High Avail secondary node IPs - How to find it
-
Hey folks,
Im taking over a pfsense High Availability installation at a remote site.
There isn't a lot of good documentation unfortunately so I'm trying to see what the secondary pfSense IPs are. Is there a way to get that information?
You would think that the IPs are assigned in order , .1 for the VIP .2 for the primary .3 for the secondary but I'm quickly finding that it isn't the case.Maybe there's a cli way to get that info because the GUI status page isn't really reflective of who the peer is.
-
@michmoor
Log into the secondary's Web GUI and check out Status > Interfaces.If you don't know any of the secondary's interface IPs go to System > High Availability on the primary and pick the sync IP.
Ensure that the sync subnet is routed over your VPN. If it isn't add a route for it. Also ensure that there is an outbound NAT rule in place on the sync interface as described in Troubleshooting VPN Connectivity to a High Availability Secondary Node and that access to the sync IP is allowed by firewall rulesThen you should be able to connect to the secondary's sync IP.
-
Yup the primary will reference the secondary sync IP and you may be able to access it using that. That does depend on what the sync interface allows, though a lot of users will allow anything there if it's a direct connection.
-
@stephenw10 @viragomann
Thank you both you are correct!
Now the secondary isn’t responding to ssh or https. Yet there are no errors when syncing. Weird. . -
@michmoor
Did you check the outbound NAT and firewall rules on the sync interface? -
@viragomann hmm
Maybe thats the problem? I am trying to access the secondary node over VPN.
Here are the outbound rules i am using
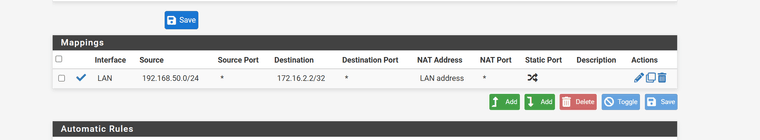
Source - My office LAN address that goes over the VPN
Destination - pfSync address of the backup node
NAT Address - That is the LAN address of the master (not the VIP lan address)Is this accurate?
-
Ok...That fixed it. It was the outbound NAT rule requirement
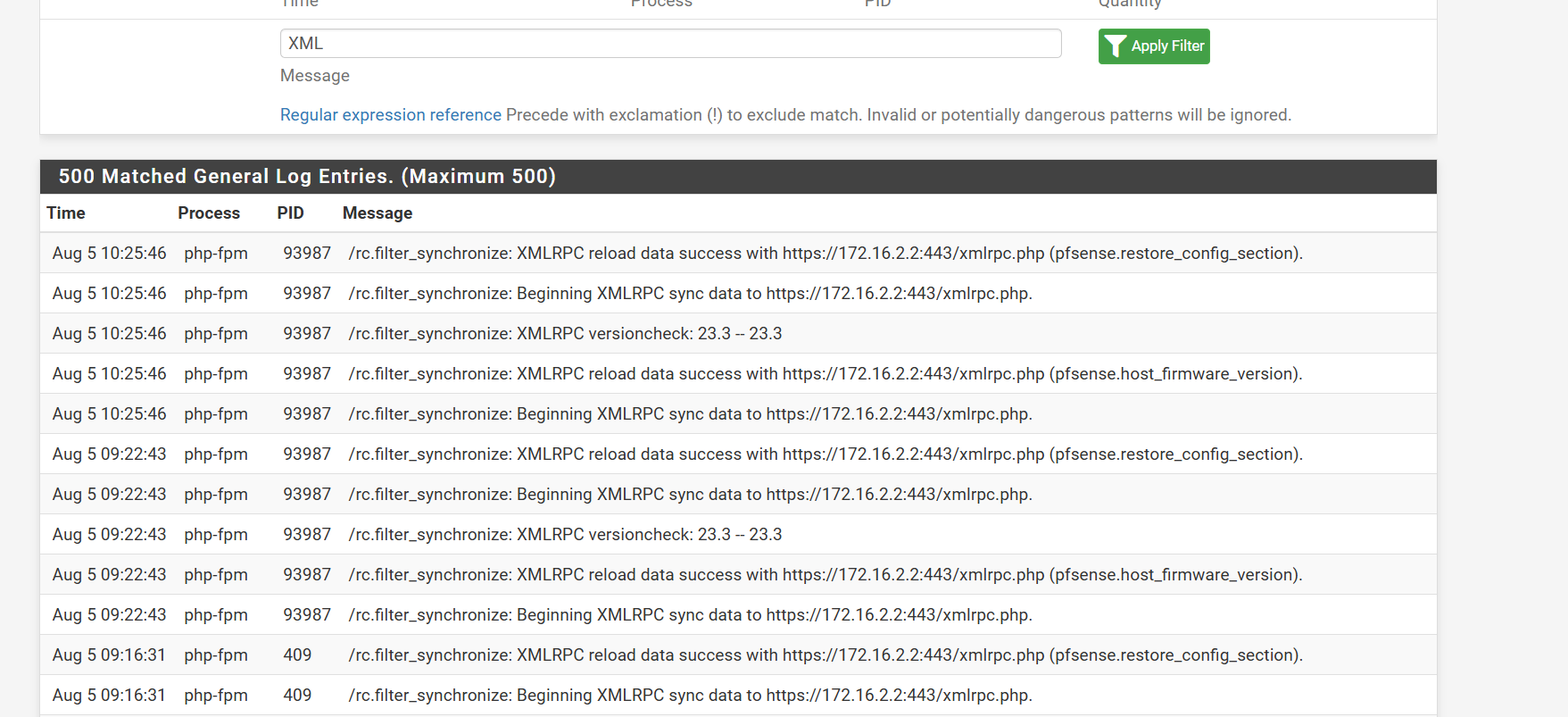
Backup node is accessible over VPN and boy..........does not look good.
I also see packages not synced over - such as SUDO, OpenVPN client export, mtr...
Firewall rules are there but things appear missing.
-
@michmoor I was going to say, disconnect the primary and log in using the shared IP. :)
Package installs do not automatically install on the secondary. Package config may sync if the package supports it.
-
@SteveITS Full disclousre. This is my second time working on a HA configuration on pfsense so the nuances I'm not familiar with namely package sync.
So on the standby node i have to manual install the same set of packages? Thats no problem i just wanted to be clear.
And get this....The secondary had the pfSync interface using WAN while the primary had the pfSync interface using the dedicated interface labeled HA
So clearly this can work but its so weird.
-
@michmoor yeah…agree with your label.
https://docs.netgate.com/pfsense/en/latest/highavailability/settings.html
There is state sync and one-way config sync. The latter I’d think could be allowed on WAN by firewall rules, but why???
Yes install packages yourself.
-
@SteveITS
One last thing. Im using IPsec here and I'm testing failover. So far it does failover to the Backup node but i noticed the firewall rules are not syncing to my VTI interface.According to the documentation i must create the interface manually which i understand but shouldn't the firewall rules come over as well?
-
@michmoor
Yes, presumed you have configured the VTI interface on the backup node as well. -
@viragomann yep. Same interface assignment
-
Im really not understanding why my VTI interfaces are not syncing up.
The interface assignments are the exact sameMaster
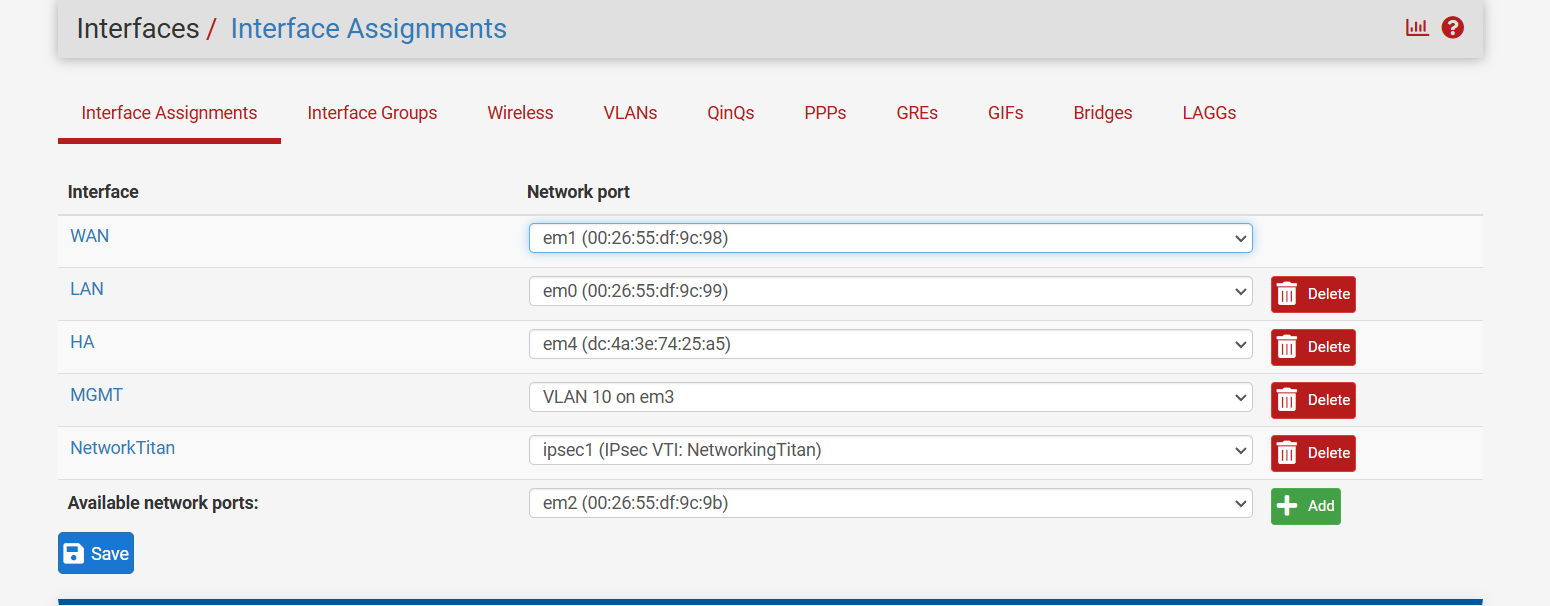
Backup
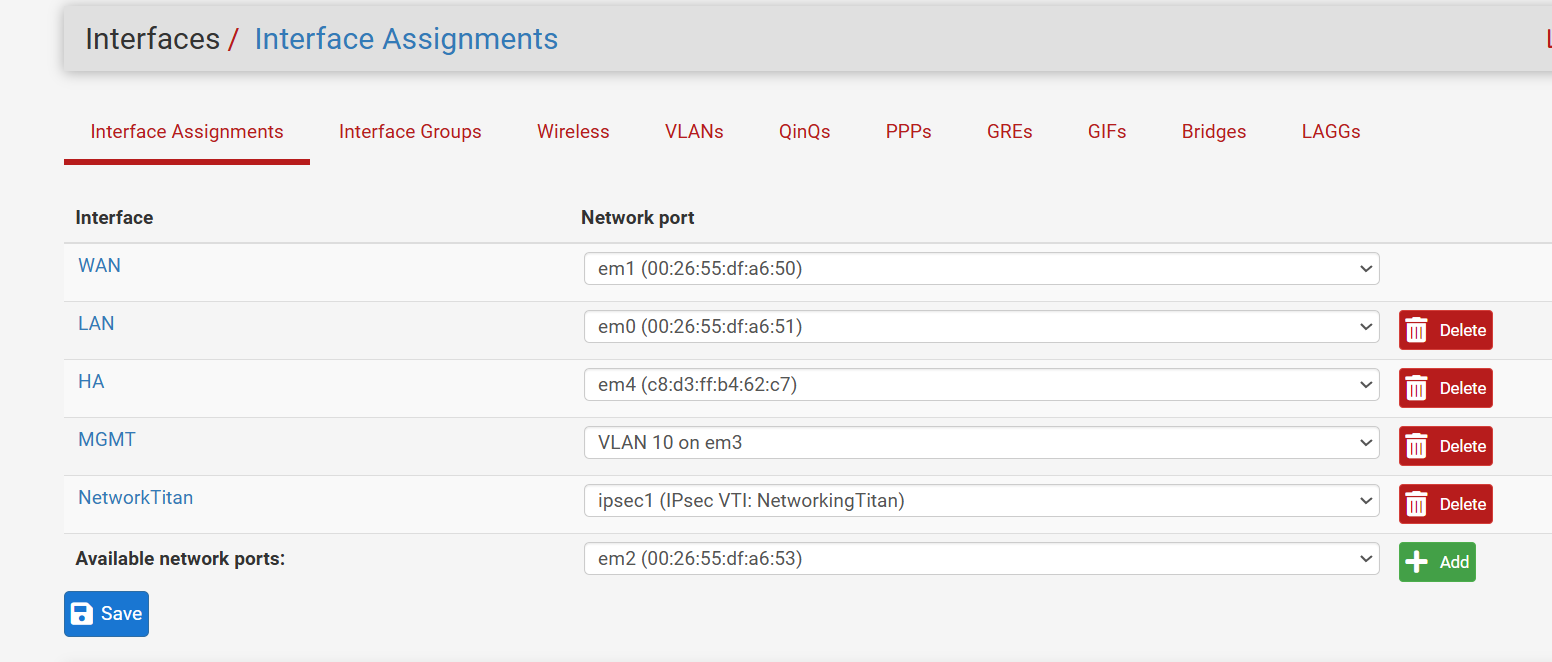
Yet the only interface with firewall rules not syncing is the VTI. Very strange behavior.
-
Is it ipsec1 on the primary too or ipsec0?
Yeah sync can work between any interfaces but it's much better to use a dedicated sync interface if you can.
-
@stephenw10 ipsec1 on both. I shared pictures above
-
Is the IPSec filter option set to VTI mode on both nodes?
-
@stephenw10 Yep it sure is.
-
Hmm, well it's possible to set individual rules to not sync. That might have been done for some reason.
-
 S stephenw10 referenced this topic on
S stephenw10 referenced this topic on
-
I thought the same as well but the "No XMLRPC Sync" checkbox is unchecked.
Logs show no errors. I even tried re-creating the interface and still no luck