Simple way to open up SSH port from LAN to DMZ
-
Hi
After spending most of yesterday trying failing miserably to setup an SSH port from my LAN to my DMZ, I'm asking for help.
I have a pfsense firewall that has a LAN network on 192.168.1.x and a DMZ on network 192.168.2.x
I've setup a small server on the DMZ on 192.168.2.20 and that works fine for external access. I've routed ssh traffic from the WAN to it and it's OK.
I'm trying to open a port so that I can access a local server using ssh from my LAN (192.168.1.8) to the server on 192.168.2.20.
I thought that doing the same port configuration on the WAN but changing it to come from the LAN work work., but no dice.
My google searching seems to produce nothing but garabage from Reddit as the top 100 hits.
There;s talk of NAT reflection, which I assume means I go from the LAN to the WAN to the DMZ.
I would have thought a simple rule on the DMZ would have been enough but I've gone around in circles so many times that my head hurts, None of the examples seem to work for me at all. I'm so confused about what I think should be easy, but is clearly not.
Can somebody point me to a simple way I can open up ssh between my LAN and DMZ please?
Thanks
Rob
-
@rwillett what firewall rules do you have for LAN and DMZ at the moment?
No NAT or NAT reflection is necessary.
Usually for the LAN to be able to access SSH on .2.20, you'll need a rules on LAN, like
IPv4, proto tcp, source 192.168.1.8, port any -> destination 192.168.2.20, port 22
The firewall rules are in direction 'in' (exception are floating rules) and 'quick'.
Direction 'in' is from the router 'looking' to the network in question. 'in' for the LAN network refers to connections coming from the LAN into the router.
'quick' means the first matching rule is used and no further rules are evaluated.You create the rule in the network the connection is initiated, LAN in that case.
-
Thanks for the helpful reply.
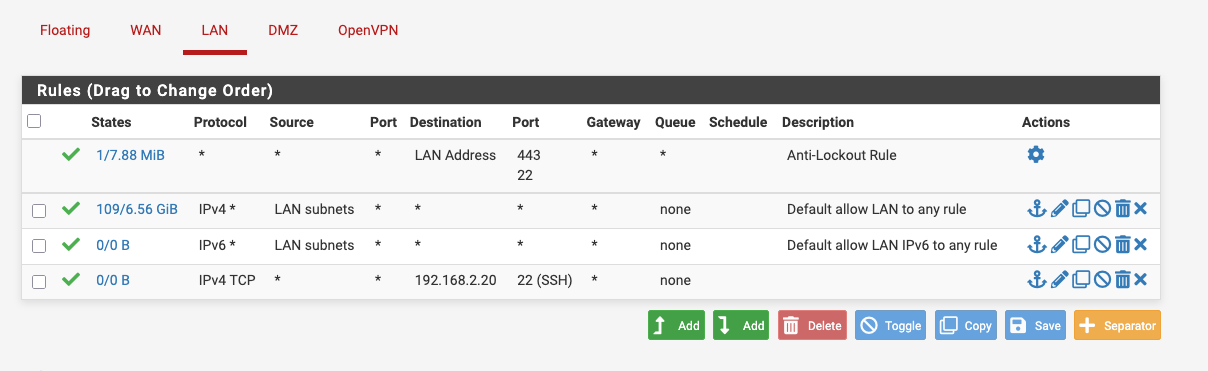
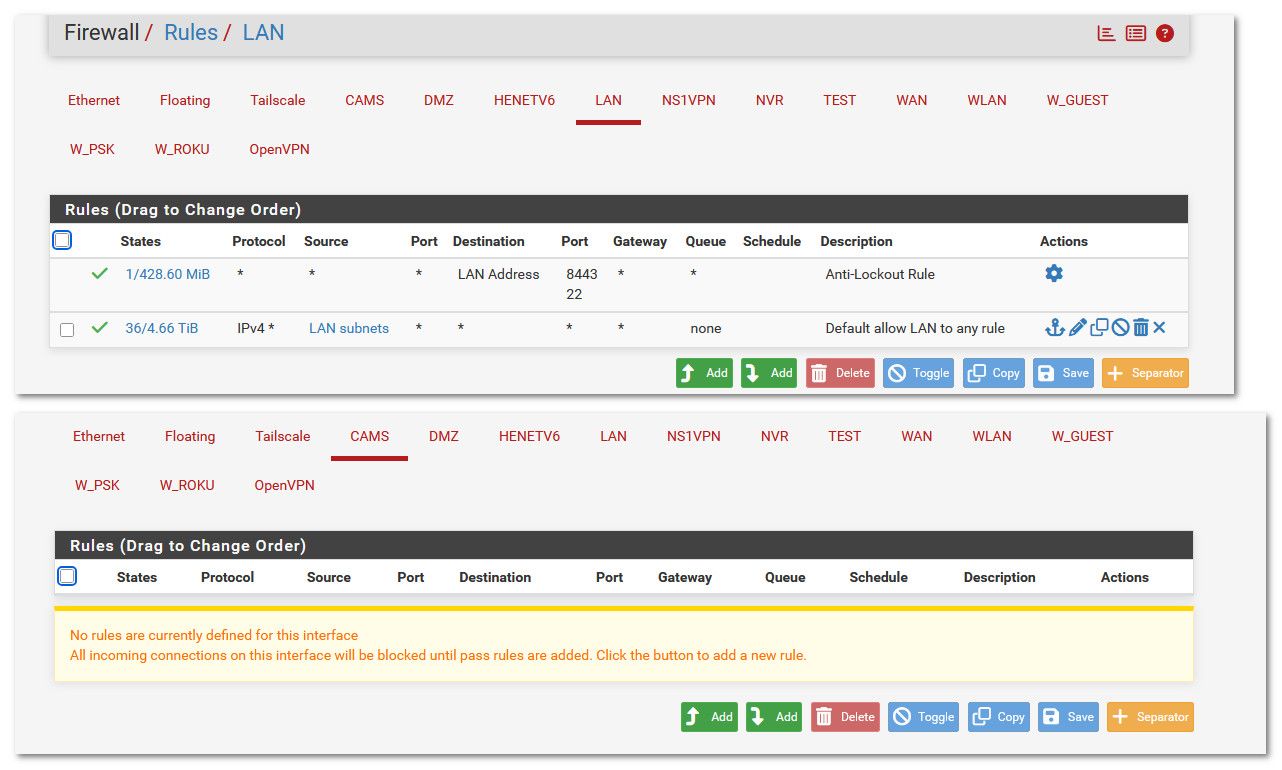
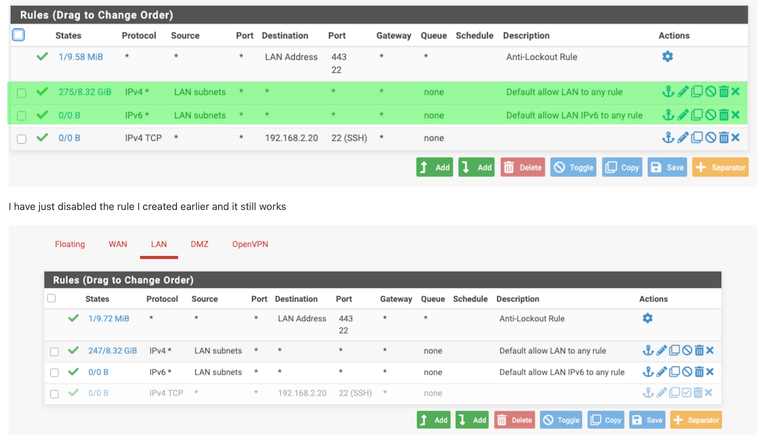
On my LAN network I have this rule
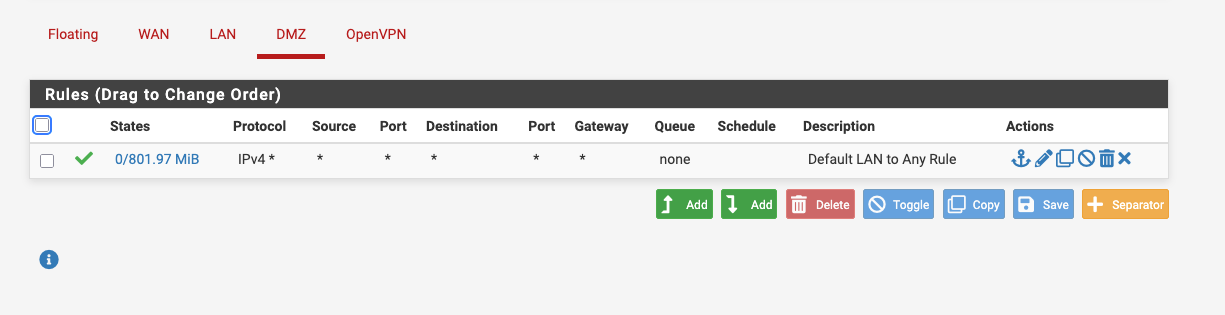
On the DMZ network I have this rule
The rule you described in your mail is slightly more specific than mine as it has the host address in it, but I don't see a fundamental difference. I have tried that rule before as well.
Thanks
Rob
-
@rwillett since the rules are quick rules, you see the rule after the 'Default Allow LAN ...' rule never matches (0/0B).
The default allow does already allow LAN traffic to travel everywhere, including DMZ. And the same is true for DMZ, it's not isolated.With the default allow rule on LAN you should be able to access the SSH server.
What error you get when you try to connect from 192.168.1.8 to 192.168.2.20? If you run ssh with -v (e.g.
ssh -v 192.168.2.20) you get more feedback about the connection progress. -
Hi the ssh connection has worked. I must have done this twenty times yesterday and it never worked.
I have no idea why this has worked now.
Thanks very much, but I now need to work out what has changed to allow this. I'm really confused now.
Rib
-
And it didn;t work when I put that rule in, so nothing has changed unless it's a timing issue from the firewall reloading the rules.
I'm really confused.
Rob
-
@rwillett please show the
ssh -voutput when you try to connect and doesn't work.
Firewall rules-wise, it either works or not and if you check the rules, all with '0/0 B' in the 'States' column are never matched. -
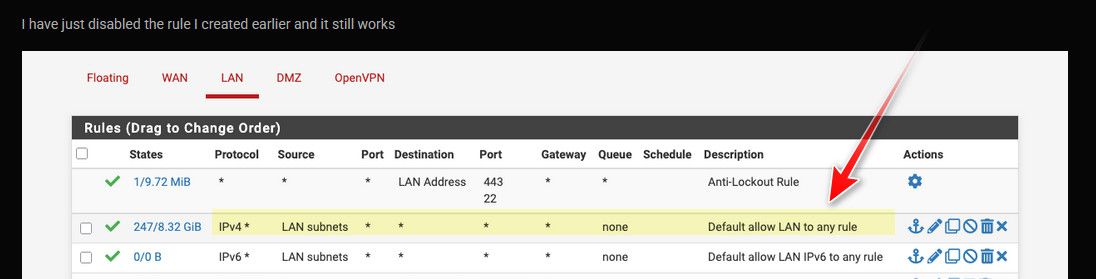
Hi I can't show the ssh output you as it now works.
Looking at the tables again, the LAN rule I added is not activated as it has 0/0B
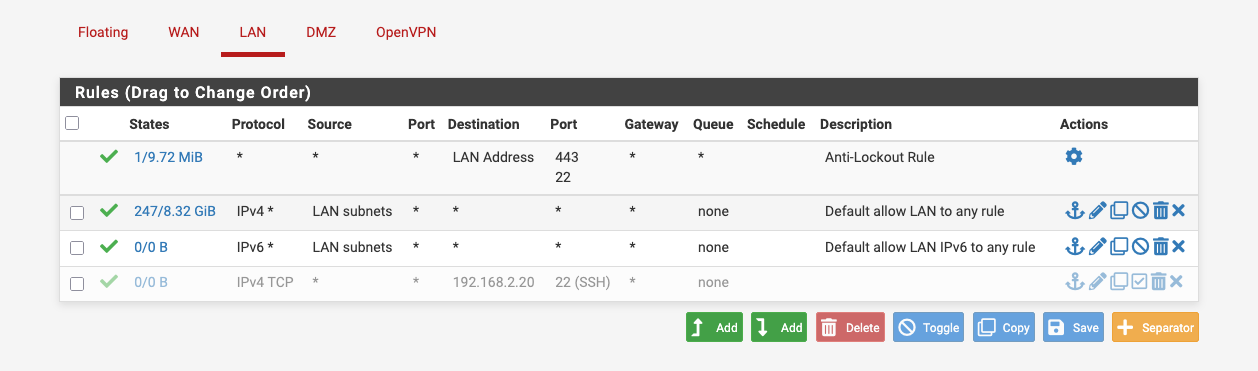
I have just disabled the rule I created earlier and it still works
Nothing has changed on the NAT side.
The only thing I noticed was that my Macbook Pro has two interfaces, a wired Ethernet and an wifi connection. The wifi connection was trying to connect to the hotspot on my mobile phone. The wired connection is static and stable. I've just changed the wifi to connect to my hotspot on the phone and the ssh connection still works, so its not that.
I've not changed the ssh settings on the server in the DMZ, its not been rebooted, but clearly it works.
I don't like this as I have no idea whats gone on its annoying but I can't get it back to not working, which is a funny position to be in.
Grateful for your help here but I'm not sure I can break it the same way now.
Thanks
Rob
-
@rwillett
Kill any existing states and try with MBP on WiFi? -
@rwillett you understand your first default lan rule allows any client on your lan to go anywhere you want - be that ssh, http, https etc.. doesn't matter if that something is out on the internet or on your local dmz segment. Wouldn't even matter if your dmz rules were empty or deny specific. Because the return traffic would be allowed by the state created when your default allow rule let it talk to your dmz host
If your not allowed to get to your 192.168.2.20 box you either have a floating rule that is over riding your lan rule, or you mention something about two interfaces - you could have asymmetrical flow?
More than likely if you can not talk to something on your dmz with the default lan rule your problem is the box your talking to host firewall, or lack of a gateway, or different gateway than pfsense dmz IP.
I can talk to my ip cameras from my lan, no need for any return rules on the cam interface... My default lan rule allows anything on the lan to go anywhere - kind of what any means ;)
-
@rwillett move your ssh rule to the top see if that helps…
-
johnpoz LAYER 8 Global Moderatorlast edited by johnpoz Mar 29, 2025, 10:15 AM Mar 29, 2025, 10:14 AM
@JonathanLee how would that help??? This rule allows everything!!
His issue is not related to needing to allow 22 on lan to dmz or any rules on his dmz.. this rule allows ANY to ANYWHERE!! Which includes his DMZ...
-
@rwillett you understand your first default lan rule allows any client on your lan to go anywhere you want - be that ssh, http, https etc.. doesn't matter if that something is out on the internet or on your local dmz segment. Wouldn't even matter if your dmz rules were empty or deny specific. Because the return traffic would be allowed by the state created when your default allow rule let it talk to your dmz host
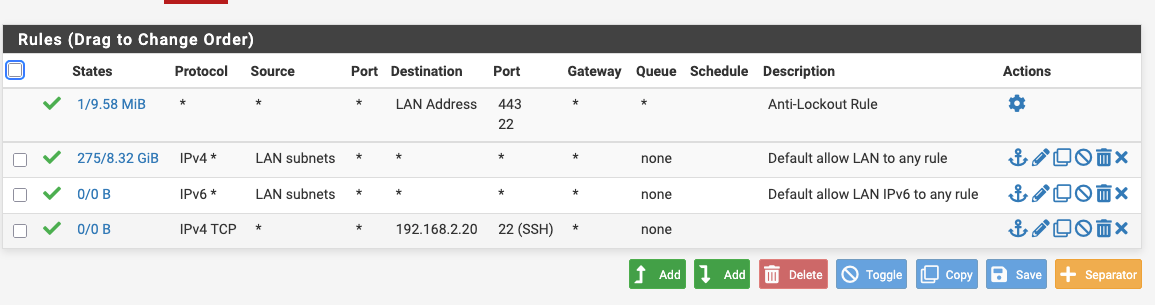
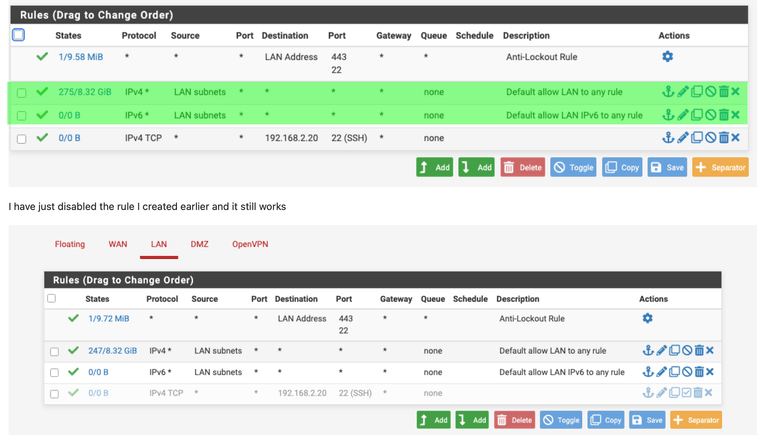
I do now , so I've removed that rule that I inserted so I am back to the default out of the box rules for the LAN and DMZ and it's working correctly.
I do not know why it didn't work before and there may have been some weird behaviour from the wifi, the Macbook might have tried to connect to various hotspots on my various personal and wok phones, or the Ethernet. I misunderstood the default rule on the DMZ, I now know.
I cannot create the issue that my ssh did not work. It works fine now. I think this is some weird networking from my Macbook due to wifi and the Ethernet doing something, but I don't know what. I;'m back to the out of the box rules and it now works. I'm happy with that and thanks very much for the help. I appreciate the time taken,.
best wishes
Rob
-
@rwillett said in Simple way to open up SSH port from LAN to DMZ:
Macbook due to wifi and the Ethernet doing something
is the macbook the client you were connecting from, or is the device that was in the dmz.
Is this wifi network a different network, other than your lan or dmz? Or is the wifi a guest network or something with isolation setup? Without more details can not tell you what was going on.
Glad you got it sorted.
-
I was connecting from a Macbook to a newly created Linux server in the DMZ. I had checked that ssh was working on the Linux server, I did not try to connect from the DMZ to the LAN.
I have a wifi network running OpenWRT on the 192.168.1.x network, but nothing wifi related on the 192.168.2.x network. It now just has two low level Linux servers for work related activities. It only had one before and that’s been there for a long time even before the pfsense firewall. I had a Smoothwall there before.
I'm still trying to work out what was going on, but I'm coming to the conclusion that some networking on the Macbook was simply wrong and that I'm now back to the OOTB config and it just works. The rules I created were at the bottom of the list so it should have worked with the default settings, so even if I screwed the rule up, it wouldn;t have made any difference as the first rule should have matched.
I've never used a floating rules so thats not the issue.
I'll be honest and say I have no idea what went on, but its working now AND I udnerstand the default rule so I'm going to chalk it up to a bad day but its fixed.
Thank you all for your help
Rob -
@johnpoz why does he have any ACLs if he has a any any rule ??? I didn’t even see that.
-
@JonathanLee I have no clue to what you are talking about???
-
Assuming ACL is a pfsense ACL rather than Anterior Cruciate Ligament, the answer is "No".
Most of the pfsense setup is out of the box. Didn't even know pfsense did ACL's until now.
https://docs.netgate.com/tnsr/en/latest/acl/standard.html#standard-acl-example
I think the issue was with my Macbook, no idea what happened, but suspect it was a networking config on the client and the firewall was OK. I could connect to 192.168.1.1 (the pfsense firewall) from the Macbook, but it was the 192.168.2.x connection that was the issue.
Thanks
Rob
-
@johnpoz This reply was related to the any any rule comment
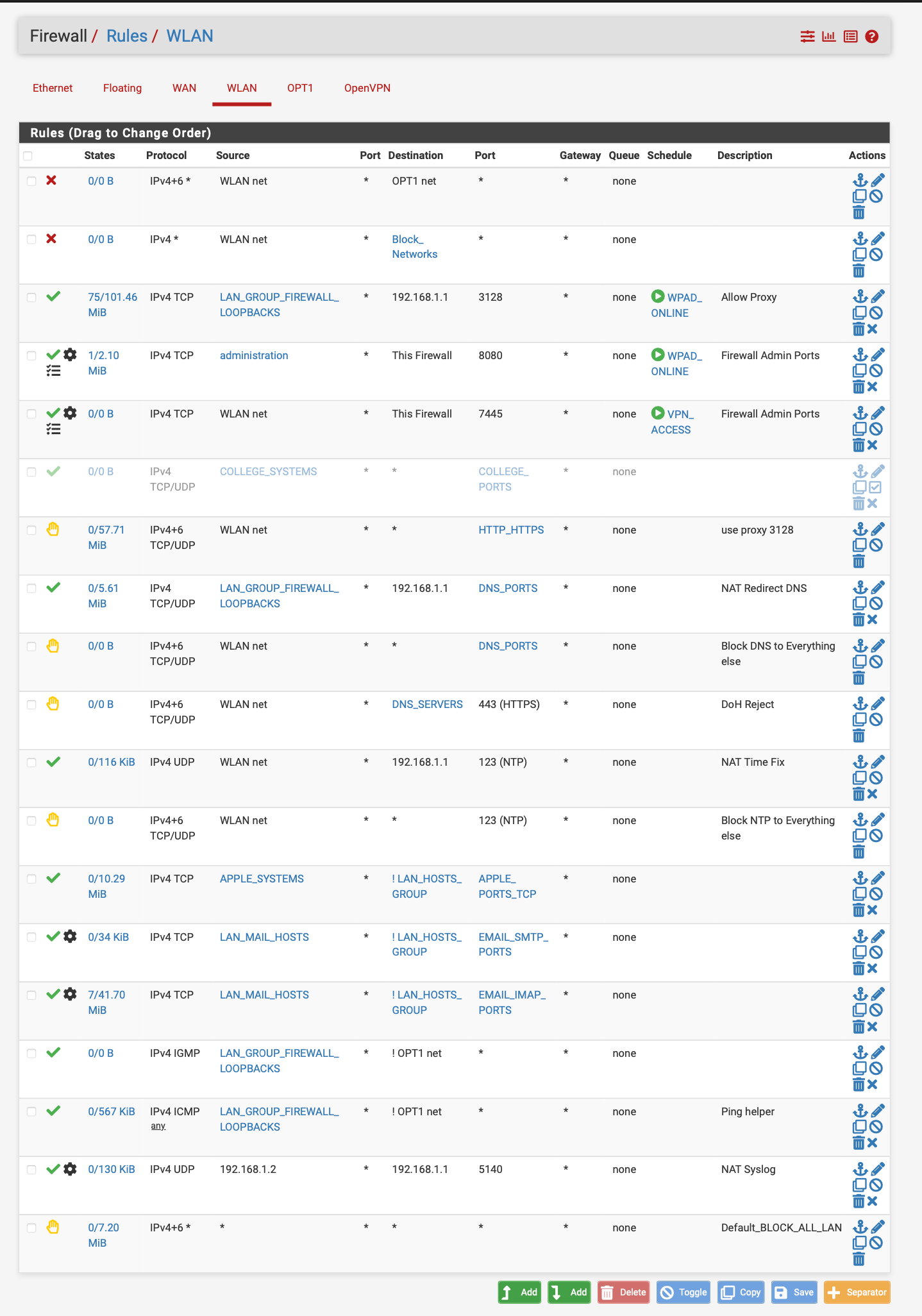
I did not see this before its any any rules so why have any rules at all it allows any thing and everything out.
Now that it is working try, working on making it more granular too so it is just not approving everything and anything.
Make it more specific to your needs. This is an example, I have time based rules, specific areas are blocked from being accessed. I have rules I enable when I need outbound vpn ports to the university. Some default blocks etc.
pfsense can do so much why just leave it as approve everything.... At least set some time rules up. You lock a door when you leave right so why not lock a network when you leave or are not using it. I have time rules for my proxy see WPAD online or VPN access hours...
Another example of use of time based restrictions. Especially if you have a vpn to access your network set up for like a private cloud or whatever it may be.. lock it down or hypothetically lock the door when you are not using it.. -
Thanks for the information. I didn't set this rule up. This is what came out of the box.
I'll read it through and see what I need. Since I work from home and have two teenage daughters, I tend to need the network 24/7 :)
Your point on being granular is well made and I've been lazy. I'll look at how to take as much access oput as I can.
Thanks
Ron