Under attack, anything I should do?
-
@elvisimprsntr said in Under attack, anything I should do?:
Does your public IP respond to ICMP pings? If so, figure out how to disable in your ISP kit and/or pfSense
While many people suppress ICMP echo for IPv4, attempting to imitate a black hole, suppressing echo responses really has no impact on security. Also of note is that suppression of echo response is specifically prohibited with IPv6.
If you monitor your WAN link for potential evildoers, you will find lots of various TCP or UDP attempts, but little or no ICMP echo. The reason for this is that it's simply not worth the time for the attacker, because the presence or absence of an echo response provides them with no useful information. In short, an attacker is going to try your ssh et al. ports regardless of whether you respond to ping or not.
-
@dennypage exactly I allow ping for my use, the monitoring tools that let me know if my internet connection is down, etc.
There is little reason not to allow for ping..
edit: also good for sanity checks... Out and about and trying to vpn in and not working, does ping work, if so then prob just a firewall block or vpn service issue vs connectivity issue.
Only sort of extra steps I take is I lock down the services I have open to my country IPs, and I also block known scanners from talking to any of my ports, no reason to be listed in some db that bad guys can access that lists my IPs and ports that answer, etc.
-
If you are not providing any services, then yes you are correct.
But if you are providing services and never open any ports, how would anyone reach the services you are providing?That was the context for my statement.
If google never opened any ports, no one could access gmail, google DNS, etc.
A HUGE difference between opening ports specifically for services and your statement.
OP obiviously opened 443 for an OpenVPN server INBOUND from the internet so he could access home stuff from a hotel.
-
@johnpoz said in Under attack, anything I should do?:
Only sort of extra steps I take is I lock down the services I have open to my country IPs
of note, i don't think this is working right now via pfblocker so finding all U.S. ranges (for example) is quite a task.
-
Thank you for all the response. Let me respond to various without quoting.
First, I have been a pfSense user for more than a decade. All has been working well so I never signed up for the new forum. This explains the low post number.
Having used pfSense for a long time, and having monitored my firewall logs, I can tell that the current activity is unusual. I am well accustomed to many opportunistic hits from various IPs htting various ports. But certain block of IPs trying to access a single common port is new. Hence my inquiry.
I am not running a web server on this port. I use it for openvpn access into my home network. So a server in the cloud does not help here.
Port 443 is a backup port because some hotels block port 1194. Many hotels do allow this port but I need a backup for those who do not. I am running wireguard only experimentally, so do not know about blocking of those ports which are in the 5 digit range.
I have not stated that I am suffering a DDOS attack. I agree that 5/s is low, and my connections are in no way affected. But the behavior is different from what I have observed in the past so its more than normal "noise". Thus, I wanted to check whether any action is required. Theoretically nobody should be able to get in, but I am not sure what the attacker is trying to accomplish. I did some packet captures but cannot interpret the content. I am an advanced home user but not a network export.
The worst case scenario seems to be someone getting in and encrypting my server for ransom. However, no body seems to be overly concerned so that I will simply let it be. The hits themselves do not bother my.
Thank you again for the discussion.
-
@michmoor said in Under attack, anything I should do?:
i don't think this is working right now via pfblocker so finding all U.S. ranges
Its working here.. yeah pfblocker.. why would you think that isn't working?
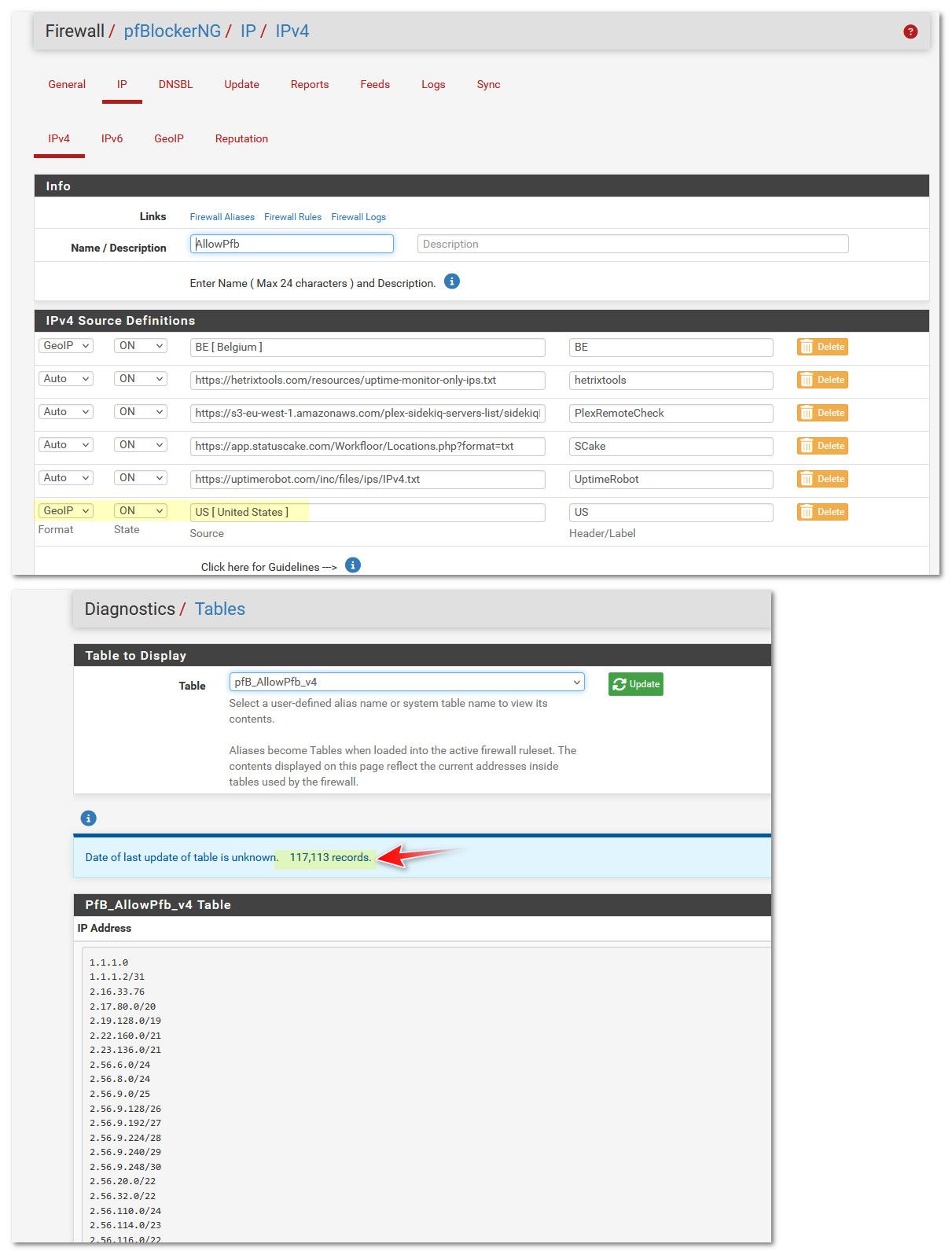
I also have a few other lists in there, some of which are non US Ips.. Beligum for example - have a family member living there currently, so they can access my plex server.
-
@revengineer some syn to 443 isn't going to get far.. since openvpn right away will see its not openvpn traffic, and you should be using tls keys, etc. so yeah openvpn would drop those pretty much instantly and not even attempt to start a openvpn connection - even if they wanted too..
-
@johnpoz pulling IP blocks from countries. Isnt there an intermittent issue with bgpview.io?
I think BBCan said he was looking into it and looking at other sites to pull that info from. -
@michmoor said in Under attack, anything I should do?:
pulling IP blocks from countries. Isnt there an intermittent issue with bgpview.io?
I think that was an issue with ASNs. I believe that the country info comes from Maxmind. [Edit: Specifically, the GeoLite2 City database,]
-
FWIW, I run my OpenVPN on a rando high port and NAT it. But is many moons since I traveled anywhere that offered WiFi over anything more sophisticated than a Netgear router. LOL
-
@dennypage said in Under attack, anything I should do?:
I think that was an issue with ASNs
Well I haven't validated that all the asn info is actually being pulled and correct, I do have some ASN aliases - and they sure seem to be pulling info..
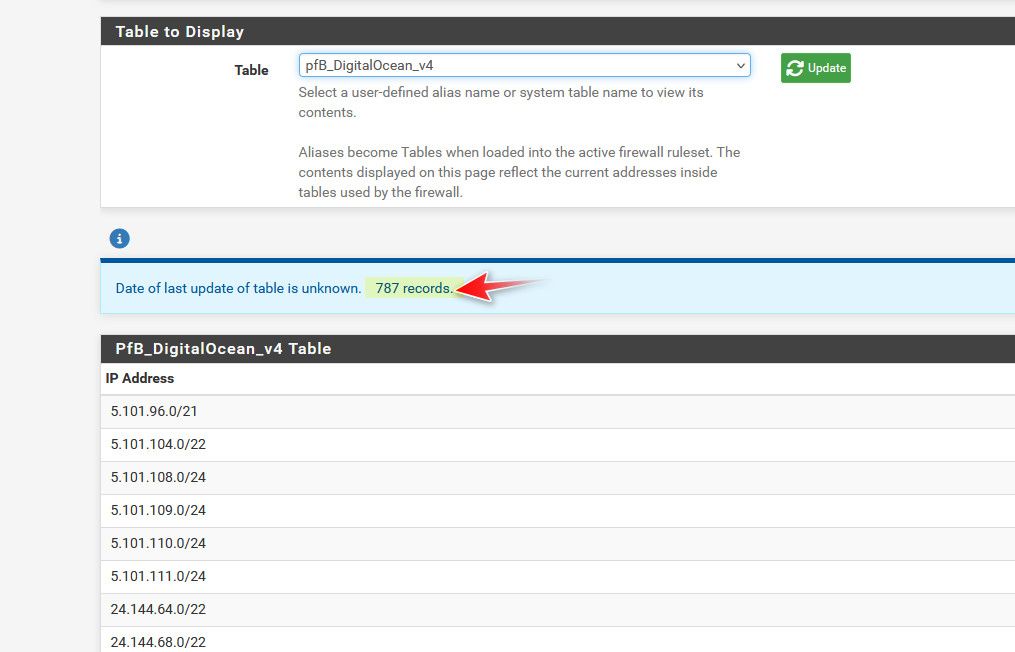
There is never anything good that will ever come unsolicited from DO, which is why I block all of their asns..
-
@johnpoz said in Under attack, anything I should do?:
Well I haven't validated that all the asn info is actually being pulled and correct, I do have some ASN aliases - and they sure seem to be pulling info..
Information available here.
-
@johnpoz last question as i dont want to hijack this thread.
How do you know what IP block falls under what country?
So for example, i want to accept all routes from a country like Saint Thomas (Virgin Islands). I would go into pfBlocker and using ASN - search for Saint Thomas - which comes back as AS32907. As of today, this doesn't work because of the issue with bgpview.
But if i do GeoIP, STTHOMAS, doesn't even come up. It does fall under US but how would i know that? -
@revengineer said in Under attack, anything I should do?:
Having used pfSense for a long time, and having monitored my firewall logs, I can tell that the current activity is unusual. I am well accustomed to many opportunistic hits from various IPs htting various ports. But certain block of IPs trying to access a single common port is new. Hence my inquiry.
Actually, I'm also seeing a recent change in behavior. The number of failed login attempts on my sshd port used to be quite low --- there were 32 attempts during August, for instance. So far this month (a bit less than 5 full days):
$ sudo grep 'Invalid user' /var/log/secure | wc 40152 481848 3454355Somebody's amped up the level quite a lot. Digging a little deeper, the connections are coming from a whole lot of places, though I did identify a couple of Korean and Chinese netblocks that seemed disproportionately represented (and are now blocked). The usernames are just random, looking more like a dictionary attack than anything targeted.
Not sure what to make of this. I don't believe I'm being specifically targeted, and they're wasting their time anyway because my server will only accept certificate-based logins. But somebody's gotten really enthusiastic about brute-force ssh breakins.
-
Mmm, you should definitely consider limiting the source on the rule allowing that IMO.
-
@michmoor said in Under attack, anything I should do?:
STTHOMAS, doesn't even come up. It does fall under US but how would i know that?
How would you know that st thomas is a US territory? Isn't that something they teach in elementary school still. Basic geography? Why would anyone think to use an ASN for a country or region.. ASNs are assigned to companies or entities - not countries normally.
Its also in the name, I mean when someone says Saint Thomas, there is always that , U.S. Virgin Islands isn't there? Just like I would assume everyone knows that ST. Barts and ST. Martin and lets not forget Martinique are all french, etc.
I mean I think the US has something over 25K different ASNs - I think they are like 10x the next highest..
I mean I guess some small country might just have 1 ASN, where the gov controls the internet in that country? But they should also be listed in the geo IP db..
-
@michmoor said in Under attack, anything I should do?:
So for example, i want to accept all routes from a country like Saint Thomas (Virgin Islands).
Saint Thomas isn't classified as a country. It's part of the United States Virgin Islands. There is a standard country code for that, which is "VI".
-
@stephenw10 said in Under attack, anything I should do?:
Mmm, you should definitely consider limiting the source on the rule allowing that IMO.
yep
@Patch said in Under attack, anything I should do?:
use an IP alias in pfsense for this which includes the address of my laptop while I'm on the road (via a dynamic domain name client on my laptop).
-
@johnpoz STT was an example. Calm down....
-
@dennypage said in Under attack, anything I should do?:
Does your public IP respond to ICMP pings? If so, figure out how to disable in your ISP kit and/or pfSense
@dennypage said in Under attack, anything I should do?:
While many people suppress ICMP echo for IPv4, attempting to imitate a black hole, suppressing echo responses really has no impact on security. Also of note is that suppression of echo response is specifically prohibited with IPv6.
Thank you! This. The whole stick about being invisible or somehow stealth by not answering ICMP is so completely bullshit I don' even know how that got so famous in the first place! TTL and other measures can easily show if there's another hop on the line that is playing dead. Hell even ISPs on dialup lines often have the first hop not responding to anything and you know it's there. Allowing ICMP echo reply is no bad thing or makes you a target. Playing sneaky and stealthy makes you one. Comparable to the nonsense of hiding a WiFi SSID that also adds a whole lot of other problems for other WiFis.
@Bob-Dig said in Under attack, anything I should do?:
Already forgotten that it is OpenVPN behind Port 443?

Seems so
 With that little traffic it should be no problem to re-open the port. I'd throw in to use pfBlockerNG, add the PRI1-3 or even PRI1-5 lists and the "SCANNER" list and silent block drop them on WAN in front of the allow rule for the VPN. That should eliminate quite a bit of that noise one sees on ports like 443/tcp. That will shut up nonsense hosts, scanners like censys or Shodan and stuff so it won't ring the bell that often.
With that little traffic it should be no problem to re-open the port. I'd throw in to use pfBlockerNG, add the PRI1-3 or even PRI1-5 lists and the "SCANNER" list and silent block drop them on WAN in front of the allow rule for the VPN. That should eliminate quite a bit of that noise one sees on ports like 443/tcp. That will shut up nonsense hosts, scanners like censys or Shodan and stuff so it won't ring the bell that often.@revengineer said in Under attack, anything I should do?:
Having used pfSense for a long time, and having monitored my firewall logs, I can tell that the current activity is unusual. I am well accustomed to many opportunistic hits from various IPs htting various ports. But certain block of IPs trying to access a single common port is new. Hence my inquiry.
You should take into consideration that with the whole shebang of AI bullshit out there, the amount of bots and crawlers has gone awry. Working for a company that besides firewalls and network stuff does hosting for a big chunk of our business, we see things like facebooks crawlers, claudebot from openAI and stuff spiking at an all time high and running wild on webservers of our customers. That got large enough we block whole IP ranges now to stop them from crawling as quite a number of them are ignoring stuff like robots.txt to reign in their crawling behavior.
So if you're running on a dynamic IP it's not impossible that this IP was somehow known for a web service beforehand or that some crawlers and bots simply don't care and try to exploit it. Also there were a number of HTTPS/webservice exploits again, so scanner/exploit kits searching for targets in a kind of "wave-like" surge in traffic isn't that unusual. It happens. That's why I'd add pfB IP blocks in front of the VPN rule and be done with it. OpenVPN itself is quite capable of ignoring those BS connection attempts :)
@revengineer said in Under attack, anything I should do?:
I have not stated that I am suffering a DDOS attack. I agree that 5/s is low, and my connections are in no way affected.
Yeah absolutely. Didn't read it as DDOS, but your wrote "under attack" while most of is wouldn't count 5/s on any service as even an attack ourselves but of course YMMV.
@revengineer said in Under attack, anything I should do?:
but I am not sure what the attacker is trying to accomplish.
It doesn't have to be attackers at all! As stated before, there are numerous scanner services like censys, Shodan etc. that will also spike in traffic when new CVEs or exploits are released and they kick off their search for vulnerable systems.
@provels said in Under attack, anything I should do?:
FWIW, I run my OpenVPN on a rando high port and NAT it. But is many moons since I traveled anywhere that offered WiFi over anything more sophisticated than a Netgear router. LOL
Wanted to add to that comment a general recommendation: just run OpenVPN on localhost and udp/tcp 1194 for basic setup. Then add port forwards with an alias and a small set of ports and redirect them to localhost/1194 for either udp/tcp. Done.
You now have the same fallback strategy implemented like the "bigwig" VPNs that spam your ad channels everywhere, like PIA, Nord, etc. They all run on a number of IPs but with various different ports for fallback reasons for when the default 1194/udp/tcp won't work.Normally those are like:
- UDP: 1194, 80, 4569, 5060, 51820
- TCP: 1194, 443, 8443, 7770
Those are quite common for Nord or Proton and other VPN providers to use as alt ports and even in some restrictive hotel environments and with shitty portals I normally get through to home with them.
Otherwise when not wanting to open any port at all, using a VPN with an intermediate (run by yourself or from the VPN provider) like tailscale (or self hosted headscale) or sth. would be another possibility.Cheers :)