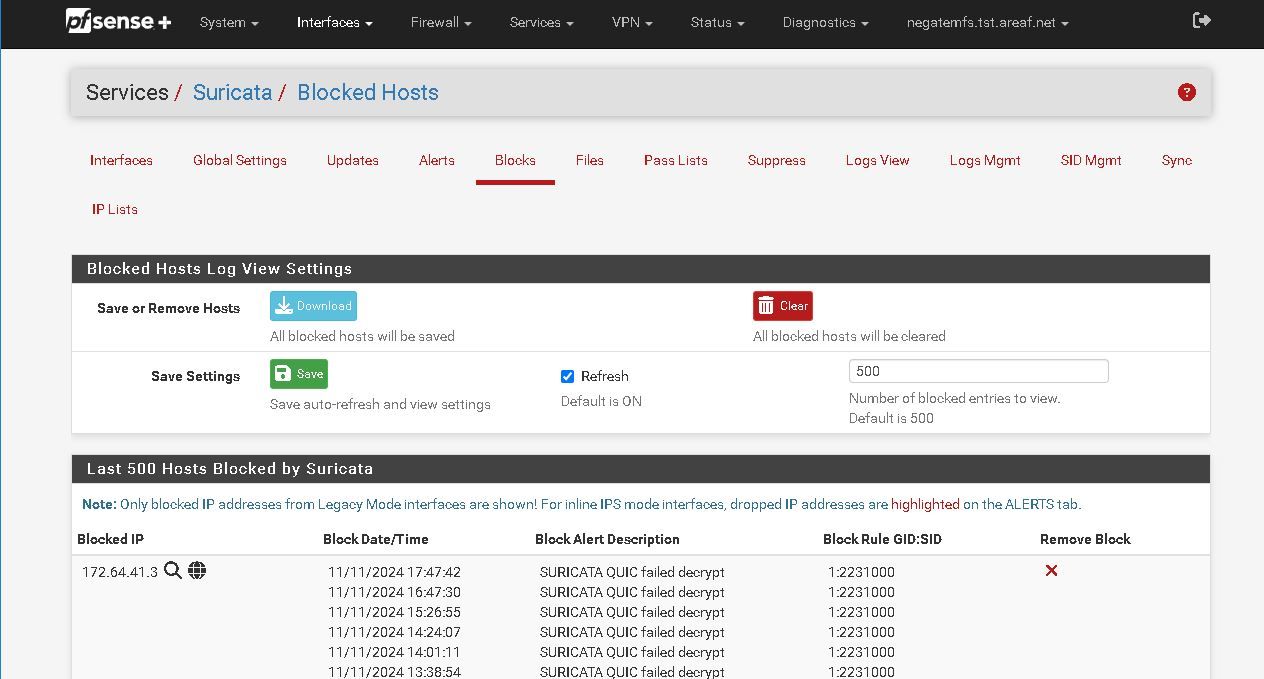
Suricata Permit QUIC
-
What is a good way to have suricata not block and QUIC?
-
-
@focaccio Only block what you want and don't block everything.
-
@Bob-Dig i can see that approach, since QUIC is encapsulated in UDP maybe there is no easy way to permit all QUIC? but with deep inspection one would think it could be possible. also maybe a permit any udp on port 443 would work also?
-
@focaccio You can disable individual rules from the Alerts tab or rules lists.
I don't know what "failed decrypt" means, AFAIK Suricata can't inspect any encrypted traffic.
-
That alert is coming from the built-in QUIC-events rules that ship with the Suricata binary.
The events rules are simply informational in nature and don't indicate any malware or other compromise. I suggest disabling that rule or else using the "suppress by SID" feature on the ALERTS tab to prevent the alert the resulting block of a host.