DoH list
-
I created a large DoH list if anyone wants to use it as a block list for added DNS protections..
jp.tiar.app dns.nextdns.io captnemo.in example.doh.blockerdns.com doh.securedns.eu dns.dns-over-https.com firefox.dns.nextdns.io mozilla.cloudflare-dns.com doh.dns.apple.com.v.aaplimg.com doh.dns.apple.com doh.42l.fr i.233py.com i.233py.com.a.bdydns.com opencdn.jomodns.com dns.233py.com dns.233py.com.cdn.cloudflare.net edns.233py.com ndns.233py.com sdns.233py.com wdns.233py.com dns-gcp.aaflalo.me dns-nyc.aaflalo.me dns.aaflalo.me doh.abmb.win doh2.abmb.win dns.adguard.com dns-family.adguard.com dns-unfiltered.adguard.com dns.adguard-dns.com family.adguard-dns.com unfiltered.adguard-dns.com doh.nl.ahadns.net doh.in.ahadns.net doh.la.ahadns.net doh.ny.ahadns.net doh.pl.ahadns.net doh.it.ahadns.net doh.es.ahadns.net doh.no.ahadns.net doh.chi.ahadns.net dot.nl.ahadns.net dot.in.ahadns.net dot.la.ahadns.net dot.ny.ahadns.net dot.pl.ahadns.net dot.it.ahadns.net dot.es.ahadns.net dot.no.ahadns.net dot.chi.ahadns.net dnsnl.alekberg.net dnsse.alekberg.net dns.alidns.com doh.appliedprivacy.net doh.applied-privacy.net dot1.applied-privacy.net doh.armadillodns.net dohtrial.att.net doh1.blahdns.com doh1.b-cdn.net doh2.blahdns.com doh2.b-cdn.net dot-ch.blahdns.com doh-ch.blahdns.com dot-fi.blahdns.com doh-fi.blahdns.com dot-de.blahdns.com doh-de.blahdns.com dot-jp.blahdns.com doh-jp.blahdns.com dot-sg.blahdns.com doh-sg.blahdns.com doh.bortzmeyer.fr dns.brahma.world free.bravedns.com bravedns.com doh.captnemo.in ibuki.cgnat.net canadianshield.cira.ca family.canadianshield.cira.ca private.canadianshield.cira.ca protected.canadianshield.cira.ca dns.cloudflare.com cloudflare-dns.com 1dot1dot1dot1.cloudflare-dns.com one.one.one.one dns64.cloudflare-dns.com family.cloudflare-dns.com mozilla.cloudflare-dns.com security.cloudflare-dns.com cloudflare-gateway.com doh.cleanbrowsing.org security-filter-dns.cleanbrowsing.org adult-filter-dns.cleanbrowsing.org family-filter-dns.cleanbrowsing.org dns.cmrg.net commons.host dns.containerpi.com dohdot.coxlab.net doh.crypto.sx jit.ddns.net dns.decloudus.com doh.defaultroutes.de dns.developer.li dns2.developer.li dns.digitale-gesellschaft.ch dns1.digitale-gesellschaft.ch dns2.digitale-gesellschaft.ch doh.disconnect.app ns1.recursive.dnsbycomodo.com ns2.recursive.dnsbycomodo.com dnsforge.de dns.google dns64.dns.google dns.dnshome.de dns1.dnscrypt.ca dns2.dnscrypt.ca doh.dns.sb public-dns-a.dns.sb public-dns-b.dns.sb doh.dnslify.com a.ns.dnslify.com b.ns.dnslify.com a.safe.ns.dnslify.com b.safe.ns.dnslify.com a.family.ns.dnslify.com b.family.ns.dnslify.com dns.dnsoverhttps.net doh.dnswarden.com doh.li doh.ffmuc.net dot.ffmuc.net rdns.faelix.net pdns.faelix.net dns.flatuslifir.is dns.google.com google-public-dns-a.google.com google-public-dns-b.google.com query.hdns.io ordns.he.net dns.hostux.net opennic.i2pd.xyz public.dns.iij.jp jcdns.fun us1.dns.lavate.ch eu1.dns.lavate.ch resolver-eu.lelux.fi doh.libredns.org dot.libredns.gr.com dot.libredns.gr doh.libredns.gr adblock.mydns.network dns.neutopia.org dns.aa.net.uk dns.nextdns.io dns1.nextdns.io dns2.nextdns.io odvr.nic.cz lv1.nixnet.xyz ny1.nixnet.xyz lux1.nixnet.xyz dns.njal.la doh.opendns.com doh.familyshield.opendns.com doh.sandbox.opendns.com resolver1.opendns.com resolver2.opendns.com resolver1-fs.opendns.com resolver2-fs.opendns.com dns.oszx.co a.passcloud.xyz i.passcloud.xyz doh.post-factum.tk doh.powerdns.org rpz-public-resolver1.rrdns.pch.net dns.pumplex.com rpz-public-resolver1.rrdns.pch.net dns.quad9.net dns9.quad9.net dns10.quad9.net dns11.quad9.net dns12.quad9.net dns13.quad9.net dns-nosec.quad9.net dns.rubyfish.cn ea-dns.rubyfish.cn uw-dns.rubyfish.cn rumpelsepp.org dns1.ryan-palmer.com doh.seby.io doh-2.seby.io dot.seby.io dnsovertls.sinodun.com dnsovertls1.sinodun.com dnsovertls2.sinodun.com dnsovertls3.sinodun.com fi.doh.dns.snopyta.org fi.dot.dns.snopyta.org dns.switch.ch ibksturm.synology.me dns.t53.de dns.therifleman.name doh.tiar.app dot.tiar.app doh.tiarap.org jp.tiar.app jp.tiarap.org dns.twnic.tw dns.wugui.zone dns-asia.wugui.zone adfree.usableprivacy.net doh.xfinity.com doh.gslb2.xfinity.com fdns1.dismail.de fdns2.dismail.de anycast.censurfridns.dk deic-lgb.anycast.censurfridns.dk deic-ore.anycast.censurfridns.dk kracon.anycast.censurfridns.dk rgnet-iad.anycast.censurfridns.dk unicast.censurfridns.dk anycast.uncensoreddns.org deic-lgb.anycast.uncensoreddns.org deic-ore.anycast.uncensoreddns.org kracon.anycast.uncensoreddns.org rgnet-iad.anycast.uncensoreddns.org unicast.uncensoreddns.org dns.comss.one dns.east.comss.one dns-doh.dnsforfamily.com dns-dot.dnsforfamily.com asia.dnscepat.id eropa.dnscepat.id doh.360.cn dot.360.cn doh.pub dns.pub dot.pub kaitain.restena.lu getdnsapi.net dns-tls.bitwiseshift.net ns1.dnsprivacy.at ns2.dnsprivacy.at privacydns.go6lab.si dnsotls.lab.nic.cl tls-dns-u.odvr.dns-oarc.net doh.centraleu.pi-dns.com dot.centraleu.pi-dns.com doh.northeu.pi-dns.com dot.northeu.pi-dns.com doh.westus.pi-dns.com dot.westus.pi-dns.com doh.eastus.pi-dns.com dot.eastus.pi-dns.com doh.eastau.pi-dns.com dot.eastau.pi-dns.com doh.eastas.pi-dns.com dot.eastas.pi-dns.com basic.bravedns.com freedns.controld.com p0.freedns.controld.com p1.freedns.controld.com p2.freedns.controld.com p3.freedns.controld.com family.freedns.controld.com uncensored.freedns.controld.com doh.mullvad.net adblock.doh.mullvad.net chrome.cloudflare-dns.com dot.xfinity.com doh.xfinity.com dot.cox.net doh.cox.net dns.sb 8888.google chromium.dns.nextdns.io doh.quickline.ch doh-02.spectrum.com doh-01.spectrum.com mask.icloud.com mask-h2.icloud.com dandelionsprout.asuscomm.com basic.rethinkdns.com max.rethinkdns.com anycast.dns.nextdns.io 0.0.0.0 0.0.0.64 token.safebrowsing.apple mask.apple-dns.net ussjc1.mask.apple-dns.net global-wrr.mask.apple-dns.netLet me know if you have any others Apple products are focusing on DoH over QUIC or HTTPS3 right now even if you force set the DNS to your firewall they are not following proper protocols in that sense. The admin should be able to force set the DNS to use the firewall and that is not occurring at all on my end. They ignore it and use DoH over QUIC.
when you have systems that need to use the correct DNS DoH can cause major issues as it acts as an injector and items in the security system will only start to show IPs and no longer be blocked. Once DoH is blocked it normalizes again and the firewall is used as the DNS.
I mean what is the point of hard setting the DNS if the client bypasses it anyway as if they don't care...
-
I'm assuming you are DNSBL ing these names,
I run it for a while and see if it picks up anything different than the list I already use..
Current List

Your list

This might be fun. Because it should (in theory) for those actors using the name vs a direct IP, cause a shift in the hit counts from current list to the name list ..
-
@jrey Wow you got a big list
-
@jrey any change? Can you please send me the list you use if you can access the text file..
-
Firewall > pfBlockerNG > DNSBL > DNSBL SafeSearch ?
-
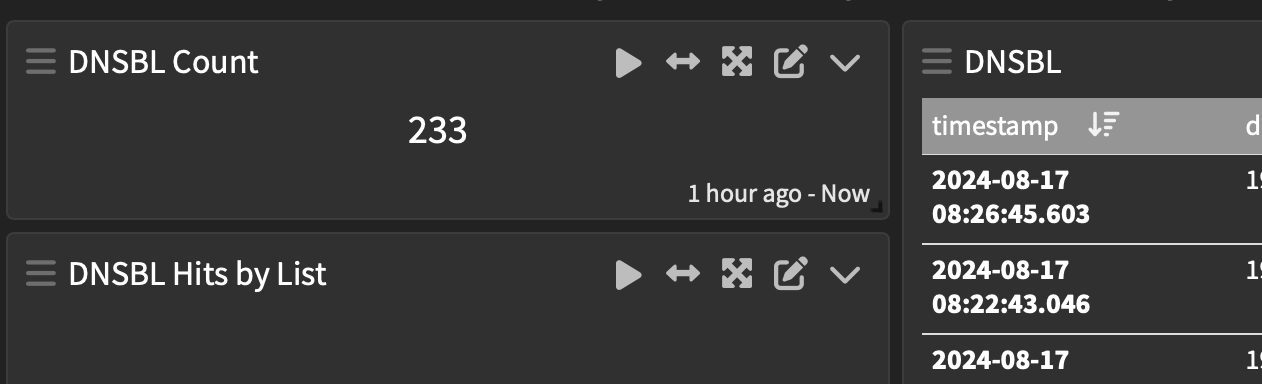
Not prepared to give away all the tricks but my graylog - realtime DNSBL logging is showing a few records from your list - I won't have a clear set of numbers until there is more activity Monday to Friday..
your list is the "orange" section on the pie
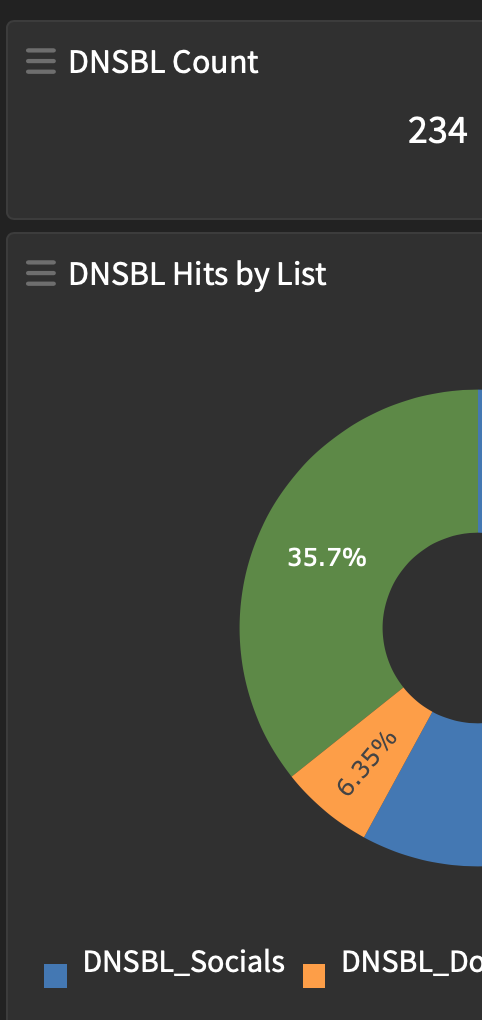
-
@JonathanLee My approach to blocking DoH has been to use IP blocking rather than DNSBL. I'd be interested in knowing the pros & cons of each. It hadn't occurred to me to do it via DNSBL.
-
I'd be interested in knowing the pros & cons of each
Too soon to say, but in theory, the names they encode are pretty static, the IP's they point those name to can change in a heart beat... so ....
The best approach for those interested in blocking this, might actually be a combo of both.
Traffic is lower here on a Saturday, so far I haven't noticed a significant shift of blocking from my IP list to @JonathanLee name list. Graylog will tell me if/when it does.
It's also possible the shift may be small if the names are already in another list.. Again once I have a larger volume of data in Graylog I'll be able to match the list by names blocked and seefrom Graylog the DNSBL_DoHName is Jonathan's list
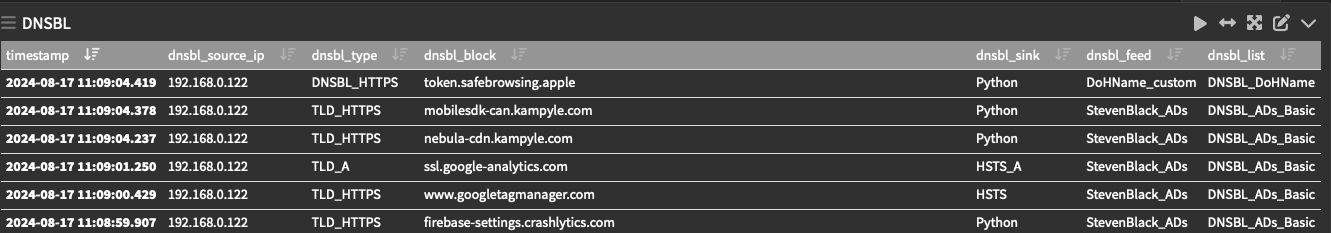
Each to their own.
-
@Gertjan do you possibly have the URL or text file that is used, this list is massive compared to mine, again a lot of mine was manually done and a lot added on from other lists.
-
@jrey so you are getting hits from mine. That token one came from a blacklist doh category. I thought it would have been some mask.apple-dns.net one they are really pushing this one right now manual set dns or not. I have a regex for it they seem to make a new one every couple months
-
Researched and found this..
No longer working:
https://heuristicsecurity.com/dohservers.txt
https://raw.githubusercontent.com/bambenek/block-doh/master/doh-hosts.txt
https://raw.githubusercontent.com/oneoffdallas/dohservers/master/list.txtStill active:
You can also block all public DNS IPs with this feed:
https://public-dns.info/nameservers.txthttps://github.com/dibdot/DoH-IP-blocklists/blob/master/doh-domains.txt
-
The best approach for those interested in blocking this, might actually be a combo of both.
I guess it depends how applications, that make use of DoH, determine DoH server IP. I'd completely overlooked the fact that some|most might arrive at this via a regular DNS query. If that is the case for all apps using DoH, then it would seem DNSBL is an appropriate way to block.
AIUI some of the DoH IPs serve stuff other than DoH. The pihole discourse cdn is one case, I believe!
But I suppose there are applications discovering a DoH server IP in ways other than a regular DNS lookup. -
I wonder if the mask.apple.... is blocked without logging because it is already on this list
pfBlockerNG -> DNSBL -> DNSBL SafeSearch
-
Unbound Resolver can also be configured to use DoH, it works with advanced config. Again would other DoH requests still get around it? Again I wonder about a snort ips/ids signature to see any DoH request. I don’t think it is possible
-
Sure enough
I unselected it from the list above, reload the DNSBL then dig it
shows up logged from your list ..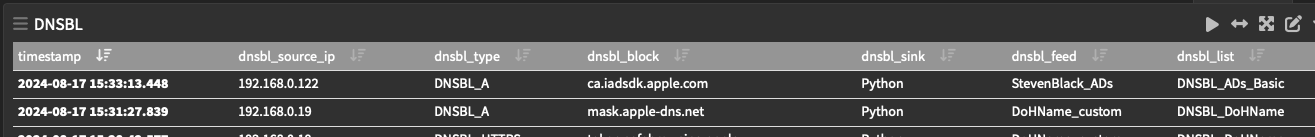
difference is when on the DNSBL Safesearch above and you dig (not logged in DNSBL, is logged in dnsreply )
because you get NXDOMAiN;; global options: +cmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NXDOMAIN, id: 58941 ;; flags: qr rd ra; QUERY: 1, ANSWER: 0, AUTHORITY: 0, ADDITIONAL: 1 ;; OPT PSEUDOSECTION: ; EDNS: version: 0, flags:; udp: 1432 ;; QUESTION SECTION: ;mask.apple-dns.net. IN AWhen it is not on the list above it falls to your list, is logged and returns
;; ANSWER SECTION: mask.apple-dns.net. 60 IN A 10.10.10.1That being the case the place to put this might be better in the SafeSearch above and not a special DNSBL blocking -- Clearly the NXDOMAIN interception point before user defined DNSBL lists, would cause the (application/website) whatever to not try and get a response from 10.10.10.1 ?
Since the only one from your list that has been logged here is token.safebr.. I might like to confirm next that it is actually DoH traffic going to/from there? Have you?
guess I'll have to look at pulling realtime dnsreply logs in to graylog so I can make another pretty graph lol -
-
@jrey what GROK patterns are you using for dnsbl?
-
umm, you can write your own you know..
funny, and there I though the first question someone would ask would be more like wait minute -- DNSBL records to syslog in realtime..
-
@darcey some I have found if you block the DoH FQDN start to use an IP address as if it had been coded as a if else statement, so you have to at times block the IP and the FQDN. I don’t understand if an administrator sets the DNS to a firewall and all the sudden a device starts to attempt DoH and bypass admin settings. It’s like wack a mole.
-
@jrey the url comes from a blacklist in France, they have had it listed as DoH for years. I have never seen it not blocked on my system. I have never had issues with it being blocked. It would be so simple if there was a standard ips/ids signature for DoH that it could just AppID block, all DoH signatures must act in the same way per protocol design right? I mean it’s not just Apple creating new ones every couple days it’s a list that grows and grows, if we had a simple DoH Snort detection signature all of this could be solved with much less cycles.
https://docs.snort.org/start/rules
There is something we can use to detect DoH use, that way it could be blocked with inline or legacy blocking mode
-
@JonathanLee said in DoH list:
There is something we can use to detect DoH use
DoH is a TLS data stream going a some destination IP using port 443.
Just by looking at the random bit stream, the size of entire stream open - data exchange and stream end, you might be able to say : hey, that's not a classic web page, but something way smaller like a DNS request. But how to be sure ?
DoH server are special, and by nature their IP addresses are semi static or 'always the same', so they can't hide for long time, they will get known. If you're not sure, throw a DoH DNS request on it, and you'll be sure its a DNS server, as a web server will say 'sorry, error'.
To block DoH the explicit way, there is only one solution : go MITM.