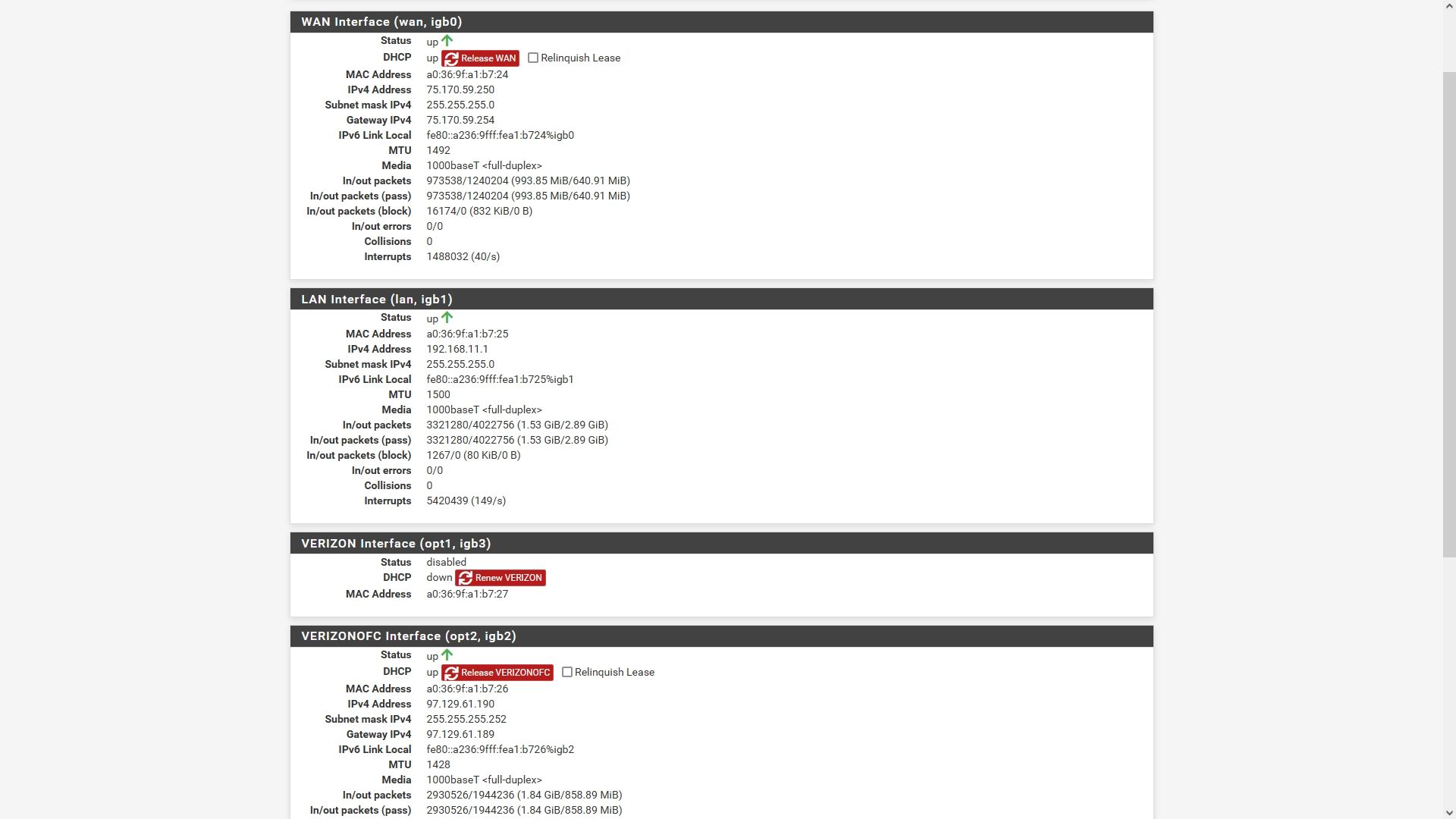
-
You should see them in Status > Interfaces on the WANs like:
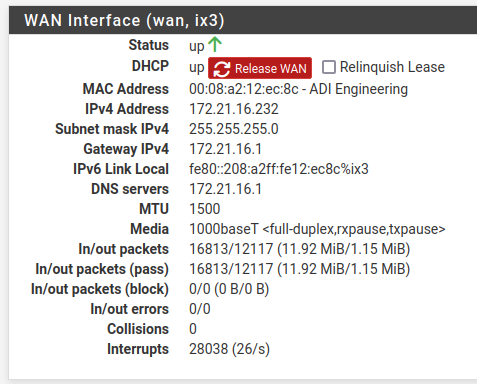
However this should wok fine with only the local resolver. The only reason it may not is because that will use the default route to reach the root servers and that has now changed to WAN2.
-
@stephenw10 Weird, no mention of DNS on either WAN.
I'm not sure I quite follow your 2nd statement. Are you saying it's trying to use the DNS servers from my original WAN, but it's connecting through the new Verizon WAN, and getting confused?
-
Well that's odd that neither DHCP server passes any DNS server to use but that shouldn't cause an issue by itself.
The DNS resolver (Unbound) should always work. But what may have changed here is that traffic from Unbound is now using WAN2.
So one thing you can try is setting the outbound interface Unbound is using using in Services > DNS Resolver. If you set that to WAN (DSL) instead of all that puts the system back in the same conditions it was before adding the second WAN. The test host being routed via DSL should work as before at that point.
-
@stephenw10 I'll give that a try, thanks. Would you suggest leaving the routing rule in place, or removing it temporarily while testing the DNS thing?
If I leave it in please, I'm thinking we won't know which one is fixing the trouble, since everything is working fine right now, with the rule active...
Is that wrong? -
I would leave the rule in place initially.
If moving the outgoing DNS to the old WAN appears to fix things then try disabling to the policy routing rule and see if it's still good. I doubt it will though TBH