Wireguard with IPv6
-
Alright, i made progress but its still not working as i want it to be.
I am sure there is something i misunderstand or i am not doing properly.Here is what i did so far:
I created a wireguard tunnel on my netgate router and gave it an interface IPv4 address and choose a port.
Lets say 192.168.4.4/24 on port 52490After that i added a client as a peer which i want to access the netgate router from remotely.
I added the public key from my remote windows client and set allowed IPs for said peer on my netgate to 192.168.4.0/24I also created a firewall rule on wan that lets me connect to the IPv6 address of one of my other interfaces
that - as we discussed earlier - gets a globally unique IPv6 assigned via track interface -> WAN.
In addition to that i created a "allow all" rule on the wireguard interface, so that wireguard clients are not restricted at all.
(just for testing purposes)On the client i created a wireguard config with the aforementioned IPv6 address as the endpoint on port 52490.
For simplicity, i route all traffic through the wireguard tunnel by setting allowed IPs on the client side to 0.0.0.0/0.Here is the thing:
When i connect from my windows machine to the netgate router over wireguard, i can see that the connection is established and working.
I can ping the tun_wgX interface on my netgate (192.168.4.4) from my client and get a correct response.
I can also ping other interfaces on the netgate router.
But i cannot connect to the pfsense webinterface that should be available on 192.168.4.4:443 (https)
The connection attempt doesn't get any log responses and its just times out after a while. -
@FreeYourMind said in Wireguard with IPv6:
But i cannot connect to the pfsense webinterface that should be available on 192.168.4.4:443 (https)
I could be wrong (Yeah, I know it's hard to believe.
 ), but I suspect the computer used to access the interface has to be on the LAN, though it may be possible to configure it for elsewhere.
), but I suspect the computer used to access the interface has to be on the LAN, though it may be possible to configure it for elsewhere. -
From my experience the web interface bins itself to any interface available and you just regulate access via firewall rules.
I have a similar setup working, where the UI is in fact accessible over the ip address that is assigned to the tun_0 of wireguard.I also cannot access any other services. (DNS on 192.168.4.4) doesn't work either but i can ping it properly without any issues.
I also opened up the firewall rules to make sure that this isn't the issue. -
Hmm, interesting I would expect that to work.
There can sometimes be some odd routing behaviour on the VPN interface itself, though it's been a while since I've seen it.
Can you access the webgui on any other address? If you're passing all traffic over the VPN it should respond on any address.
-
Thats the thing, i can try any IPv4 on any other interface and there is no response whatsoever.
There is also no entry in the system logs that would indicate the firewall rejects the request.I tried it on a netgate 4100 and a netgate 1100. The only thing is, that both Netgates already have one wireguard connection active that is running for quite some time now. I don't know if that might be the issue.
-
@FreeYourMind said in Wireguard with IPv6:
I created a wireguard tunnel on my netgate router and gave it an interface IPv4 address and choose a port.
Lets say 192.168.4.4/24 on port 52490What? Why would you do that.
-
@Bob-Dig
I guess i described that not correctly.
What i did is, i created a new tunnel with 192.168.4.4 as the interface address for tun1 and 192.168.4.0/24 as the network for tunnel clients.
As i learned earlier from stephen and JKnott, this address is not really the address wireguard listens on but instead wireguard listens on all addresses assigned to any interface, be it IPv6 or IPv4 (by default) and its up to the user to give grant access via firewall-rules. -
@FreeYourMind said in Wireguard with IPv6:
As i learned earlier from stephen and JKnott, this address is not really the address wireguard listens on but instead wireguard listens on all addresses assigned to any interface, be it IPv6 or IPv4 (by default) and its up to the user to give grant access via firewall-rules.
It can not listen to that because this is the address space of your tunnel. To create that tunnel, WireGuard needs to listen on your WAN-IP for example on port 5120 or whatever. WireGuard is listening on all interfaces, every WAN and every LAN interface you got. But there is no point of listening on the tunnel-interface itself...
-
@Bob-Dig
Yes, i understand. I did not describe that earlier correctly. My bad.
-
Do you guys have any other ideas?
I honestly don't know how to troubleshoot my issue.Like i described earlier, the wireguard connection to one of the available (globally unique) IPv6 addresses on my Netgate router works fine and i can also ping the tun interface of wireguard once the connectiuon is established. I can also ping other (physical) interfaces on the netgate from the remote peer but i cannot connect to any service, doesn't matter if its DNS or accessing the web interface.
The firewall rules are all set up properly, i double checked but it just doesn't work. -
On my WireGuardVPN server - for road warriors remote access. To access the WEB GUI I have a firewall rule in the WireGuardVPN server rules page directing/routing access to the WEBGUI the source I have is an Alias of all the Wireguard Client Static IP's, however to be less restrictive use wireguard/vPN Server address or Subnets and the destination should be the This Firewall (self) and the port you are using for the WEB GUI.
I also believe you will have to do the same to gain remote access to other computers, NAS etc.
Hope I am providing help, never sure.
-
@FreeYourMind said in Wireguard with IPv6:
The firewall rules are all set up properly, i double checked but it just doesn't work.
Maybe you should show them here.
-
Yup probably going to need some screenshots to review at this point.
-
Sure. :)
Rule to allow access from anywhere to one IPv6 address on the UDP port WG is listening on:
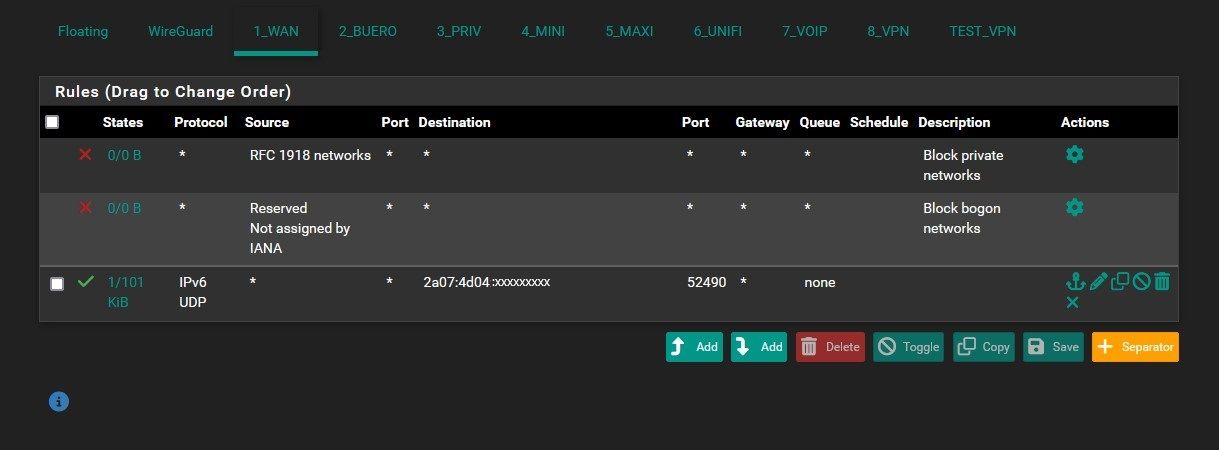
Allow everything on the tunnel interface, so connected clients are not restricted at all. (for testing purposes only)
Let me know if you need some additional information.
Thank you. -
@FreeYourMind said in Wireguard with IPv6:
Let me know if you need some additional information.
Usually one would use the WAN-address-Alias or, if you don't have one, the LAN-address-Alias for example (your first screenshot) and not a real address.
According to your problem description, the problem must be in the interface called WireGuard, show that. Or you need to set MTU and MSS to 1420 on your assigned interface.
-
Yup the WireGuard interface group will apply first before any assigned interface so if you have any rules there they will take precedence.
-
@Bob-Dig
Yes, i have just set it up for testing purposes. Once the problem is solved i will absolutely use an alias for the actual IPv6.
As far as i know (and correct me if i am wrong) the rules under the interface wireguard only apply for
"unassigned wireguard tunnel interfaces"
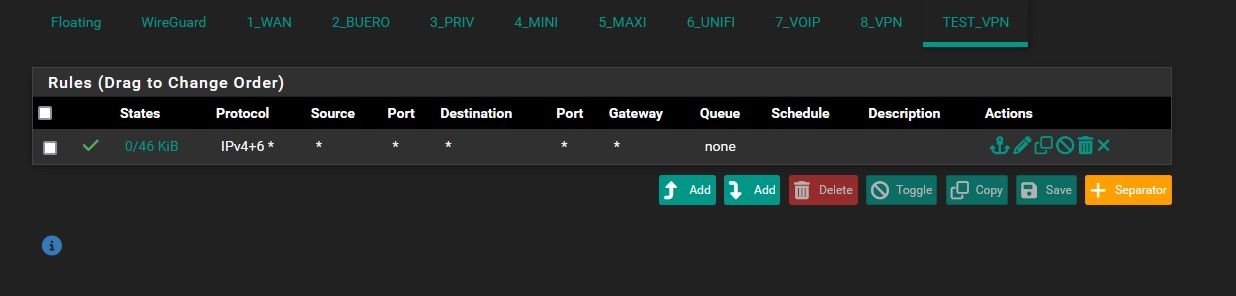
In my case i did assign an interface and named it TEST_VPN, hence why i showed your the firewall rules for TEST_VPN.
There are no rules for the wireguard interface at the moment.I tried to change the MTU / MSS to 1420 like you said (under Interfaces -> TEST_VPN) but unfortunately it still did not work after that.
-
Thats actually good to know, i wasn't aware of that. In my case there are no rules under the wireguard interface at the moment.
-
Sorry for bringing this up again but i wasn't able to find a solution so far.
There is one thing though that seems interesting which i didn't mention earlier.I am still not able to connect to the pfsense webui from a wireguard peer.
Other than that there is a NAS in the network the wg peer has access to. Like i described earlier, i can ping the NAS just fine but i am not able to access the web interface of it. Interestingly enough, i can SSH into the NAS from said wireguard peer but i cannot find out why i am not able to connect to its web interface. There is still nothing that pops out in the firrewall logs and i am a bit out of ideas tbh.Ok quick edit from me:
I was finally able to find the solution. You were already suggesting to lower the MTU to 1420 bytes. I tried that but it didn't work initially.
Now i tried it again but this time i lowered it to 1380 bytes and that did the trick for me. So the MTU suggestion was right after all.
Thank you very much for your help. :) -
Ah, nice catch!