Unbound DNS Resolver not starting
-
I disabled a few interfaces a few days ago but that change also reflected on the backup node. Yes, DHCP Registration is disabled. WHat I don't understand is why the logs are not showing my startup attempts.
Question: Is it possible to reinstall unbound? Or maybe I reset the config? If so, how would I go about that?
-
@Gertjan Also, do you know if pfBlocker could have messed with unbound?
-
@KKIT said in Unbound DNS Resolver not starting:
Question: Is it possible to reinstall unbound?
Noop. I don't think so.
It's just an executable. And some support files like unbound-control etc.@KKIT said in Unbound DNS Resolver not starting:
Or maybe I reset the config?
This is pfSense.
This is FreeBSD.
This means : we all have the same identical binary executable Library etc files.
Only our "config file" file is different : it's here /var/unbound/unbound.conf
and this file is re generated just before pfSense starts unbound.
Like any other process on the system.@KKIT said in Unbound DNS Resolver not starting:
If so, how would I go about that?
I would : open a console or SSH to pfsense, go médecin mode (option 8) and :
tail -f /var/log/resolver.logNow, in the GUI, interact with unbound and see what the log tailing tells you.
In another SSH session, medecin mode, use :topOn another SSH, option also, use
dig @127.0.0.1 google.com +traceto question unbound with a hots name lookup. You should repeat this test as often as possible.
Normally, unbound should listen to 127.0.0.1 - and you should receive an answer.Ask if unbound is running, lists on what interface it listens :
24.03-RELEASE][root@pfSense.bhf.tld]/root: sockstat | grep 'unbound' unbound unbound 39327 3 udp6 *:53 *:* unbound unbound 39327 4 tcp6 *:53 *:* unbound unbound 39327 5 udp4 *:53 *:* unbound unbound 39327 6 tcp4 *:53 *:* unbound unbound 39327 7 tcp4 127.0.0.1:953 *:* unbound unbound 39327 8 dgram -> /var/run/log unbound unbound 39327 10 stream -> [39327 12] unbound unbound 39327 12 stream -> [39327 10] unbound unbound 39327 13 stream -> [39327 14] unbound unbound 39327 14 stream -> [39327 13]The first 4 lines means : unbound listens on port 53 :
For UDP and TCP
For IPv4 and IPv6
For every interfaceBtw : these are not really 'pfSense instructions'. Not even FreeBSD instruction - or Linux for that matter. These commands are - with some nuances - avaible on every OS on planet earth ^^
-
@Gertjan said in Unbound DNS Resolver not starting:
tail -f /var/log/resolver/log
Thanks for your suggestions, right off the bat, I get this:
tail: /var/log/resolver/log: No such file or directoryI went in with option 8, as you mentioned. So I guess there is a deeper rooted issue. Do you suggest I reinstall pfSense and load from a backup?
-
@KKIT I did fiddle with the Unbound settings yesterday and wasn't able to start Unbound. In my case it turned out that Unbound wasn't stopped cleanly and the therefore couldn't bind to port 53.
Maybe check that no Unbound instance is running. Under Diagnostics / Command Prompt and run:
ps aux | fgrep -i unbound unbound 38035 0.0 4.3 210648 175800 - Is 16:11 0:47.64 /usr/local/sbin/unbound -c /var/unbound/unbound.conf root 52767 0.0 0.1 13400 3020 - S 14:20 0:00.00 sh -c ps aux | fgrep -i unbound 2>&1 root 53148 0.0 0.1 12832 2496 - S 14:20 0:00.00 fgrep -i unboundAnd set LogLevel to at least 2 for the testing.
-
@KKIT said in Unbound DNS Resolver not starting:
tail: /var/log/resolver/log: No such file or directory
tail -f /var/log/resolver.log
-
@patient0 said in Unbound DNS Resolver not starting:
unbound 38035 0.0 4.3 210648 175800 - Is 16:11 0:47.64 /usr/local/sbin/unbound -c /var/unbound/unbound.conf
I get this when putting in line 2
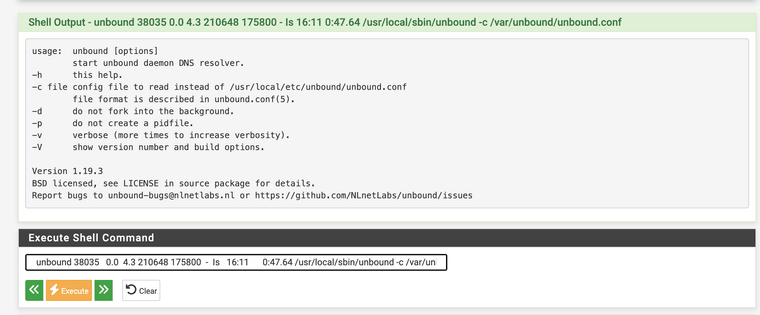
-
@KKIT I'm sorry I wasn't clear: you enter only the first line
ps aux | fgrep -i unboundand the other lines are the result of that command in my case. -
Nooooo.
Never - ever use the GUI Diagnostics > Command Prompt
GUI command line is ... bad, or worse.
Use SSH. -
@fireodo said in Unbound DNS Resolver not starting:
@KKIT said in Unbound DNS Resolver not starting:
tail: /var/log/resolver/log: No such file or directory
tail -f /var/log/resolver.log
I did and nothing changes in the log when I try to adjust anything
-
Thanks, I get this:
root 64053 0.0 0.0 13412 3064 - S 14:46 0:00.00 sh -c ps aux | fgrep -i unbound 2>&1
root 64286 0.0 0.0 12840 2532 - S 14:46 0:00.00 fgrep -i unbound -
@KKIT said in Unbound DNS Resolver not starting:
I did and nothing changes in the log when I try to adjust anything
With :
you will only see the start and stop lines.
When a stop arrives, unbound will log about 30 "info" lines, the ones you've showed above.Btw : when you change edit whatever do something with the 3 unbound (revolver) settings pages, unbound won't get restarted. So no log lines.
Only when you click on Apply on the top of any resolver settings page, unbound will get stopped, a new config file gets created, and unbound gets started. Then you see the the stop announcement, dump of the info and the the restart line.With a log level of 3, 4 or a whopping 5 you will see much more.
Remember to reset to "1" when you're done (and apply ^^), as with level 5 unbound will log huge quantities. -
@KKIT said in Unbound DNS Resolver not starting:
Thanks, I get this:
root 64053 0.0 0.0 13412 3064 - S 14:46 0:00.00 sh -c ps aux | fgrep -i unbound 2>&1
root 64286 0.0 0.0 12840 2532 - S 14:46 0:00.00 fgrep -i unboundOk, that means no Unbound instance is running at that time. Next I'd set the LogLevel to > 1.
Do you have a fairly standard Unbound config? Running as a resolver or forwarder? Nothing else listening to port 53?
-
Unfortunately absolutely nothing happens when I set it to 5, I am still connected via SSH and within the logfile with tail, I also made sure to apply the settings as well as manually start the service under the "Services" section, nothing :(
-
I set the log level to 5 and still nothing, only the second node is listening on port 53 and the resolver is running as expected. No custom configuration on unbound and no DNS forwarder active.
-
I've just :
tail -f /var/log/resolver.logand then :
and then
and oh boy .... the tail command had a hard time keeping up with the pace. tens of lines a second, impossible to follow.
Btw : I've no HA setup, just one box, and about 5 PC connected and some other stuff.
I know that every device in my network uses my 'pfSense' as a DNS source, not some 1.1.1.1 or 8.8.8.8 or other data collector.If your unbound doesn't log anything on level 5 : isn't that a sign that LAN devices uses another device, and not (this !) pfSense, to do DNS requests ?
Another trick : GUI this time ^^
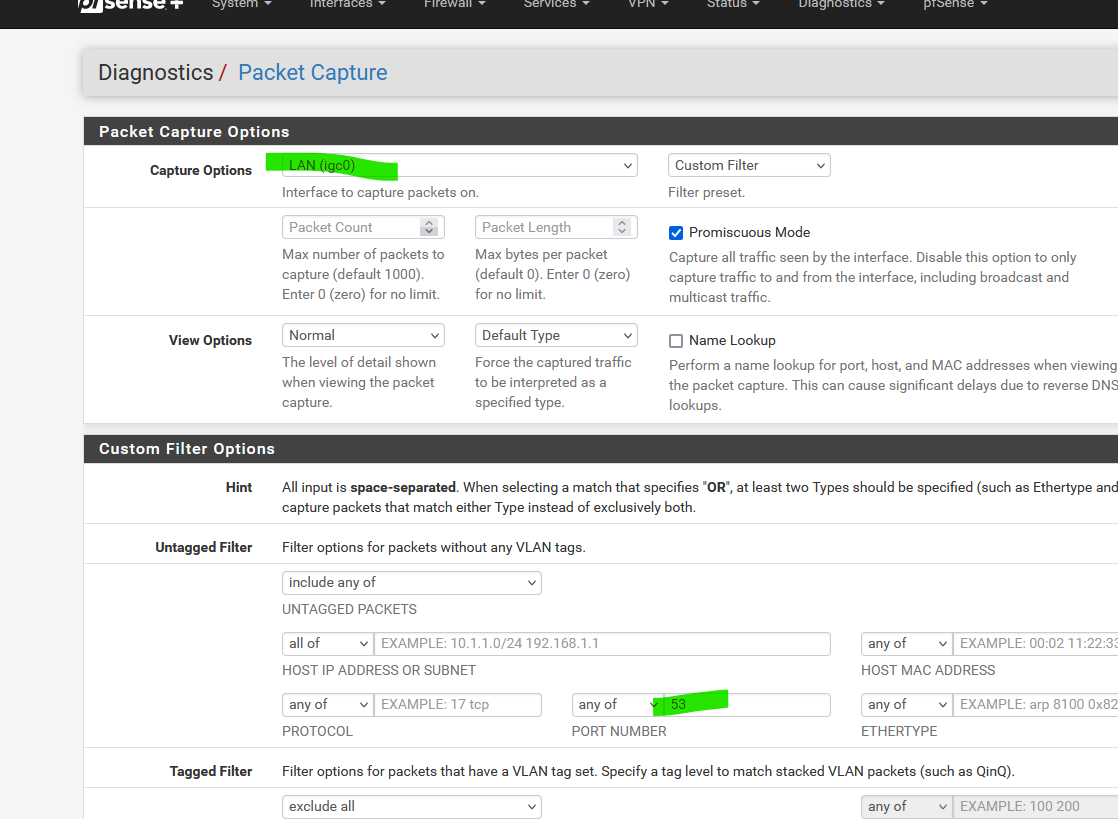
Set interface to your LAN interface, or any other LAN type interface.
Set the port to '53' (DNS, recall)
And hit Start.Now you should see "destination port 53".
Add the IP of your pfSense, so now you'll see what LAN devices want to talk to your pfSense for DNS needs :
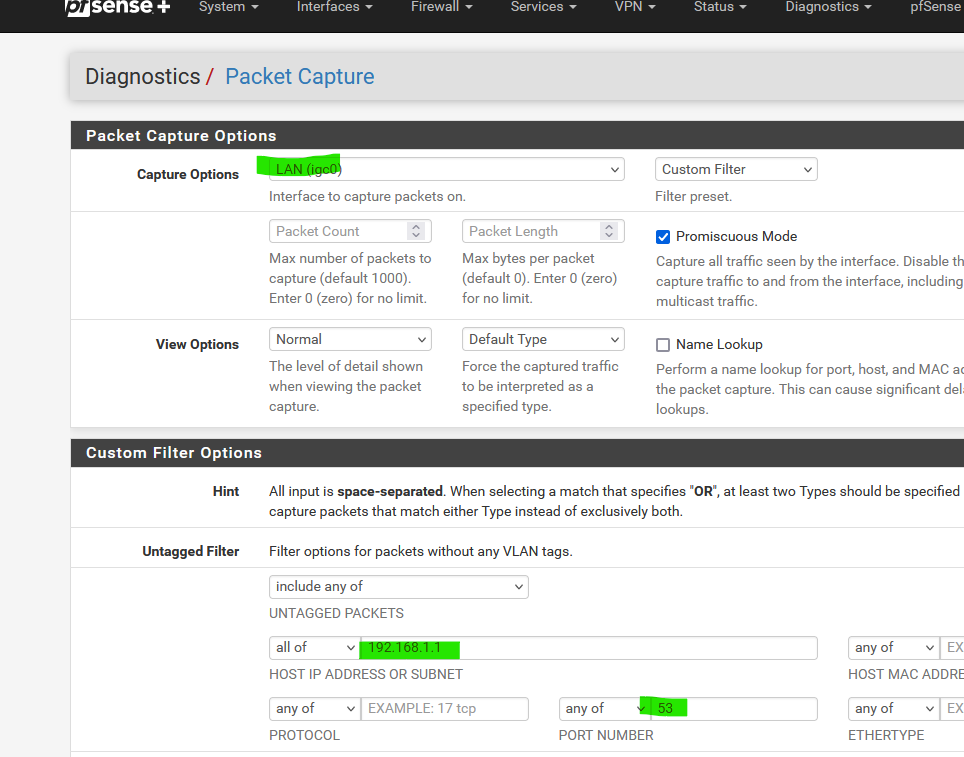
Btw : I presume the default 192.168.1.1
if there is no ore little DNS traffic, its normal that unbound doesn't 'log' ^^ -
@Gertjan
I appreciate the input, but I think we are looking at the wrong end here. The Unbound service is not running at all, as confirmed above. Additionally, the node is currently in maintenance mode, I already tried putting it back into production but I wouldn't accept any requests. At this point I assume that either pfBlocker messed it up or I improperly shut the service down. I will go for a reinstall and see from there. THanks so far, really appreciate it and will keep you guys updated! -
So I wanted to give a followup on this issue, I dug a little deeper and looking at this post:
https://forum.netgate.com/topic/154372/unbound-dns-resolver-will-not-start/3I am pretty sure it has something to do with pfBLockerNG messing up my config file. I checked the directory of the config file and see that there are two with one having a ".error" added to it:
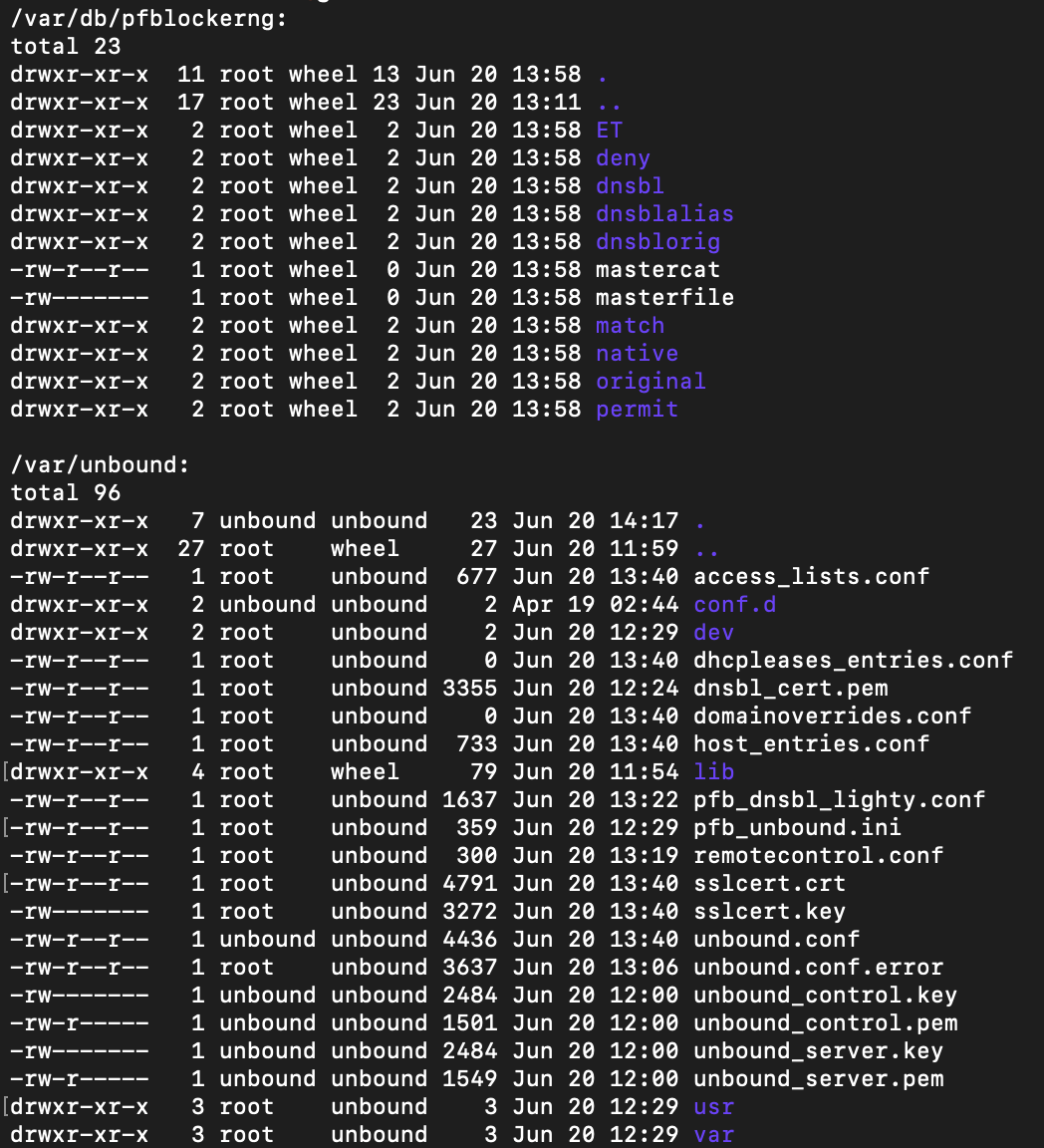
Trying to reload unbound via shell shows this error:
unbound-control[85585:0] error: connect: Connection refused for 127.0.0.1 port 953Unfortunately I lost my backups after the reinstall so my question is if I can transfer the unbound.conf from my functioning pfSense (Node B) to make it work again?
-
@KKIT said in Unbound DNS Resolver not starting:
I am pretty sure it has something to do with pfBLockerNG messing up my config file.
Easy to test.
Remove pfBlockerng from your pfSEnse, and get a copy from the unbound config file.
/var/unbound/unbound.confInstall pfBlockerng, activate it, give it some DNSBL feeds and get a copy again from the unbound config file.
Compare the two copies.
You'll find a single difference, at the end :
If you use Python mode :# Python Module python: python-script: pfb_unbound.pyIMHO : this small python script file is very well tested by now.
Not python mode :
It "includes" a (one) 'master DNSBL' file ... forget about that file, as I switched to python mode (after years asking for it).So, no, sorry, dead end.
pfBlockerng can restart unbound ones in a while (you decide how often).
But pfBlockerng isn't the only one doing so, other, network events for example, can also restart many services.Edit :
Your unbound. conf file is rather big = 4k.
Mine is just over 2k.
Can you show it ? -
Sure
##########################
Unbound Configuration
##########################
Server configuration
server:
chroot: /var/unbound
username: "unbound"
directory: "/var/unbound"
pidfile: "/var/run/unbound.pid"
use-syslog: yes
port: 53
verbosity: 1
hide-identity: yes
hide-version: yes
harden-glue: yes
do-ip4: yes
do-ip6: yes
do-udp: yes
do-tcp: yes
do-daemonize: yes
module-config: "iterator"
unwanted-reply-threshold: 0
num-queries-per-thread: 512
jostle-timeout: 200
infra-keep-probing: yes
infra-host-ttl: 900
infra-cache-numhosts: 10000
outgoing-num-tcp: 10
incoming-num-tcp: 10
edns-buffer-size: 1432
cache-max-ttl: 86400
cache-min-ttl: 0
harden-dnssec-stripped: no
msg-cache-size: 4m
rrset-cache-size: 8mnum-threads: 4
msg-cache-slabs: 4
rrset-cache-slabs: 4
infra-cache-slabs: 4
key-cache-slabs: 4
outgoing-range: 4096
#so-rcvbuf: 4mprefetch: yes
prefetch-key: yes
use-caps-for-id: no
serve-expired: no
sock-queue-timeout: 0
aggressive-nsec: noStatistics
Unbound Statistics
statistics-interval: 0
extended-statistics: yes
statistics-cumulative: yesTLS Configuration
tls-cert-bundle: "/etc/ssl/cert.pem"
Interface IP addresses to bind to
interface: WAN NODE B
interface: 172.16.71.2
interface: 2001:0db8:85a3:0000:0000:8a2e:0370:7334
interface: 172.16.1.2
interface: 10.0.20.2
interface: 10.0.30.2
interface: 10.0.90.2
interface: 10.0.91.2
interface: 10.0.31.2
interface: 172.16.71.1
interface: WAN NODE A
interface: 10.0.20.1
interface: 10.0.30.1
interface: 10.0.90.1
interface: 10.172.17.1
interface: 10.0.91.1
interface: NETWORK A
interface: NETWORK B
interface: NETWORK C
interface: 10.0.40.1
interface: NETWORK D
interface: NETWORK E
interface: 10.0.31.1
interface: NETWORK F
interface: 127.0.0.1
interface: ::1Outgoing interfaces to be used
outgoing-interface: WAN NODE B
outgoing-interface: 172.16.71.2
outgoing-interface: xxx
outgoing-interface: 172.16.1.2
outgoing-interface: 10.0.20.2
outgoing-interface: 10.0.30.2
outgoing-interface: 10.0.90.2
outgoing-interface: 10.0.91.2
outgoing-interface: 10.0.31.2
outgoing-interface: 172.16.71.1
outgoing-interface: WAN NODE A
outgoing-interface: 10.0.20.1
outgoing-interface: 10.0.30.1
outgoing-interface: 10.0.90.1
outgoing-interface: 10.172.17.1
outgoing-interface: 10.0.91.1
outgoing-interface: NETWORK A
outgoing-interface: NETWORK B
outgoing-interface: NETWORK C
outgoing-interface: 10.0.40.1
outgoing-interface: NETWORK D
outgoing-interface: NETWORK E
outgoing-interface: 10.0.31.1
outgoing-interface: NETWORK F
outgoing-interface: 127.0.0.1
outgoing-interface: ::1DNS Rebinding
For DNS Rebinding prevention
private-address: 127.0.0.0/8
private-address: 10.0.0.0/8
private-address: ::ffff:a00:0/104
private-address: 172.16.0.0/12
private-address: ::ffff:ac10:0/108
private-address: 169.254.0.0/16
private-address: ::ffff:a9fe:0/112
private-address: 192.168.0.0/16
private-address: ::ffff:c0a8:0/112
private-address: fd00::/8
private-address: fe80::/10Access lists
include: /var/unbound/access_lists.conf
Static host entries
include: /var/unbound/host_entries.conf
dhcp lease entries
include: /var/unbound/dhcpleases_entries.conf
Domain overrides
include: /var/unbound/domainoverrides.conf
Forwarding
forward-zone:
name: "."
forward-tls-upstream: yes
forward-addr: ::1@853
forward-addr: 1.1.1.1@853#one.one.one.one
forward-addr: 1.0.0.1@853#one.one.one.one
forward-addr: 8.8.8.8@853#dns.google
forward-addr: 8.8.4.4@853#dns.googleRemote Control Config
include: /var/unbound/remotecontrol.conf