Access Modem GUI Behind Firewall
-
@johnpoz said in Access Modem GUI Behind Firewall:
DON'T Set the gateway on the rule so pfsense can use its normal routing.. It is attached to the 192.168.5 network - it knows how to get there - you can ping it right.. So why would you think you should force it out the pppoe connection.
The rules say nothing of the sort.
If your doing auto nat, pfsense would change your lan connection to the 192.186.5.2 address when talking to the vigor .1 address. Unless you have modified your outbound nat this should be clicky clicky.
You have multiple wan interfaces, and are doing policy routing.. You have to have rules that allow the traffic you want without policy routing.
Your taking instructions for a simple setup, one pppoe connection which normally people wouldn't policy route with and trying to apply them to your not common setup..
DON'T Set the gateway on the rule so pfsense can use its normal routing... It is attached to the 192.168.5 network - it knows how to get there - you can ping it right... So why would you think you should force it out the pppoe connection.
i don't think anything i just tried something on the advice of the other user.
The rules say nothing of the sort. ok
If your doing auto nat, pfsense would change your lan connection to the 192.186.5.2 address when talking to the vigor .1 address. Unless you have modified your outbound nat this should be clicky clicky. i have set the outboundd nat ruele as in the instructions
You have multiple wan interfaces, and are doing policy routing... You have to have rules that allow the traffic you want without policy routing ok
which ones would that be and how do i set them on my edge router i just had one nat rule and that was enough for that ?
Your taking instructions for a simple setup, one pppoe connection which normally people wouldn't policy route with and trying to apply them to your not common setup... I wasn't sure of anything so I asked if it was the Multi WAN Wan failvoer setup
-
I lost a bit the overview of what got done and what not.
If you have the patience I'd start over. For me it worked well by only creating the modem interface and the NAT Outgoing rule, nothing else needed. Even as I added a second WAN-over-USB-tethering interface and created a gateway group with it (WAN tier 1 and WAN-tethering as tier 2).
-
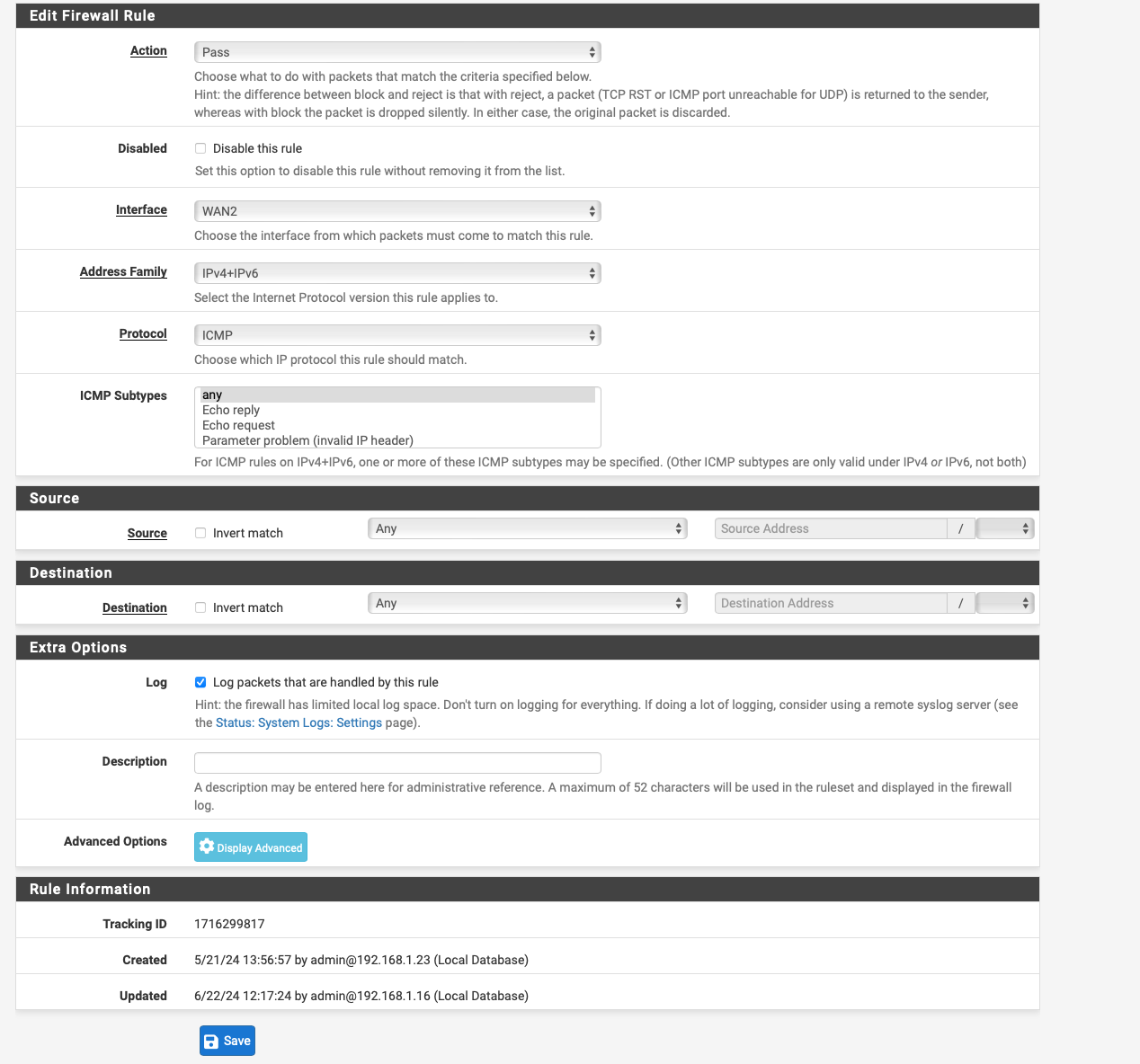
@patient0 I have now removed the gateway with 192.168.5.1 from the firewall rules as well.
yes i am also a bit confused because in the beginning i only had WAN inteferaces with multi WAN and failover setup including iPV4 gateway and V6 gateway and a gateway group with tier 1 2 3 and set this in the LAN any rule
then I worked as described in the instructions.
again it does not workI will start again from the beginning
-
@Globaltrader312 I ran/run into a bit of a problem since Friday afternoon that I loose my internet access although I get the public IP but I can't ping the ISP gateway anymore on IPv4. With that I sometimes can't access the modem either sometimes. In that case I can't ping the modem ip neither and the route to the modem/modem net is gone.
I then have to remove PPPoE and add it again, plus have to go into the modem interface and just save it. The route is there again and it voila :/ ... let's hope you don't have that strange point of <whatever the reason of it>
-
@patient0 I also had a complete outage several times a day, only 100 packet loss on all 3 WANs, a known problem when bagoon networks are blocked because the table is full, even though I use a Dell EMC 430 server for the Pfsense.
-
You need an arp entry for it to work. What interface can you ping it from?
-
-
Have you tried to set it to that interface for the floating rule? You have 3 wans so that rule would need to float to be able to be accessed in all of the interfaces. Please enable logging so we can see where it fails also. All interfaces turn on logging and after we can search for 192.168.5.1 traffic
-
@JonathanLee said in Access Modem GUI Behind Firewall:
Have you tried to set it to that interface for the floating rule? You have 3 wans so that rule would need to float to be able to be accessed in all of the interfaces. Please enable logging so we can see where it fails also. All interfaces turn on logging and after we can search for 192.168.5.1 traffic
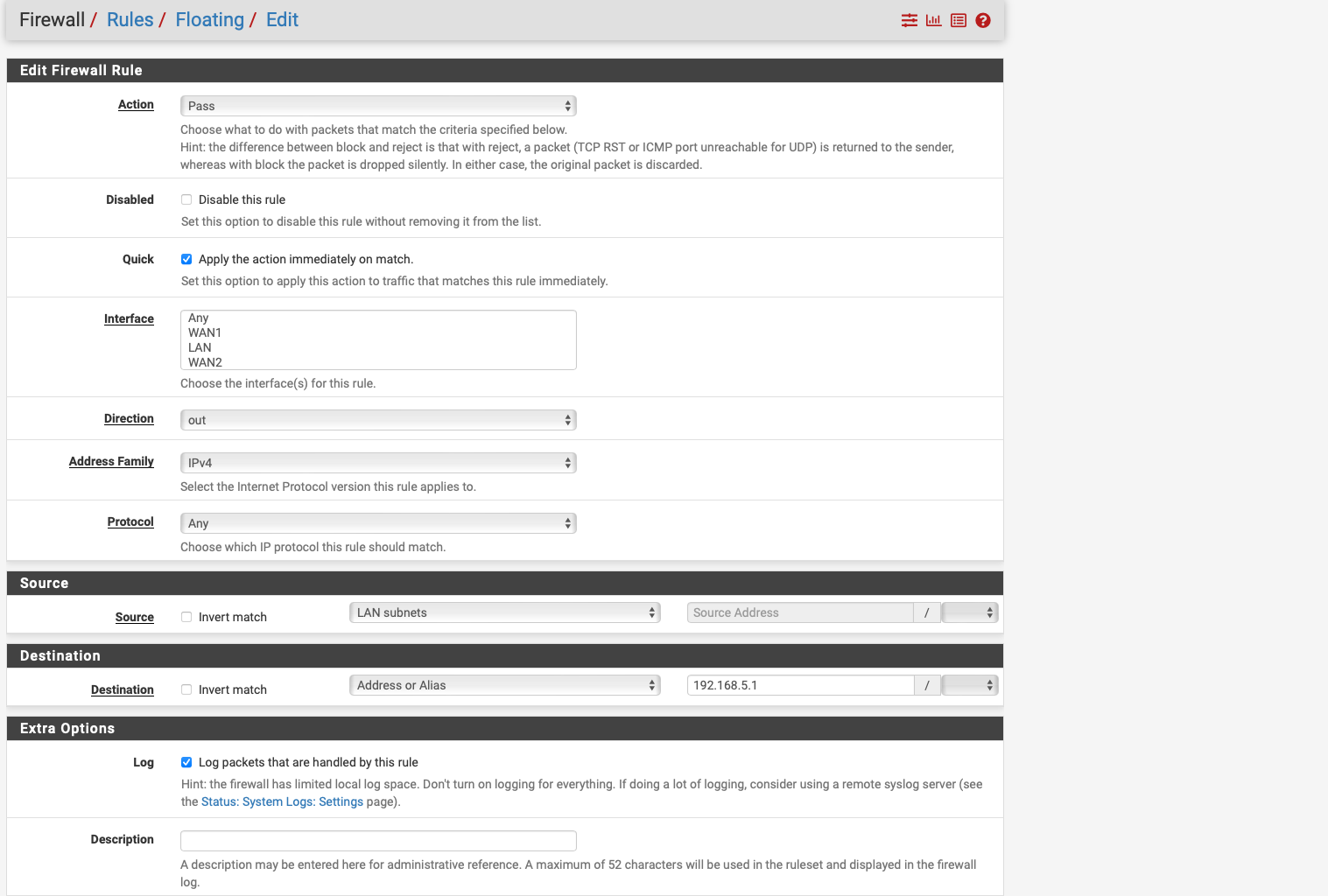
I have set the floating rule to Vigor as the interface, but I'm not sure which one I need to set to make it work.
When I ping the Vigor interface it works and is displayed in the ARP table for a while but not permanently.
Jogging ist active
-
@Globaltrader312 said in Access Modem GUI Behind Firewall:
ARP table for a while but not permanently.
why would you think it should be perm? The default arp cache is 20 minutes in freebsd/pfsense..
Why are you creating a floating rule? You don't need a floating rule, and you don't need your rule above your lock out rule.. Jut place your rule on your lan above your policy routing rules.
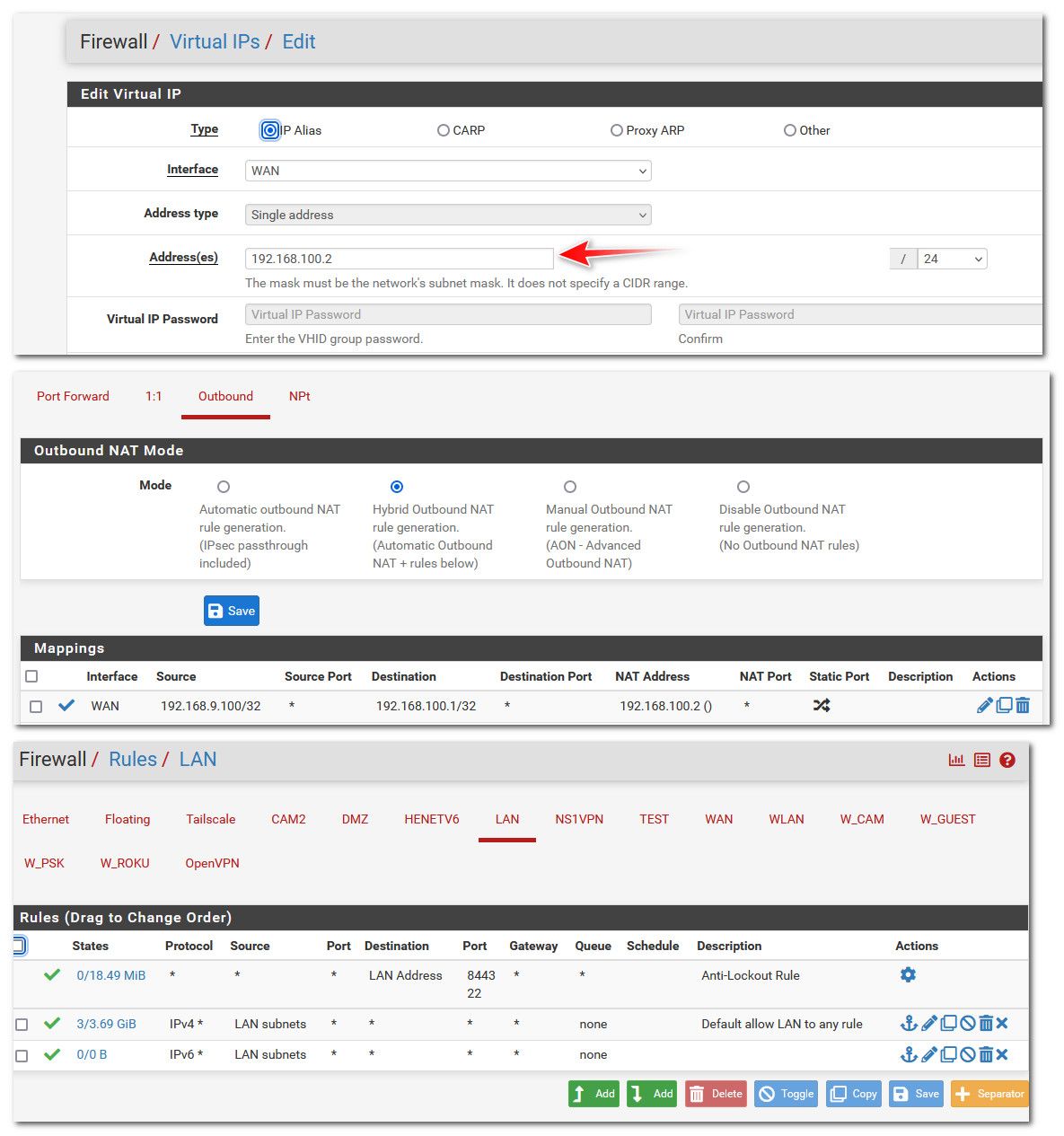
Here maybe this will help you understand what is happening.. Here is my setup to access my modems gui IP 192.168.100.1, since my pfsense gets public IP on its wan.
Created a vip (another IP on the interface) 192.168.100.2
Switched to hybrid nat so could setup outbound nat so traffic wanting to go to 192.168.100.1 was natted to my 192.168.100.2 address
My rules do not do any policy routing and allow the traffic just via normal default lan any any rule.
-
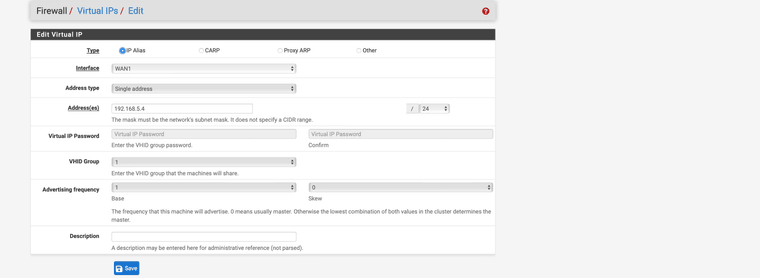
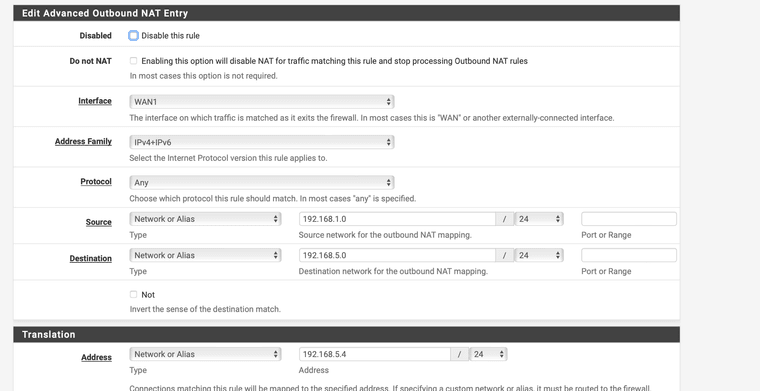
So I have now created a virtual IP with 192.168.5.4/24, which is one from the vigor subnet if I have understood it correctly, this should be correct.
then i created an outbound nat rule. i just can't enter 192.168.5.1/24 the pfsense always changes it to 192.168.5.0/24
Unfortunately it still does not work.
one thing is still not clear to me i have not created any special policy based rules but there are only the anti lockout rule and the two any to any rules and nothing more.
Which rule would I have to create so that I have access to the modem?
-
@Globaltrader312
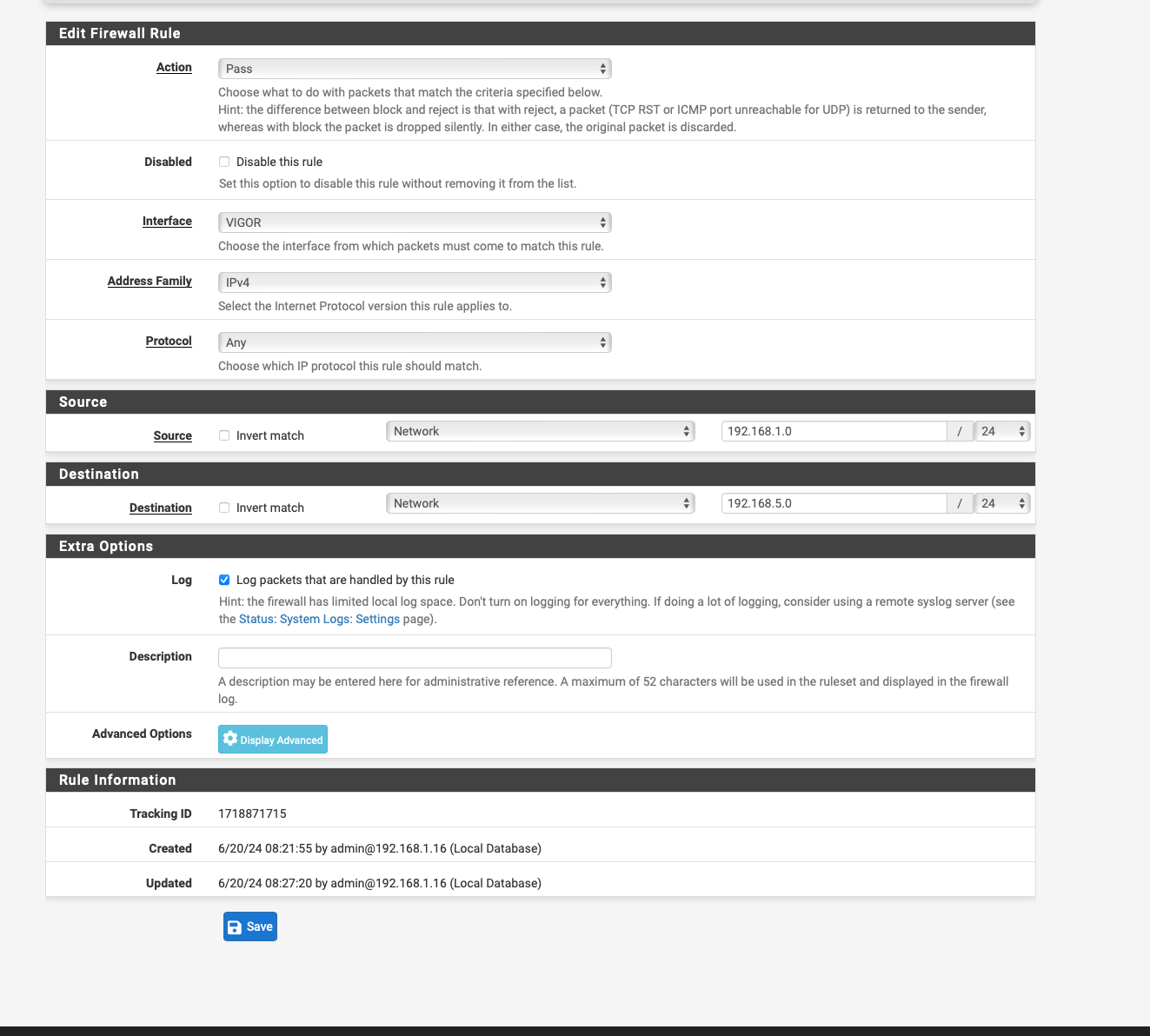
I have never used PPPoE but why do you have two separate interfaces for the WAN and the VIGOR device? Seems they are based on the igb1 interface but PPPoE sais igb1.7.I get that the VIGOR device is in MODEM mode and simply passes the public IP through to pfsense. When I had an LTE router that was working in bridge mode (modem mode) all I had to do was to create a static route to that IP/32.
Destination : 192.168.5.1 /32
Gateway : VIGOR
Description : Static route to modem UI -
i followed the instructions and there i understood it like this because pppoe only has a virtual inertafce so pppoe1 on bge 1 i have to set a second interface on bge 1 with vigor static ipv4 192.168.5.3/24 1.7 is only vlan tag 7 for dialling in to Vodafone DSL
-
@Globaltrader312 said in Access Modem GUI Behind Firewall:
So I have now created a virtual IP with 192.168.5.4/24,
I didn't say to do that - I did that because my wan interface already had a public IP on it, I do not use PPPoe..
You need an IP that can talk to 192.168.5.1 on the physical interface that is connected to your device that your PPPoe runs on..
Do you also need a vlan tag??
-
@johnpoz
then i misunderstood that i thought that would be the solution
i added the interface vigor to bge 0 and gave this interface the ip 192.168.5.3 and with this and the outbound nat rule it does not work.i thought if i did exactly that it would work.
with my other interface where i use DHCP to get the fixed IP from the ISP i can access the modem without extra rules but not with the SVDSL MOdem.
yes i need vlan tag 7 therefor the interface is 1,7
pppoe runs on bge1 / ppoe1 and the interface vigor too -
@Globaltrader312 said in Access Modem GUI Behind Firewall:
yes i need vlan tag 7 therefor the interface is 1,7
you need a vlan tag for pppoe, but do you need it to just talk to the devices IP?? That seems unlikely to me.
Forget pppoe for a second. If you connect just say a laptop to this vigor device.. Does it get a 192.168.5.x address? If so then there is no tagging needed.
-
@johnpoz said in Access Modem GUI Behind Firewall:
you need a vlan tag for pppoe, but do you need it to just talk to the devices IP?? That seems unlikely to me.
Forget pppoe for a second. If you connect just say a laptop to this vigor device.. Does it get a 192.168.5.x address? If so then there is no tagging needed.
VLAN Tag 7 is only required for dialling in to the ISP to get internet and also the public IP.
no VLAN TAG needed for 192.168.5.1 /24
if I connect my macbook to the VIGOR directly then I only have to manually set the IP 192.168.5.5 or similar once then DNS 192.168.5.1 and then I can access it directly.
-
@Globaltrader312 said in Access Modem GUI Behind Firewall:
no VLAN TAG needed for 192.168.5.1 /24
Well then why did you say you set a vlan
yes i need vlan tag 7 therefor the interface is 1,7
On the interface you created that has the 192.168.5.2 address?
-
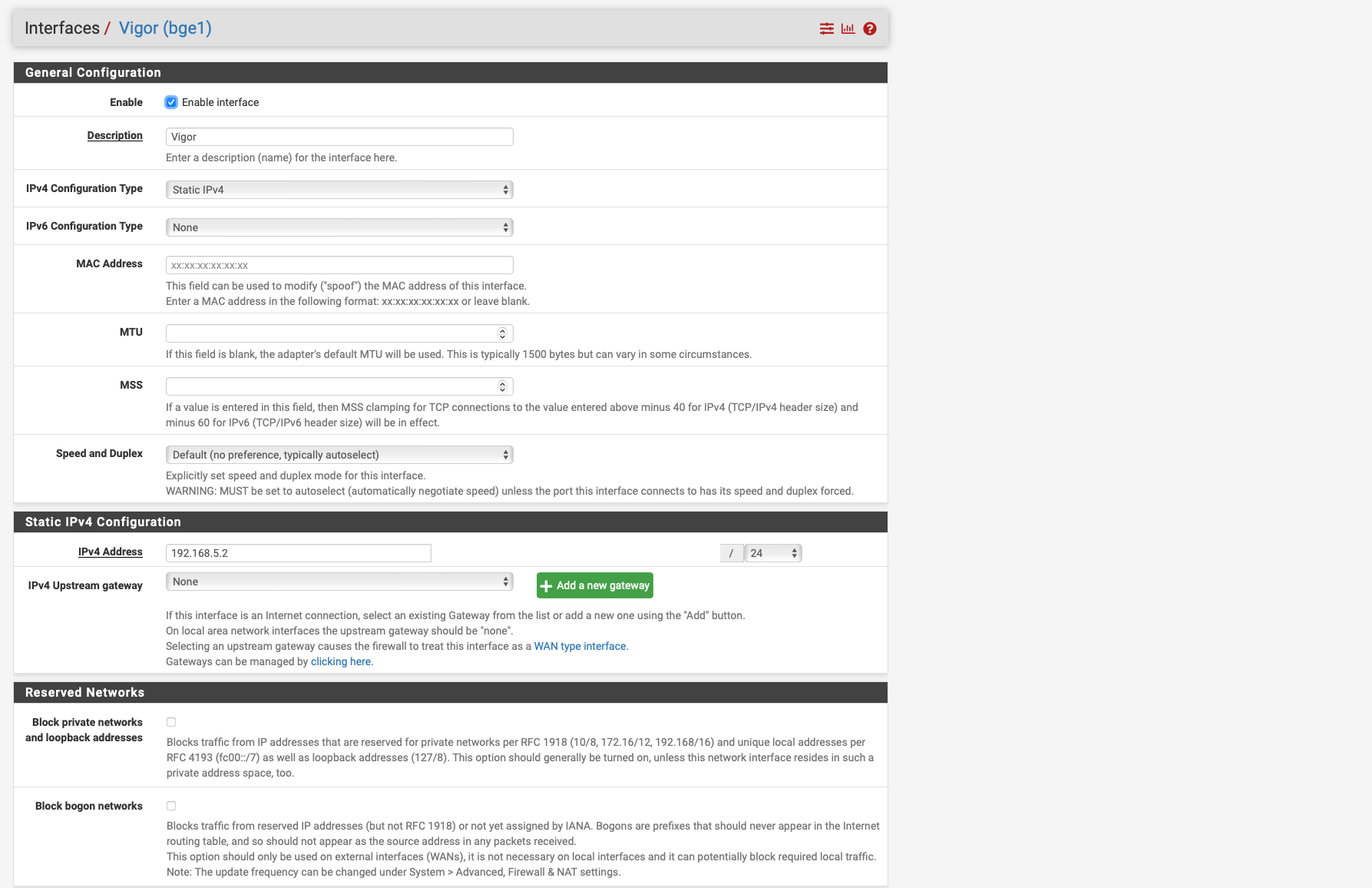
I have the VLAN Tag 7 only on the interface 1.7 nowhere else.
I have created the interface Vigor for the connection to the modem and this interface has the IP 192.168.5.2/24 see screen shot
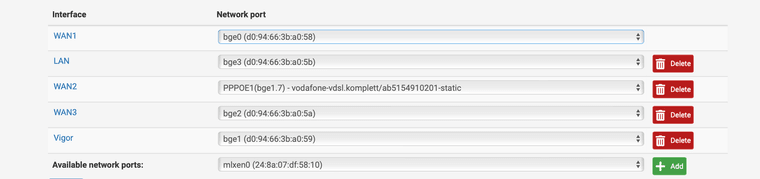
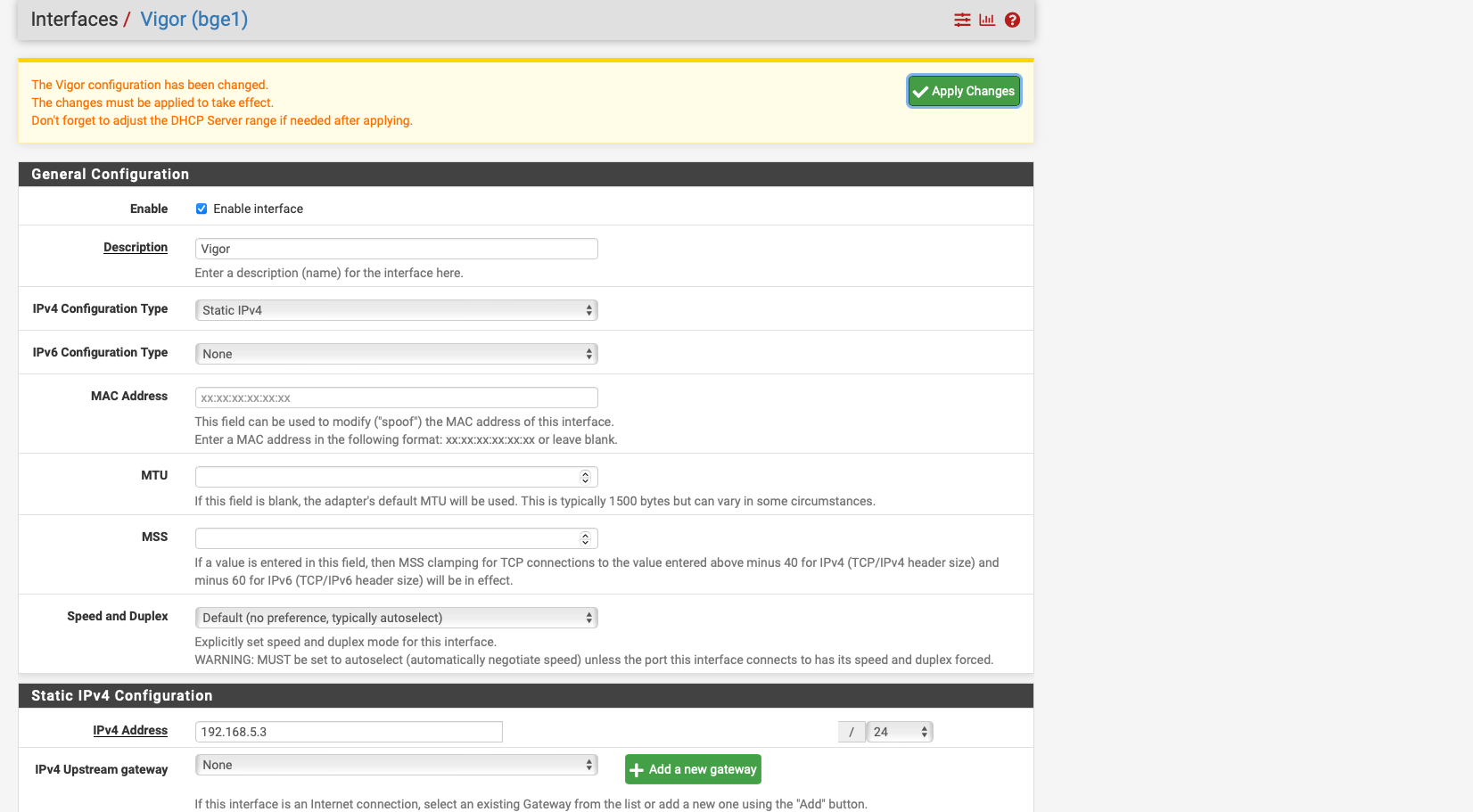
-
@Globaltrader312 so sniff on your vigor interface when you ping this 192.168.5.1 address from a client on your lan... Do you see the traffic go out, is it natted to your vigor address.. Which you have now changed from .2 to .3
Do you see a response?
So for example, here I am pinging that 192.168.100.1 address from device on my network.. You can see it is natted to the pfsense wan address I created of 192.168.100.2
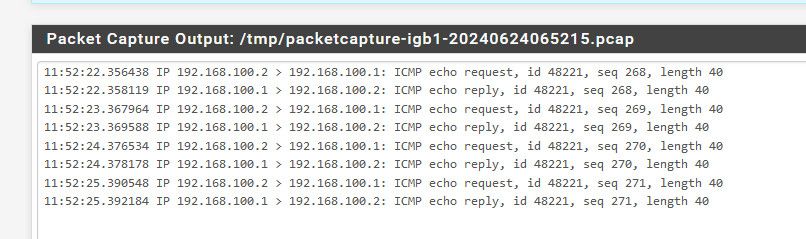
If you do not see the pings going out at least, then no it not going to work because you got something not quite right in your setup, be it your outbound nat, be it your firewall rules with your policy routing.
If you do see it going out properly natted to your vigor IP you set, but no response - then something on your vigor device is not answering.
What firewall rules do you have in floating - could you have something blocking the traffic? I for example have a rule that blocks rfc1918 from leaving my wan, just being a good netizen - no reason to send rfc1918 traffic to my isp/internet if I typo something that is not one of my local networks. or my work laptop likes to try and talk to work IP and if the vpn is not up on it - it would just route out to my isp.
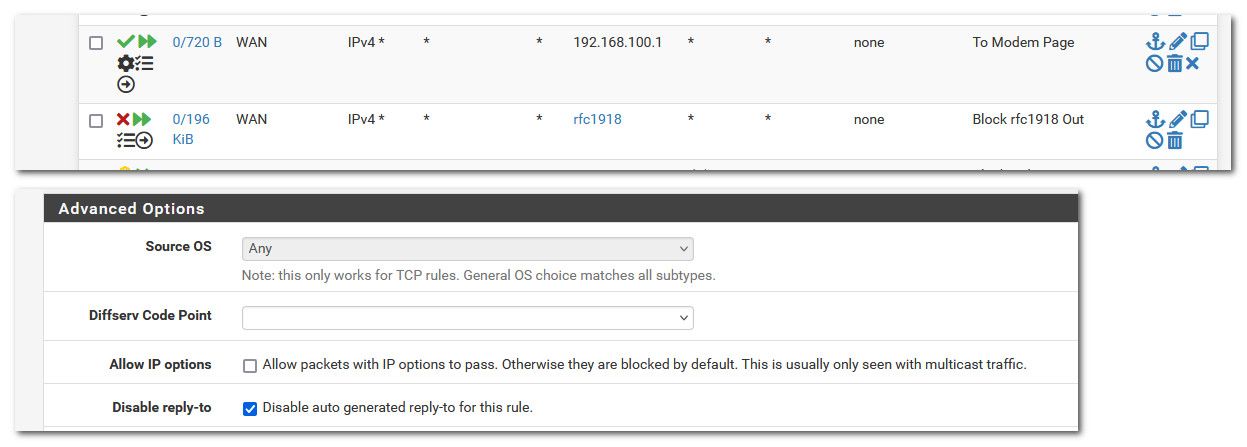
As to the reply-to being disabled.. You might also need to set this.. But maybe not since you don't have a vip setup.. But the sniff should tell us if traffic is indeed going out the proper interface and being natted to your IP so that your device can answer.