@mmarco said in Suricata scheduling rules:
@bmeeks thank you for the very good explanation.
Yes , it fully makes sense what you say. So my idea will not work .
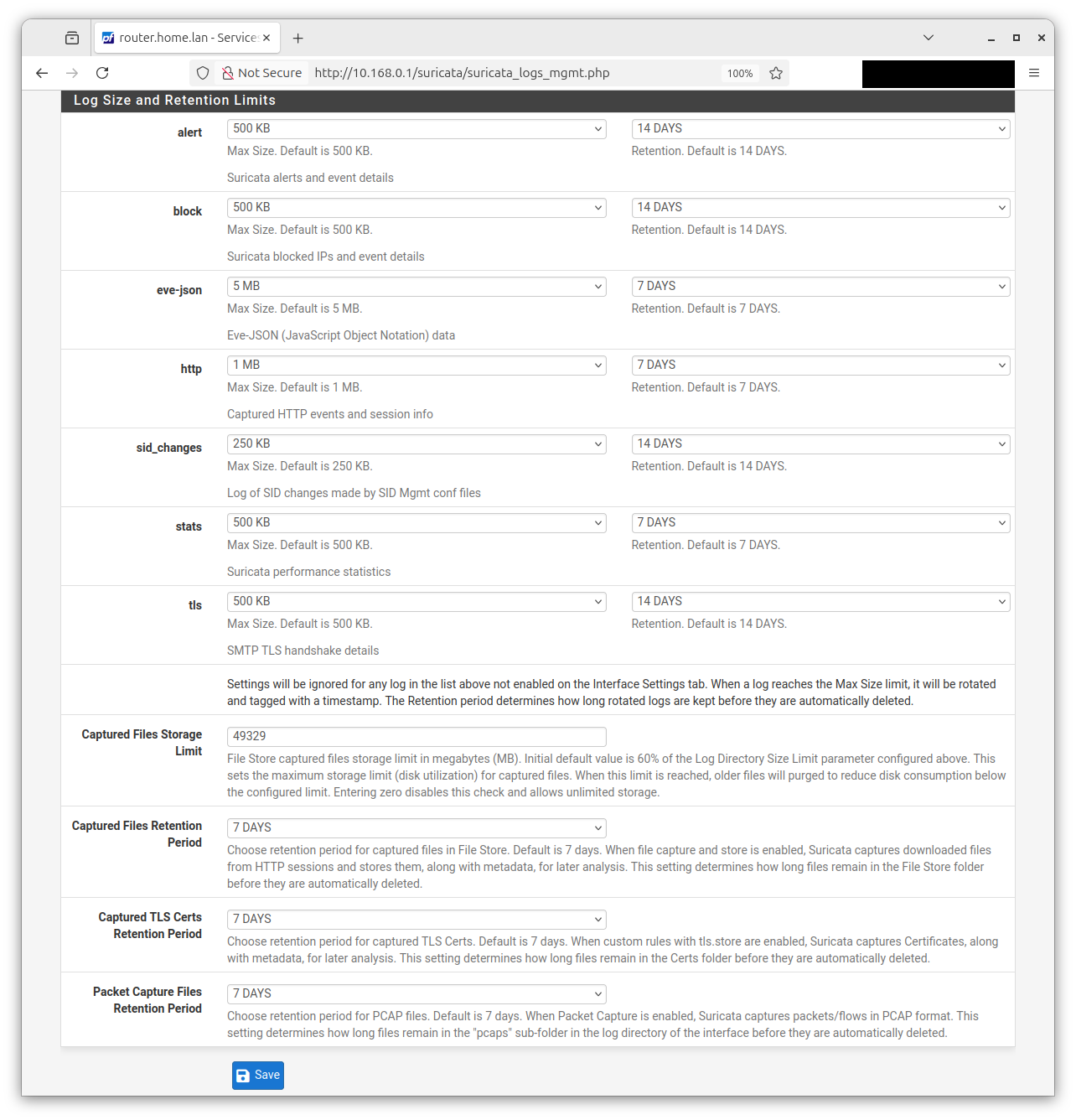
I don't know how to recalculate rules, so my first thought was to simply save two configuration profiles in some other folder and then swap them, but then I realized that these rules get updated, and if I do this, I will be using outdated rules.
So the only way would be to "tell" frontend to rebuild rules once I change SID management configuration, but I don't know how to trigger that, except perhaps to try to simulate request on GUI.
You could adapt the official Suricata rules management tool from upstream, suricata-update to potentially accomplish what you wish. Here is a link to the official documentation for that tool: https://docs.suricata.io/en/latest/rule-management/suricata-update.html. That tool is packaged and deployed within the Suricata package on pfSense. So, the code is there. It's just not normally used on pfSense.
You will have to adapt and customize the usage of that tool a bit in order to have it work within the confines of the existing GUI code and the logic used with the Suricata package on pfSense. But if you point that tool to the master rules repository and to the output rules directory for a Suricata instance on pfSense, in theory it should be able to construct a suricata.rules file for you. You would just need to duplicate the dropsid.conf and any other SID management files you created in the GUI out to plaintext files in a directory that suricata-update can access and use. I've never tried this, but I believe it could be make to work with some customization.
I have considered a few times in the past attempting to incorporate this upstream tool into the Suricata GUI package code, but have not yet seriously attacked the problem nor analyzed it deeply enough to identify any potential show stopper issues.